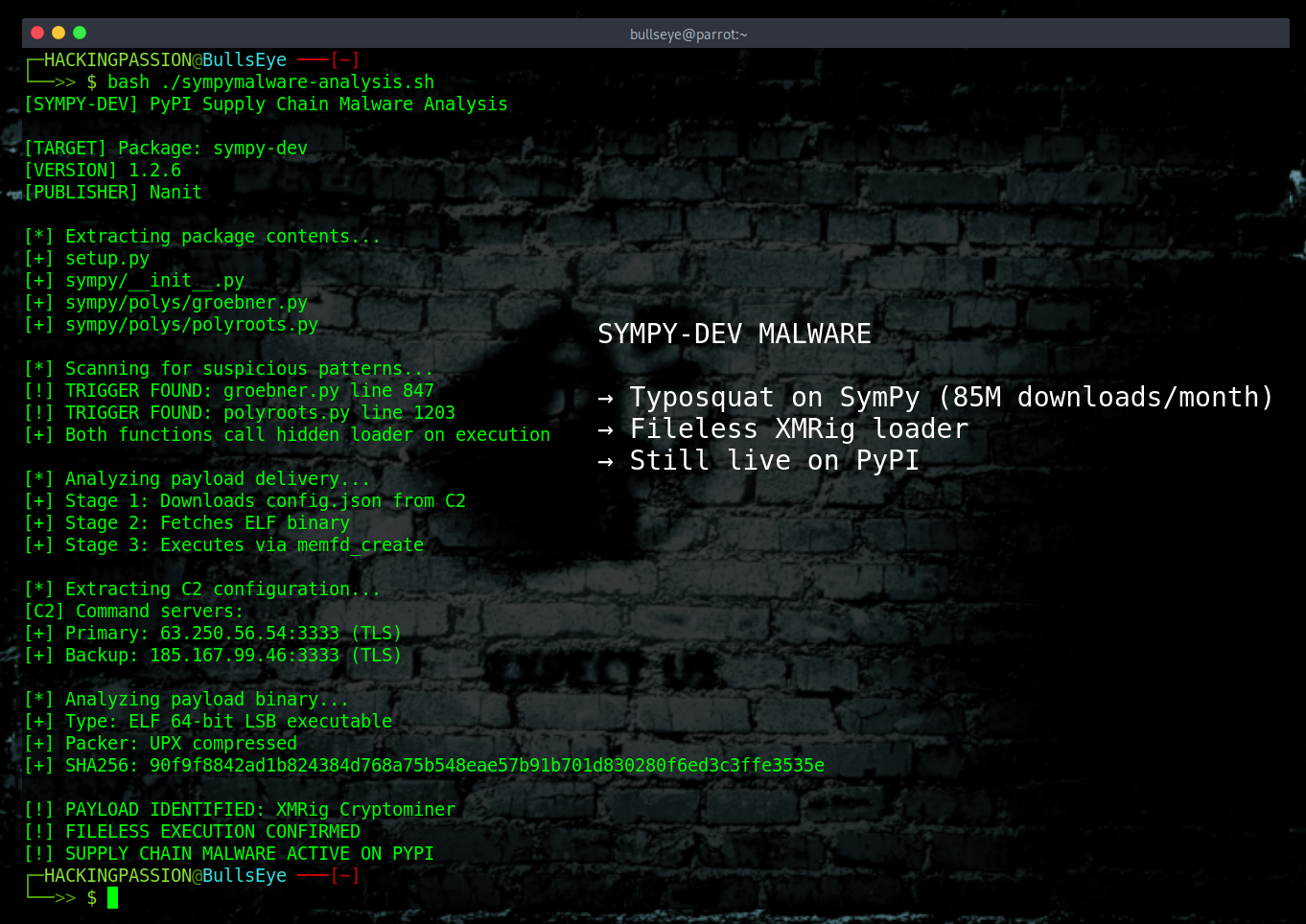
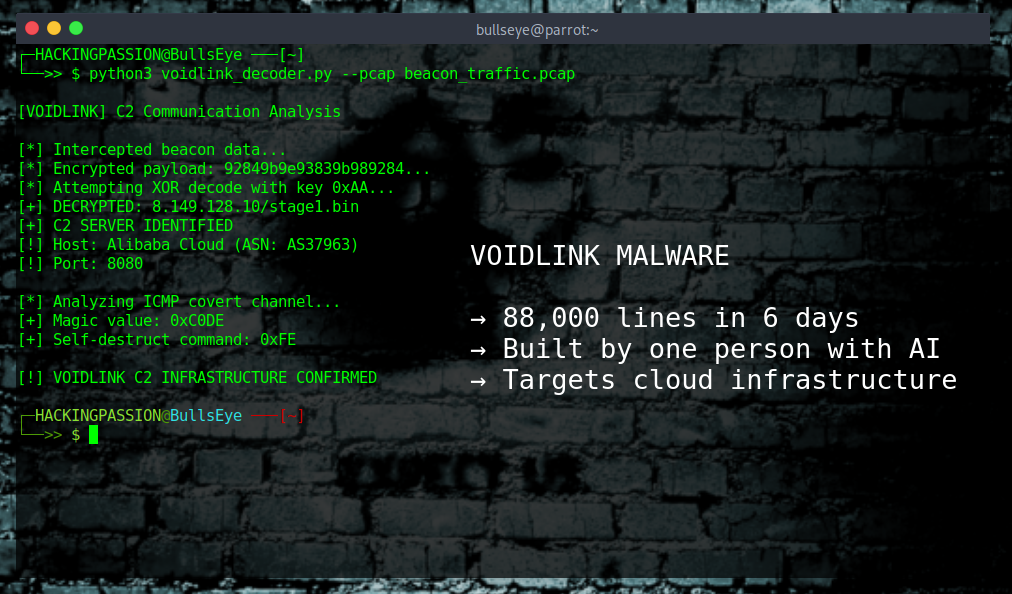
Ollama Security Failure Exposes 175,000 AI Servers to Attackers
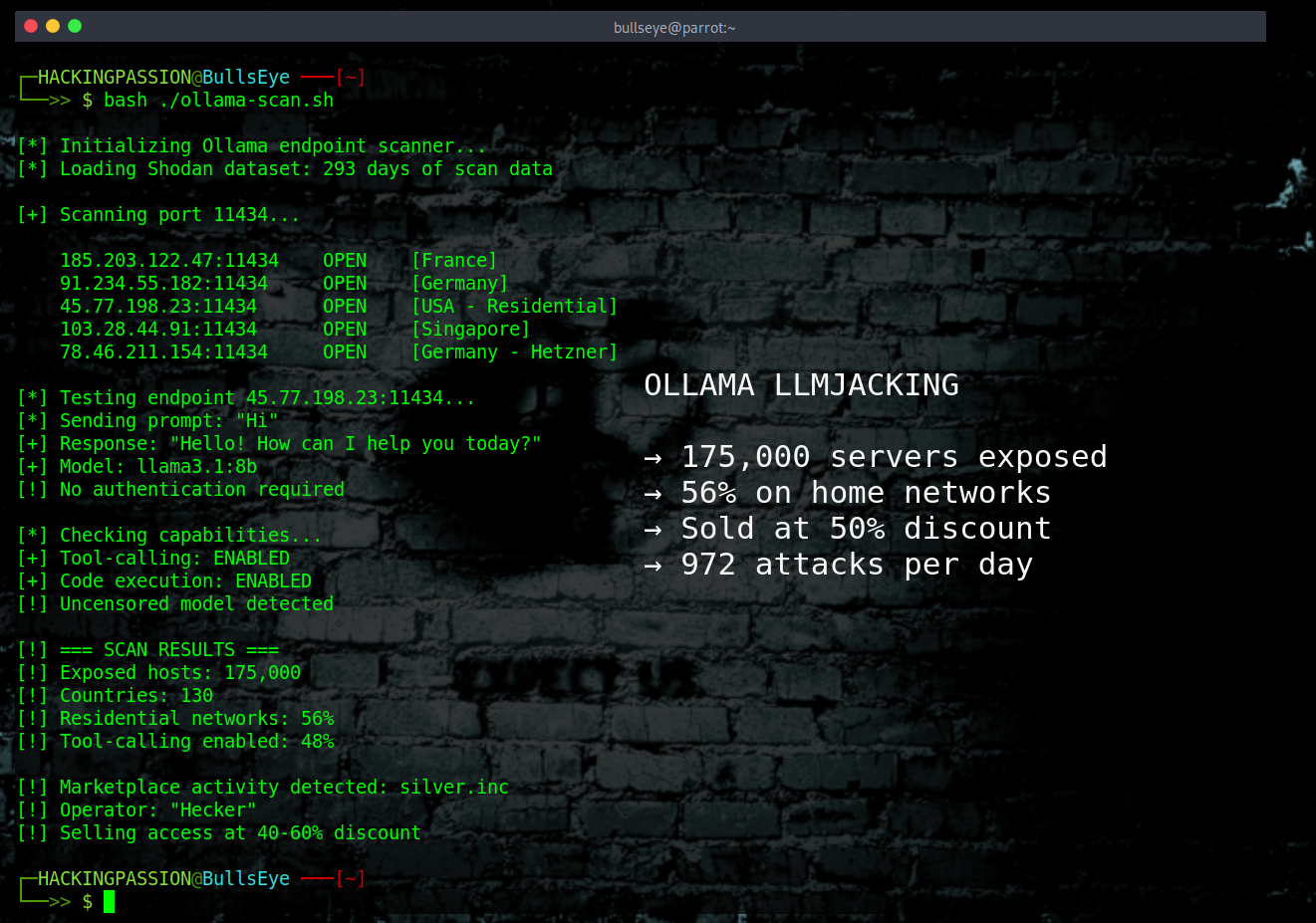
175,000 AI servers wide open to the internet. 130 countries. Attackers are selling access to other people’s hardware at a 50% discount, and using it for spam, phishing, and worse. 🧐
Running AI locally sounds like the safe option. No cloud, no third parties, everything stays on your own machine. So people install Ollama, fire up a language model, and assume they’re good. Except the default settings expose the server to anyone who knows where to look, and a lot of people know where to look.