Dorks Eye | Google Hacking, Dorks Scraping an Searching Script

Dorks Eye is a script I made in python 3. With this tool, you can easily find Google Dorks. Dork Eye collects potentially vulnerable web pages and applications on the Internet or other awesome info that is picked up by Google’s search bots. You can save the output in a file so that you can view it at a later time. You can determine the number of searches yourself. The number of websites to display
You can also use Dorks Eye as a command-line interface (CLI) to quickly search through Google. Dorks Eye shows only the links, without advertising, and is also really fast.
But be careful not to overdo it, otherwise, you have a chance that If you perform too many requests over a short period, Google will start to throw captchas at you. This is annoying and will limit how much or how fast you do the search.
I did build a little delay in the script so that the chances are smaller. - But still, be careful not to choose too large numbers.
What data can we find using Google Dorks?
- Username and passwords
- Admin login pages
- Sensitive documents
- Govt/military data
- Email lists
- Bank account details
- Vulnerable websites
- So much more …
What is Google Dorks
A Google Dork is a search that uses one or more of these advanced techniques to reveal something interesting. Something important to keep in mind, the web can be crawled by anyone. Google automatically indexes a website, and unless sensitive information is explicitly blocked from indexing (nofollow, robots.txt), all of the content can be searched via Dorks or advanced search operators.
I have previously written an article about Google Dorks, here you can find much more information about its use.
https://hackingpassion.com/google-dorks-an-easy-way-of-hacking/
Install Dorks Eye
Here is the Link to the GitHub page Dorks Eye
Linux
A prerequisite for a script that I make must be that it is simple and easy to use and understand for everyone.
Dorks Eye has tested it so far on:
Kali Linux
Parrot Security
BlackArch
Termux
This list will be expanded
Dork Eye is written for Python 3. Clone the git repository and install the requirements.
|
|
|
|
|
|
Dorks Eye Usage Linux
|
|
That’s all ..!
Termux Install Dorks Eye
Dorks Eye can also be used in Termux ..!
|
|
|
|
|
|
Usage Termux
Termux switched to python3. This is now standard. So you now only have to use the command “python”.
|
|
Video Android With Termux | Dorks Eye Google Dorks Script
Dorks Eye is a script I made in python 3. With this tool, you can easily find Google Dorks. Dork Eye collects potentially vulnerable web pages and applications on the Internet or other awesome info that is picked up by Google’s search bots. You can save the output in a file so that you can view it at a later time. You can determine the number of searches yourself. The number of websites to display.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
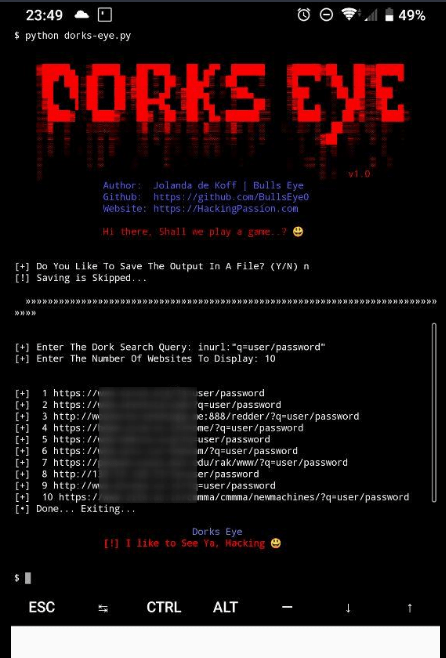
Dork Eye Search Install
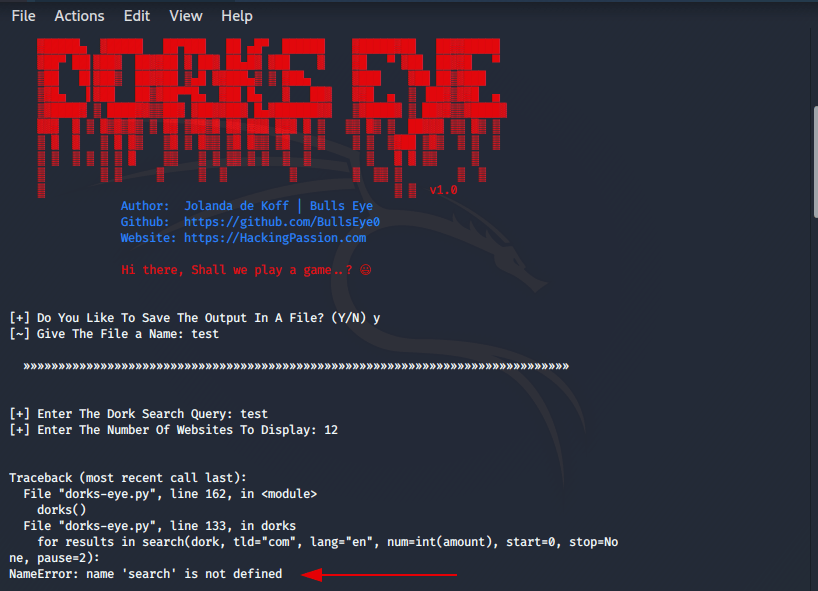
It may be that if you have just installed a new OS (Operating System) you may get some installation errors. First, check if python3 is installed on your computer. You can easily do this by typing python3 in your terminal.
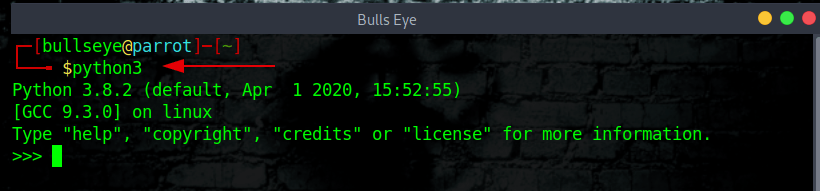
If not, you can easily install it with the following command: (Debian-based)
|
|
The next step is to install pip3, this is also very simple, and you can do it with the command below:
|
|
In the photo below you can see exactly how.
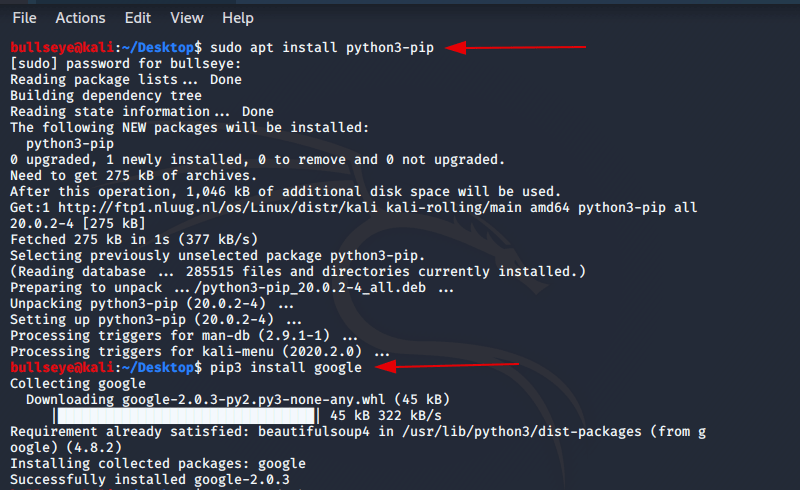
The last step is to install Google. Again this is also very simple, and you can do it with the command below:
|
|
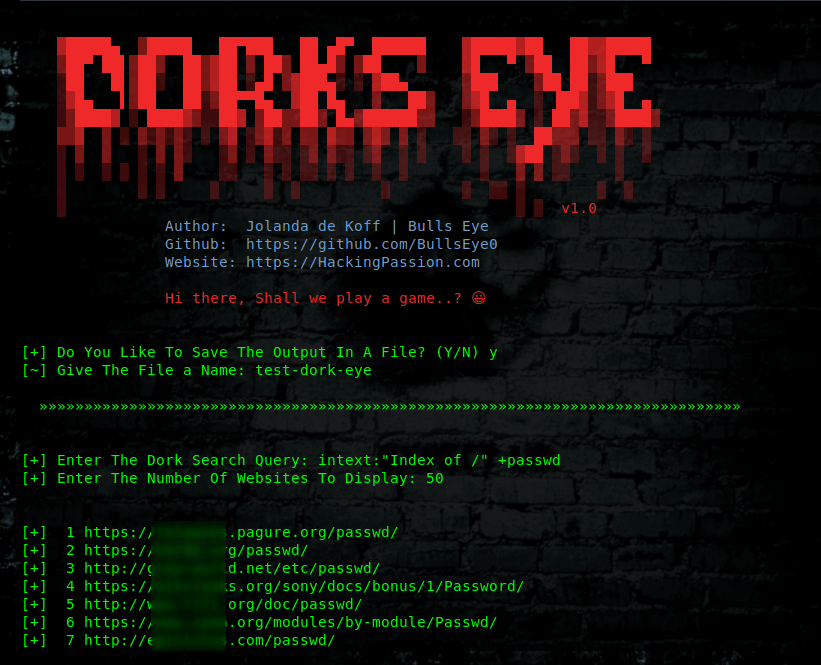
Google Dorks lists
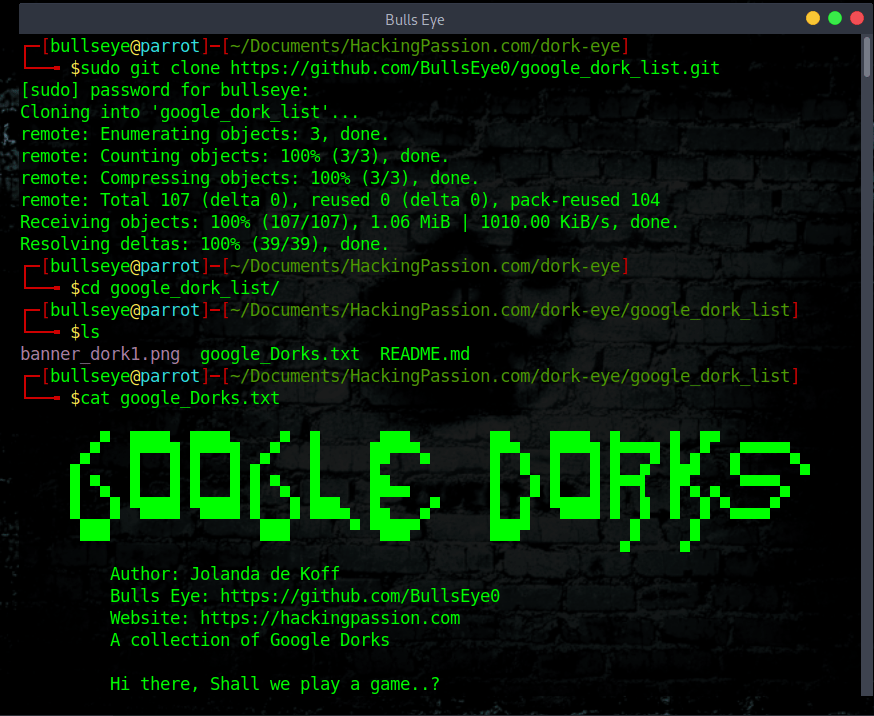
I have stored on GitHub a complete list of up to 13.760 different Dorks. If you want to clone this Dork List to your machine you can do it using the below commands.
|
|
|
|
|
|
|
|

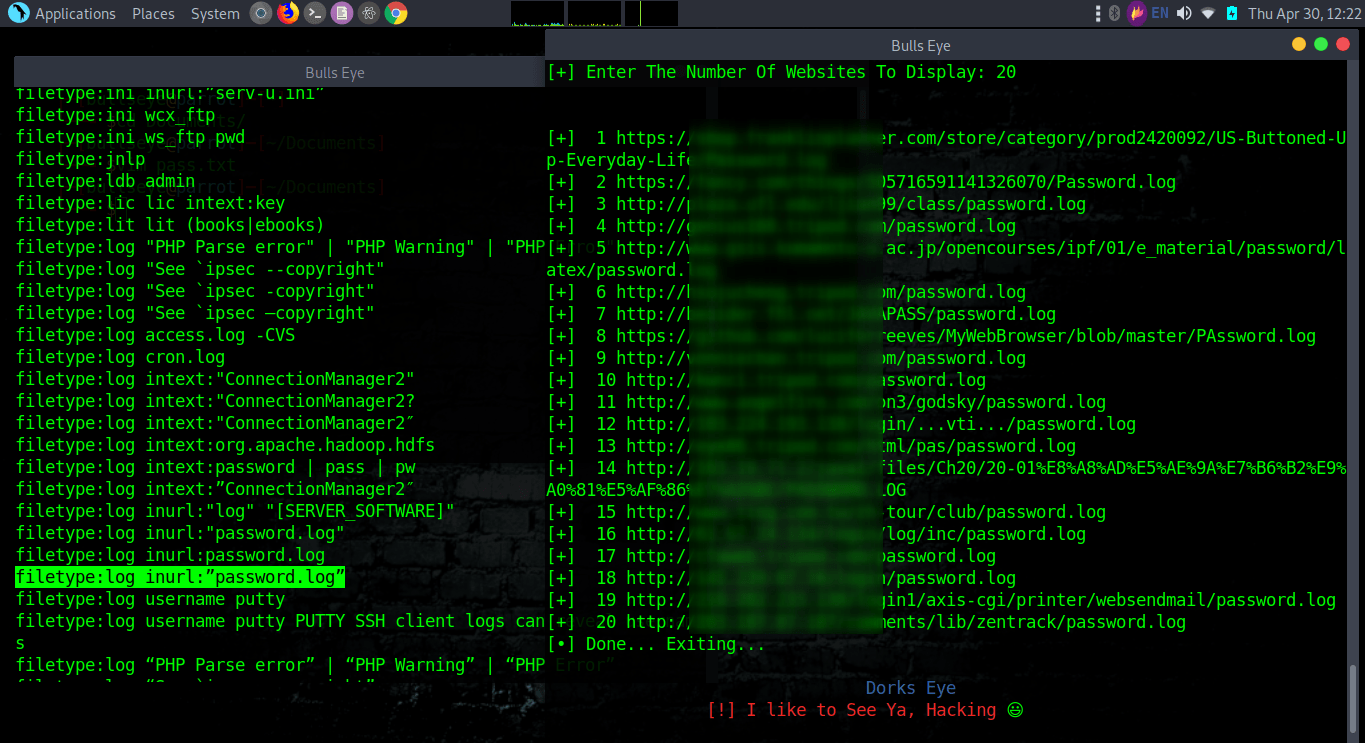
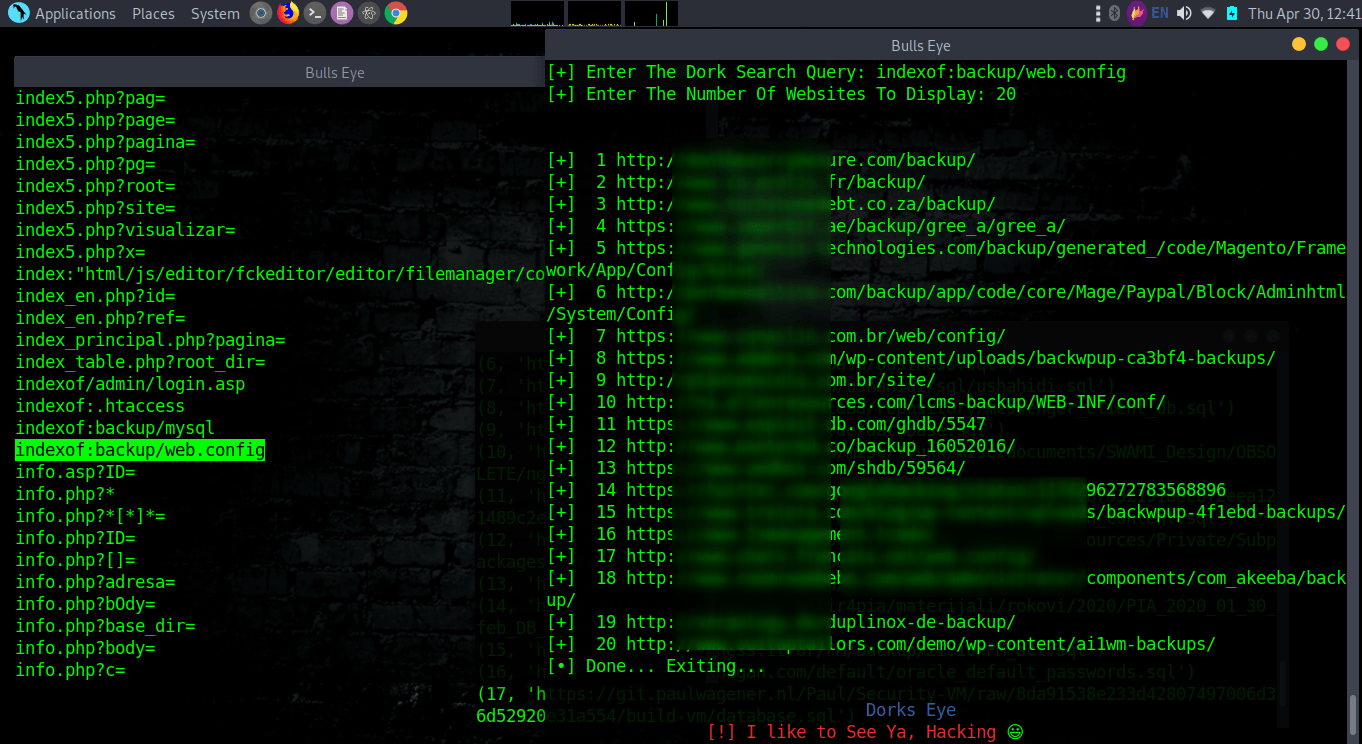
Some Google Dorks examples with Dork Eye and Google Dorks List
|
|
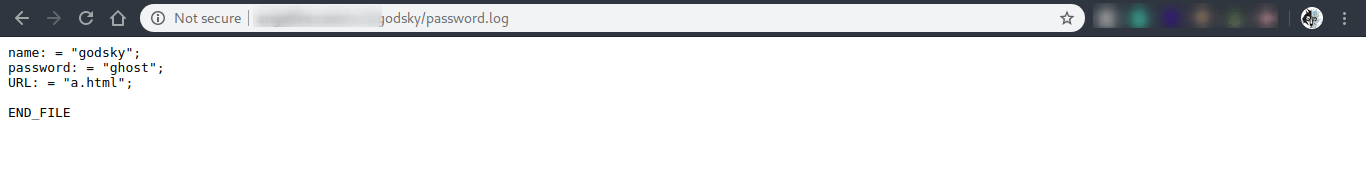
It is wise not to save your login details in this way
Another small example
|
|
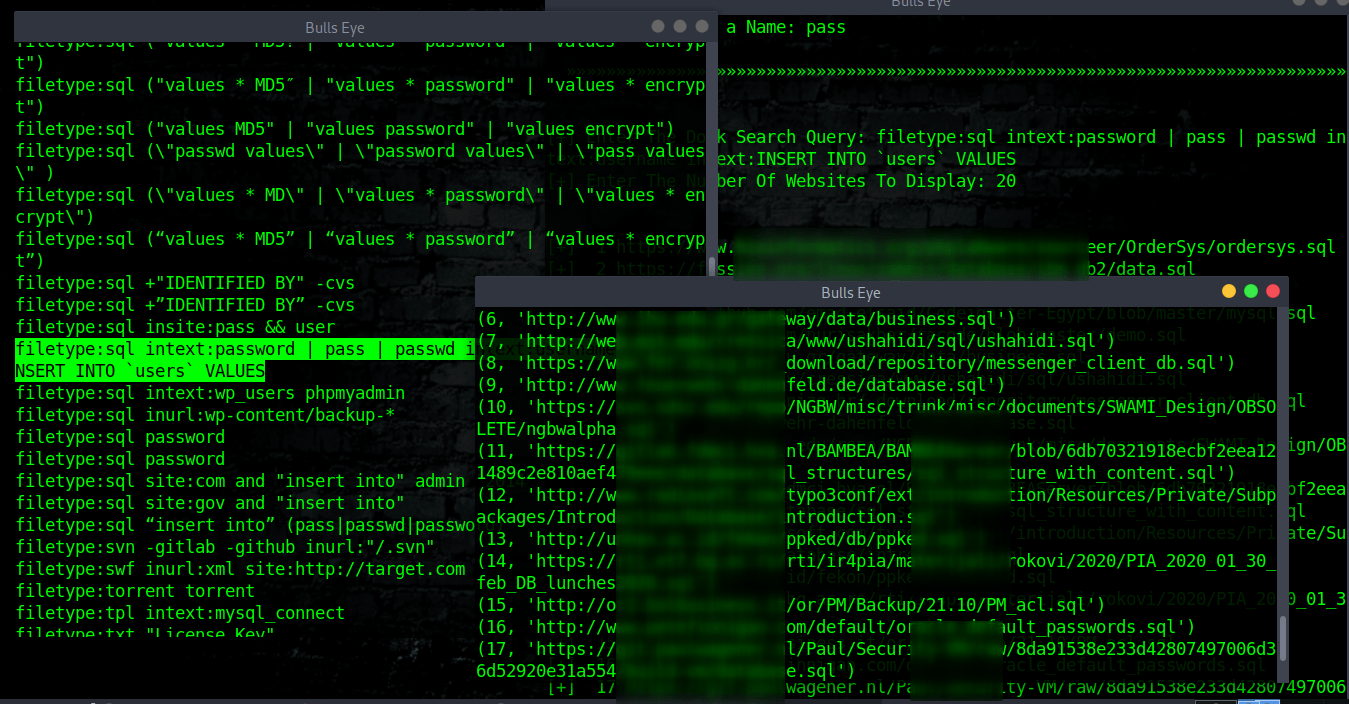
However senseless, there is always an entrance.
|
|
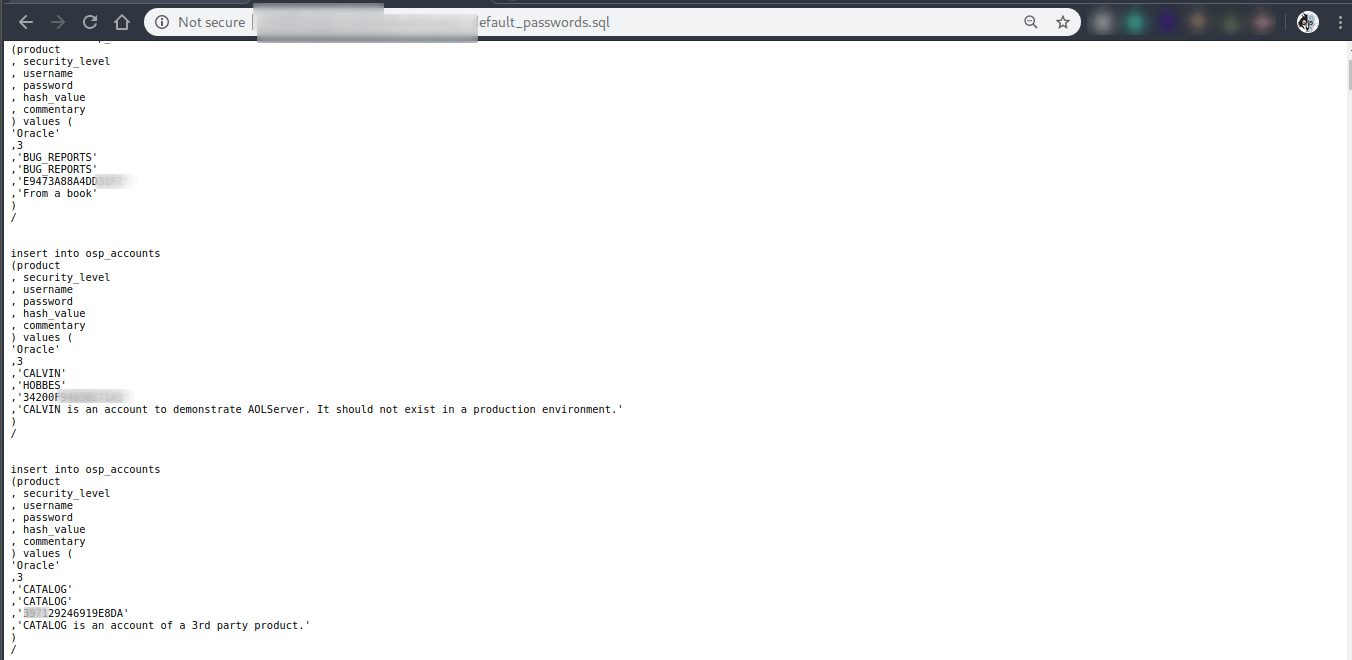
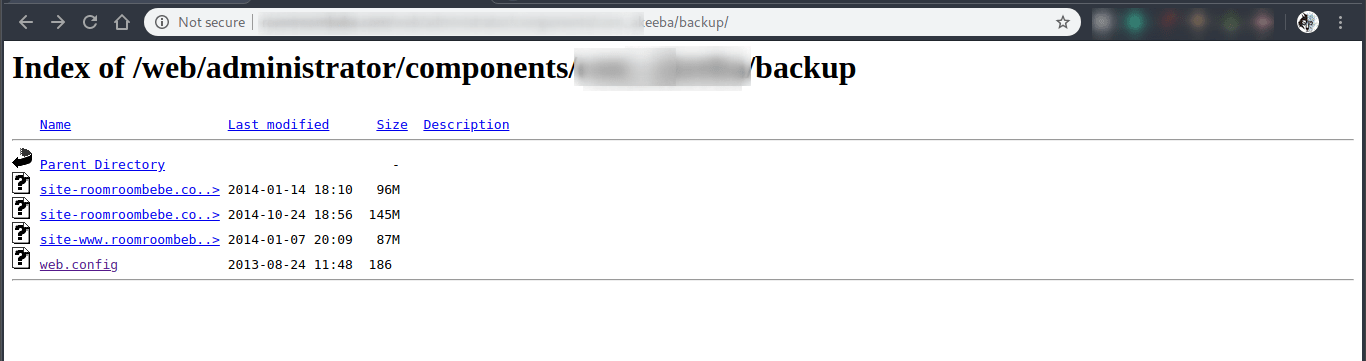
Maybe not a good idea to keep your backups this way.
Google is blocking me
If you start getting HTTP 503 errors, Google has rightfully detected you as a bot and will block your IP for a set period of time. Just wait a while or: A good solution is to use proxychains.
(Or AnonSurf) Here in this article, I explain how to install: Install AnonSurf
Install Tor on Windows, (Kali) Linux and search The Dark Web is also a way.
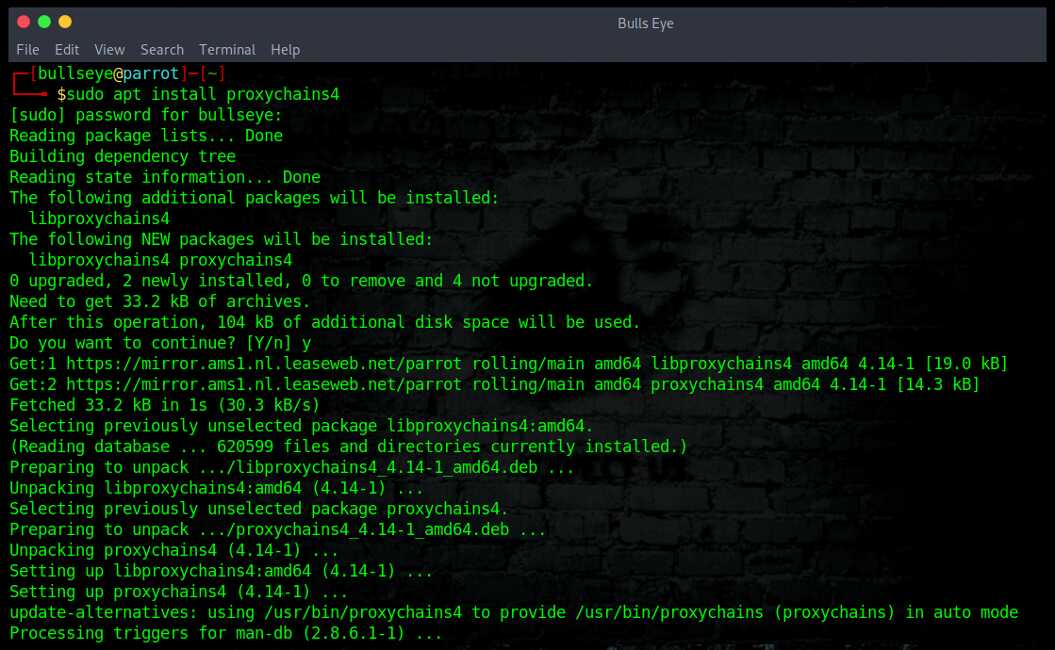
Install Proxychains4 on Debian and derivated distributions
|
|
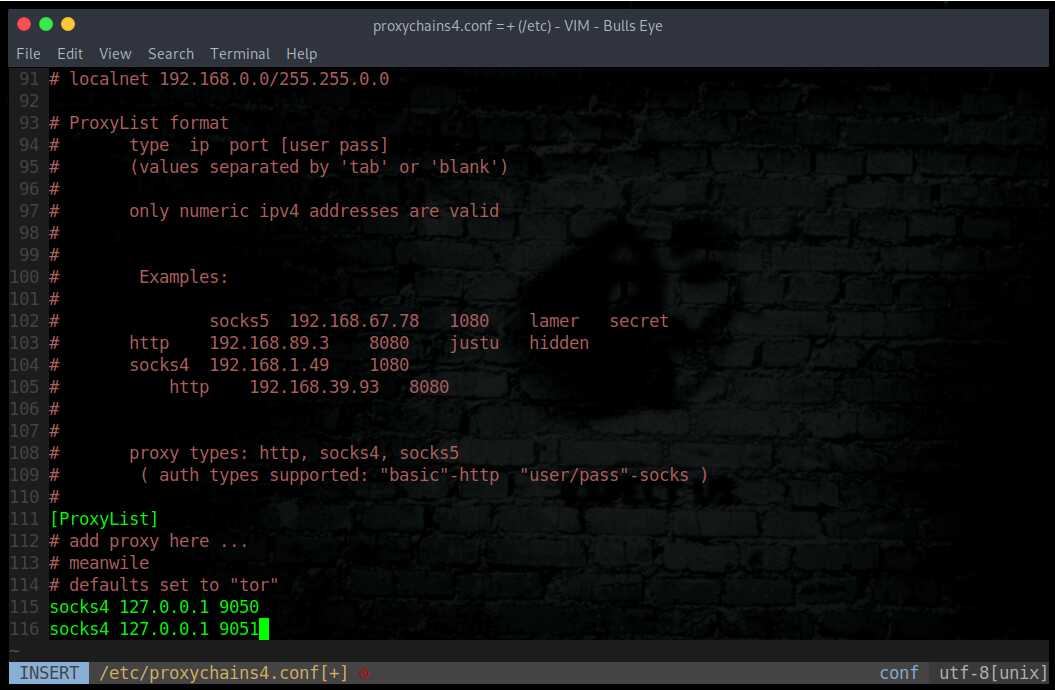
Edit the /etc/proxychains4.conf configuration file to round robin the look ups through different proxy servers. In the example below, 2 dynamic socks proxies have been set up with different local listening ports (9050 and 9051).
|
|
Or
|
|
Video
Dorks Eye Google Hacking Dork Scraping and Searching Script
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
HACKERS LOVE THE TERMINAL
“You are a hacker. Your home is the terminal. You work on several projects at once, You know every keystroke is valuable. With just some commands, you can automate tasks, install your favorite software, view a whole network, find vulnerabilities on just about anything connected to the internet, compile a script, create additional user accounts, properly configure anonymity software, and optimize our interactions with terminals. When you search for something, it should be blazing fast. If something is less than 100% efficient, you will spend hours figuring out the right way to save yourself seconds.”
Conclusion
As I mentioned above, for me personally an outcome of just the left is the best. So I can see in a glance if there is a vulnerability somewhere, just by seeing the whole link.
There is also a great advantage that there is no advertising. And that it is reasonably fast ..
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.