Fake Blue Screen of Death Installs $5 RAT Malware via ClickFix Attack
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
$5 buys two months of complete access to someone’s computer. Keylogging, webcam, passwords, files. The malware is called DCRat. The delivery method: a fake Blue Screen of Death that tricks people into hacking themselves. 😱
ClickFix attacks surged 517% in six months. Now the second most common attack vector after phishing. 8% of all blocked attacks. The campaign is called PHALT#BLYX. Securonix published their analysis January 5, 2026.
An email arrives with subject “Reservation Cancellation.” Sender appears to be Booking.com. The message mentions a refund over €1,000 and urges the recipient to click and review. Booking.com has been a popular target before, with similar campaigns in 2023 and 2024.
The link leads to a perfect clone of Booking.com with the correct colors, logos, and fonts. Indistinguishable from the real site.
Then a loading error appears. “Taking too long. Click to refresh.” One click and the browser goes fullscreen.
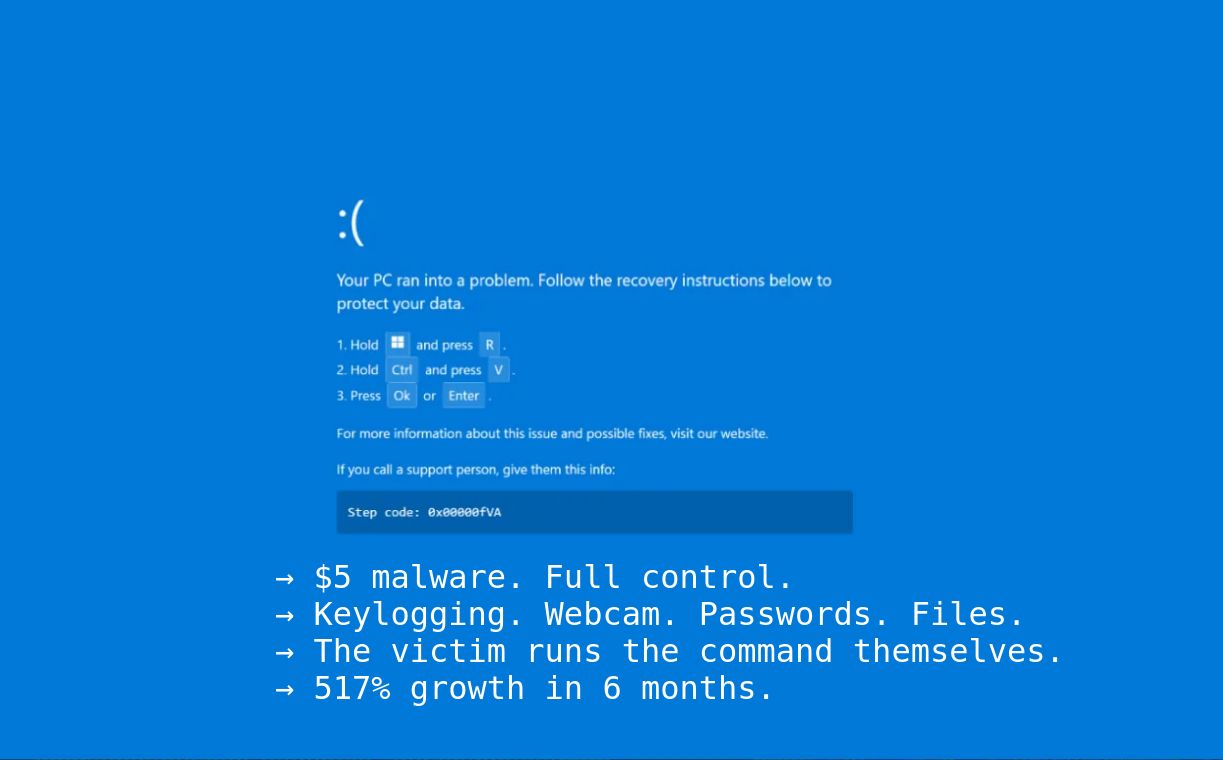
A Blue Screen of Death fills the screen.
But Windows is not crashing. This is a webpage designed to look exactly like a system failure. The victim cannot easily escape.
Instructions appear: press Win+R, then CTRL+V, then Enter.
The malicious webpage runs JavaScript that silently copies the PowerShell command to the clipboard the moment you click. You never see it happen. When you press CTRL+V in the Run dialog, it’s already there waiting.
The victim thinks they are fixing their computer. What they are actually doing is pasting a malicious PowerShell command that was silently copied to their clipboard.
The command downloads a project file and Windows’ own MSBuild.exe compiles it into malware. This is called living off the land: using trusted system tools against the user.
The malware disables Windows Defender, adds exclusions, and establishes persistence. Then it injects the final payload into Windows process.
The payload is DCRat. A remote access trojan available since 2018. Price on underground forums: $5 for two months. $40 for lifetime access.
What DCRat can do: → Keylogging → Webcam access → File theft → Password extraction → Remote desktop → Drop additional malware
In this campaign, attackers also installed a cryptominer. Initial access brokers like TA571, who have been pushing ClickFix since March 2024, are known to sell this kind of access to ransomware groups.
ClickFix was first observed March 2024. It exploded because it bypasses almost everything. There is no malicious file to scan and no exploit to patch. The victim runs the command themselves.
Since then, official reports have linked ClickFix to nation-state actors from Russia, North Korea, Iran, and Pakistan. But in cybersecurity, attribution is one of the hardest problems. IP addresses can be spoofed, tools get shared between groups, and code artifacts can be planted to mislead investigators. I leave attribution where it belongs: uncertain.
What matters: the attack works. And it is spreading fast.
This BSOD variant specifically targets European hospitality: hotels, hostels, and bed and breakfasts.
The technique adapts. Earlier versions used:
→ Fake Google Meet errors
→ Fake Microsoft Word prompts
→ Fake Windows Update screens
→ Fake CAPTCHA verifications
All designed to trick people into copying, pasting, and running malicious code.
Real Blue Screen of Death messages NEVER ask for action. They show an error code and restart, nothing else.
Signs of ClickFix attempts: → Any webpage asking to press Win+R → Instructions to paste something into PowerShell → Fullscreen browser that cannot easily be closed → “Fix it” buttons that copy invisible commands
What to do: → Never paste commands from websites into Run or PowerShell → If a BSOD appears in a browser, close it (Alt+F4 or Ctrl+W)
Already infected? What to do: → Disconnect from the network immediately. Do not shut down the machine. → Reset all passwords from a different, clean device. → Check other systems on the same network for signs of lateral movement. → Preserve logs and evidence for forensic analysis. → Consider reporting to relevant authorities (CERT, police cybercrime unit).
The malware establishes persistence and may have already spread.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.