Best Operating System for Ethical Hacking and Pentesting

Linux is an extremely popular operating system for hackers. First of all, Linux’s source code is freely available because it is an open-source Operating System (OS). This means that Linux is very easy to modify and customize. Second, there are countless Linux security distros available.
It is extremely important to develop your Linux skills to become an “Ethical Hacker”. Nearly all the tools that hackers use are developed for Linux. Linux gives us capabilities that we don’t have using Windows.
DISTROTEST
If you want to test a different kind of Linux distros without having to install it on your PC, or if you don’t know how to use Linux, DistroTest can be very useful.
DistroTest allows you to test a new Linux operating system, streaming the operating system right to your web browser.
There are large numbers of operating systems available, which you can test directly online without required to install or set up anything on your machine. There are no restrictions made on the usage of the operating system. You can use all functions of the system, Uninstall and install software, test installed programs and even delete or format the hard disk or system files.
They currently have around 250 different Linux distros to choose from. You can use this system for an hour for free. You can test the live OS, install applications, remove applications, delete or modify system files, and test a configuration or script. After every shutdown, the machine will revert to the default settings.
Once you’re done, go back to the DistroTest page and stop your test system. If you don’t want to enable the pop-ups in the DistroTest page, just use any locally installed VNC client applications in your system. The VNC client login details are given on the same page itself.
For more information or to have a try, I recommended to visit the direct DistroTest website and have a look at all the options available to you.
OSBOXES
Free Unix/Linux Virtual machines for VMWare and VirtualBox.
If you want to try out Linux versions easily on your own VMWare or VirtualBox than OSBoxes offers ready-to-use Unix/Linux guest operating systems for both architectures 32bit and 64bit for free.
All images for VirtualBox and VMware have the same username and password. After logging in to a virtual machine that you’ve downloaded from OSBoxes you will be able to change the ‘username’ and the ‘password’ or either create a new user if you want.
For Default user account
- Username: osboxes
- Password: osboxes.org
For Root user account
- Username: root
- Password: osboxes.org
Don’t worry, you can also find the login details on the download page OSBoxes for every respective Virtual Machine. Cool, isn’t? Just download the VM that you like and play with it.
However, I would like to make a comment on this
In my opinion, it is very easy to get a ready-to-use Linux/Unix guest operating systems for VMWare and/or VirtualBox. But I would never choose this myself because I don’t know what “they” have added to these “ready-to-use guest operating systems”. Maybe a bit of paranoia from my parts, but you have to think about it, especially if you do this kind of work. I myself choose at all times to download the legitimate ISO from the Linux distro in question directly from the official website or repository. So you know for sure that it is good, and especially that there is nothing added to this. Anyhow, I leave the choice to you.
IMPROVE YOUR LINUX SKILLS
If you need to improve your Linux skills, or if you’re a beginner and just getting started with Linux OS, I recommend you to have a look in the best Linux commands hacks and other cool tricks for beginners article that I wrote.

MAKE YOUR OWN PEN-TESTING DISTRO
How great would be to install a Debian, Ubuntu, Arch or any other Linux distro and then decide for yourself what tools to have, or conversely what are the tools that you will never use and that take up unnecessary space on your hard disk you do not want to have? Soon you will read more about this. Anyway, I deviate a bit again …
LEARN NEW THINGS
I tested all the Linux distros mentioned here, of course, because I like doing this, but also because I want to know what I am talking about. It is actually recommended for everyone to try out several types of Linux distributions. First, you can find out what works best for you, without having to rely on the opinion of others since tastes vary a lot.
Secondly, you learn a lot from this, If you are used to Kali Linux, try a BlackArch, or if you have tried Network Security Toolkit (NST), then switch to for example ParrotSec, you will see that quite a lot differences and the great thing about this are that you learn a lot.
Thirdly and finally… It’s just fun !!
HERE ARE SOME OF THE BEST LINUX SECURITY DISTROS IN A “RANDOM” ORDER.
PARROT SECURITY
Discover Parrot Security and get the most from an awesome Debian-based platform. Professional tools for security testing, software development and privacy defense, all in one place.
Parrot is a GNU/Linux distribution based on Debian Testing and designed with Security, Development, and Privacy in mind. It includes a full portable laboratory for security and digital forensics experts, but it also includes all you need to develop your own software or protect your privacy while surfing the net.
Always updated, frequently released and fully sandboxed! Everything is under your complete control. Parrot OS is a lightweight Linux distro — runs over machines that have a minimum of 265Mb of RAM.
Homepage | Download Security Edition
Video Parrot Security OS 4.10
KALI LINUX
One of the well-known and favorite ethical hacking operating systems used by hackers and security professionals is Kali Linux. Kali is a Debian-based Linux distribution designed for hackers or digital forensics and penetration testing. It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of BackTrack, their previous forensics Linux distribution based on Ubuntu. Kali Linux has over 600 preinstalled penetration-testing programs.
Apart from desktop support, Kali Linux also has a dedicated project set-aside for compatibility and porting to specific Android devices, called Kali Linux NetHunter. When comes to security tools, this top ethical hacking operating system is equipped with 600+ preinstalled pen testing tools and they are frequently updated and are offered for different platforms like ARM and VMware. Now Kali Linux is based on a rolling release model
Homepage | Download Kali Linux
Video Kali Linux 2021.1
BLACKARCH
BlackArch Linux is an Arch Linux-based penetration testing distribution for penetration testers and security researchers. The repository contains 2347 tools. You can install tools individually or in groups. BlackArch Linux is compatible with existing Arch installs.
Black Arch is similar to usage to both Parrot OS and Kali Linux when fully installed. A critical difference between the other distributions and BlackArch however, is that BlackArch does not provide a desktop environment but provides a Window Managers preconfigured.
Homepage | Download BlackArch | Getting Started
Video BlackArch
LINUX KODACHI
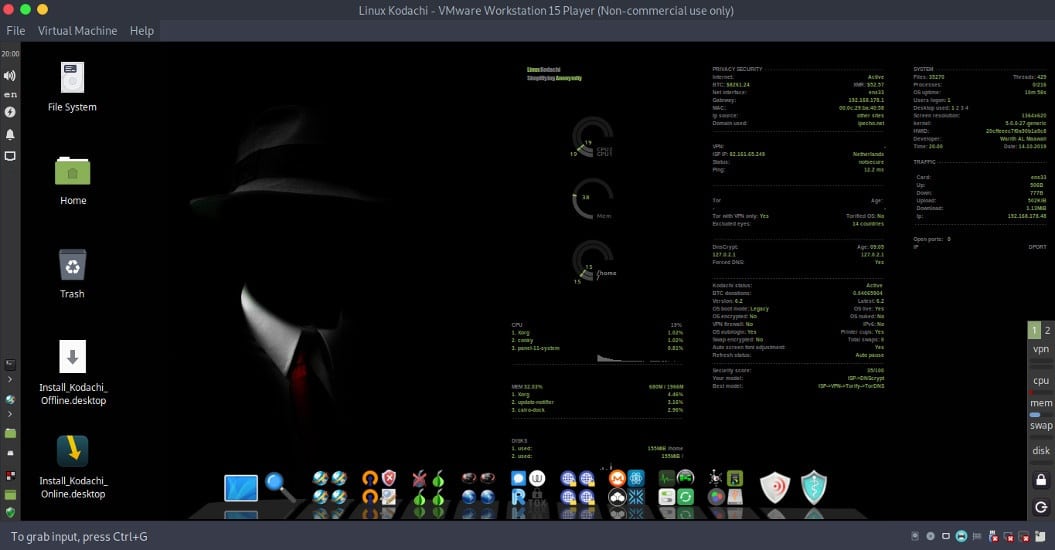
Linux Kodachi is a Debian-based distribution that can be run from a DVD or USB thumb drive. The distribution filters all network traffic through a VPN and the Tor network, obscuring the user’s network location. The distribution attempts to clean up after itself, removing traces of its use from the computer.
Kodachi is a live operating system that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity and helps you to:
- Use the Internet anonymously.
- All connections to the Internet are forced to go through the VPN then Tor network with DNS encryption.
- Leave no trace on the computer you are using unless you ask it explicitly.
- Use state-of-the-art cryptographic and privacy tools to encrypt your files, emails and instant messaging.
- Kodachi is based on the solid Linux Xubuntu/Debian with customized XFCE this makes Kodachi stable, secure, and unique.
Homepage | Download from Sourceforge | Alternative Download
BUGTRAQ
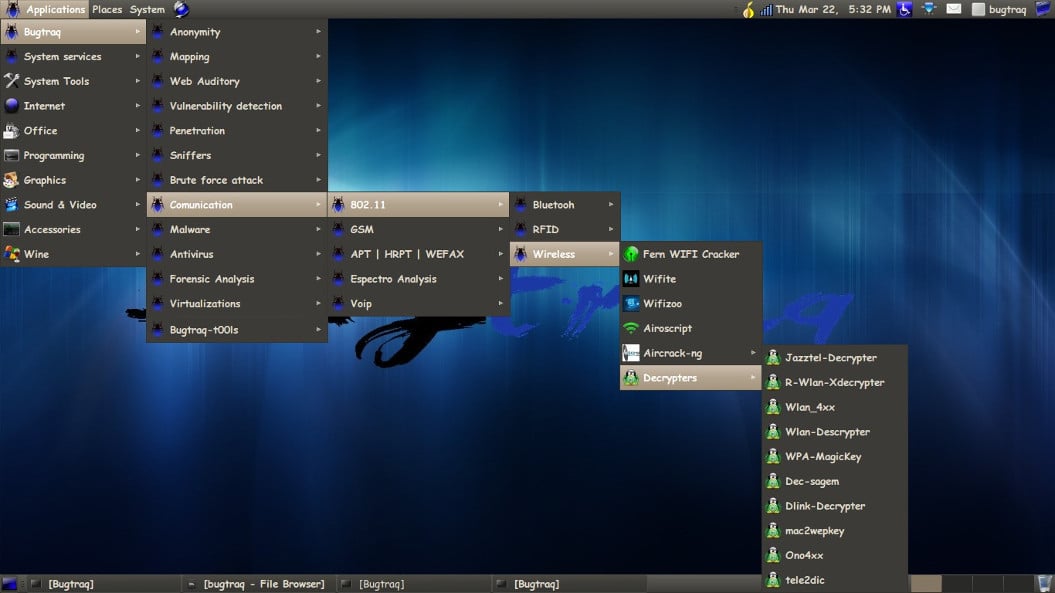
Bugtraq professional penetration testing distro designed for Penetration Testing Operations and Reverse Engineering and Malware Analysis Missions. Based on Debian, it contains a lot of hacking tools. Developed by Bugtraq-Team, the first release was in 2012.
Bugtraq system offers the most comprehensive, optimal, and stable with automated services manager in real-time distribution. You can install our distribution from a Live DVD or USB drive. Depending on your desktop environment, the features vary. The minimum requirements are based on XFCE and KDE. 1GHz x86 processor & 512 MB of system memory 15 GB of disk space for installation.
One of the novelties of Bugtraq is its wide range of tools in different branches. We can find mobile forensic tools, malware testing laboratories, tools of the Bugtraq-Community, audit tools for GSM, wireless, Bluetooth and RFID, integrated Windows tools, tools focused on ipv6, and typical pentesting and forensics tools that should not miss in Bugtraq-II.
BACKBOX
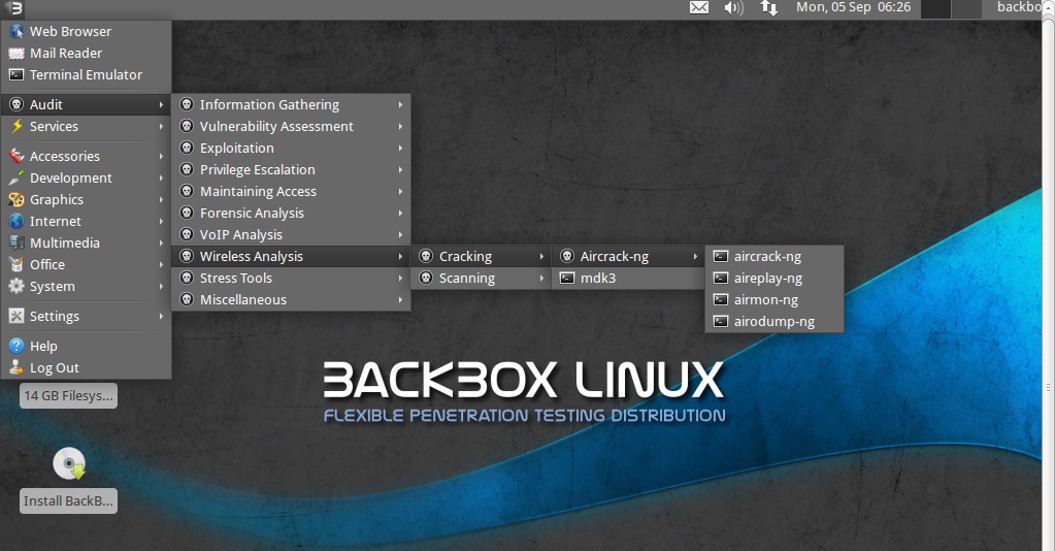
BackBox is an Ubuntu-based penetration testing Linux distribution. It provides penetration test and security assessment oriented providing a network and informatics systems analysis toolkit along with a complete set of other tools required for ethical hacking and security testing.
It includes some of the most used security and analysis Linux tools to help out security experts from stress tests to sniffing including vulnerability assessment, computer forensic analysis, and exploitation.
BackBox has its own software repository providing the latest stable versions of various system & network analysis toolkits and the best known ethical hacking tools. It is designed with minimalism in mind and uses the XFCE desktop environment. It’s a fast, effective, customizable and complete experience. It also has a very helpful community behind it.
Homepage | Download Backbox | Documentation
NETWORK SECURITY TOOLKIT
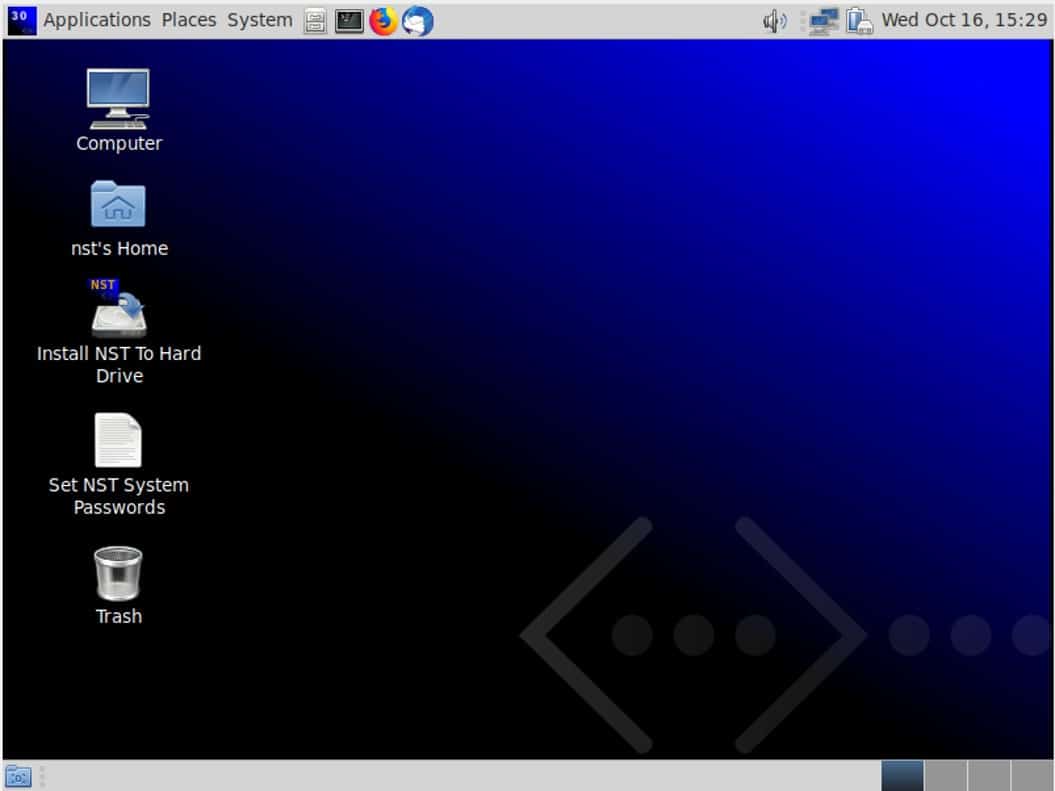
Network Security Toolkit (NST) is a Fedora-based Linux distro “Network Security Toolkit”. This bootable live CD is created to give you a right to use the best open-source network security applications for pen testing purposes. This easy-to-use hacking distro easily converts the x86 systems into an ethical hacking machine that is helpful in intrusion detection, network traffic sniffing, network packet generation, network/host scanning, etc.
The main intent of developing this toolkit was to provide the security professional and network administrator with a comprehensive set of Open Source Network Security Tools. The majority of tools published in the article: Top 125 Security Tools by INSECURE.ORG are available in the toolkit. An advanced Web User Interface (WUI) is provided for system/network administration, navigation, automation, network monitoring, host geolocation, network analysis and configuration of many network and security applications found within the NST distribution. In the virtual world, NST can be used as a network security analysis validation and monitoring tool on enterprise virtual servers hosting virtual machines.
Homepage | Download NST | Wiki
CAINE

Caine Security-focused distro Caine “Computer Forensics Linux Live Distro” is an Ubuntu-based operating system that is available as a live disk. It stands for Computer-Aided Investigation Environment. This Linux distro comes with a wide range of tools to help you in computer forensics. Caine comes with various numbers of databases, memory, forensics, and network analysis applications.
Caine offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface. The main design objectives that Caine aims to guarantee are the following:
- An interoperable environment that supports the digital investigator during the four phases of the digital investigation
- A user-friendly graphical interface
- A semi-automated compilation of the final report
Homepage | Download Caine Live
HONEYDRIVE

How great it is to set up your own honeypot, for that HoneyDrive3 is a great choice as a start. HoneyDrive is the premier honeypot Linux distro. It is a virtual appliance (OVA) with Xubuntu Desktop 12.04.4 LTS edition installed.
It contains over 10 pre-installed and pre-configured honeypots software packages such as Kippo SSH honeypot, Dionaea and Amun malware honeypots, Honeyd low-interaction honeypot, Glastopf web honeypot, and Wordpot, Conpot SCADA/ICS honeypot, Thug and PhoneyC honey clients and more.
Additionally, it includes many useful pre-configured scripts and utilities to analyze, visualize and process the data it can capture, such as Kippo-Graph, Honeyd-Viz, DionaeaFR, an ELK stack and much more. Lastly, almost 90 well-known malware analysis, forensics, and network monitoring related tools are also present in the distribution.
DISTROWATCH
Are you curious and want to try out more different Linux, then take a look at distrowatch.com website.
DistroWatch is a website that provides news, popularity rankings, and other general information about various Linux distributions as well as other free software/open-source Unix-like operating systems such as OpenSolaris, MINIX and BSD. It now contains information on several hundred distributions.
Look what Linux distributions are the most popular distrowatch.
Other Articles I wrote about this subject
I wrote an article on the BullsEye website. This is about how I got started with Linux myself. and why it is not always necessary to have a “Hacking distribution” This might be fun to read too
I don’t care what Linux distribution you use
Another article, also on BullsEye, is about how you can easily turn a “regular” Linux into a “hacking” distribution. At the time of writing - renewing this article, September 2020 - I use this myself as the main Operating System
Install Anarchy Linux for penetration testing and Ethical Hacking
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.