Malicious Chrome Extensions Steal ChatGPT Conversations from 900,000 Users
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
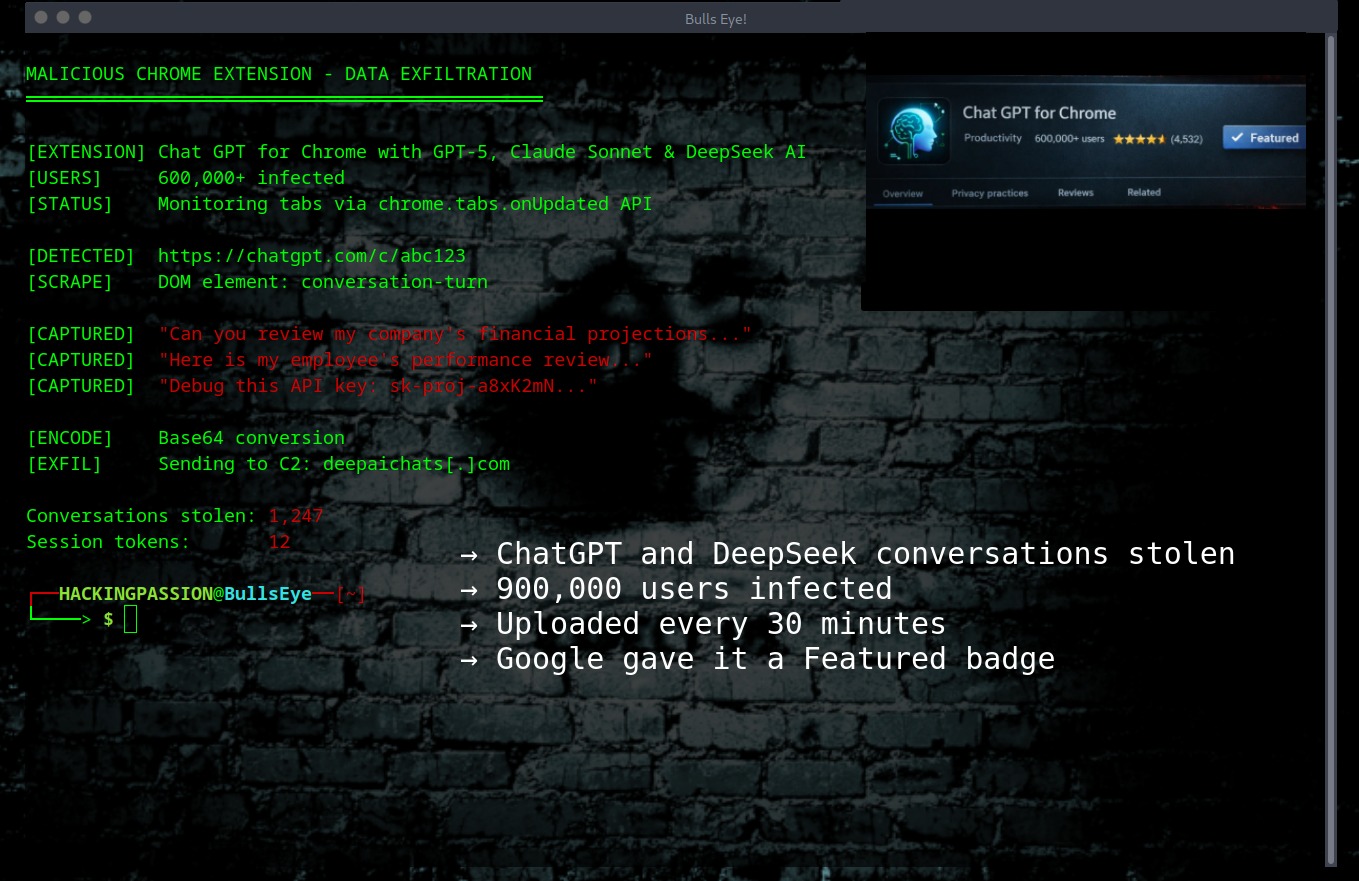
Two Chrome extensions. 900,000 users. Every ChatGPT and DeepSeek conversation stolen. Sent to attacker servers every 30 minutes. Google gave one of them a Featured badge. The extensions are still live in the Chrome Web Store right now. 🤔
This is the third major case in three weeks. First the sleeper extensions that waited 7 years before activating. Then Urban VPN selling 8 million users’ AI chats to data brokers. Now this. Security researchers have a name for it: “Prompt Poaching.” And it’s becoming a gold rush.
The extensions are called “Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI” with 600,000 users and “AI Sidebar with Deepseek, ChatGPT, Claude and more” with 300,000 users.
Here’s how they work.
When you install the extension, it asks for permission to collect “anonymous, non-identifiable analytics data.” Sounds harmless. What it actually collects is everything.
The attackers copied a legitimate extension called AITOPIA that has over 1 million users. They built the same interface with the same features and the same look. Users see a helpful AI sidebar. What they don’t see is malware running in the background.
The copy goes deep. The fake extensions even mention AITOPIA in their privacy policies. Anyone trying to check if it’s real finds what looks like a legitimate company.
To hide their tracks, the attackers host their privacy policy pages on Lovable, an AI-powered website builder. There’s no company address and nothing to trace back to them.
Every 30 minutes, the extensions send everything to attacker servers: → Complete ChatGPT and DeepSeek conversations → Every URL from all open tabs → Search queries → Session tokens and authentication data → Internal corporate URLs
The data goes to deepaichats[.]com and chatsaigpt[.]com, where it’s Base64 encoded before transmission. You won’t notice anything.
The technical execution: → Extensions monitor tabs using chrome.tabs.onUpdated API → When ChatGPT or DeepSeek URLs are detected, DOM scraping begins → Every prompt and response gets grabbed as you type → Data is cached locally, then batch-uploaded to C2 servers
One extension had Google’s Featured badge until researchers went public. That badge means a human at Google reviewed it and approved it.
Here’s the nasty part. Uninstall one extension and it automatically opens a new tab pushing you to install the other one. Remove that one and the cycle repeats.
The bigger picture.
It’s not just criminals doing this anymore. Legitimate companies are collecting AI conversations too.
Similarweb, a web analytics company with over 1 million extension users, quietly added AI chat monitoring in May 2025. On January 1, 2026, they updated their terms. Now it says they collect “prompts, queries, content, uploaded files and other inputs that you may enter or submit to AI tools.”
They’re not hiding it. They’re monetizing it. Your AI conversations are being packaged and sold to advertisers, data brokers, and whoever else is willing to pay.
Researchers are calling it “Prompt Poaching.” Browser extensions are the new data goldmine.
Think about what people share with ChatGPT: → Source code and development questions → Business strategies and planning → Personal information during support chats → Confidential research and legal matters → Internal company communications
All of that is now a product being bought and sold.
Check your extensions now.
Go to chrome://extensions/ and look for: → Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI → AI Sidebar with Deepseek, ChatGPT, Claude and more
Extension IDs to search for: → fnmihdojmnkclgjpcoonokmkhjpjechg → inhcgfpbfdjbjogdfjbclgolkmhnooop
If you find them, remove them immediately.
For ANY AI-related extension, ask yourself: does this need access to all my browser data? Most sidebar tools don’t need those permissions to function.
Fewer extensions means smaller attack surface.
This is social engineering at scale. Attackers don’t need to trick you into clicking a phishing link when they can trick you into installing an extension that looks exactly like a legitimate tool with a million users.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.