CVE-2023-31096: Microsoft Modem Driver Exploit Fixed Three Years Later
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
In January 2026, Microsoft had already patched 114 vulnerabilities! Four modem drivers deleted since October. Companies that wrote them: gone. Source code: inaccessible. Microsoft’s only option: remove them entirely. Meanwhile, ransomware groups are loading over 900 other vulnerable drivers that still ship with Windows. 😱 Hackers discovered they could use a 20-year-old telephone code to take over any Windows machine. No hardware required.
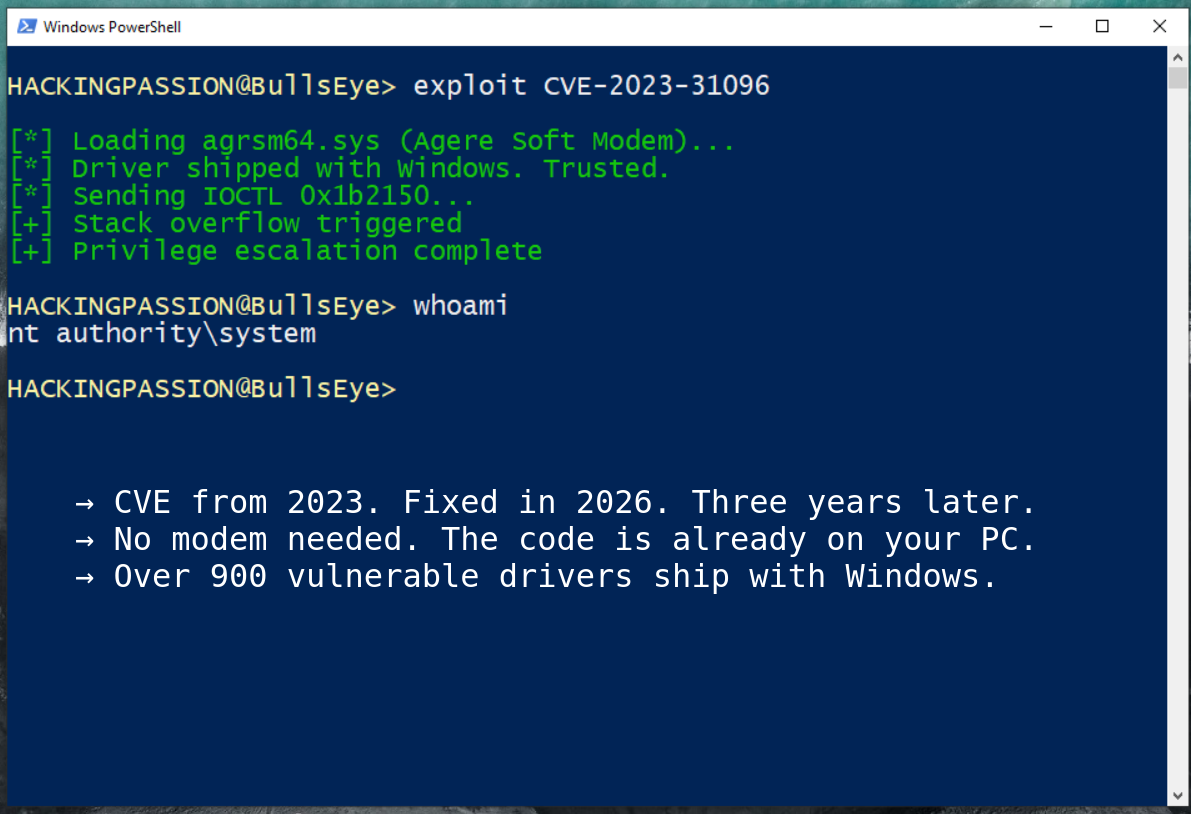
One vulnerability stood out: CVE-2023-31096. A CVE number from 2023. Fixed in 2026. Three years later.
The vulnerability is a stack overflow in the Agere Soft Modem driver. An attacker with basic user access sends a crafted request to IOCTL 0x1b2150. The driver copies data without checking the size. Stack corrupted. Privileges escalated. Standard user becomes SYSTEM.
The drivers affected:
- → agrsm64.sys
- → agrsm.sys
- → SmSerl64.sys (Motorola)
These files exist on every Windows installation. The modem hardware they were designed for has been obsolete for a decade. But the vulnerable code sits there, waiting.
Microsoft’s fix? Delete the drivers. Not patch them. Remove them entirely.
Why couldn’t they fix it?
Follow the ownership chain. Bell Labs invented the transistor in 1947. They created the first modems. AT&T spun off their equipment division as Lucent Technologies in 1996. Lucent spun off their chip division as Agere Systems in 2002. LSI Corporation acquired Agere in 2007. Avago acquired LSI in 2014. Avago bought Broadcom in 2016.
The code is orphaned. The engineers who wrote it are gone. The documentation is lost. Microsoft has no way to safely modify third-party kernel code from a company that no longer exists.
This is what Microsoft removed since October:
- → October 2025: ltmdm64.sys removed after active exploitation (CVE-2025-24990 and CVE-2025-24052)
- → January 2026: agrsm64.sys and agrsm.sys removed (CVE-2023-31096)
- → January 2026: SmSerl64.sys removed (CVE-2024-55414)
Attackers call this technique BYOVD. Bring Your Own Vulnerable Driver.
They don’t need to install malware. They just load a legitimate Microsoft-signed driver that happens to be vulnerable. The operating system trusts it. Antivirus ignores it. Then they exploit it.
The LOLDrivers project tracks over 900 vulnerable drivers that ship with Windows or common software. Living Off The Land Drivers. With these modem exploits: Living Off The Landline.
Ransomware groups love this attack. Cuba ransomware uses vulnerable Avast drivers. BlackByte uses drivers to kill over 1,000 security processes. Qilin evades EDR by loading old Intel drivers. DeadLock exploits Baidu antivirus drivers.
The Agere modem drivers join this list. Proof-of-concept exploits are already on GitHub. Any attacker can download the code and target unpatched systems.
Meanwhile, Microsoft also patched an actively exploited zero-day this month.
CVE-2026-20805 in Desktop Window Manager leaks memory addresses that help attackers bypass security protections. CISA added it to their Known Exploited Vulnerabilities catalog. This is the first information disclosure bug in DWM exploited in the wild. Microsoft’s own Threat Intelligence Center discovered it being used in attacks.
The irony: Microsoft spends billions on AI features nobody asked for while 20-year-old telephone code sits in the kernel waiting to be exploited.
If your organization still relies on analog fax, the January update will break your hardware.
Your options:
- → Switch to cloud fax services (eFax, HelloFax, RingCentral)
- → Use a network fax gateway appliance
- → Buy USB modem hardware with actively maintained drivers
- → Keep one isolated legacy machine offline for fax only
Check if the drivers exist on your system:
- → Open PowerShell as Administrator
- → Run: Get-ChildItem -Path C:\Windows\System32\drivers\agrsm*.sys -ErrorAction SilentlyContinue
- → If files appear, they will be removed by the January update
For IT administrators:
- → Inventory all fax/modem hardware before deploying updates
- → Search your fleet for ltmdm64.sys, agrsm64.sys, agrsm.sys, SmSerl64.sys
- → Prepare migration plans for healthcare, legal, and financial departments that still use fax
- → Consider T.38 fax over IP solutions if you use VoIP
The CVE from 2023 finally has a fix. Don’t wait another three years.
Apply Windows updates immediately.
Hacking is not a hobby but a way of life.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.