70 Million Bluetooth Chips Have a Backdoor: Sony, Bose, JBL Headphones at Risk
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Your headphones just became a backdoor to your phone. No pairing. No popup. Just Bluetooth range. 70 million chips. Sony. Bose. Marshall. JBL. A debug protocol active on production devices. Attackers can dump your Bluetooth keys, impersonate your headphones, and hijack your phone. 🤔
Three CVEs. Zero authentication required. Full technical disclosure: December 27, 2025 at 39C3.
The vulnerabilities
→ CVE-2025-20700: No authentication on Bluetooth Low Energy → CVE-2025-20701: No authentication on Bluetooth Classic → CVE-2025-20702: Debug protocol exposed that should never be accessible
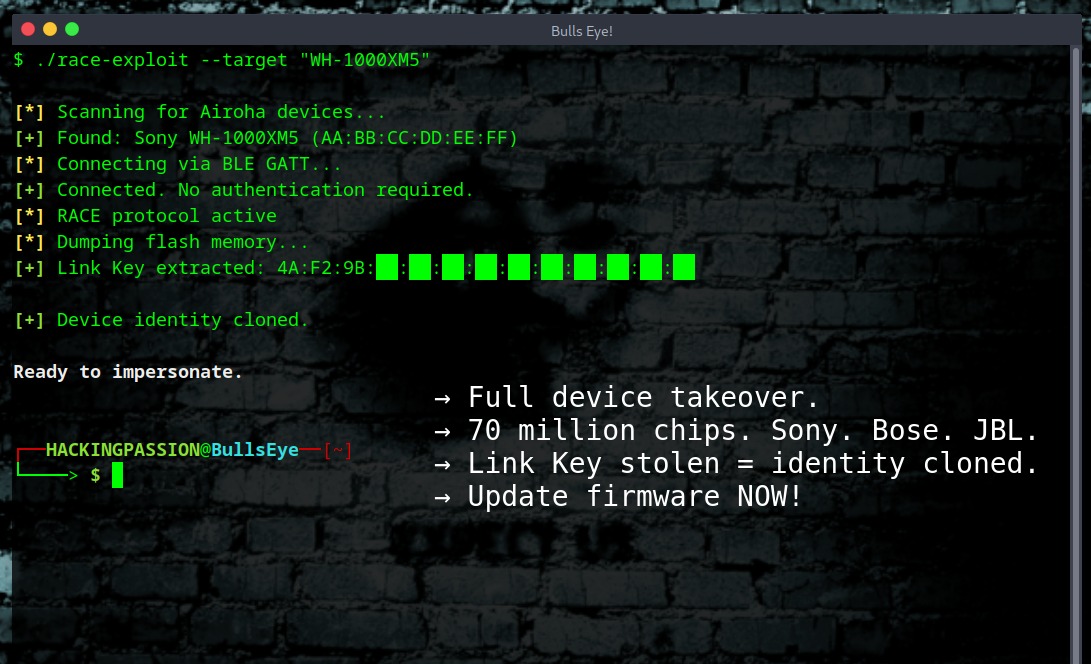
RACE is Airoha’s factory protocol. Meant for testing and firmware updates during production. It exposes read/write access to RAM and flash memory over three channels: USB HID, Bluetooth Classic RFCOMM (channel 21), and BLE GATT services.
The protocol was never disabled before shipping.
An attacker within 10 meters connects via BLE or Bluetooth Classic. No user interaction. The connection is silent.
Once connected, RACE commands dump the flash. Inside: the Bluetooth Link Key. This 128-bit key is what your phone uses to verify your headphones are trusted.
With the Link Key, the attacker clones your headphones’ Bluetooth identity. Your phone sees “Sony WH-1000XM5” connecting. It trusts it automatically. No pairing popup.
→ Get your phone number using HFP commands → Access contacts and call history → Trigger Siri or Google Assistant → Accept incoming calls silently → Make outgoing calls to premium numbers → Activate your phone’s microphone and listen
At 39C3 the researchers demonstrated WhatsApp and Amazon account takeover. Live.
Confirmed vulnerable
Sony WH-1000XM4, WH-1000XM5, WH-1000XM6, WF-1000XM5, LinkBuds S Bose QuietComfort Earbuds Marshall Major V, Minor IV, Acton III, Stanmore III JBL Live Buds 3, Endurance Race 2 Jabra Elite 8 Active (patched) Beyerdynamic Amiron 300 Teufel Tatws2 JLab Epic Air Sport ANC
Not the complete list. Airoha chips are in hundreds of products. Some manufacturers do not even know they use Airoha because they outsourced the Bluetooth module.
NOT vulnerable: Apple AirPods.
→ Airoha released a fix to manufacturers June 4, 2025. Six months later, most devices still run vulnerable firmware. → Jabra acknowledged the CVEs. Marshall quietly patched. Sony did not respond until they heard about the public disclosure.
Firmware updates come through manufacturer apps. Most users never open these apps after setup. Patches exist but are not reaching devices.
→ Update firmware through your manufacturer’s app → Remove old Bluetooth pairings from your phone → Disable Bluetooth when not in use → High-value targets: use wired headphones
Hacking is not a hobby but a way of life!
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.