Cracking Windows Domain Admin Passwords Just Got Simple
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Cracking Windows domain admin passwords just got simple. A massive set of rainbow tables just went public, a $600 laptop is enough, and it takes 12 hours max. This flaw has existed since 1999. Microsoft ignored it for 25 years. So Google decided to force the conversation. 🔓
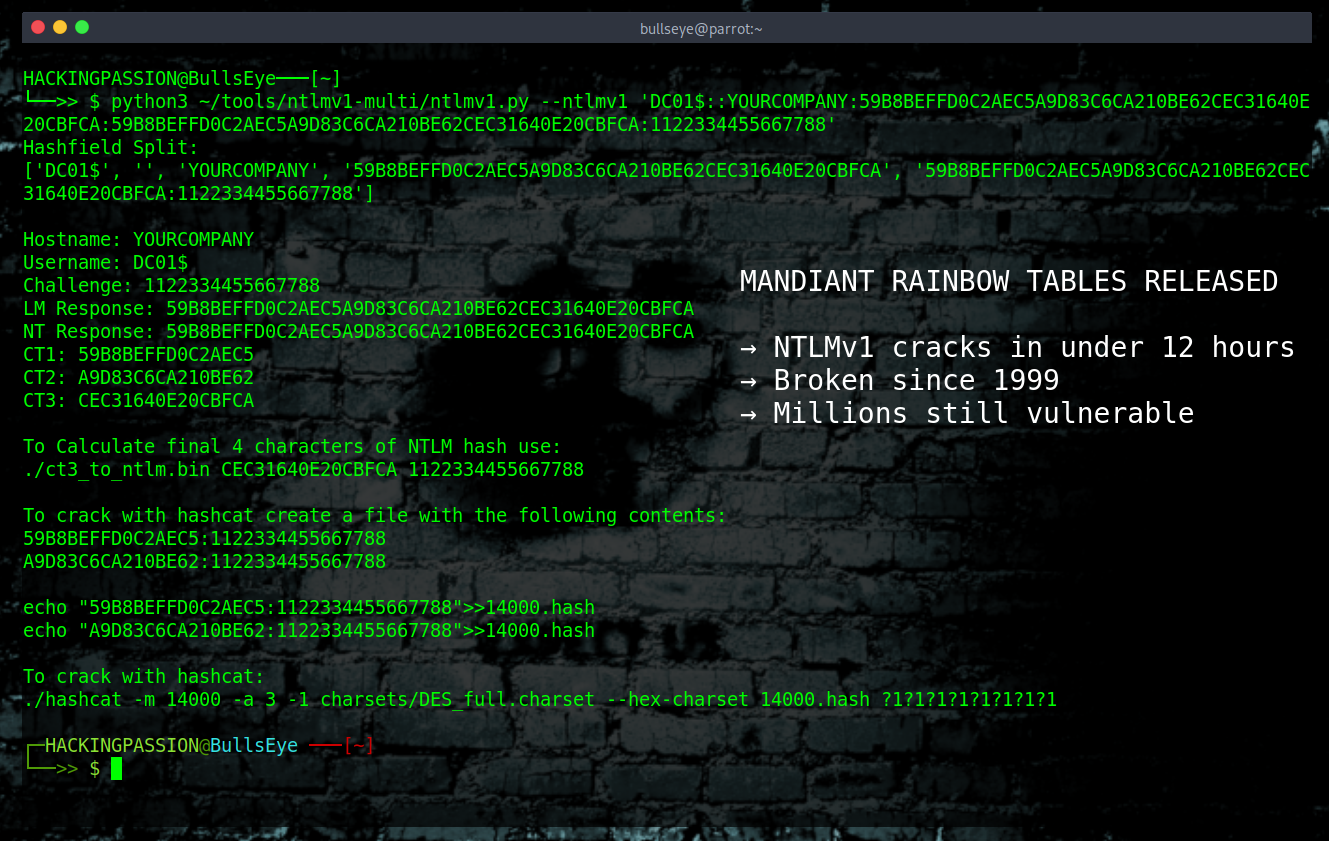
The flaw is in NTLMv1. That’s an authentication protocol from 1993. When a Windows machine logs in over a network, it sends an encrypted response based on the user’s password. The problem? That encryption uses 56-bit DES. Cryptographers declared that dead decades ago.
In 1999, Bruce Schneier and Mudge published a paper showing exactly why this was broken. Mudge later worked on security research at Google, the same Google that just released these tables through Mandiant. The circle closes itself.
Here’s how rainbow tables work. NTLMv1 uses a predictable challenge value (1122334455667788) every single time, which means attackers can precompute every possible response to that challenge and store it in a massive table. Once you capture the hash, you search the table and get the password without any guessing involved.
What Mandiant released is a complete set of these tables, hosted on Google Cloud and free for anyone to download.
Before this, you had to upload sensitive hashes to third-party services or buy expensive hardware. David Hulton built a cracking service called crack.sh using custom chips. It worked, but cost money and required trust. That barrier is gone now.
The attack chain uses tools that have existed for years:
- → Responder captures login requests on the network
- → PetitPotam forces domain controllers to authenticate to attacker-controlled servers
- → The captured hash goes into the rainbow tables
- → 12 hours later, the password falls out
- → DCSync attack dumps every password in Active Directory
- → Complete domain takeover
At DEFCON 2012, researchers demonstrated this live on stage. Guest to domain admin in 60 seconds. Microsoft had known about the weakness for 13 years at that point. NTLMv1 was still enabled by default.
The timeline:
- → 1993: Microsoft releases NTLMv1 with Windows NT
- → 1999: Schneier and Mudge publish paper showing it’s broken
- → 2012: DEFCON demo shows full domain takeover in 60 seconds
- → 2021: PetitPotam makes forcing authentication trivial
- → 2024: Microsoft announces NTLM deprecation
- → January 2026: Mandiant releases complete rainbow tables for free
Research from Silverfort found that 64% of Active Directory accounts still use some form of NTLM. Healthcare systems run legacy apps that were never updated. Industrial systems need NTLM for compatibility. Government networks built 20 years ago never finished migrating.
Microsoft finally removed NTLMv1 in Windows 11 24H2 and Server 2025. But millions of older systems are still running.
Signs your network might be vulnerable:
- → Legacy applications from the early 2000s still in production
- → Windows Server 2012 or older still running
- → Software that only supports NTLM authentication
- → Event ID 4624 showing NTLMv1 in authentication logs
The fix:
- → Disable NTLMv1 through Group Policy
- → Audit Event ID 4624 to find systems still using the old protocol
- → Update, replace, or isolate those systems
Security teams argued for years that demonstrating this risk was too difficult. That argument died the moment these tables went public.
The irony? Google’s security division just made attacking Windows networks easier, not to help criminals but to force defenders to finally fix what researchers have been screaming about for 25 years.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.