GootLoader Tricks Security Tools Into Seeing a Safe File While Windows Runs Malware
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
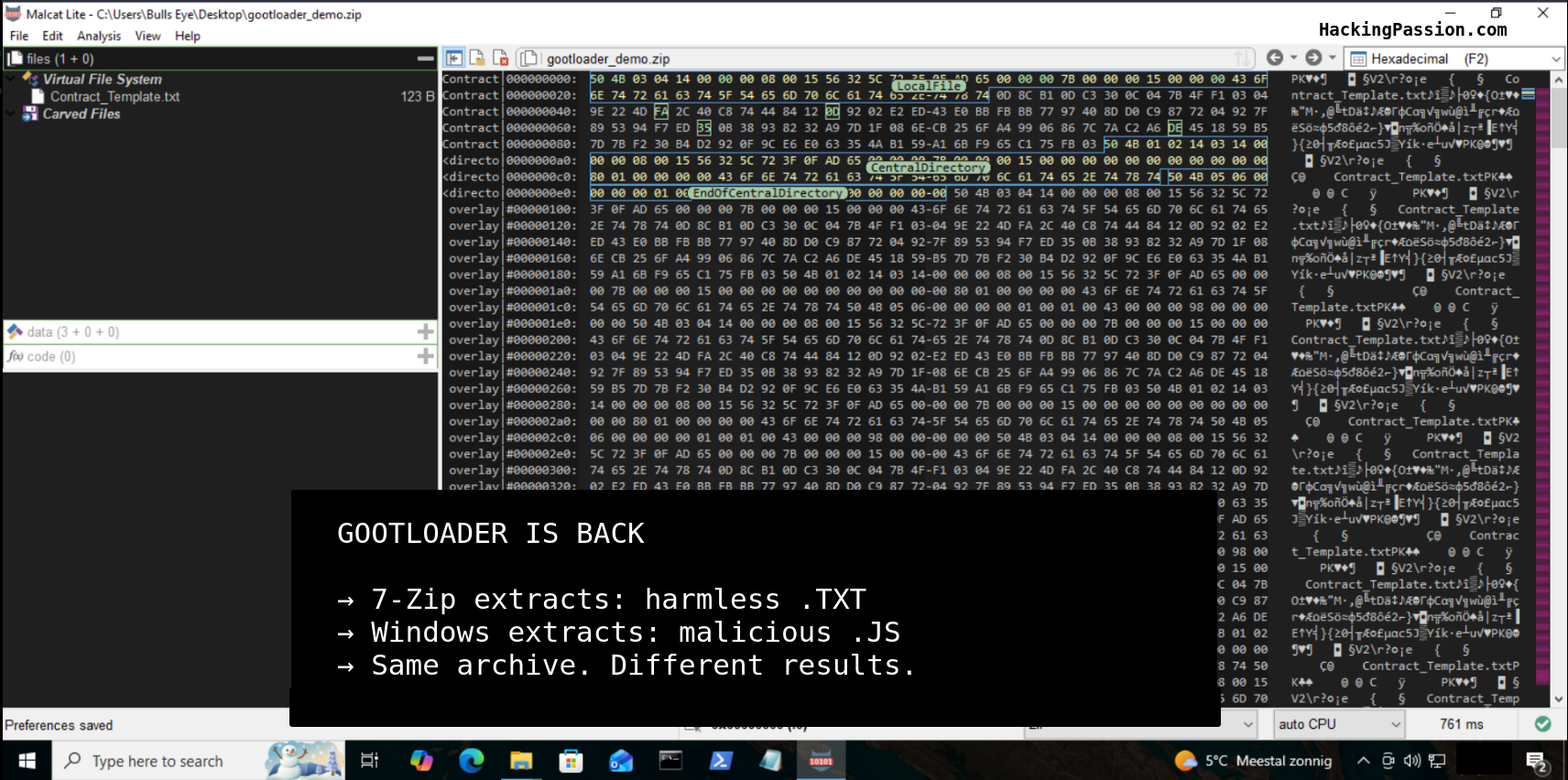
GootLoader is back. This week, researchers discovered their newest trick: a way to make security tools completely blind. Your antivirus scans the ZIP file. Nothing found. WinRAR tries to open it. Fails. 7-Zip tries. Also fails. Corrupted file, right? But when you double-click it, Windows opens it just fine. And now you’re infected. 🧐
The trick is simple but brilliant. They take 500 to 1000 ZIP files and glue them together into one massive file. Most analysis tools read ZIP files from the beginning. They hit the first archive, see garbage, and crash. But here is the thing about ZIP files. They are actually read from the END. The “End of Central Directory” record tells the reader where to find the actual content. Windows knows this. It skips all the junk, finds the last valid archive, and happily extracts the malware.
But they did not stop there.
They deliberately break specific bytes in the file structure:
- → The End of Central Directory is missing two critical bytes that parsers need
- → The “Disk Number” fields are randomized, so tools think the ZIP is split across multiple disks that do not exist
- → The CRC32 checksum is wrong on purpose, making tools think the file is corrupted
Open the ZIP with 7-Zip and it extracts a harmless .TXT file. Open the exact same ZIP with Windows Explorer and it extracts a malicious .JS file. Same archive, different tools, completely different results. Automated security analysis sees a text file and moves on. The victim sees JavaScript and runs it.
Every single download is unique. When a victim clicks that download button, the browser receives an XOR-encrypted blob. The browser then BUILDS the ZIP file itself by decoding and copying that blob hundreds of times. No two victims ever receive the same file. Hash-based detection is completely useless. Network-based detection sees encrypted garbage, not a ZIP file.
They abuse WordPress sites and hide their payload in the comment submission endpoint at /wp-comments-post.php. When someone clicks download, the malicious data comes from what looks like a normal WordPress function.
Before the victim even sees the filename, they have already been tricked. The webpage shows "Contract_Template.pdf" but the source code contains complete gibberish like "›μI€vSO₽*'Oaμ==€‚‚33O3". They embed a custom WOFF2 font file directly in the JavaScript using Z85 encoding, a Base85 variant that compresses the 32KB font into 40K of code. The font metadata says the letter “O” maps to the glyph named “O”. But they swapped the actual vector paths. The shape that renders on screen is completely different. Security tools scanning the source code see nonsense. The browser renders a clean filename.
The infection chain moves fast.
- → You search for “contract template” or “NDA agreement” on Google
- → A compromised WordPress site appears in the top results
- → Looks like a helpful forum, someone posted exactly what you need
- → You click download, the ZIP opens fine in Windows
- → Inside is a JavaScript file that looks like a legal document
- → You double-click it
Game over!
The JavaScript runs via wscript.exe from the Temp folder. It drops a shortcut file in the Startup folder, but not pointing directly to the malware. The shortcut points to ANOTHER shortcut in a random folder, which then points to a second JavaScript file. They use NTFS 8.3 short filenames like FILENA~1.js to hide the real path. Legacy naming from 1993 being used to evade modern security tools.
Those shortcut files have keyboard hotkeys assigned. CTRL+ALT+M or CTRL+ALT+G. If you accidentally hit that key combination at any point, the malware executes again.
Within 20 minutes, the attackers deploy the Supper backdoor, a SOCKS5 proxy that gives them remote access. They start reconnaissance immediately. Kerberoasting. SPN scanning. Looking for paths to the Domain Controller.
Within 17 hours, they own it. Sometimes just one hour.
The group behind this has been around since 2014. They started as GootKit, a banking trojan targeting banks across Europe. In 2019 they suffered a data leak and went quiet. In 2020 they came back as GootLoader, pivoting from stealing bank credentials to selling network access to ransomware gangs.
Security researchers track them as Storm-0494, Hive0127, or UNC2565 depending on who you ask. But here is the thing about attribution. In cybersecurity, attribution is one of the hardest problems. IP addresses can be spoofed. Tools can be shared. Languages in code can be faked. What we know for sure is how the malware works, not necessarily who is behind it.
What researchers do agree on is that they do not deploy ransomware themselves. They sell access. Their current partner is Vanilla Tempest, also known as Vice Society, the group behind Rhysida ransomware that has been hitting hospitals across the US. McLaren Health Care. NHS Scotland. Healthcare is their favorite target.
A security researcher operating under the name “Gootloader” tracked this group for years. Filing abuse reports. Contacting hosting providers. Getting their infrastructure taken down. On March 31, 2025, his efforts paid off. The entire GootLoader operation went dark.
Seven months later, they came back with all these new tricks.
In previous years, GootLoader malware made up 11 percent of all malware that bypassed other security tools. One in ten. That is how good they are at evading detection.
The ransomware connections run deep. GootLoader has delivered initial access for REvil, BlackCat, Rhysida, INC Ransomware, Zeppelin, and Quantum Locker.
Who are they targeting now?
- → Law firms searching for legal templates
- → Healthcare organizations
- → Finance
- → Education
- → Manufacturing
Mostly in the US, UK, Australia, Canada, Germany, and France.
How to protect yourself.
Change your Group Policy so JavaScript files open in Notepad instead of executing. This one change stops the entire attack chain. If someone double-clicks a malicious JS file, they just see code instead of running malware.
Block wscript.exe and cscript.exe from running downloaded content if your business does not need them.
Watch for these warning signs:
- →
wscript.exerunning JavaScript from the Temp folder - → Shortcut files appearing in the Startup folder pointing to strange locations
- → CScript spawning PowerShell which spawns another PowerShell
- → Unusual Active Directory enumeration activity
- → Shortcuts with keyboard hotkeys assigned
The speed of this attack is what makes it dangerous. From first click to domain takeover in under a day. Most organizations cannot detect lateral movement that fast.
Expel released a YARA rule to detect these malformed ZIP files. It looks for more than 100 occurrences of the same local file header and more than 100 End of Central Directory records. Normal ZIP files have one of each.
Security tools see a corrupted file. Windows sees an opportunity to help. And that gap is exactly where GootLoader lives.
Hacking is not a hobby but a way of life. 🎯
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.