Fake GitHub Exploits Target Security Researchers: Download a PoC, Get Malware
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Attackers are targeting security researchers through GitHub. You downloaded a proof-of-concept exploit from GitHub. Professional README. Detailed instructions. Real CVE number. Except it’s malware. 😱 And now your system is compromised.
Kaspersky published their findings on December 23, 2025.
Attackers are creating GitHub repositories with fake exploits for real vulnerabilities. CVE-2025-59295 (CVSS 8.8), CVE-2025-10294 (CVSS 9.8), CVE-2025-59230 (CVSS 7.8). Fake exploits that install malware.
Kaspersky identified 15 malicious repositories pushing this malware. GitHub has removed them, but new repositories will pop up under different account names.
The business model behind it is disturbing. WebRAT subscriptions cost around €11 per month. And the operators aren’t just stealing credentials and crypto wallets. According to Solar 4RAYS research, stolen personal data is being used for blackmail and swatting, calling fake emergency reports to send armed police to victims’ homes.
The repositories look completely legitimate with professional structure, vulnerability overviews, affected systems, installation guides, usage instructions, and even mitigation advice.
Kaspersky identified the README content as AI-generated by the identical structure and nearly identical mitigation advice across all malicious repos.
Linux and Mac users are safe from this one. It’s Windows-only malware.
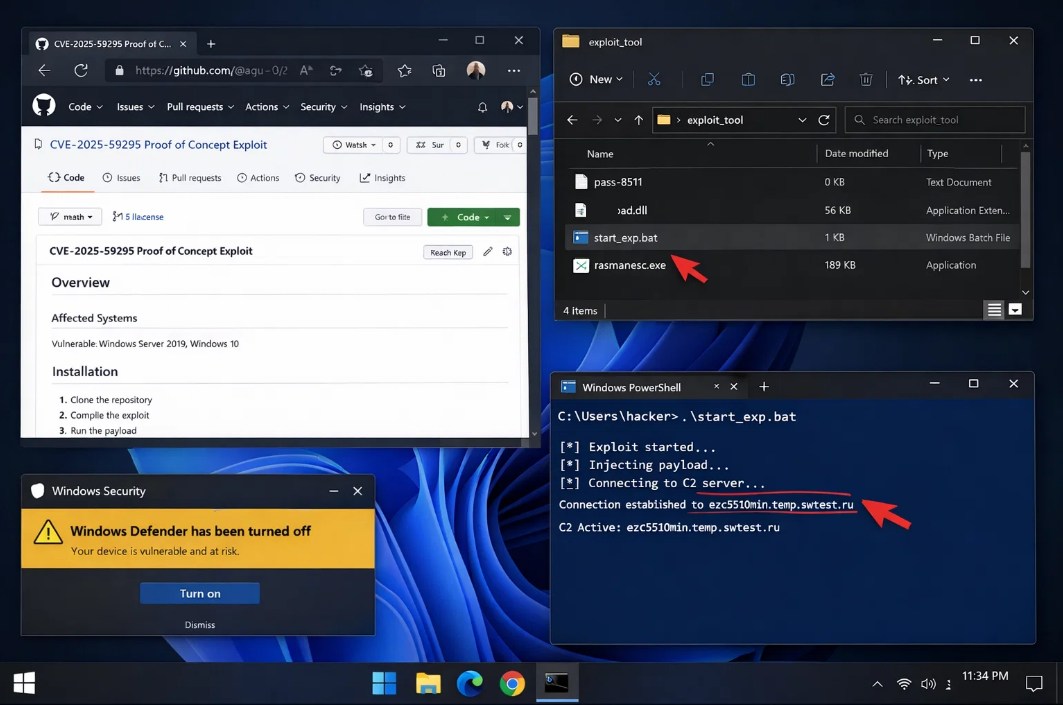
Here’s the attack flow: → Download the password-protected ZIP file → The password is hidden in a filename inside the archive (pass-8511) → Extract four files: an empty file with the password in its name, a decoy DLL (payload.dll), a batch file (start_exp.bat), and the loader (rasmanesc.exe) → The loader escalates to admin privileges → It disables Windows Defender → Downloads Webrat from a remote C2 server → Executes the payload
What Webrat does once it’s on a system: → Full backdoor access for remote control → Steals cryptocurrency wallets → Grabs Telegram, Discord, and Steam credentials → Records the screen in real-time → Activates the webcam without indication → Activates the microphone → Logs every single keystroke
The malware is sold by a group called NyashTeam, the same group that also distributes DCRat. They previously distributed Webrat through game cheats and cracked software. Now they’ve expanded their targeting to security researchers and anyone downloading PoC exploits.
Kaspersky identified multiple malicious repositories including accounts like RedFoxNxploits, FixingPhantom, h4xnz, and others.
Technical indicators from the Kaspersky report: → C2 servers: ezc5510min[.]temp[.]swtest[.]ru and shopsleta[.]ru → Kaspersky detects this as HEUR:Trojan.Python.Agent.gen and HEUR:Trojan-PSW.Win64.Agent.gen
Anyone who searches GitHub for exploits is a potential target. The attackers specifically choose CVEs that are trending in security news or don’t have working public exploits yet because they know people are actively searching for these.
This is why everything should be tested in an isolated environment. A VM, a sandbox, whatever works. A main machine with credentials, wallets, and sensitive data is not the place to run unknown code from GitHub, no matter how professional the repository looks or how many stars it has.
Verify before you execute. Learn to read the code.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.