Google Dorks an Easy Way of Hacking
Google Dorks
Google Dorks A frequently asked question to me, “Where should I start learning how to hack ?”. And every time, the first thing I want to answer is: “Why don’t you start by using Google ?”. Personally, Google is one of my best friends in Hacking, and I’m sure Google will be yours too after reading this article.
All you need to carry out to move further with “Google Dork”, is a computer, an internet connection, and knowledge of the appropriate search syntax. A number of examples are given down below and if you need more, you can visit Github, a large number (10.000) of Google Dork can be found here.
How it all started..
The concept of “Google Hacking” dates back to 2002 when Johnny Long began to collect interesting Google search queries that uncovered vulnerable systems and sensitive information, labeling them Google Dorks.
“In the years I’ve spent as a professional hacker, I’ve learned that the simplest approach is usually the best. As hackers, we tend to get down into the weeds, focusing on technology, not realizing there may be non-technical methods at our disposal that work as well or better than their high-tech counterparts. I always kept an eye out for the simplest solution to advanced challenges ~ Johnny Long 2011.
What data can we find using google dorks?
- Username and passwords
- Admin login pages
- Sensitive documents
- Govt/military data
- Email lists
- Bank account details
- Vulnerable websites
- So much more …
Google Dorks is a search that uses one or more of these advanced techniques to reveal something interesting. Something important to keep in mind, the web can be crawled by anyone. Google automatically indexes a website, and unless sensitive information is explicitly blocked from indexing (nofollow, robots.txt), all of the content can be searched via Dorks or advanced search operators.
Most of the time, users might post the link, not realizing what they’ve shared. This information will be exposed to the “referrer” header. Consider a web page: “wp-content/uploads/private””, if the browser needs to make a request to another domain to render this web page (for instance, to download an image), a header will be included: “Referer: http://yourdomain.com/wp-content/uploads/private”.
How to use Google dorks
cache: Google will highlight words within the cached document. For instance, [cache:www.google.com] web will show the cached content with the word “web” highlighted. This functionality is also accessible by clicking on the “Cached” link on Google’s main results page. The query [cache:] will show the version of the web page that Google has in its cache.
link
The query [link:] will list web pages that have links to the specified web page. For instance, [link:www.google.com] will list web pages that have links pointing to the Google homepage. Note there can be no space between the “link:” and the web page URL.
related
The query [related:] will list web pages that are “similar” to a specified web page. For instance, [related:www.google.com] will list web pages that are similar to the Google homepage. Note there can be no space between the “related:” and the web page URL.
info
The query [info:] will present some information that Google has about that web page. For instance, [info:www.google.com] will show information about the Google homepage.
define
The query [define:] will provide a definition of the words you enter after it, gathered from various online sources. The definition will be for the entire phrase entered (i.e., it will include all the words in the exact order you typed them).
stocks
If you begin a query with the [stocks:] operator, Google will treat the rest of the query terms as stock ticker symbols and will link to a page showing stock information for those symbols. For instance, [stocks:intc yhoo] will show information about Intel and Yahoo. (Note you must type the ticker symbols, not the company name.)
site
If you include [site:] in your query, Google will restrict the results to those websites in the given domain. For instance, [help site:www.google.com] will find pages about help within www.google.com. [help site:com] will find pages about help within “.com” URL.
allintitle
If you start a query with [allintitle:], Google will restrict the results to those with all of the query words in the title. For instance, [allintitle:google search] will return only documents that have both “google” and “search” in the title.
intitle
If you include [intitle:] in your query, Google will restrict the results to documents containing that word in the title. For instance, [intitle:google search] will return documents that mention the word “google” in their title, and mention the word “search” anywhere in the document (title or no).
inurl
If you include [inurl:] in your query, Google will restrict the results to documents containing that word in the URL. For instance, [inurl:google search] will return documents that mention the word “google” in their URL, and mention the word “search” anywhere in the document (url or no). Note there can be no space between the “inurl:” and the following word. Putting “inurl:” in front of every word in your query is equivalent to putting “allinurl:” at the front of your query: [inurl:google inurl:search] is the same as [allinurl:google search].
Some small examples of Google Dorks
- intitle:the title you are looking
- inurl:the website URL you are targeting
As per the examples mentioned above, you can use the same way Google Dork as follows:
- site:
- phonebook:
- maps:
- book:
- info:
- movie:
- weather:
- link:
Google dorks lists
I have stored on GitHub a complete list of up to 14.000 different Dorks. If you want to clone this Dork to your machine you can do it using the below commands.
Once cloned you can use nano, vim, cat or any other text editor to view and edit it
| |
| |
| |
Some examples of dangerous, useful and funny Dorks
Finding PDF Files with Google Dorks
| |
| |
| |
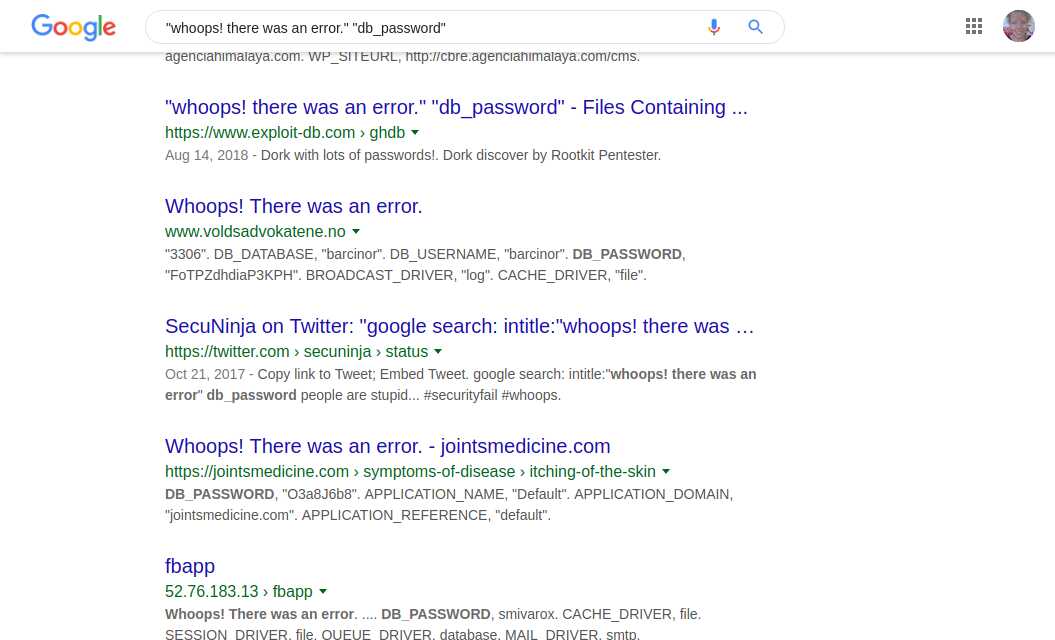
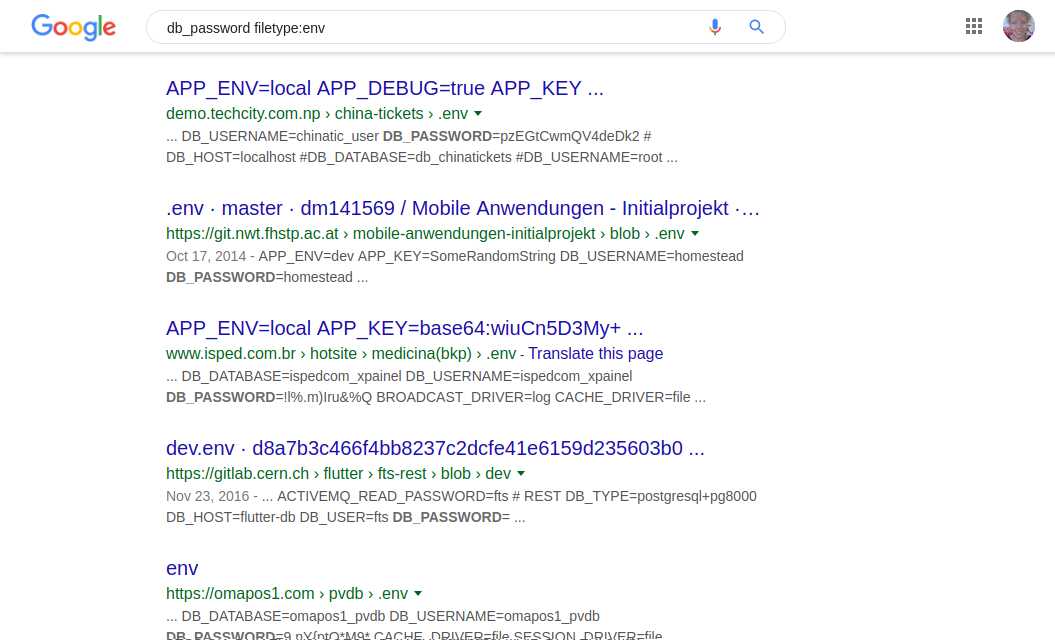
Personally I highly recommended you to never put your .env files in the web-server directory. As you can see, this can cause serious damage.
| |
| |
With this Dork search, you can find website information as per the below screenshot. It’s something very common to find passwords, website credentials details and even login of payment systems such as PayPal.

Budgets on the US Security website
| |
| |
| |
| |
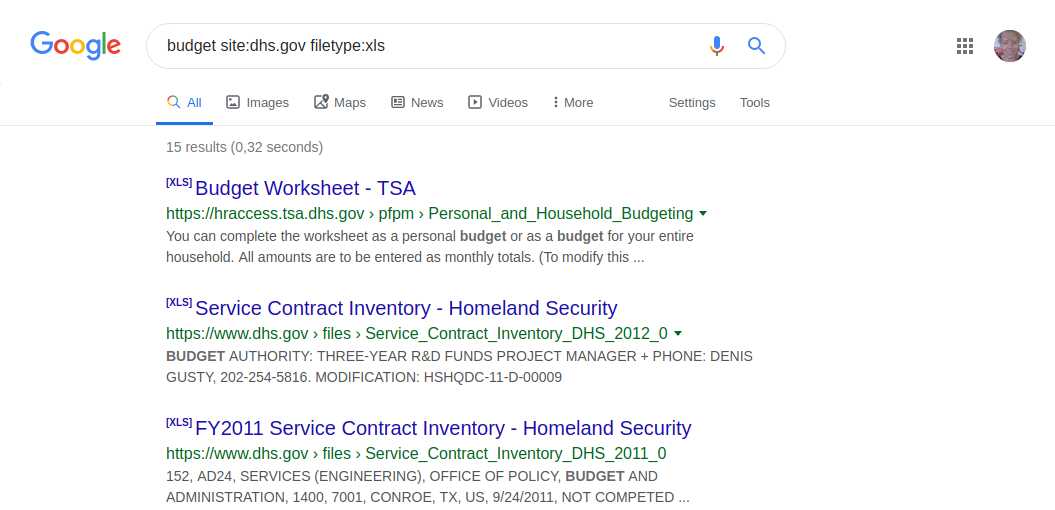
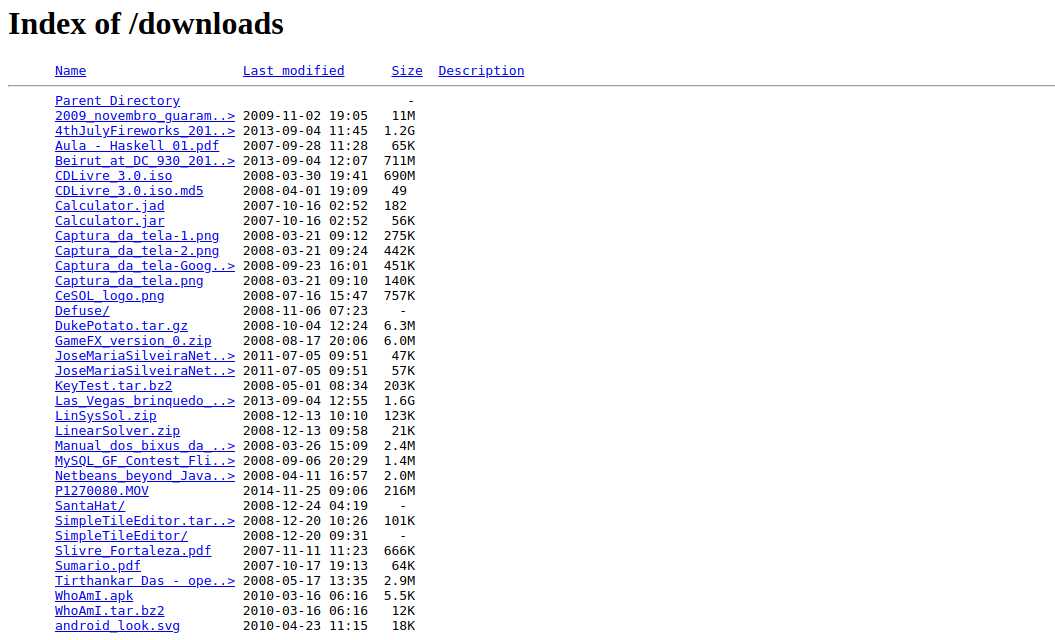
Finding Directory:
Finding directories can be something very interesting when auditing, since in them you can find files with sensitive information. Through Google Dork, you can find a directory indexed in google that otherwise would go unnoticed.
| |
| |
| |
| |
| |
| |
| |
Vulnerability SQL injection:
Once you search the website using the above dorks, now its time to check whether the website is vulnerable to SQL injection or not, we simply put in a quote " ; " at the end of the URL address. So our site URL will look like this, http://www.site.com/index.php?id=123;
Protect your privacy
In August 2014, the United States Department of Homeland Security (DHS), the FBI and the National Counterterrorism Center issued a bulletin warning agency to guard against the potential for Google Dork on their sites.
If you’re using Google Dork in a country with heavy internet surveillance, it’s possible that your searches could be recorded and used against you in the future. As a protection, we recommend using the Tor Browser or any Anon Surf when you’re using Google Dork. Tor masks your internet traffic and block webpages accessing information about your machine. This article explains to you how to hide your IP while browsing the web using TorPhantom.
Google is blocking me
If you start getting HTTP 503 errors, Google has rightfully detected you as a bot and will block your IP for a set period of time. The solution is to use proxychains.
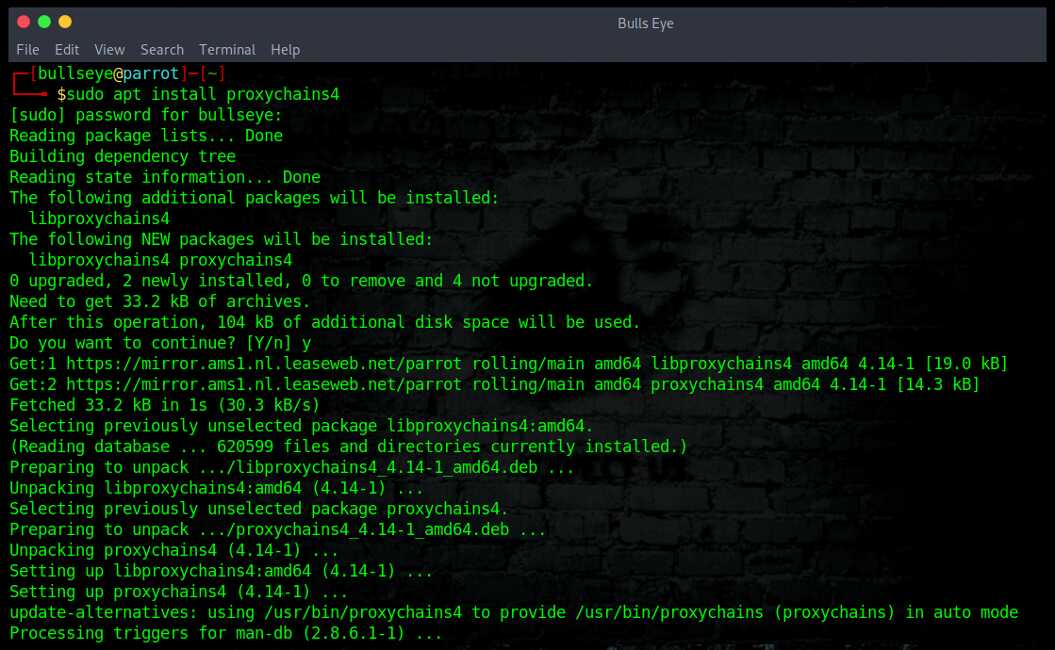
Install Proxychains4 on Debian and derivated distributions
| |
Output
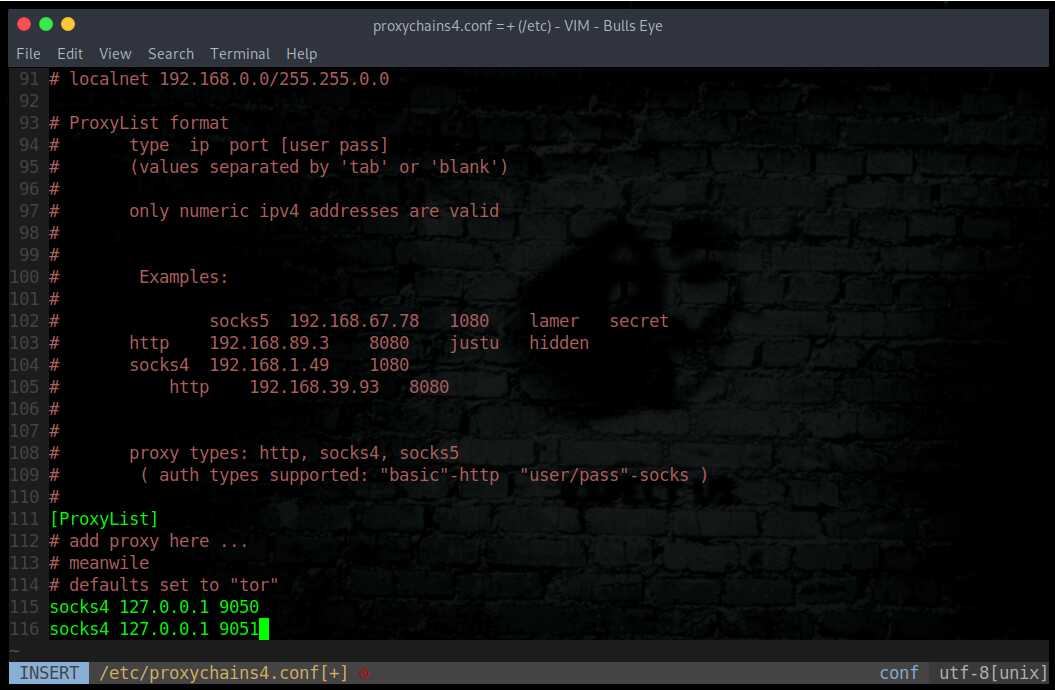
Edit the /etc/proxychains4.conf configuration file to round robin the look ups through different proxy servers. In the example below, 2 dynamic socks proxies have been set up with different local listening ports (9050 and 9051).
| |
Or
| |
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
* You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.