Clear Your Tracks on Linux
Clear Your Tracks on Linux
In this article and video, I show you how to clear your tracks in Linux. This is very important if you are a penetration tester, an ethical hacker, or a cyber security expert.
Clear Your Tracks The Final Step
It is one of the biggest mistakes an attacker makes to let a track behind.
If you see the biggest attacks in the past years, most of the detection was made really easy from the malware that the black hat hacker(s) have left, which they didn’t clear. Many of the “best hackers” got caught this way.
If you are an attacker your first have to clear your logs, modify your registry, or clear the registry you did create. And at the last remove any files or commands that you have been using. “Clearing Your Tracks” is really underestimated in my opinion.
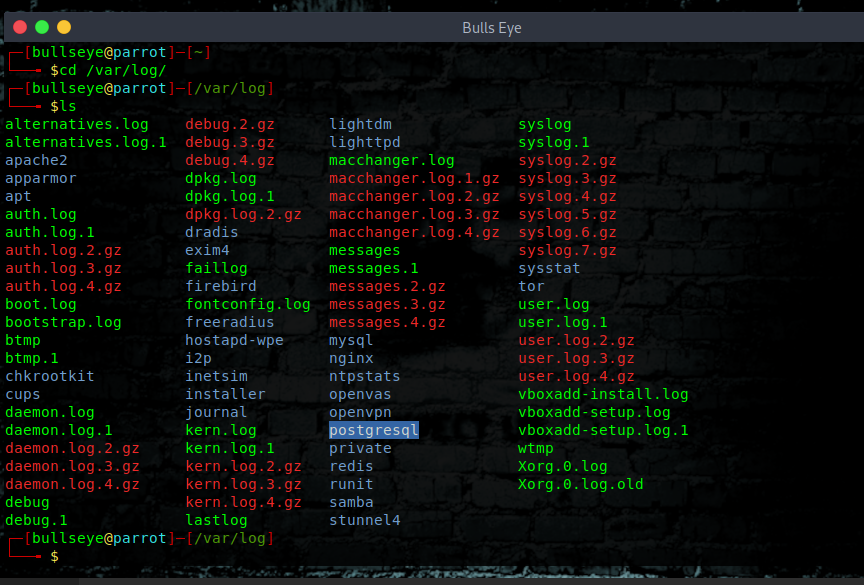
cd /var/log
As you can see below, when we open the cd /var/log they’re a lot of logs. It is pretty self-explanatory as you can guess it from the names
these log having various use cases like there is a user log, a mack changer log, an authentication log, and kernel log as well with is always interesting.
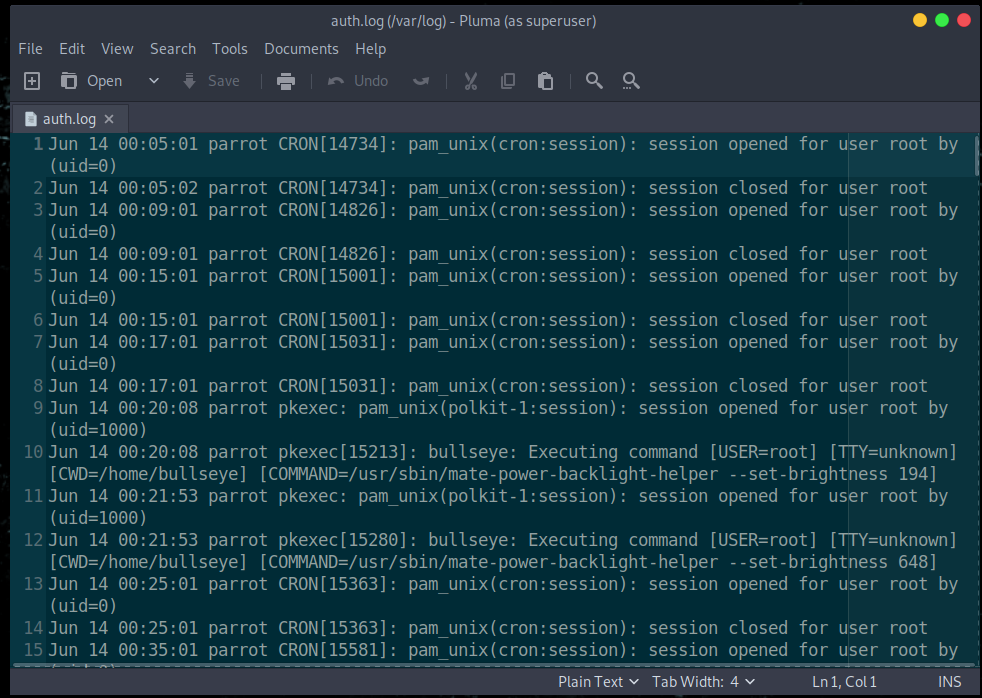
auth.log
The authentication log with stores all the auth.log, which is very important to a forensic team, they can analyze what was happen, and what activities are done. You can of course use any text editor. like vim, nano, pluma, or any other you like.
|
|
kern.log
Another log you can use to view kernel information is the /var/log/kern.log file, this logs the kernel information and events on your system, it also logs dmesg output.
|
|
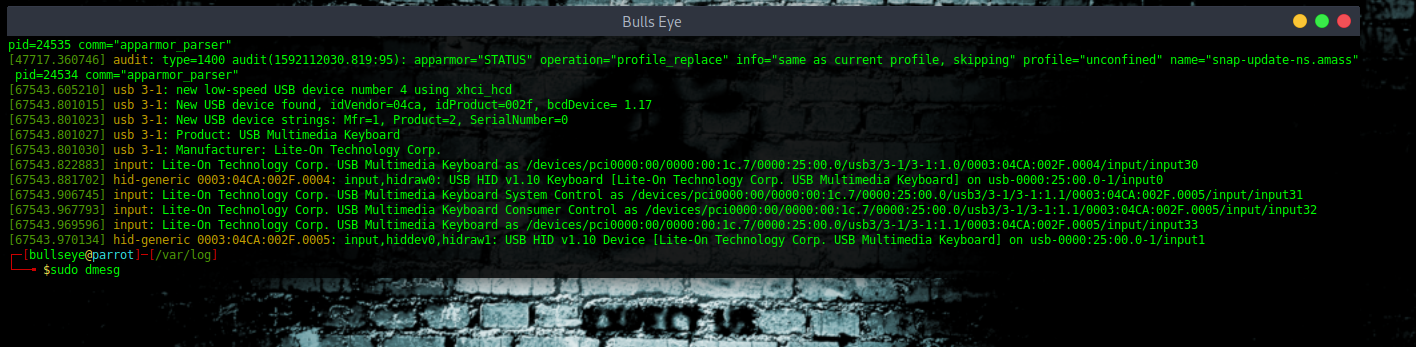
You can see what’s going on. I will not explain right now, because this can be another topic for another time. But I think you will get the idea.
Clear Your Tracks with Shred
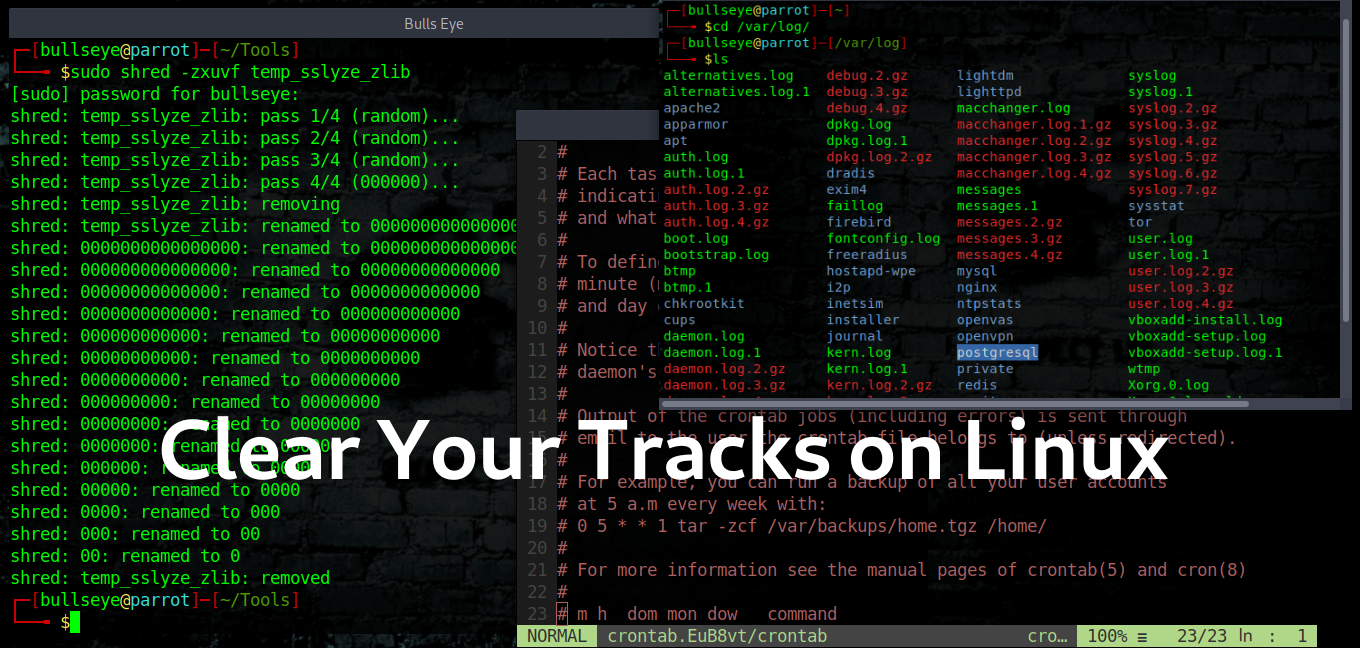
Shred is an amazing tool and for sure one of my favorites..! What shred does, it removes all logs permanently.
But why don’t we just simply delete all those files, because all the deleted files can be recovered, and deleting them with shred it actually wipes them permanently
Shred actually renames the file, and changes it to 0’s so many times, and at the end removes it completely.
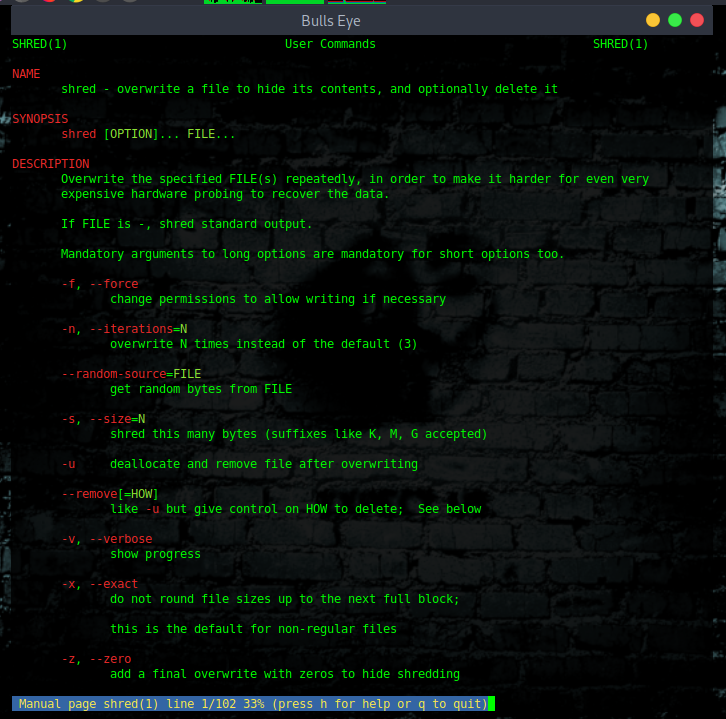
Now explored the help menu of shred
It is all self explain.. you also may like to have a look at the man page of shred.
|
|
|
|
Now let’s remove a file and clear your tracks
|
|
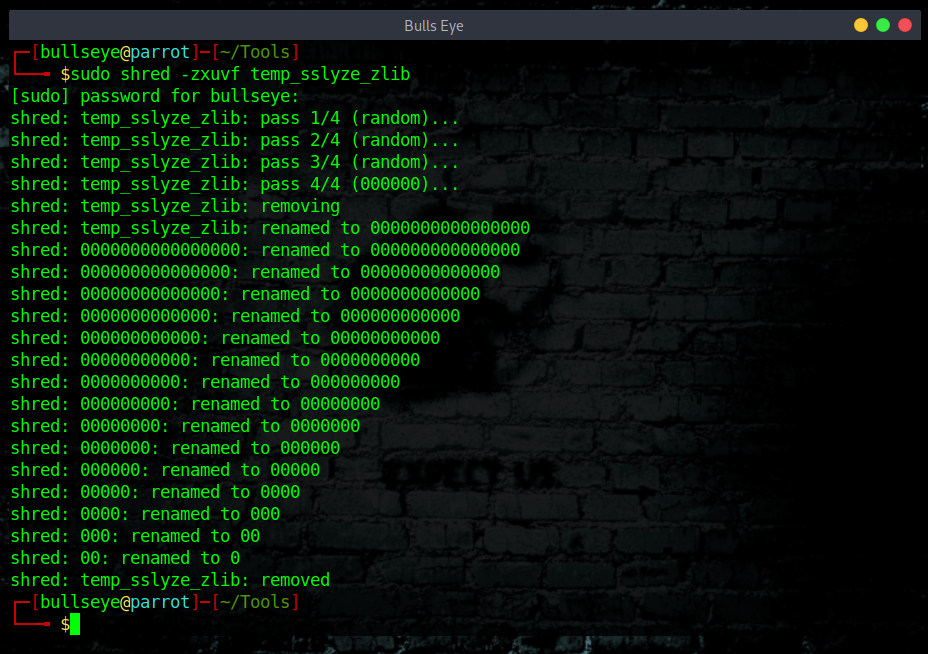
The command (Explanation) I used for this ::
|
|
As you can see it has renamed it so many times 0 and finally removed it.
This can not be recovered.
Apart from that, your bash history is also very important. Even a normal Linux user can guess what someone has done looking at the file, so make sure you delete that as well. You can delete that with shred also but I am not going to do it with shred this time.
Once again, be aware that all files that are normally removed can be recovered..!
Delete The History And Clear Your Tracks
|
|
|
|
Using the redirect for now
|
|

Here we go the history is cleared.
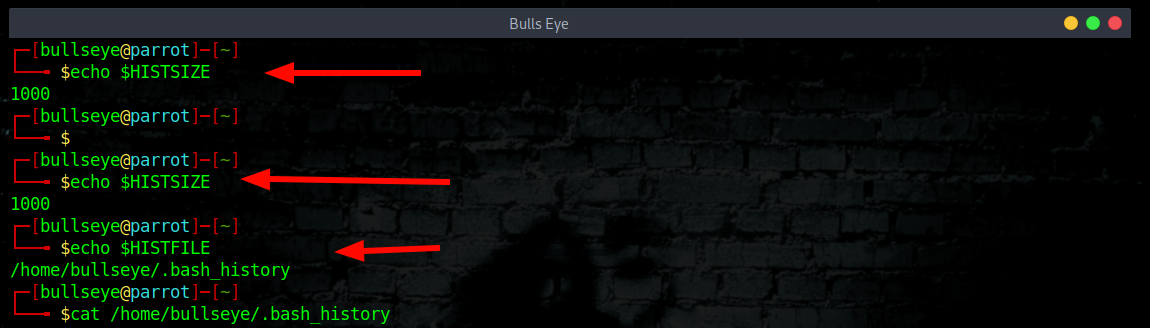
Command history #command-history
All your commands are stored at:
|
|
|
|
You can set your file-size like this to zero, to avoid storing commands.
|
|
If you set it when you get shell you won’t have to worry about cleaning up the history.
Automate the Clearing of (any) File
To automate the process so that the command history is deleted each day. In this way, if we forget to remove our history (I’m sure I will often) :-D , the system will do it at 11:00 p.m. every day, automatically.
First, open the crontab table in edit mode by typing:
|
|
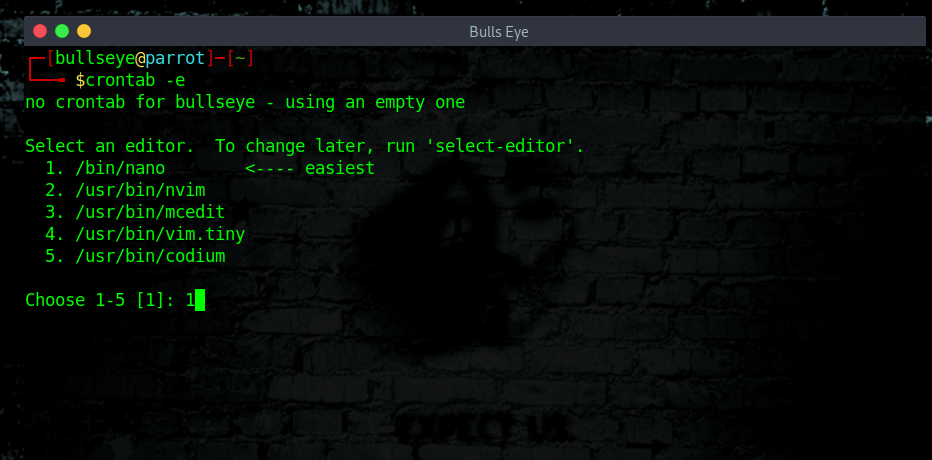
Using the crontab, we can navigate to the end of the file and add the following line.
|
|
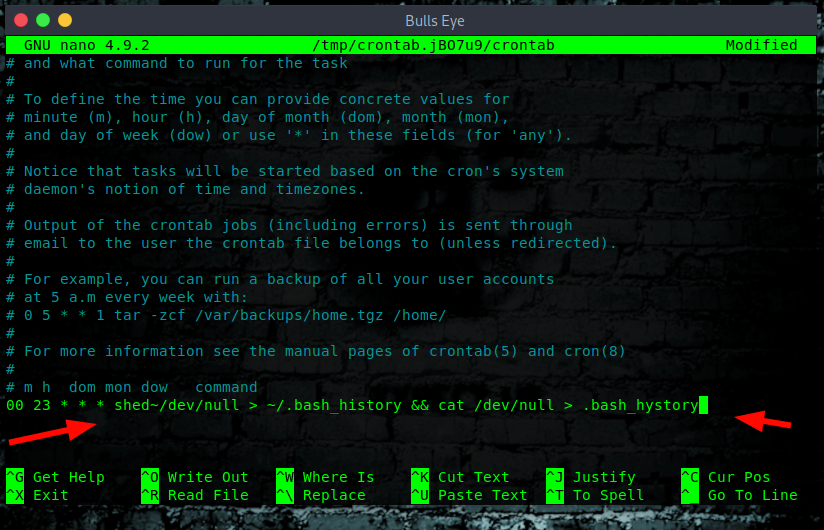
In the article below I describe in more detail about the cronjobs
* https://hackingpassion.com/determine-if-your-linux-computer-or-server-is-hacked/#Crontab_scheduled_jobs
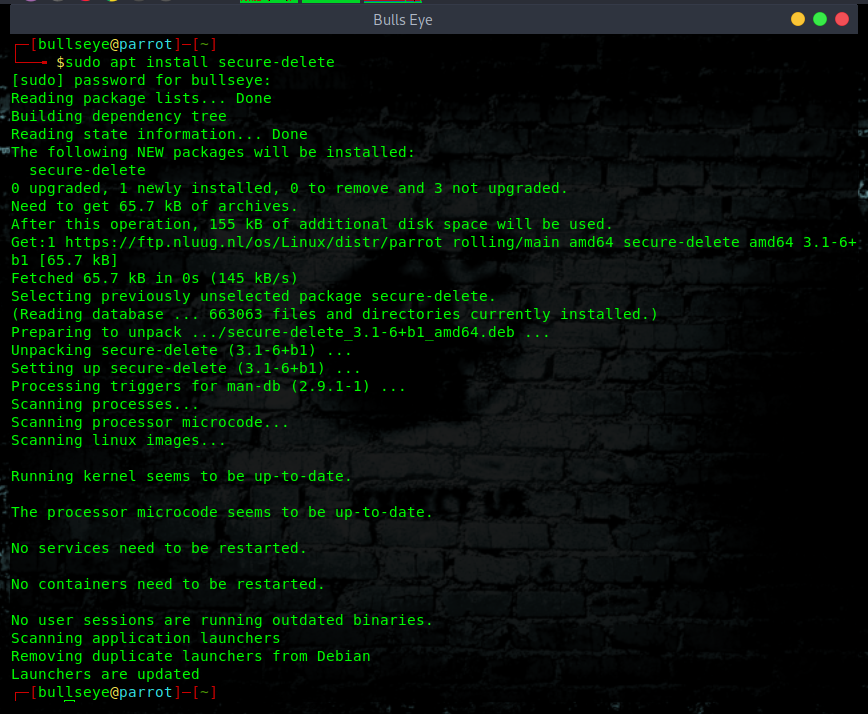
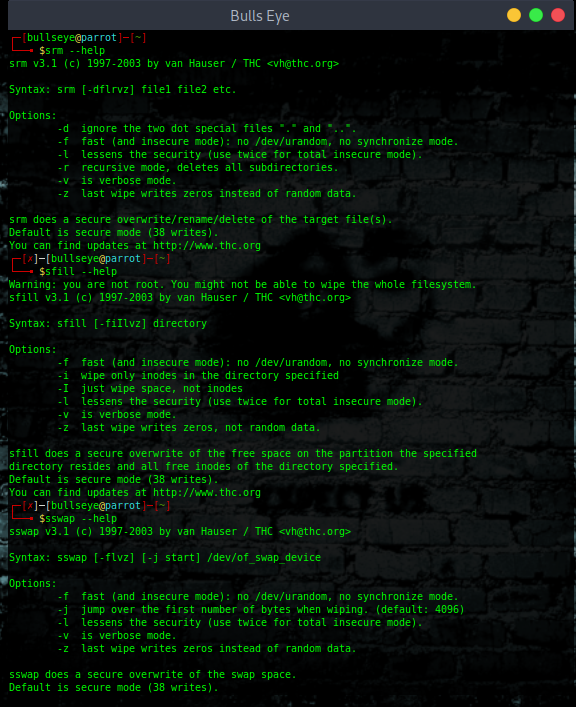
Secure-Delete
Secure-Delete is a set of tools for Linux operating system and they provide advanced techniques for permanent removal of files. Once Secure-Delete has been installed on any Linux system, it provides following four commands:
- srm
- smem
- sfill
- sswap
|
|
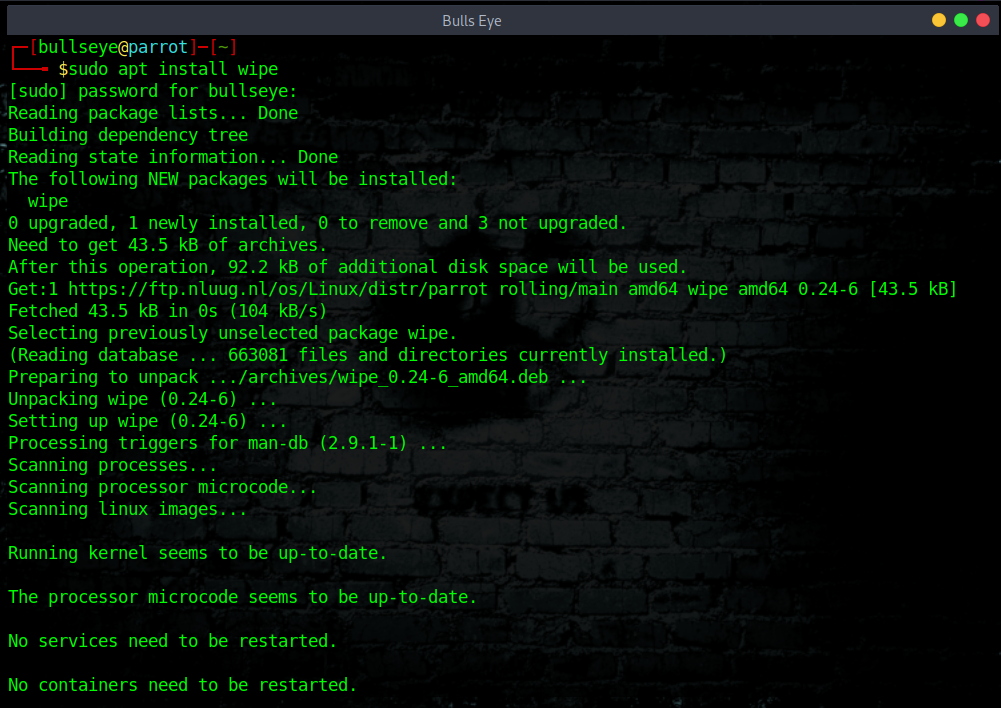
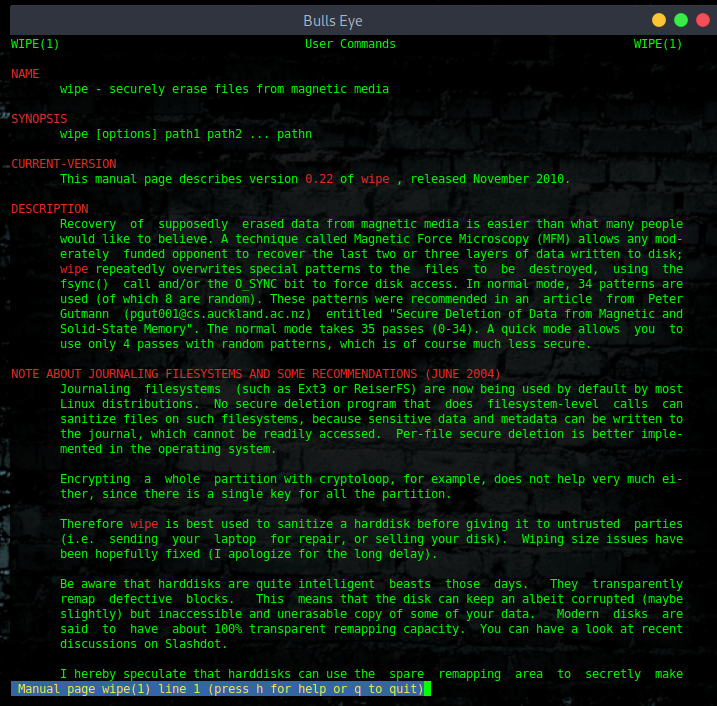
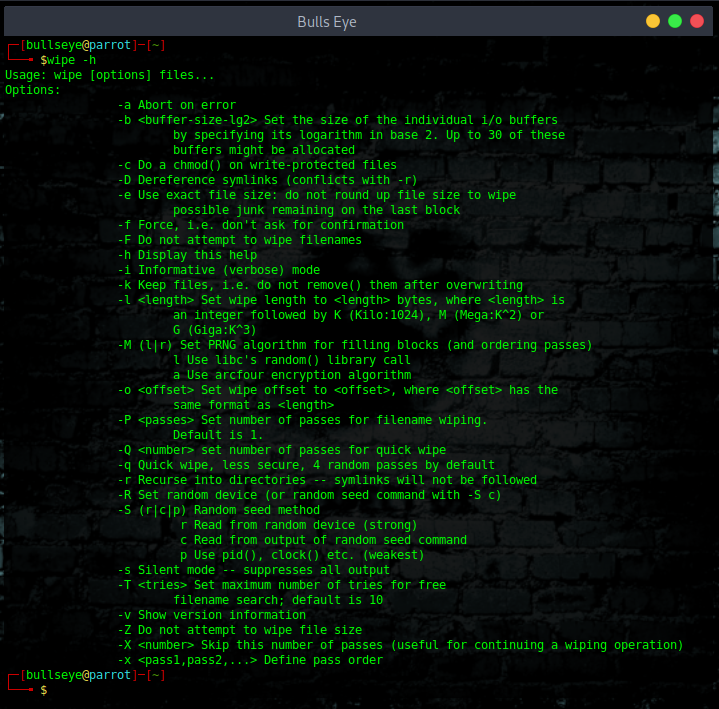
Install Wipe
“Wipe was originally developed to securely erase files from magnetic media. Wipe repeatedly overwrites special patterns to the files to be destroyed, using the fsync() call
and/or the O_SYNC bit to force disk access. In normal mode, 34 patterns are used (of which
8 are random).”
You can remove the contents of a single file, folder, or entire hard disk with this command, but the whole hard disk format using wipe command will take a good amount of time.
|
|
|
|
|
|
Remove any file as:
|
|
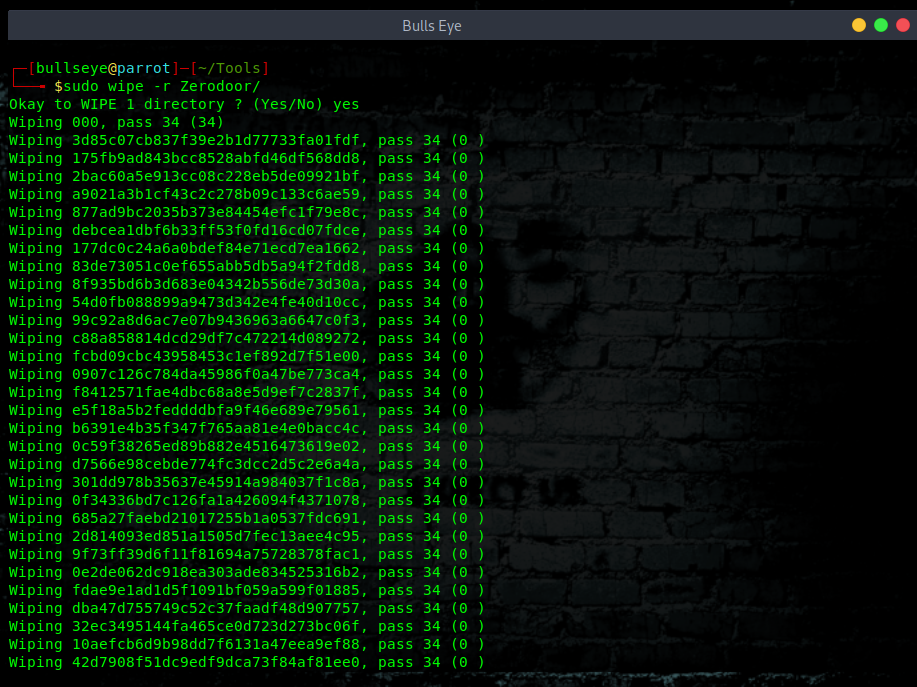
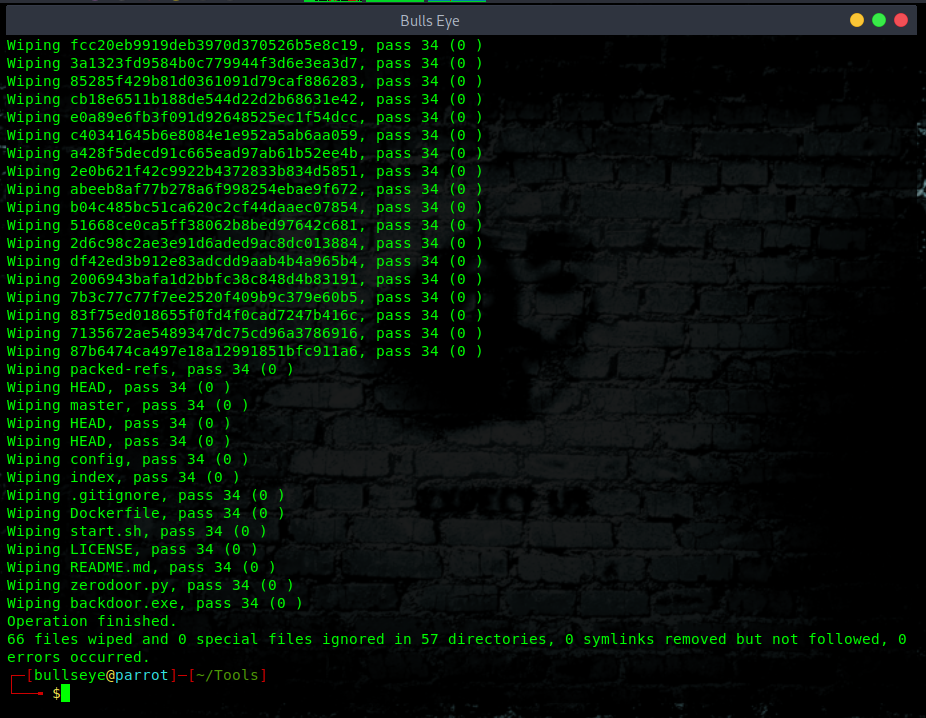
Remove any directory as:
|
|
Some other tricks
Check for hidden files
Are there recent hidden files?
|
|
Check what are the currently open files on the systems.
Currently open and active log files?
|
|
Check what are the recent documents on the systems
Recent documents on the system?
|
|
Don’t forget to remove your Bowser History
Obviously, you should also think about your browser history, your cookies and so many other things. (more about that in another article)
Linux distribution Tails
A good option is to use a Tails for example, which you install on a USB. After shutting down or restarting the system, all downloaded files, browser history, etc. - are deleted.
Clear Your Tracks linux Video
In this video, I show how you give the terminal an attitude. Is this important? No, certainly not, but it is fun.
Then I will show you where to find your all log files, and how to delete them in an easy and good way. I hope you enjoy the video ..! Talking is still a thing :)
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
Clear Your Tracks Conclusion
I hope from now on, you think a little further than the usual “How to hack” Before you start doing anything, you must have already thought in advance ::
"How am I going to make sure I don’t leave any tracks behind"
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.