How to Hack and Exploit Printers in Seconds
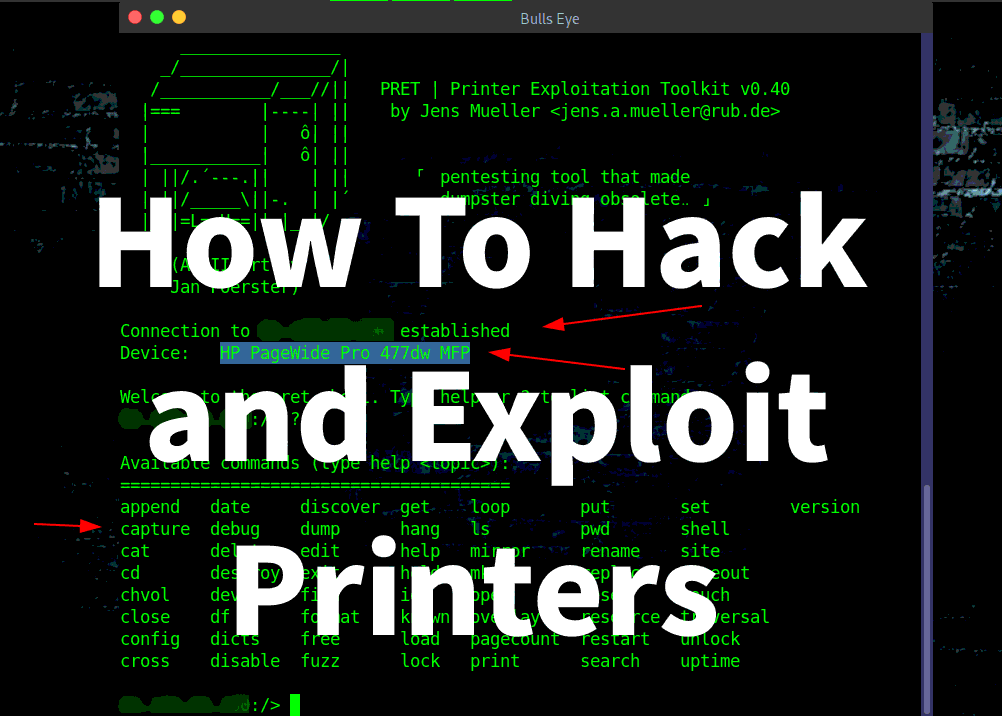
A Step-by-Step walkthrough..! In this article and video, I will show you how to hack and exploit printers. How easy it is to hack, how to get full control, capture, and start sending documents our way. So all future print jobs that are going to come across the printer we’ve connected to which are going to start spooling over.
Why I chose to show you this
Again… I chose to show you this, because it is so incredibly easy to hack printers, and through this hack to get further in systems and can cause incredible damage. Secret documents or whatever.
Here you can find the post about the Security Webcam Hacking As you see this is also incredibly simple to hack.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
I feel it as my mission that people and certainly also the companies and governments become aware of the safety risks. How to protect this “In this case the” (Printers) I hope SOMEDAY this will be captured and that much attention will be paid to it.
I will continue to make things like this public..! Because there is a long way to go. As for me, this is only child play.
Who would put a printer on the Internet?
After all, it is not just the normal household that is only at risk with these types of hacks, but as you can possibly imagine, I am also talking here about companies and governments and more that pay little attention to safety. What at a certain point in time can become very “expensive”.
Make passwords different for every device you use including each app or website login
Are you as secure as you think?
When was the last time you changed your computer or the device passwords? Do you have a different password for each? And what about your printer?
It may be hard to believe but less than 2% of printers in use today are intrusion-proof. Most people do not change the default password at installation and giving hackers with this easy access to embedded system data, network information.
The key is to think of all of your devices at home and at work as mini-computers

How to secure your printer
Here are some examples to secure your printer and that you should consider when using a printer that is connected to the internet.
Change the default password of your printer
Change the default password immediately upon printer installation and use a complex and lengthy password.
Check your printers IP addresses
By default you may find that your printer has an external IP address; unless there’s a very good reason for keeping it that way, switch to an internal IP address. For extra security, consider limiting access to a specific LAN or subnet.
Secure your ports
Many printers allow jobs to be submitted to the print queue through SMTP, FTP, Telenet and USB ports. Regrettably, the same protocols and the network ports used to service them can be used by attackers as a means of retrieving documents, data, and information. If you don’t need them, disable them using the Web management interface to cut back the potential for an attack.
Apply the latest firmware updates
Every printer company that cares about security updates the firmware on printers in the wake of any discovered vulnerability. Make sure you always download the latest version from your manufacturer’s website. This may contain fixes for serious security issues or new features that could make your printers more secure.
Tools we install and use for hacking the printers
I will show you how to install Anonsurf on Kali Linux. (This feature is already installed on Parrot OS,) I also show you how to set up and use Shodan Eye, (a tool I made) works very well for these hacks. How it gives added value to use it in this way. How to install and the use of the Printer Exploitation Toolkit (PRET)
Install pip
Before we install the tools, especially if you have just installed a new Linux installation. Make sure that pip is installed.
Python 2.7
|
|
For Python 3 is the command:
|
|
Put both commands in one line, this will save you some time
|
|
As you see both pip install are already done on this PC.
Install AnonSurf
What is AnonSurf
Being anonymous for a hacker is the first step before hacking a system. Anonymizing a system in an ideal way is not an easy thing.
Always remember that no one can perfectly anonymize a system.
Anonsurf is a tool that will help you stay anonymous by routing every packet through the TOR relay. When you use Anonsurf for ethical hacking, all the traffic from your system goes through a TOR proxy server due to which your IP address is changed.
How to install AnonSurf on Kali Linux
A part of ParrotSec’s stealth and anonsurf modules to Kali Linux
This repo contains the sources of both the anonsurf and pandora packages from ParrotSec combined into one.
Install:
This package comes with an installer that makes things extremely easy
|
|
|
|
|
|
Parrot AnonSurf Module Usage:
|
|
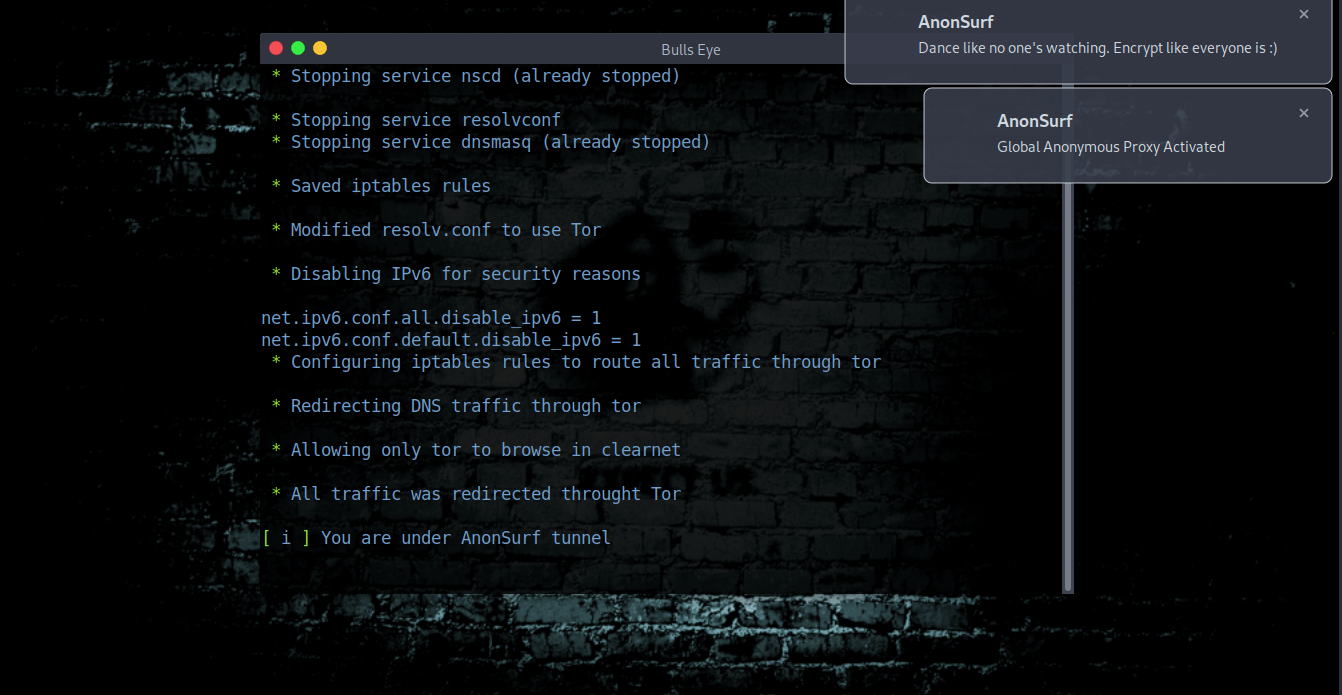
sudo anonsurf start
Anonsurf on Parrot OS
" Dance like no one’s watching
Encrypt like everyone is "
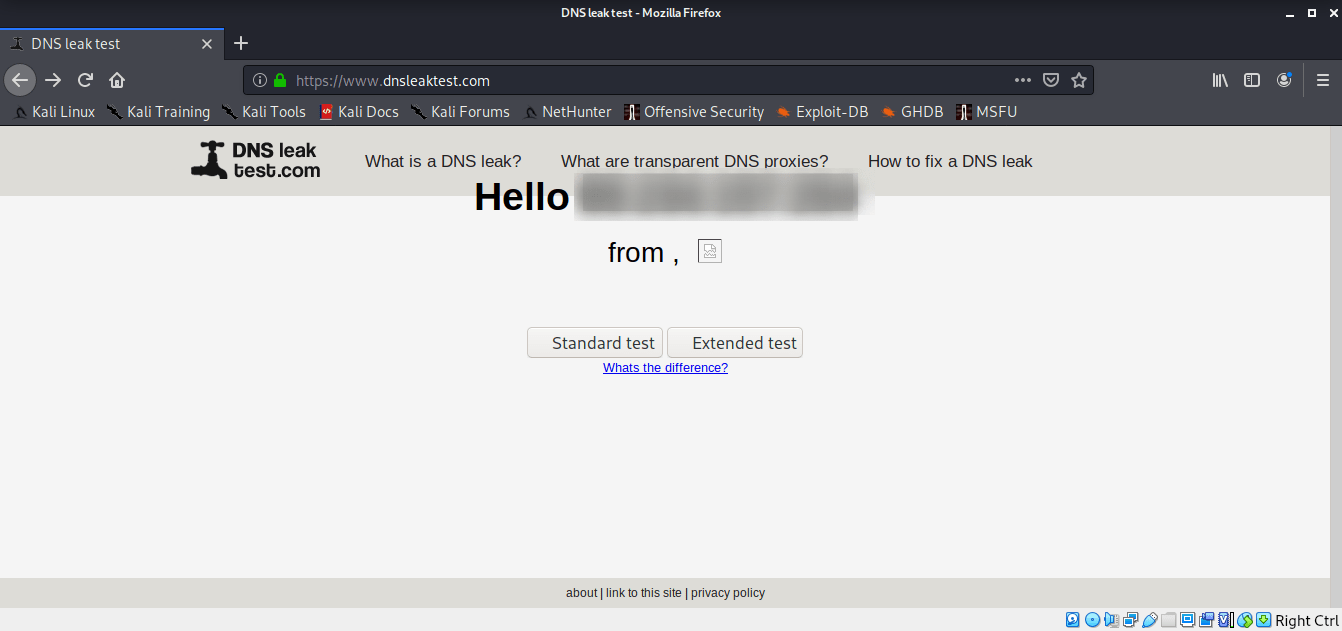
DNS Leaks test to see if you are anonymous
After the AnonSurf installation, you can find out if you are anonymous, true this link. DNS leak test
This is a simple but very effective way to find out.

Shodan Eye
Shodan Eye is a tool I make in python3. This tool can find every device that is connected to the internet. For more information about Shodan Eye, you can follow click here.
Install
|
|
|
|
|
|
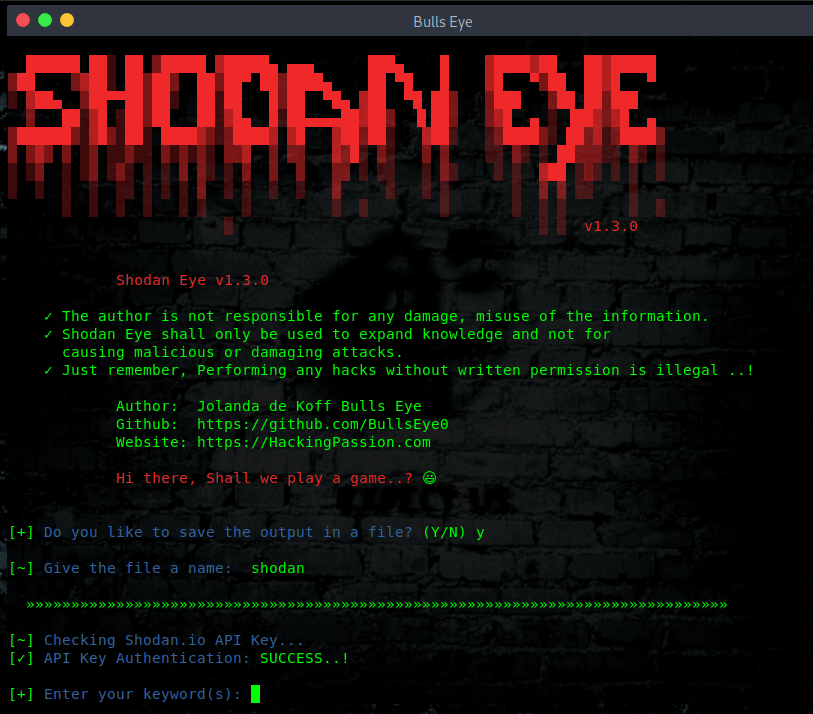
How to use Shodan Eye
(You will be asked for a Shodan API key)
|
|
A Shodan API key can be found here: https://account.shodan.io/register
Printer Exploitation Toolkit (PRET)
Is your printer secure? Check before someone else does…
Hack and exploit printers
The main idea of PRET is to facilitate communication between the end-user and the printer. Thus, after entering a UNIX-like command, PRET translates it to PostScript, PJL or PCL, sends it to the printer, evaluates the result and translates it back to a user-friendly format. PRET offers a whole bunch of commands useful for printer attacks and fuzzing.
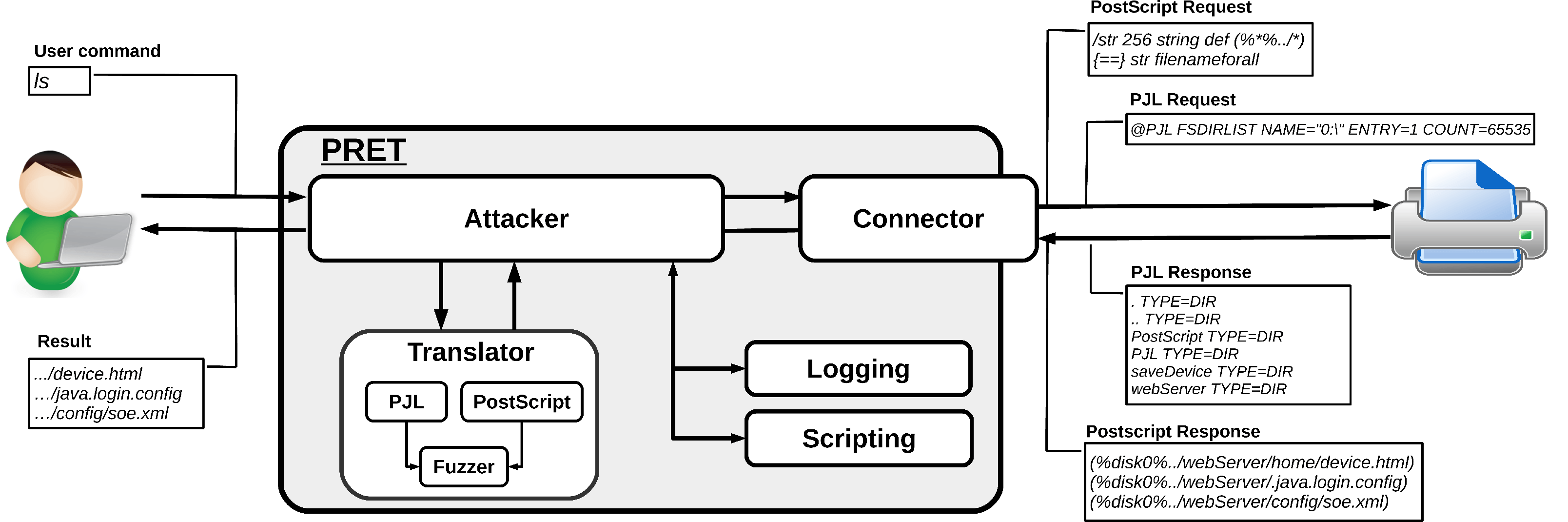
Installation PRET
PRET only requires a Python2 interpreter. For colored output and SNMP support however, third party modules need to be installed:
|
|
If running on a Windows console and Unicode characters are not displayed correctly, install the win_unicode_console module:
|
|
For experimental, ‘driverless’ printing (see print command), ImageMagick and GhostScript need to be installed:
|
|
If you have installed all of this then install the tool
|
|
|
|
Example usage PRET:
|
|
|
|
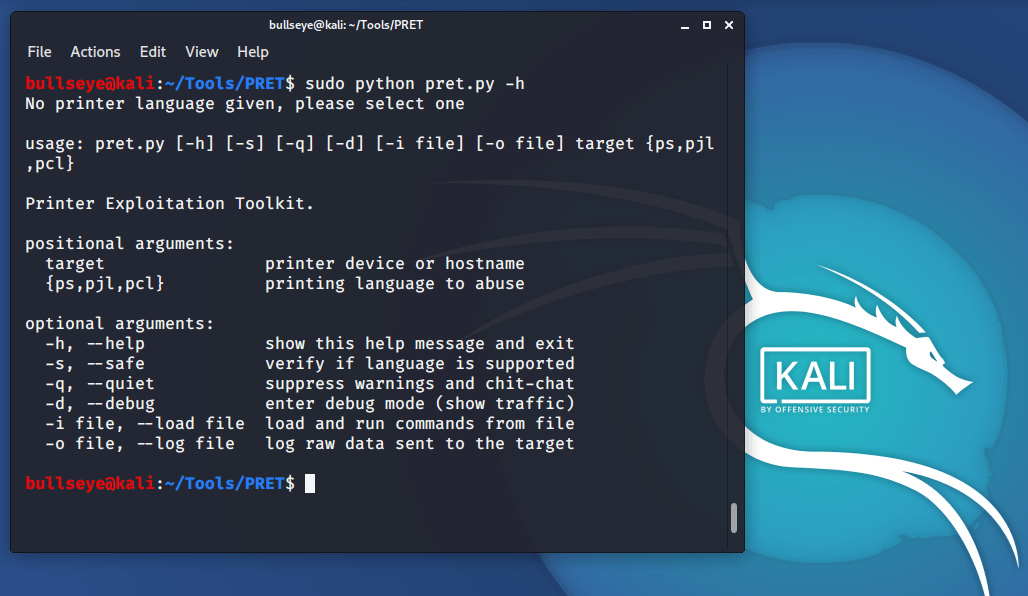
|
|
|
|
A list of generic PRET commands is given below:
|
|
For further explanation about PRET, I want to refer you to the GitHub page because there is a lot to find about this amazing tool.!
Before I continue, I want to mention the Disclaimer. Read this carefully..!
Hack and Exploit Printers
After all the tools have been installed, we can start searching for vulnerable printers. As I have already made clear, there is an incredible number of printers that can be hacked, which can simply be found on the internet - with all the data you are looking for.
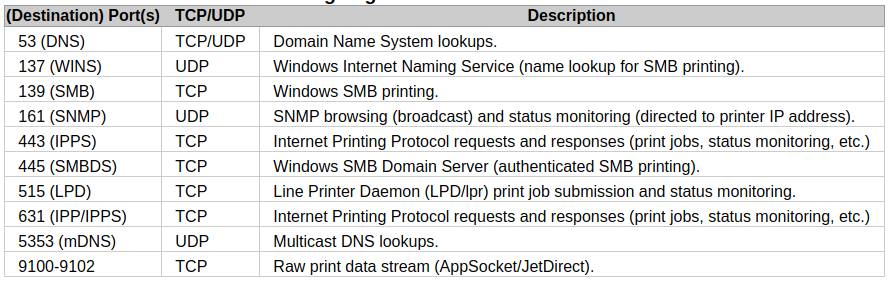
port 9100 = the default port for printers
TCP port 9100 is commonly used by printer manufacturers to provide a raw TCP port for data. Traditionally, printing over TCP/IP has been achieved using LPR (Line Printer Remote) which operates on TCP Port 515 and uses particular commands according to the protocol.
Some vulnerable printers
HP Color LastJet Pro MFP M281fdw
Xerox Phaser 3320
Brother HL-L8360CDW
Kyocera Ecosys M5526cdw
If you continue searching, you would find many more vulnerable printers.
Because “It’s all public” Already..!
For this search I use a simple search, this shows all devices and printers that are connected to this port.
|
|
Search with Shodan Eye
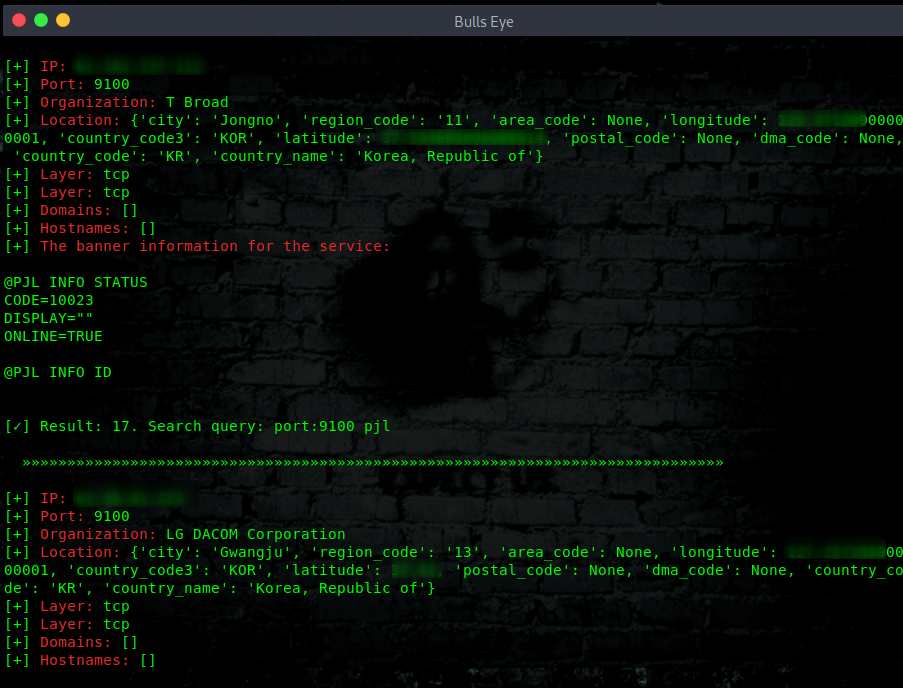
Search with Shodan
Furthermore, I like to mention that you also can do a simple Shodan search for the printers. As you can see, the outcome is much limited as the Shodan Eye tool.
|
|
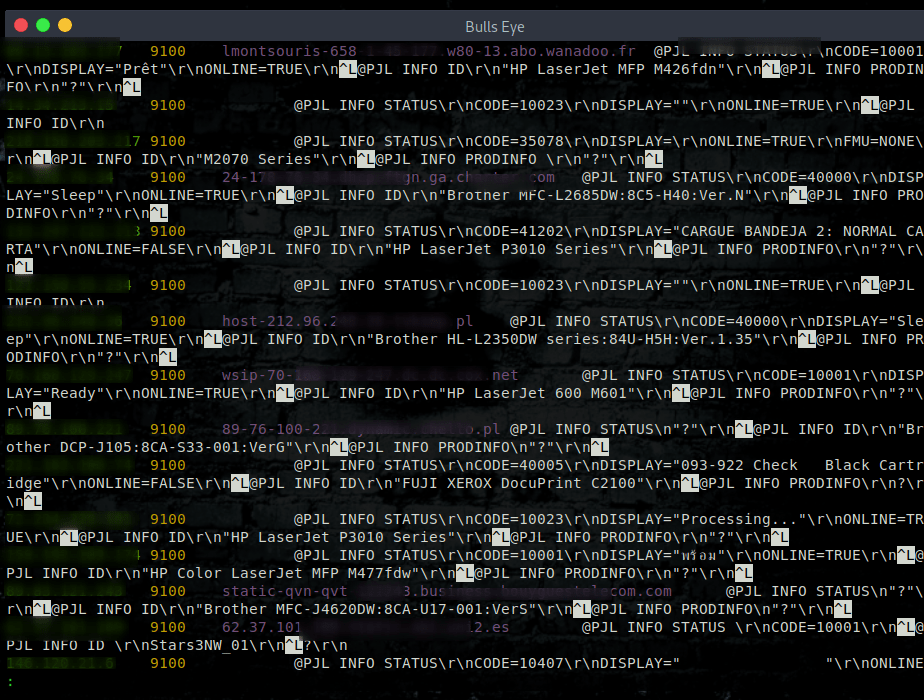
How I easy hack some printers in a few seconds
As you can see in the image below, I have already a lot of information here.
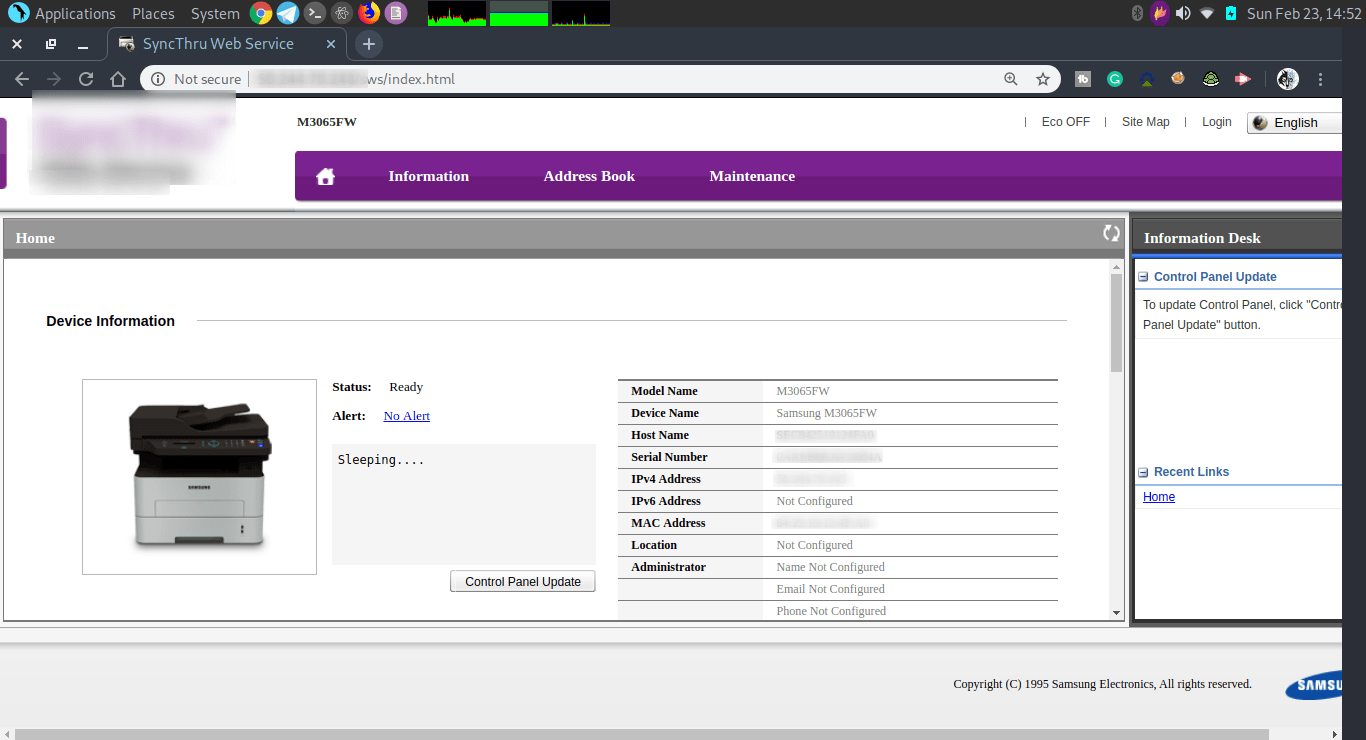
I can do what I want with this printer. And some more ..!
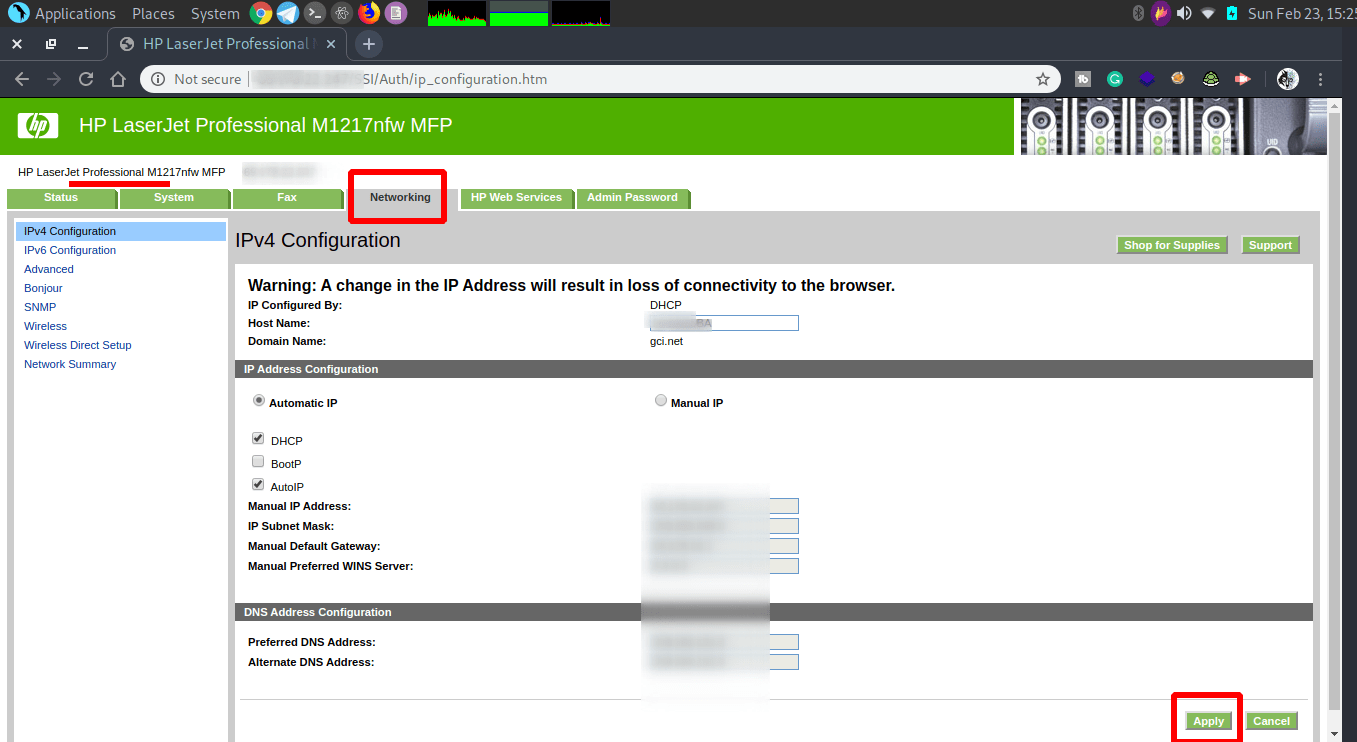
In this last screenshot of a hacked printer, I like the fact that I can personalize the printer. “I won’t” Because this is only for showing how easy it is to hack almost every printer. Or does your printer belong to the 2% I talked about? .. But even then… Hack and exploit printers.
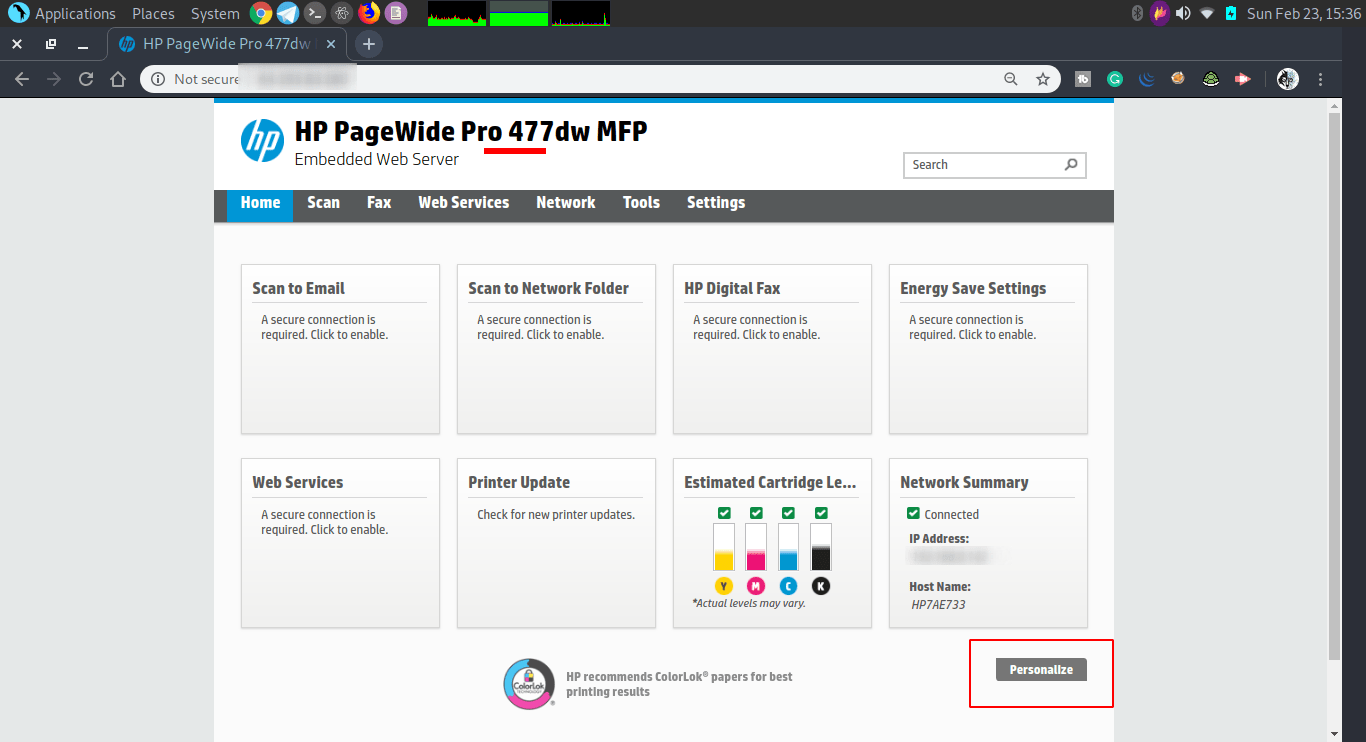
Using PRET and exploit the printer
Here I have exploited the printer (The one above) in a simple way, also within a few seconds.
You now see what is possible. If I want all the prints that will be made in the future, on this printer, then that can be done in a very simple way.
Available commands
append date discover get loop put set version
capture debug dump hang ls pwd shell
cat delete edit help mirror rename site
cd destroy exit hold mkdir replace timeout
chvol devices find id open reset touch
close df format known overlay resource traversal
config dicts free load pagecount restart unlock
cross disable fuzz lock print search uptime
Video
In this video, I show you how to install Anonsurf, Shodan Eye, and Printer Exploitation Toolkit (PRET). I show you how to search for vulnerable printers. What I don’t show you is “How to Exploit them” How this is done you read in the text above.
Become a member on Odysee
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.