Ethical Hacking Techniques With SSH Secure Tunnels and Data Transfers

Ethical hacking techniques with SSH: Secure tunnels and data transfers
Introduction
Welcome to this comprehensive guide on Ethical hacking techniques with SSH: Secure tunnels and data transfers. In this easy-to-follow guide, you’ll get the inside scoop on why secure tunnels and data transfers are the unsung heroes of ethical hacking. Plus, you’ll learn how to up your cybersecurity game with the help of Secure Shell (SSH).
Why is Ethical Hacking Important?
Ethical hacking, often termed as ‘white-hat hacking,’ is the practice of intentionally probing systems for security vulnerabilities. The primary purpose is to discover weaknesses from a malicious hacker’s viewpoint to better secure systems.
The Role of Secure Data Transfers and Tunnels
In ethical hacking, secure data transfers are not just an option; they are a necessity. When you are testing a system for potential weaknesses, it’s crucial that the data being transferred is encrypted and secure. Secure tunnels play a pivotal role in this, allowing ethical hackers to operate without risking data leakage.
SSH: The Unsung Hero in Ethical Hacking
SSH, or Secure Shell, is more than just a protocol; it’s a suite of utilities that allow for secure network services over an unsecured network. SSH provides strong password authentication and public key authentication, along with a robust set of features to handle encrypted data communication between two networked computers.
Quick Tip: Always ensure you’re using updated SSH protocols to minimize vulnerabilities.
What to Expect in This Guide
- Understanding SSH (Secure Shell)
- Setting Up SSH for Ethical Hacking
- SSH Secure Tunnels
- SSH for Secure Data Transfers
- Advanced Ethical Hacking Techniques with SSH
Understanding SSH (Secure Shell)
SSH, which stands for Secure Shell, is a cryptographic network protocol predominantly used for secure data communication and remote command execution. But what makes it a staple in ethical hacking?
What is SSH?
SSH serves as a secure channel over an unsecured network. In simpler terms, it’s like a digital handshake. SSH helps confirm that you are who you say you are, sends your commands to the remote computer, and then brings back the responses straight to your screen.
Table 1: SSH Protocol Suite
| Component | Function |
|---|---|
| SSH-TRANS | Transport Layer Protocol |
| SSH-AUTH | Authentication Protocol |
| SSH-CONN | Connection Protocol |
How Does SSH Work?
SSH operates on a client-server model. The SSH client initiates the setup of the secure connection, and the SSH server listens to incoming connections. Here’s a simplified flow:
- Negotiation: The client and server agree on the encryption standards.
- Authentication: The client proves its identity to the server.
- Encryption: Data sent between the client and server is encrypted.
Note: SSH uses public-key cryptography for authenticating the remote computer.
Why is SSH Important in Ethical Hacking?
SSH is indispensable in ethical hacking for several reasons:
- Data Encryption: Ensures that the data is unreadable to third parties.
- Integrity: Verifies that the data has not been tampered with during transmission.
- Authentication: Confirms the identity of the communicating parties.
Setting Up SSH for Ethical Hacking
Before diving into the nitty-gritty of SSH tunnels and secure data transfers, it’s essential to ensure that your SSH setup is optimized for ethical hacking activities. Excited to get started? Let’s walk through the must-know steps to get SSH up and running on your system.
Basic Requirements
To get started with SSH, you’ll need the following:
- A computer running Linux or macOS (SSH is often included by default)
- Basic understanding of terminal commands
- Network access to the server you wish to connect to
Installing SSH
If SSH is not already installed on your system, you can install it using package managers. Here’s how:
On Ubuntu:
|
|
On macOS:
|
|
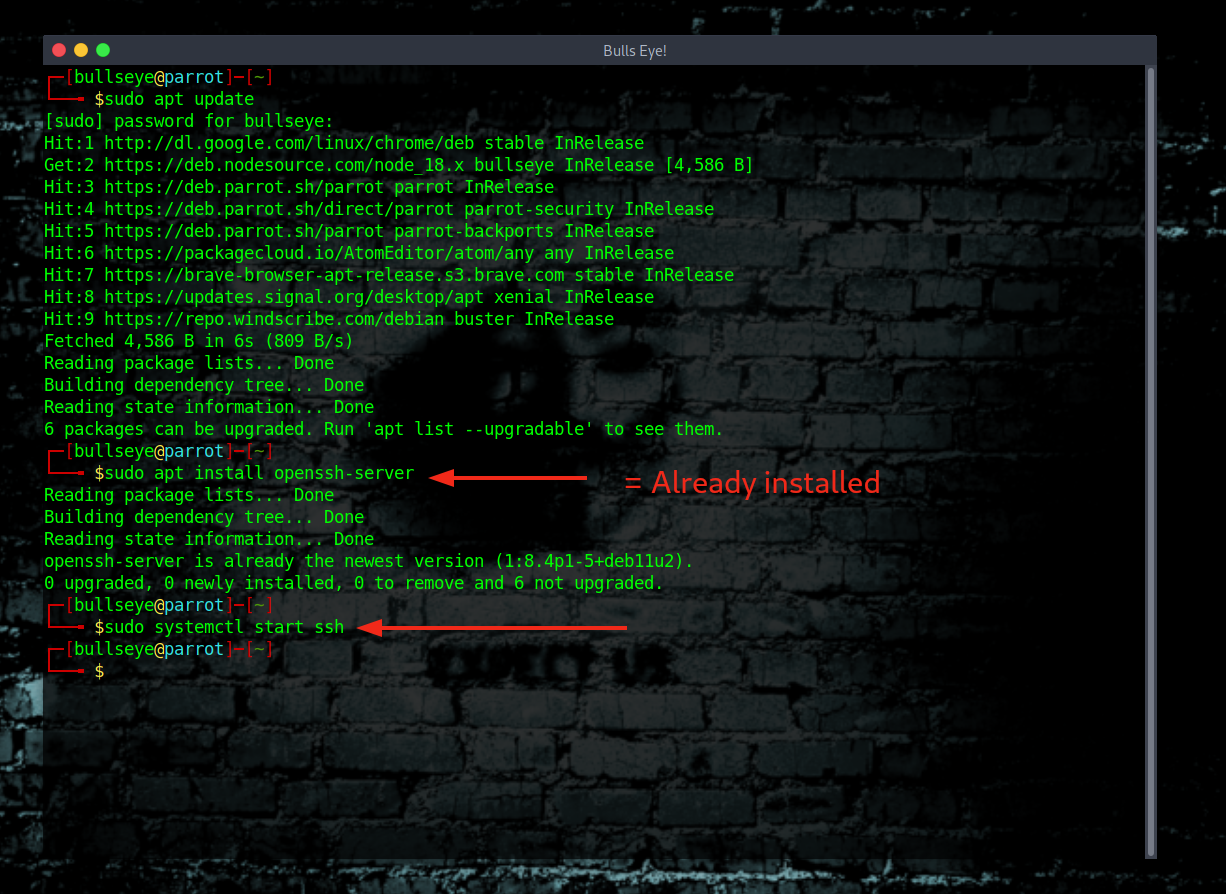
Pro Tip: Always check for the latest version of SSH to ensure you have the most secure and updated features.
Configuring SSH Settings for Secure Tunnels
Once SSH is installed, the next step is to configure it for secure tunneling. You can edit the SSH configuration file usually found at /etc/ssh/sshd_config.
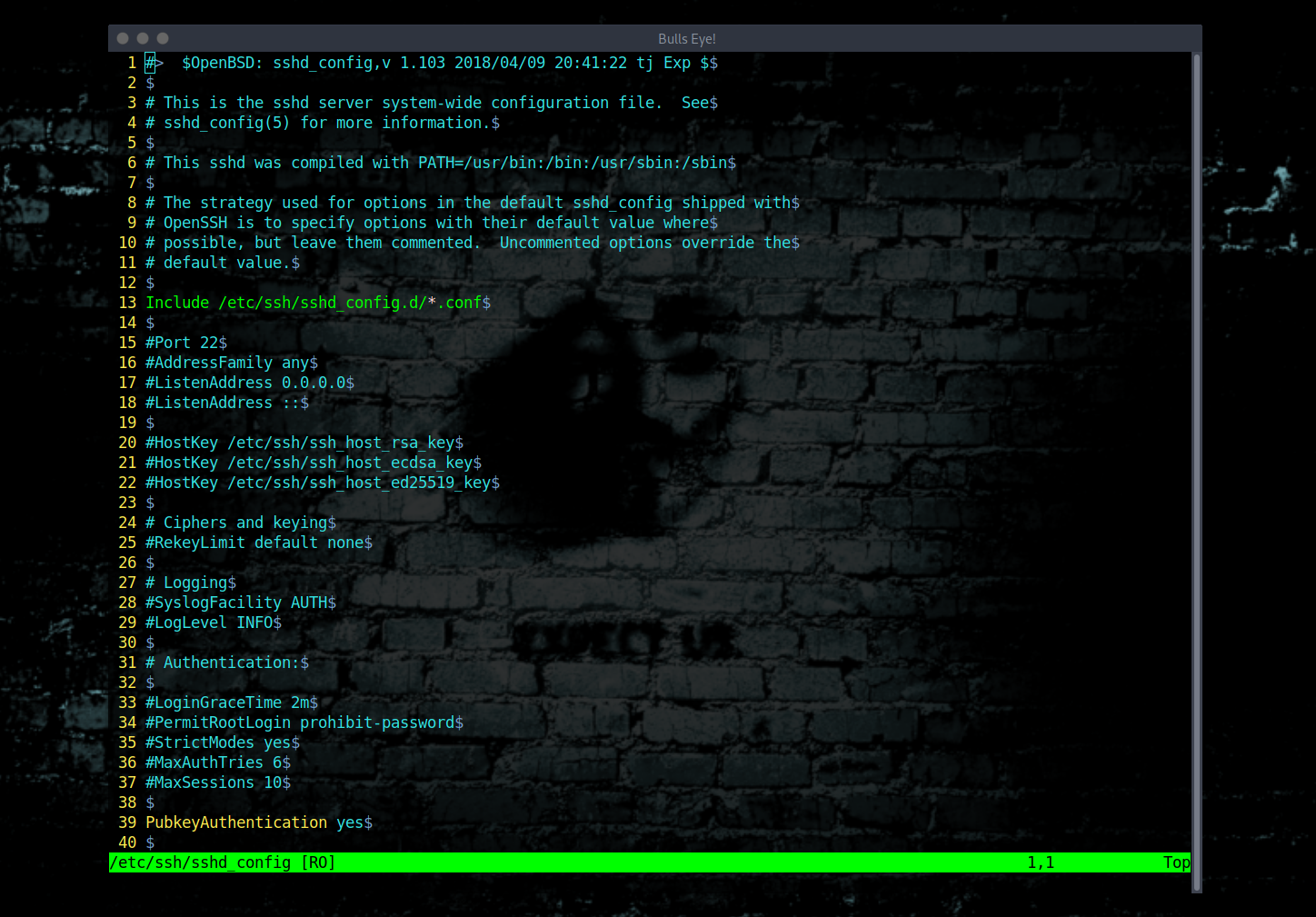
Table 2: Important SSH Configuration Parameters
| Parameter | Description |
|---|---|
PermitRootLogin |
Controls root access |
PasswordAuthentication |
Enables or disables password login |
AllowUsers |
Specifies allowed users |
To restart the SSH service after editing the config file, run:
|
|
SSH Secure Tunnels
SSH tunnels are a powerful tool for securing network traffic. They don’t just put a lock on your data; they also guide you safely when you’re wandering through the wild parts of the internet. If ethical hacking is your thing, you’re going to love these digital bodyguards. Now, let’s dig into why you need them and how to set them up.
What Are SSH Tunnels?
An SSH tunnel is essentially an encrypted tunnel created through an SSH protocol connection. By sending your internet activity through this secure tunnel, it’s like sealing your data in a vault—keeping it hidden from nosy onlookers.
Table 3: Types of SSH Tunnels
| Type | Description |
|---|---|
| Local | Forwards data from the client to the server |
| Remote | Forwards data from the server to the client |
| Dynamic | Forwards data from the client to the server, dynamically determining the destination |
Types of SSH Tunnels
SSH tunnels come in different flavors, each with its unique use-case:
- Local Port Forwarding: Useful for accessing a remote service as if it were local.
- Remote Port Forwarding: Allows a remote service to be accessed as if it were local to the server.
- Dynamic Port Forwarding: Acts like a SOCKS proxy, dynamically routing traffic based on the client’s requests.
Expert Tip: Use dynamic port forwarding for the most flexible tunneling options.
Creating an SSH Tunnel for Ethical Hacking
Setting up an SSH tunnel for ethical hacking is straightforward. Here’s a basic guide:
Local Port Forwarding
|
|
Remote Port Forwarding
|
|
Getting the hang of SSH tunnels is like adding a Swiss Army knife to your ethical hacking toolkit. It doesn’t just make you more skilled; it takes your whole cybersecurity game to the next level.
SSH for Secure Data Transfers
Transferring data securely is a cornerstone of ethical hacking. One mistake, and sensitive information could end up in the wrong hands. SSH offers two primary methods for secure data transfers: SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol).
SCP: Secure Copy Protocol
SCP is a means of securely transferring computer files between a local and a remote host or between two remote hosts, using the SSH protocol.
Basic SCP Syntax:
|
|
Options:
-P: Specifies the port-r: Recursively copy entire directories
Note: SCP works well for quick file transfers but lacks features like resuming broken transfers.
SFTP: SSH File Transfer Protocol
SFTP is another secure file transfer utility that uses SSH. Unlike SCP, it provides a range of features like the ability to resume broken transfers, directory listings, and remote file removal.
Basic SFTP Commands:
get: Download fileput: Upload filels: List directoryrm: Remove file
|
|
Choosing Between SCP and SFTP
| Feature | SCP | SFTP |
|---|---|---|
| Speed | Fast | Moderate |
| Features | Basic | Extended |
| Resume Broken Transfers | No | Yes |
In ethical hacking, both SCP and SFTP are useful, but your specific needs will dictate which is more suitable.
Advanced Ethical Hacking Techniques with SSH
SSH is not just for secure communications or data transfers; it can be a powerful tool for ethical hacking when used creatively. Let’s explore some advanced ethical hacking techniques you can perform with SSH.
Port Scanning with SSH
SSH can serve as a rudimentary port scanner, enabling you to identify open ports on a remote host. The ssh command itself can be used for this purpose.
Basic Syntax:
|
|
Note: This is not as feature-rich as specialized tools like Nmap, but it’s a quick way to check port status.
Remote Command Execution
SSH allows for the execution of commands on a remote server without the need for a full-fledged login session. This can be handy for running quick diagnostics.
Example:
|
|
SSH Tunneling for Web Traffic
While we’ve discussed SSH tunnels for data transfer, you can also tunnel web traffic through SSH. This is a way to anonymize your browsing activities.
Command for Web Traffic Tunneling:
|
|
Here’s what your terminal should look like after setting up SSH tunneling for web traffic:
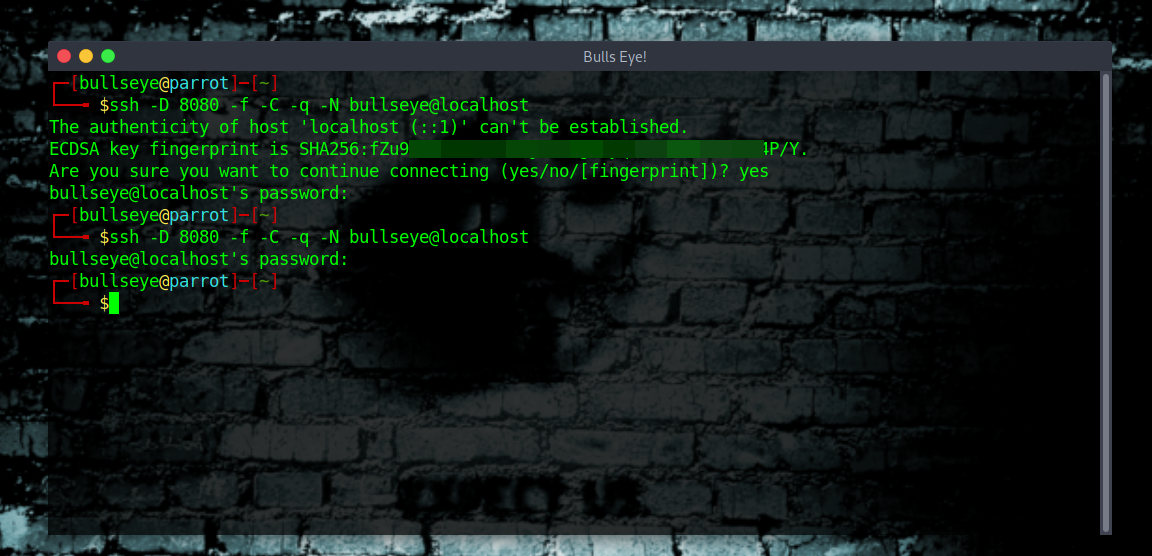
-D 8080: Specifies that the local port is 8080.-f: Forks the process to the background.-C: Enables compression.-q: Quiet mode.-N: No command will be executed after the connection is established.username@ssh_server: Replace with your username and the SSH server you’re connecting to.
Expert Tip: Tunneling web traffic through SSH provides an additional layer of encryption and security.
Key Takeaways
- SSH is versatile and can be used for various advanced ethical hacking techniques.
- Port scanning and remote command execution are quick tasks that SSH can handle.
- SSH tunneling can extend beyond data transfer to anonymize web traffic.
Conclusion
SSH (Secure Shell) is far more than a secure communication protocol; it’s a versatile tool in the ethical hacker’s toolkit. From setting up secure tunnels to transferring data and even performing advanced techniques like port scanning, SSH offers a multitude of functionalities that enhance an ethical hacker’s capabilities.
Key Takeaways
- Understanding SSH: SSH is a cryptographic network protocol used for secure data communication, remote command execution, and other secure network services between two networked computers.
- Setting Up SSH: Proper configuration and understanding of SSH settings can form the basis for many ethical hacking techniques.
- SSH Tunnels: These allow you to forward data securely from one network to another and can be of three types—Local, Remote, and Dynamic.
- Data Transfers: SSH offers SCP and SFTP for secure data transfers, each with their advantages and disadvantages.
- Advanced Techniques: SSH can be utilized for tasks like port scanning and remote command execution, providing a lightweight yet powerful tool for ethical hackers.
Final Note: As with any tool, the ethical implications and legality of SSH’s usage depend on the intent and authorization. Always ensure you have proper permission before engaging in any form of ethical hacking.
Q&A: Frequently Asked Questions
This section aims to answer some of the most frequently asked questions about SSH and its application in ethical hacking.
Q: What is the primary purpose of SSH?
A: SSH is primarily used for secure data communication between two networked computers. It encrypts the data sent over the network, making it difficult for eavesdroppers to understand the information being transferred.
Q: Is SSH only useful for ethical hackers?
A: While SSH is a valuable tool in ethical hacking, its applications extend to system administration, secure file transfers, and more. It is widely used in various domains requiring secure communications.
Q: Can SSH tunnels be used for illegal activities?
A: Like any tool, SSH can be used both ethically and unethically. The ethical implications depend on the user’s intent and whether they have proper authorization to engage in the activities they are performing.
Q: What’s the difference between SCP and SFTP?
A: SCP is optimized for speed and is useful for quick file transfers. SFTP offers additional features like the ability to resume broken transfers and provides a more interactive user interface.
Q: Are there alternatives to SSH for secure data transfer?
A: Yes, there are other protocols like FTPS (FTP Secure) and HTTPS for secure data transfer. However, SSH is often preferred due to its robust security features and versatility.
We hope this Q&A section has answered some of your burning questions about SSH and ethical hacking. If you have more questions, feel free to ask!
Thank you for reading, and happy ethical hacking!
Support My Work
If you found this article helpful and would like to see more content like this, consider supporting my work on Patreon. Your support enables me to continue creating high-quality, in-depth articles on ethical hacking, cybersecurity, and more.