16-Year-Old's AI Finds Heap Buffer Overflow in FFmpeg EXIF Parser
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
A 16-year-old built an AI that mass-hunts memory bugs. It found 6 vulnerabilities in FFmpeg in December. One was a heap buffer overflow in the EXIF parser. The code that reads your photo metadata. 😎
FFmpeg processes media on billions of devices. VLC. Chrome. Firefox. YouTube. Blender. OBS Studio. Plex. Even NASA’s Perseverance rover uses FFmpeg.
The vulnerability: CVE is still pending.
Important nuance: this bug was in FFmpeg’s development branch, not in a public release. It existed for three days before it was caught. Three days. FFmpeg called the researcher “a model security researcher” for catching it before it shipped.
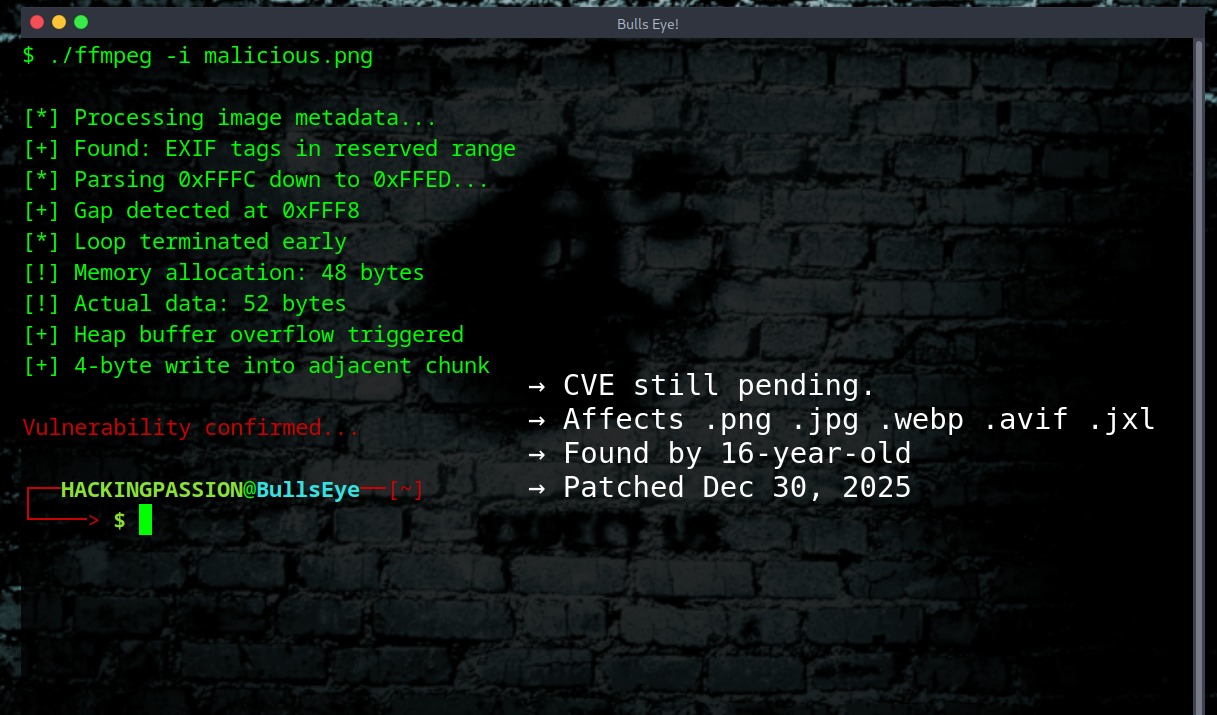
The bug sits in libavcodec/exif.c. EXIF is the metadata in your photos. GPS coordinates, camera settings, timestamps. FFmpeg stores extra metadata in reserved tags from 0xFFFC down to 0xFFED. The code expects these tags to disappear one by one. It reserves memory based on that.
But the removal loop breaks on the first gap it finds. An attacker creates an image with gaps between the tags. The loop stops early. Tags that should be gone are still there. The memory allocation is too small. A 4-byte write spills into the next heap chunk.
The trigger:
./ffmpeg -i malicious.png
Default build. No special flags. Just open the file.
Affected formats: → .png → .jpg → .webp → .avif → .jxl
Ruikai Peng found the bug, 16 years old. Founder of Pwno, an AI-powered security research company. 25 CVEs on his record. Youngest speaker in Black Hat USA history.
He submitted a patch. FFmpeg rejected it. Too invasive. The maintainer Leo Izen wrote his own fix on Christmas Day.
Timeline: → December 2025: Bug introduced in FFmpeg master → December 2025: Pwno discovers and reports it → December 2025: Pwno’s patch rejected → December 25, 2025: Leo Izen writes new patch → December 30, 2025: Patch merged
AI is now hunting bugs at machine speed. Traditional fuzzing has hammered FFmpeg for years. Google runs OSS-Fuzz on it constantly. This AI found something different. Not better or worse. Different.
The list of Pwno findings is still short for 8 months of work. But this is early. The question isn’t whether AI will change security research. It’s how fast.
A teenager pointed an AI at one of the most battle-tested codebases on the planet. It caught a bug three days after it was introduced.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.