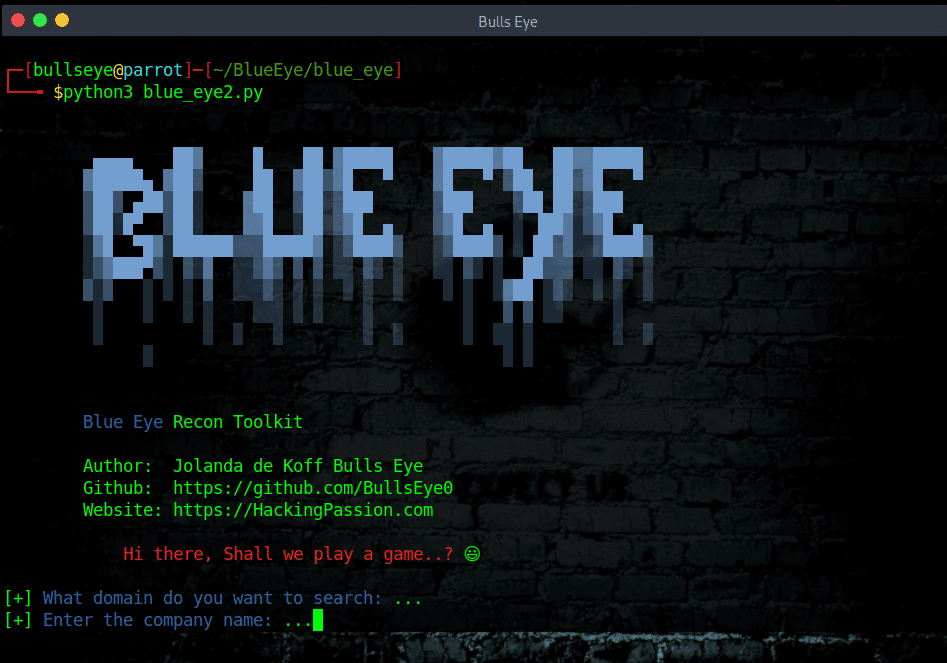
Blue Eye a Python Recon Toolkit
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Blue Eye is a Recon Toolkit script I made in python3. Blue Eye shows the subdomain resolves to the IP addresses, ports and headers, company email addresses and much more ..!
The Blue Eye script shows the:
- Subdomain resolves to the IP addresses
- Open Ports
- HTTP Header
- Mail Servers
- DNS Text Records
- Nameserver Records
- Sites of interest “email, okta, webmail and slack”
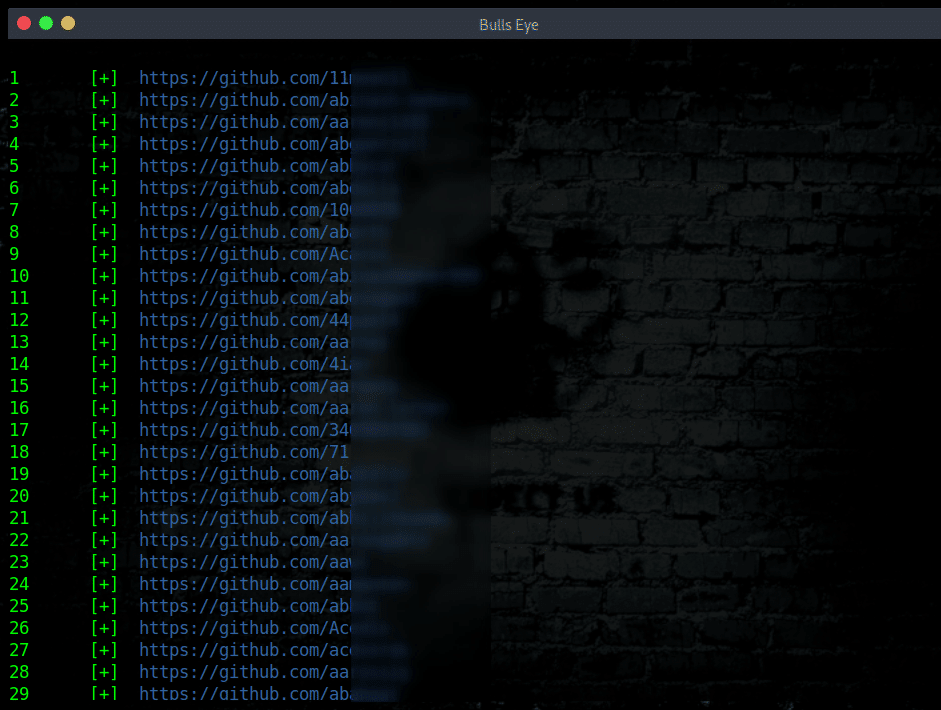
- Lists of GitHub user pages
- List of possible company email addresses harvested from GitHub user pages and from DuckDuckGo and Linkedin searches
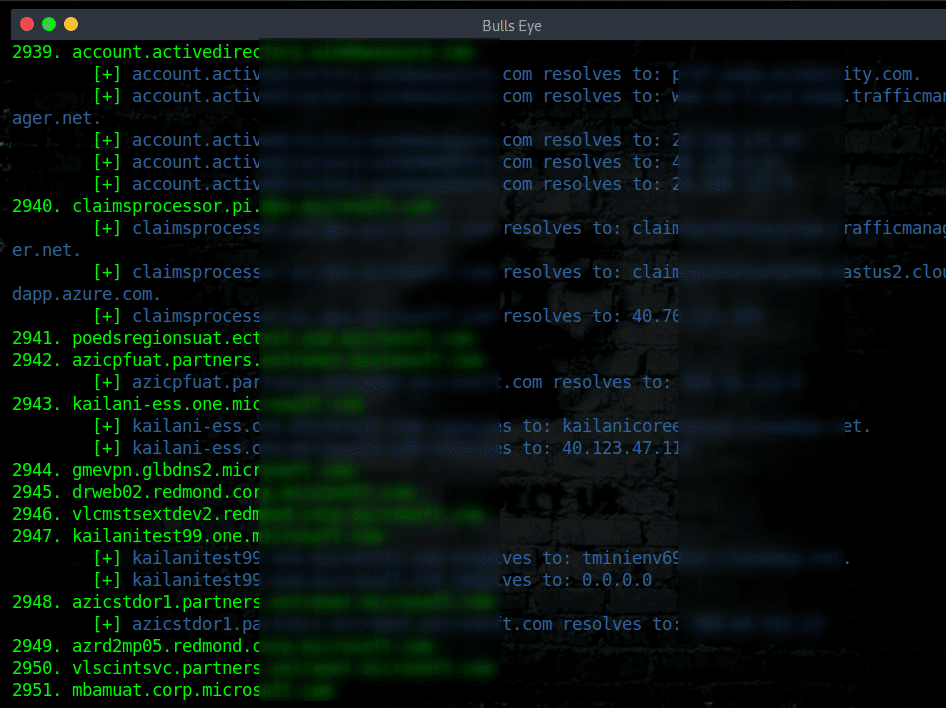
The Subdomain resolves to the IP addresses.
Discovering subdomains or a domain is an essential part of hacking reconnaissance. However, having an unsecured subdomain can lead to a major serious risk. Because subdomain takeover attacks are a class of security issues where an attacker is able to seize control of an organization’s subdomain, which leads to an account takeover and much more.
It’s very useful to know an IP address of a subdomain, without having to do a lot of complicated work and to first go to ping all the subdomain names. Therefore I made Blue Eye
In another article, I will talk about the subdomain takeover and how to implement it. How to test and also to avoid them.
Mail Servers:
Mail servers can provide a wealth of information for hackers and penetration testers. Every email that is sent passes through a series of mail servers along its way to its recipient.
DNS Text Records:
The “text” record lets a domain administrator enter text into the DNS record, as it was originally intended as a place for human-readable notes. These records are used for various purposes. One example is ownership validation: To prove you own the domain, a provider may require you to add a TXT record with a particular value to your domain.
Nameserver Records:
This record indicates which DNS server is authoritative for that domain (which server contains the actual DNS records). Because a domain will often have multiple NS records which can indicate primary and backup name servers for that domain. NS stands for “Name Server”
Video about Blue Eye on YouTube:
Blue Eye a python Recon Toolkit script Upgrade
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
Install Blue Eye on Linux:
| |
| |
| |
Use:
| |
Here you can find the GitHub page:
Blue Eye a python Recon Toolkit script
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.