Cr3dov3r Credential Reuse Attack
Cr3dOv3r This tool checks your credentials on different websites and looks for if your email is in some data leak.
Your best friend in credential reuse attacks.
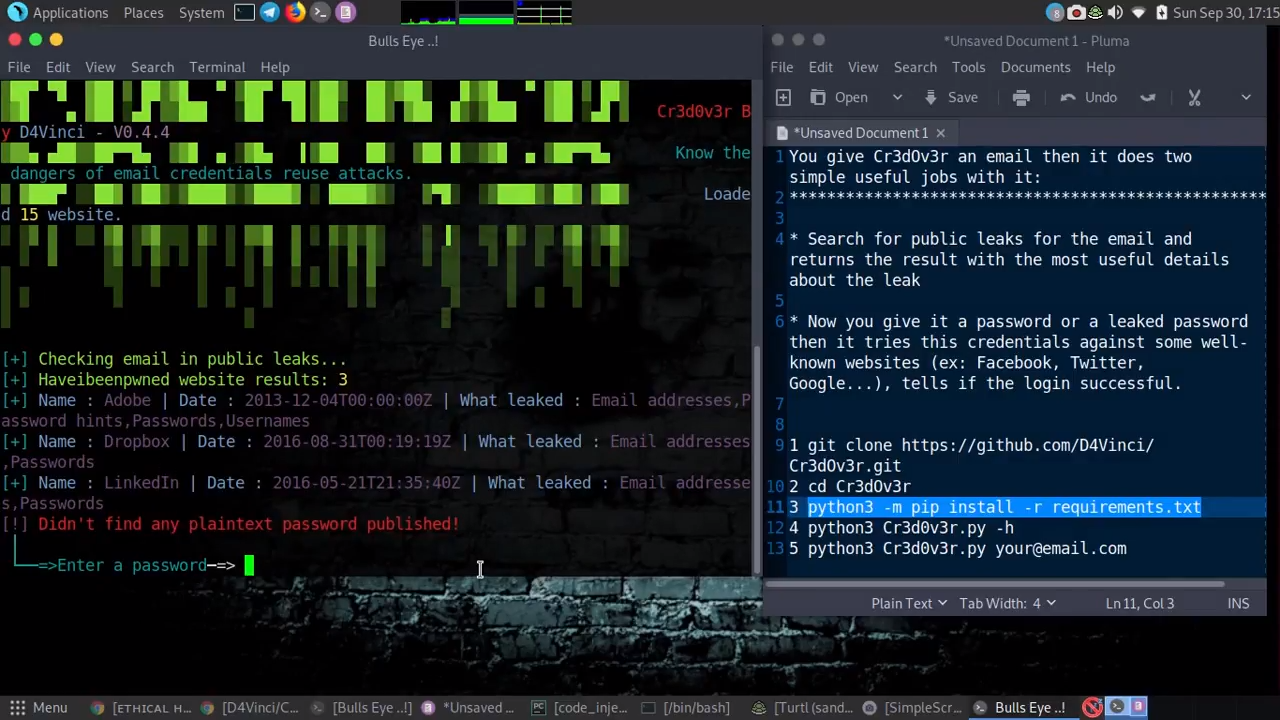
You give Cr3dOv3r an email then it does two simple useful jobs with it:
- Search for reuse attack public leaks for the email and returns the result with the most useful details about the leak
- Now you give it a password or a leaked password then it tries these credentials against some well-known websites (ex: Facebook, Twitter, Google…), tells if the login was successful and if there’s captcha somewhere blocking our way!
Some of the scenarios Cr3dOv3r can be used in it
- Check if the targeted email is in any leaks and then use the leaked password to check it against the websites.
- Check if the target credentials you found are reused on other websites/services.
- Checking if the old password you got from the target/leaks is still used on any website.
Usage
| |
| |
Video Cr3dOv3r
Cr3dOv3r Credential reuse attack
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
Check out Cr3dOv3r here: Github - https://github.com/D4Vinci/Cr3dOv3r
Installing
+For windows : (After downloading ZIP and upzip it)
| |
| |
| |
+For Linux :
| |
| |
| |
| |
+For docker :
| |
| |
| |
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.