Getting Started With Ghost Eye
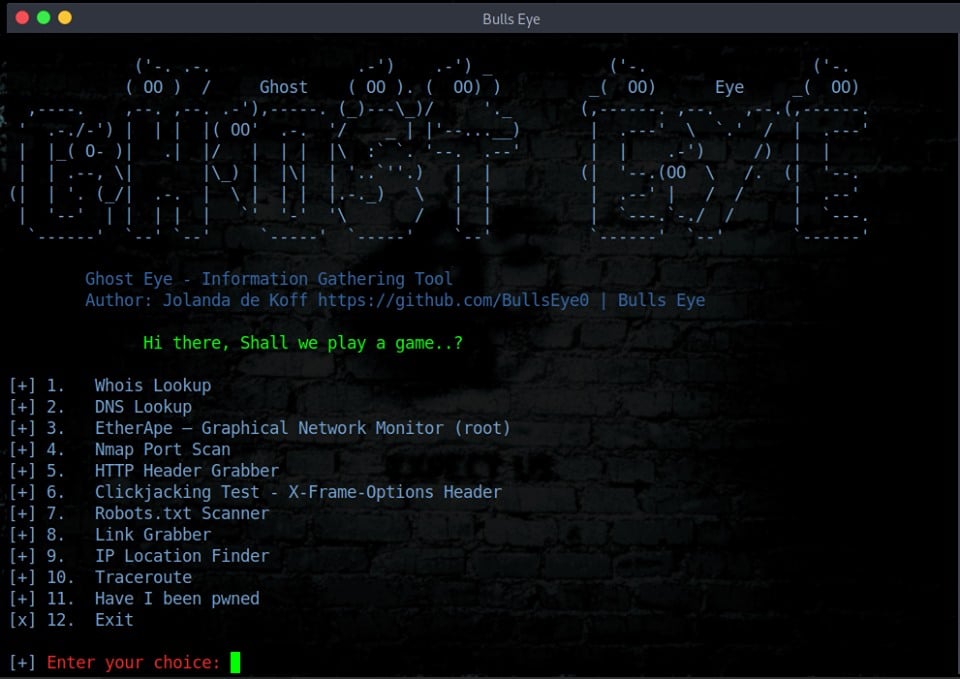
Ghost Eye is an Information Gathering - Footprinting and Reconnaissance Tool I made in Python 3. It includes some important tools for Information Gathering.
Install Ghost Eye on Linux
I advise everyone to read this carefully, it is often forgotten during installation that Ghost Eye is using python3. So before to move further, please check if Python 3 is already present in your machine. If you need to install it, just follow the below commands.
Install Python 3 on Arch Linux and its distros:
| |
Install Python 3 on Debian and its distros:
| |
Furthermore, you will need to install also Nmap and EtherApe too:
On Arch Linux and its distros:
| |
On Debian and its distros:
| |
If you are done with the above requirements, you can move on to the next step and clone the Ghost Eye repository to your computer.
| |
| |
| |
Usage
| |
In some cases, Ghost Eye can require root privilege to execute third-parties applications such as EtherApe.
| |
The unique thing you have to do, it’s to complete the above command with the website or the IP address you want to scan.
ETHERAPE
Let’s start with the third (Option 3). Personally, I think this is one of the nicest and most useful tools to see what is happening in your network environment. Certainly in combination with Wireshark. I would say, try this amazing tool, and see what happens if you open a random link. You will be amazed by this ..!
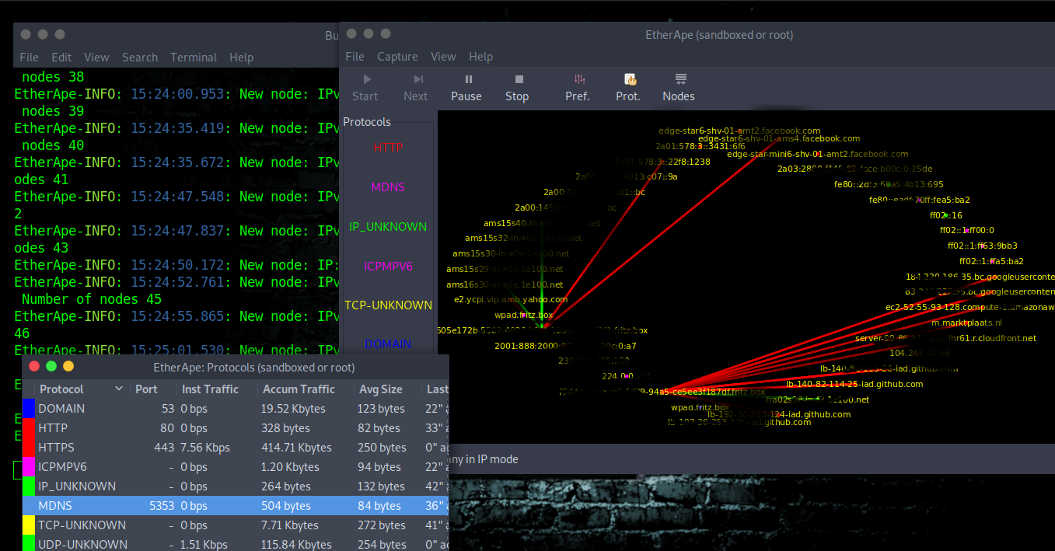
EtherApe is a graphical network monitor and a packet sniffer that collects information and displays it graphically and it supports Ethernet, FDDI, Token Ring, ISDN, PPP, SLIP and WLAN devices, plus several encapsulation formats. It can filter traffic to be shown and can read packets from a file as well as live from the network.
Below something more extensive
Ethernet: (IEEE 802.3) is a network standard with which computers in a LAN communicate with each other. The Institute of Electrical and Electronics Engineers (IEEE) defines Ethernet as protocol 802.3. But “Ethernet” is a lot easier to pronounce, and probably also the name under which you know this essential connection to the internet. On top of the Ethernet, layer is protocols, of which TCP / IP is the best known and most used.
WLAN: Abbreviation for ‘Wireless LAN’, or ‘Wireless Local Area Network’. A wireless connection between different computers or computer devices that are close together. There are various techniques for setting up a wireless local network. The most important are the WiFi and Bluetooth. This gives users the ability to move around within the area and yet still be connected to the network. Through a gateway, a WLAN can also provide a connection to the wider Internet.
FDDI: Fiber Distributed Data Interface which is an optical data communication standard used for long-distance networks provides communication with fiber optic lines up to 200 kilometers at a speed of 100 megabits per second (Mbps).
Token Ring: A local area network in which a node can only transmit when in possession of a sequence of bits (the token), which is passed to each node in turn.
EterApe was originally written by Juan Toledo. The first version of EtherApe (version 0.0.1) was released on February 18, 2000. Because it has been around for a long time, it also reflects the power of this tool. The Node statistics can also be exported.
TO USE ETHERAPE YOU NEED ROOT PRIVILEGES
If you are using any of the latest versions of pentest distributions such as Kali Linux, Parrot Security or BlackArch, EtherApe is already installed. If EtherApe is not present in your machine and you need to install it, simply open your terminal and use the below commands.
Debian-based:
| |
Arch-based:
| |
Fedora:
| |
Centos:
| |
You may receive an error message during installation. This is often GNOME related, and especially with old distros. In such a case, I recommend checking whether the below packages are installed in your machine. If these packages are not yet installed, you can install it using the below commands:
Debian-Based:
Install missing packages
| |
Install missing dependencies
| |
There are so many options for using EtherApe. To move further, you can take a look around or use the man page.
| |
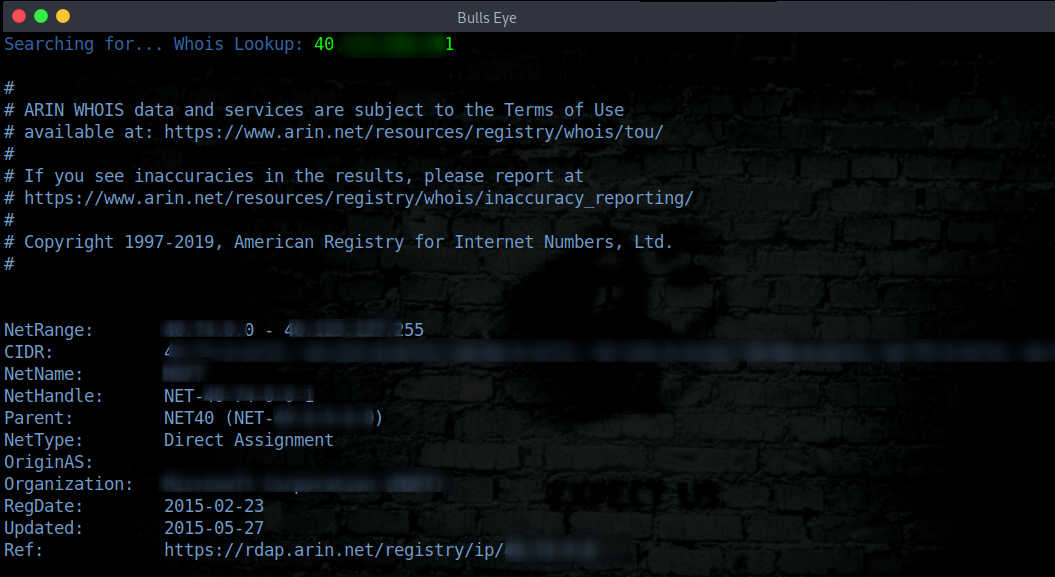
WHOIS LOOKUP
The second tool that we will discuss is the whois tool (Option 1 in Ghost Eye tool). whois searches for an object in a whois database. whois is a query and response protocol that is widely used for searching databases that present users from an internet source, such as a domain name of an IP address.
As part of the domain registration process, registrants must provide their registrar with correct and dependable contact details and make sure this information is kept up to date. Failing to provide reliable information, or a willful failure to replace out of date data supplied to a registrar can lead to your registration being canceled. The registrar that you pick will ask you to offer contact and technical records, some of which are required by ICANN (The Internet Corporation for Assigned Names and Numbers). Personal data such as e-mail addresses etc. can be included in a WHOIS result.
There will be the following details of the registrant.
- Name
- Organization
- Street
- City
- State
- Postal Code
- Country
- Phone
- Fax
As you can see, to get information from a certain website or IP address, the whois tool is very useful and can provide you quickly accurate information.
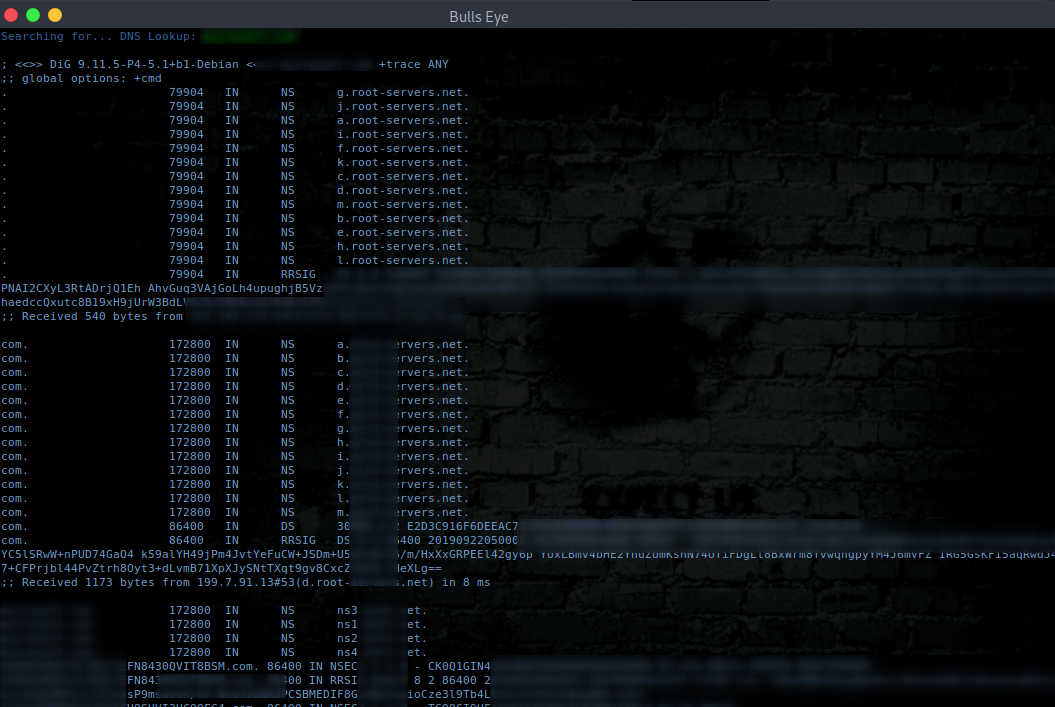
THE DNS LOOKUP
The next option that we will discuss is the DNS Lookup tool (Option 2 in Ghost Eye tool). DNS stands for “Domain Name System” and is the process by which a DNS record has been returned from a DNS server. Just like looking up a phone number in a phone book - that’s why it’s referred to as a “lookup”.
Interconnected computers, servers, and smartphones need to know how to translate the email addresses and domain names people use into meaningful numerical addresses. A DNS lookup performs this function. There is so much to tell about DNS, but I wouldn’t bore you with that.
NMAP PORT SCAN
Nmap port scan (Option 4 in Ghost Eye tool). Nmap is the most used tool for scanning open ports. Naturally, Nmap can do much more than that. Nmap (“Network Mapper”) is an open-source tool for network exploration and security auditing.
In Ghost Eye, the Nmap scans the specified link or IP address and searches for open ports. An nmap -Pn scan is used in the Ghost Eye script. -Pn is used to treat all hosts as online - skip host discovery
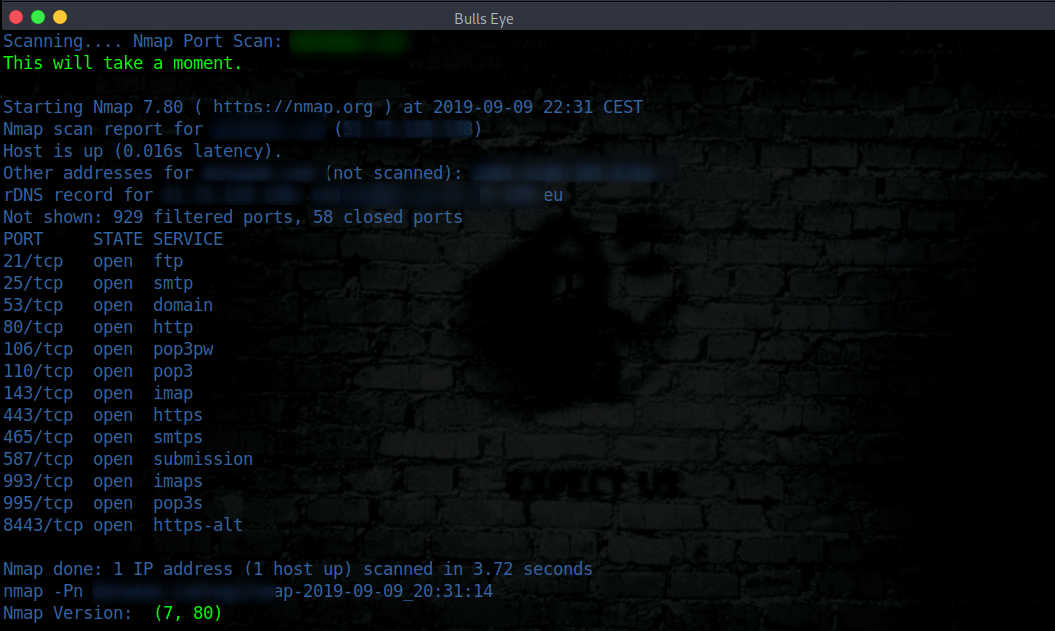
As you can see in the example above there are quite a lot of open ports. On the basis of this, you could investigate whether a port is vulnerable or not. For further research, I can refer you to one of my previous articles explaining “how to use Nmap NSE scripts to find vulnerabilities”.
HTTP HEADER GRABBER
HTTP Header Grabber (Option 5 in Ghost Eye tool). The HyperText Transfer Protocol (HTTP) is a client-server protocol powering most of the internet. Every time you surf the internet, your browser sends HTTP requests for HTML pages, images, scripts, and style sheets. Web servers handle these requests by returning responses containing the requested resource, thus completing the HTTP request-response cycle.

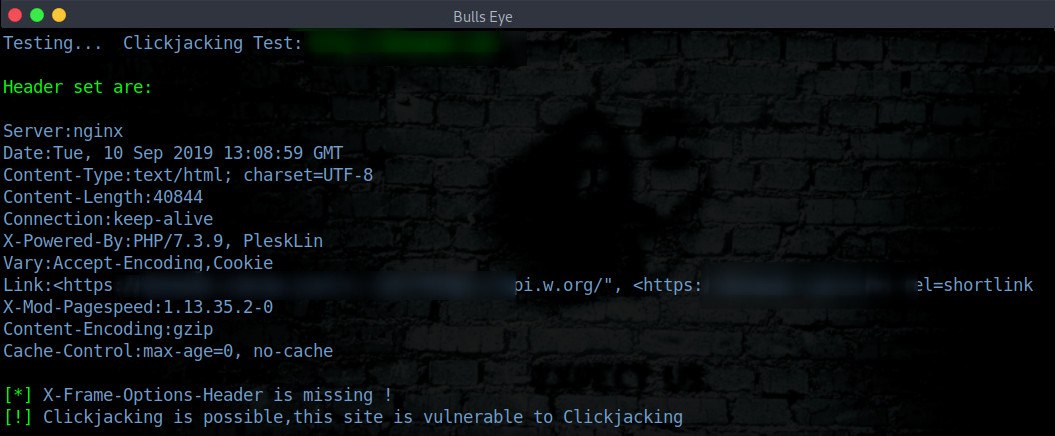
CLICKJACKING TEST - X-FRAME-OPTIONS HEADER
Clickjacking - X-Frame Options (Option 6 in Ghost Eye tool). Clickjacking is an attack when an attacker uses a transparent iframe in a window to trick a user into clicking on button or link, to another server in which they have an identical looking window. The attacker in a sense hijacks the clicks meant for the original server and sends them to the other server.
X-Frame-Options is an HTTP response header, also referred to as an HTTP security header. This header tells your browser how to behave when handling your site’s content.
X-Frame-Options are used to indicate whether the browser can render a page in an iframe, frame or object. The three possible values are:
- DENY: The page cannot be rendered in a frame under any circumstance.
- SAMEORIGIN: The page can only be displayed in a frame if the “framing” site is on the same origin.
- ALLOW-FROM: The page can only be framed from a specific origin.
HOW TO ENABLE X-FRAME-OPTIONS HEADER
Enable on Nginx
To enable the x-frame-options header on Nginx simply add it to your server block config.
| |
Enable on Apache
To enable on Apache simply add it to your httpd.conf file (Apache config file).
| |
Enable on IIS
To enable on IIS simply add it to your site’s Web.config file.
| |
ROBOTS.TXT SCANNER
Robots.txt Scanner (Option 7 in Ghost Eye tool). The file robots.txt is used to give instructions to web robots, such as search engine crawlers, about locations within the web site that robots are allowed, or not allowed, to crawl and index.
“When you say “move along, nothing to see here”, the bad guys get interested”
Vulnerabilities in robots.txt Detection is a Low-risk vulnerability that is one of the most frequently found on networks around the world. BUT sometimes you come across something special. Nevertheless, in this case, I must also refer you back to the article about Google Dorks.
Is someone trying to hide their password?
Google Dorks
| |

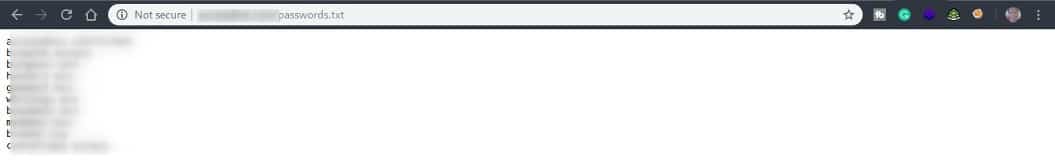
Again … You should be very careful when you are writing your “robots.txt” because if someone checks it or someone with some imagination searches on Google with these types of queries, you could be a hacker’s target!
“Hacking can be so difficult … But sometimes it’s oh so easy ..!”
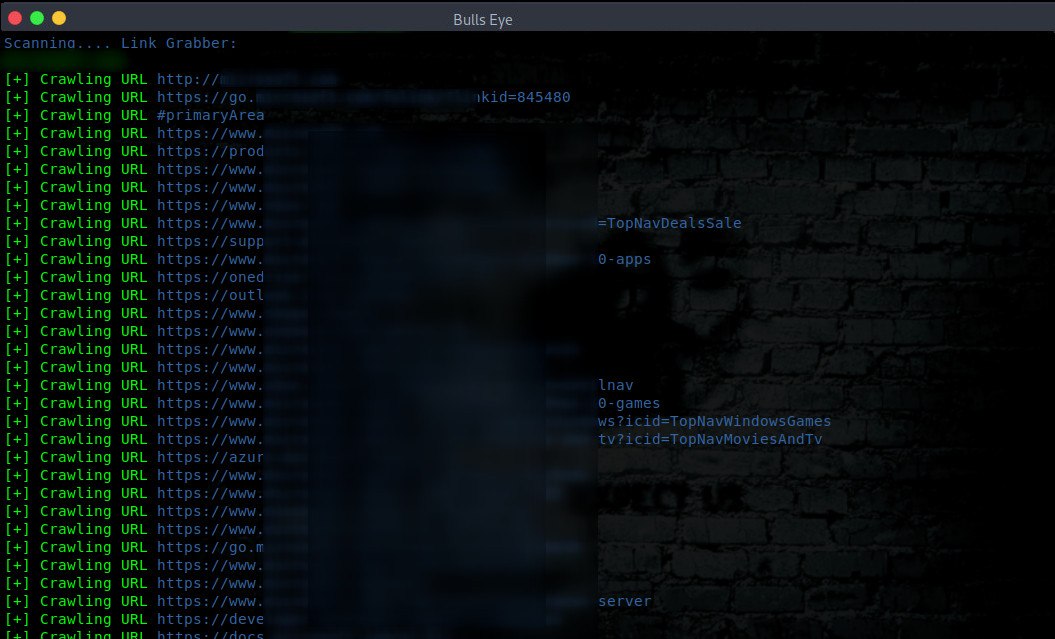
LINK GRABBER
Link Grabber (Option 8 in Ghost Eye tool). The Link Grabber will parse the html source code of a website and extract links from the page. The hrefs or “page links” are displayed in plain text for easy review.
The purpose of this tool is to find hidden links and look for irregularities on a website. It can be used also to find a login or registration page and much more.
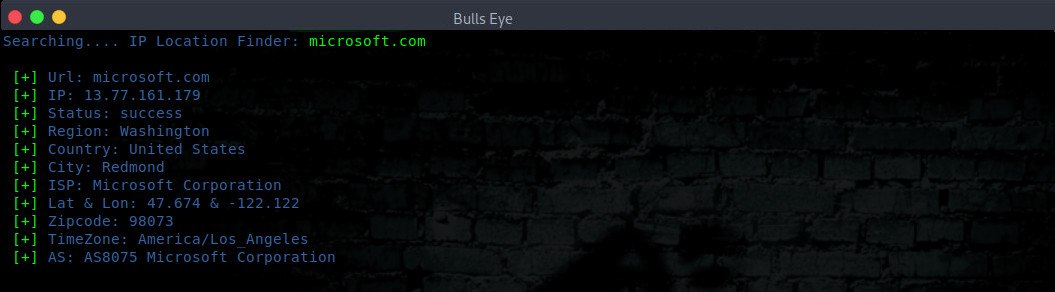
IP LOCATION FINDER
IP Location Finder (Option 9 in Ghost Eye tool). Have you ever wondered where a certain website or IP address can be located? With the IP Location Finder, you can retrieve this information. For a given URL or IP, the tool will return you the latitude and longitude of the device or the server. There is not so much to tell about this tool, I think it cannot be clearer.
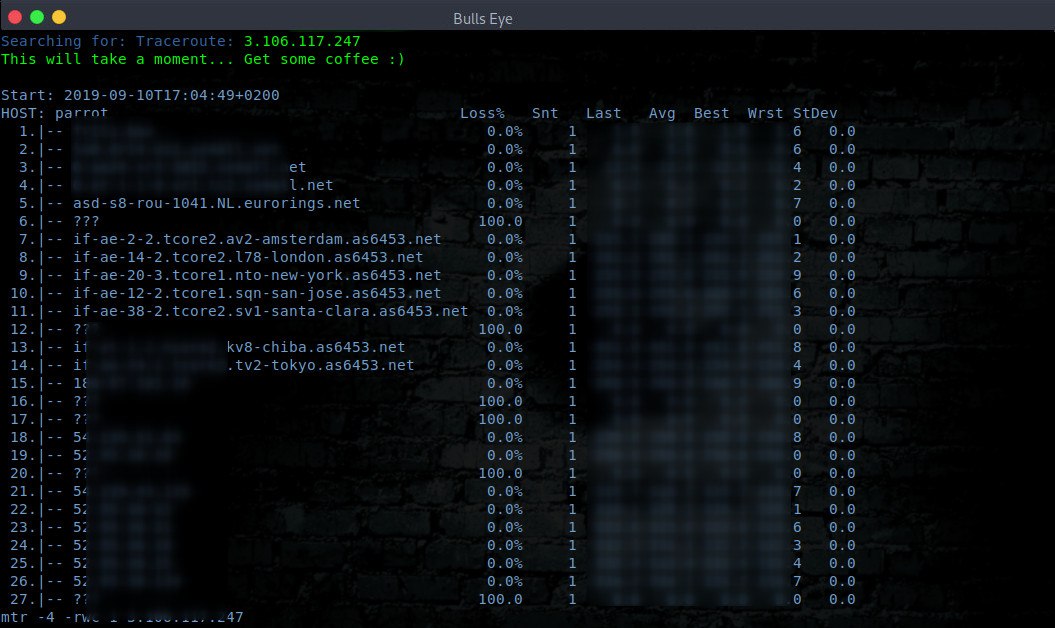
TRACE ROUTE
Trace Route (Option 10 in Ghost Eye tool). As the name suggests traceroute, means tracing the path. Traceroute is a network-based utility that shows the path over the network between two systems and lists all the intermediate routers to get to the final destination. The main purpose of traceroute is to fix network problems. This helps you in identifying while connecting to some network where the connection is actually slowing down, which intermediate router is responsible for that.
Using the internet to connect to anything that’s not on your local network or handled by your internet service provider traceroute tracks the route packets taken from an IP network on their way to a given host. It utilizes the IP protocol’s time to live (TTL) field and attempts to elicit an ICMP TIME_EXCEEDED response from each gateway along the path to the host.
When reviewing your results, you’ll see the following information for the path:
- The number
- The amount of time it took for each of the three tries in milliseconds
- The IP address of the node at that hop
- The domain name (if available).
Ghost Eye video
Ghost Eye Information Gathering – Footprinting and Reconnaissance Tool
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.