European Space Agency Hacked: 200GB Stolen in 7 Days, Data Sold on FBI Honeypot
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
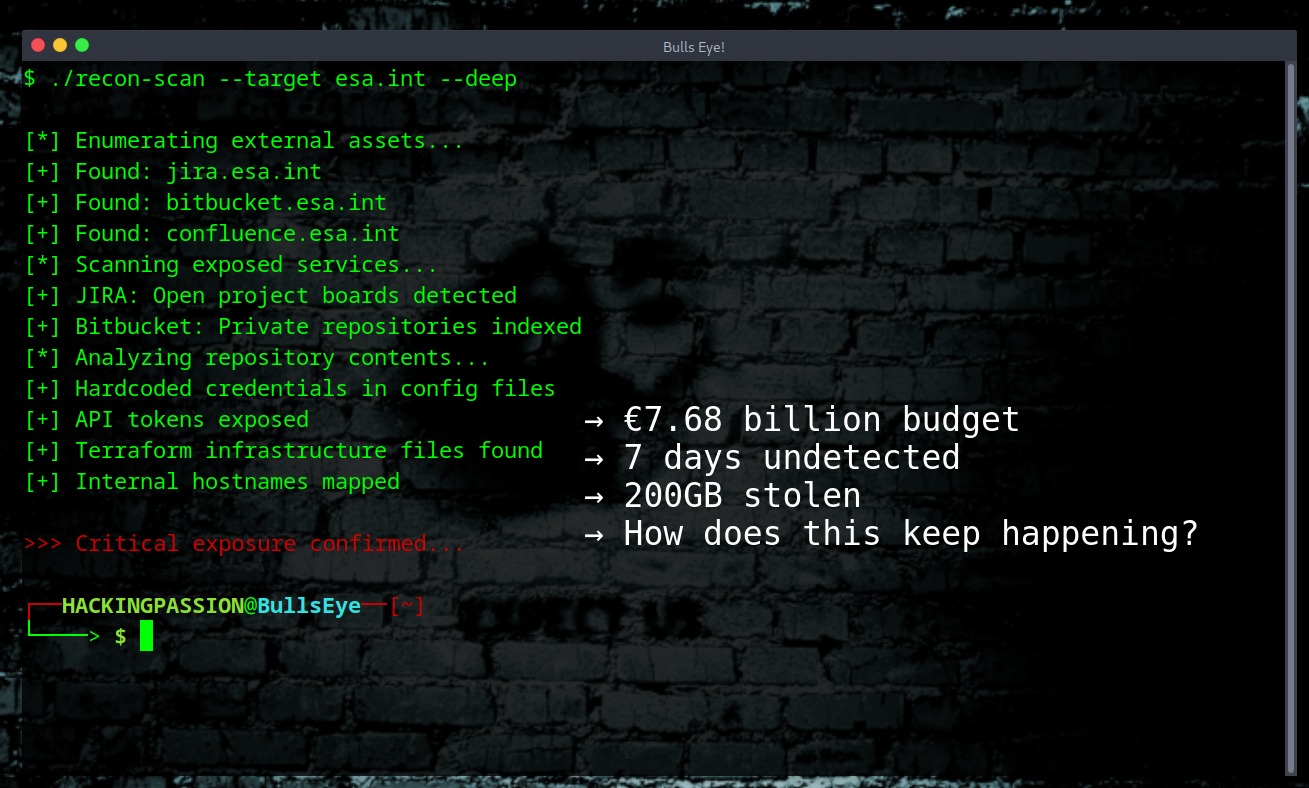
€7.68 billion budget. 3,000 staff. A brand new Cyber Security Operations Centre opened. A hacker spent 7 days inside their systems downloading 200GB of data. Data for sale on FBI honeypot 😏 On December 18, a hacker using the alias “888” got into ESA servers. JIRA project management. Bitbucket code repositories. Internal documentation systems. For seven days, nobody noticed.
On December 26, screenshots appeared on BreachForums. On December 30, ESA finally confirmed the breach.
The stolen data includes: → Source code from private Bitbucket repositories → CI/CD pipeline configurations → API tokens and access tokens → Terraform infrastructure files → SQL databases → Hardcoded credentials → Internal hostnames ending in esa.int → Database credentials and SMTP settings
Screenshots show subsystem requirements for the Ariel mission. That’s ESA’s Ariel exoplanet telescope, built by Airbus, launching 2029. Confidential documents marked Thales Alenia Space and Airbus Defence and Space were visible. Satellite control system requirements. Internal project structures.
ESA’s response: only a small number of external servers were affected. Not the corporate network. Unclassified systems.
December 2024: Hackers injected a fake Stripe payment page into their webshop. Stole customer credit card data. ESA: “External service provider. Not our corporate network.”
2015: Anonymous exploited SQL injection vulnerabilities. Leaked 8,000+ passwords. Security researchers analyzed the dump: 39% of those passwords were just three letters long. Some users had chosen “esa” as their password. ESA: “Only external systems affected.”
2011: Attackers dumped admin credentials, FTP logins, and Apache server configurations. ESA: “Not our internal network.”
Four breaches. Same excuse. 14 years.
On May 27, 2025, ESA opened their Cyber Security Operations Centre at ESOC in Darmstadt. 19 European companies led by Leonardo built it. The C-SOC monitors and protects ESA’s digital assets, from satellites in space to ground stations on Earth.
205 days later: hacker downloads their private repositories for a week straight.
The threat actor “888” has been active since 2024. Previous claimed targets: Microsoft, Nokia, UNICEF, Shell, Oracle and IBM.
Mixed track record. Some claims verified, some exaggerated. But the ESA screenshots show internal project structures and contractor documents.
The data is for sale on BreachForums. Payment in Monero only.
In August 2025, ShinyHunters warned that BreachForums had been seized by French law enforcement and the FBI. The platform is now allegedly a honeypot. All private messages exposed. All IP addresses logged. Source code modified to track every user.
So “888” might be selling European space agency secrets directly to the FBI. 😏
ESA works with NASA, JAXA, and aerospace contractors across Europe. API tokens and Terraform files from one breach? Those become ways into partner networks. That’s how supply chain attacks start.
What organizations can learn from this: → External servers ARE your attack surface → Contractor integrations need the same security as internal systems → “Not our corporate network” is not a defense → Hardcoded credentials in repositories are a disaster waiting to happen → 7 days undetected means your logging and monitoring failed
External collaboration platforms. Contractor access. Development tools outside the main network. Attackers check those first. Always.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.