How to Use Nmap Nse Scripts to Find Vulnerabilities
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
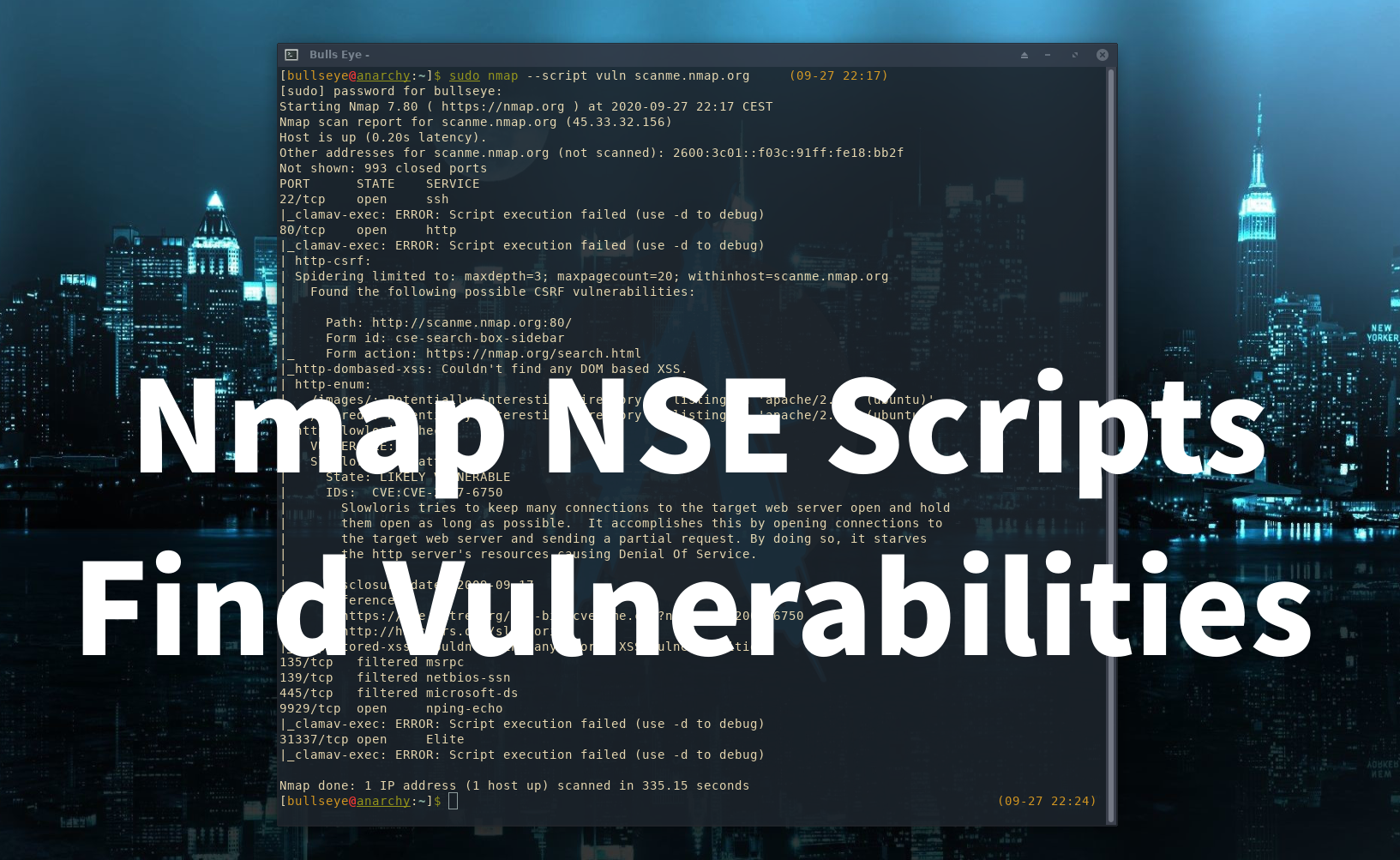
Find Vulnerabilities, Nmap has a lot of features and one of them is a built-in script interpreter called NSE Nmap Scripting Engine.
Nmap is one of the most used and best port scanning tools that exist and is the favorite for many people including for me. But Nmap is not only a port scanner, but this tool is also much more and has so many features. In this article, we highlight the Nmap Script Engine (NSE). Nmap has a lot of features, and one of them is a built-in script interpreter called NSE “Nmap Scripting Engine” Nmap stands for “Network Mapper”
Nmap scripts can be used for:
- Vulnerability detection.
- Vulnerability exploitation.
- Backdoor detection.
- Network discovery.
- More sophisticated and accurate OS version detection.
Before we move any further, take a look at these points:
- Do not execute scripts from third parties without critically looking through them or only if you trust the authors. It’s highly recommended that you do this with every script before you use it. First of all, it’s a good start for your own safety and furthermore it will help you to understand how the script is made and the scripting language used to make it.
- Many of these scripts may possibly run as either a prerule or postrule script. The current standard to choose between a “prerule” or a “postrule” is this: If the script is doing host discovery or any other network operation then the “prerule” should be used. “Postrule” is reserved for reporting of data and statistics that were gathered during the scan.
- Nmap uses the script.db database to figure out the available default scripts and categories.
Install Nmap on Windows
Nmap is available in several versions and formats. Recent source releases and binary packages are described in the download page of the software.
Install Nmap on Linux distributions
Debian based
| |
Arch Based
| |
Red Hat Based
| |
Or
| |
OpenSUSE Based
| |
Fedora Based
| |
Install Nmap using snap package
Amazingly, the Nmap tool is now available in Snap. To install this app via Snap on your system, use the below command.
| |
There are four types of NSE scripts:
Host Scripts
This scripts executed after Nmap has performed normal operations such as host discovery, port scanning, version detection, and OS detection against a target host.
Prerule Scripts
These are scripts that run before any of Nmap’s scan operations, they are executed when Nmap hasn’t gathered any information about a target yet.
Service Scripts
These are scripts run against specific services listening on a target host.
Postrule Scripts
These are scripts run after Nmap has scanned all of its target hosts.
Location of the NSE scripts
Depending on the operating system you use but also depending on the Nmap version installed on your computer, NSE scripts can be in different locations.
For Linux system
| |
Or
| |
For Mac
| |
For Windows
| |
or
if you are using a 32bits version
| |
The path of your NSE scripts folder
For Linux, the easiest way to find the path of your NSE scripts folder is to use the below command in your terminal:
| |
Output
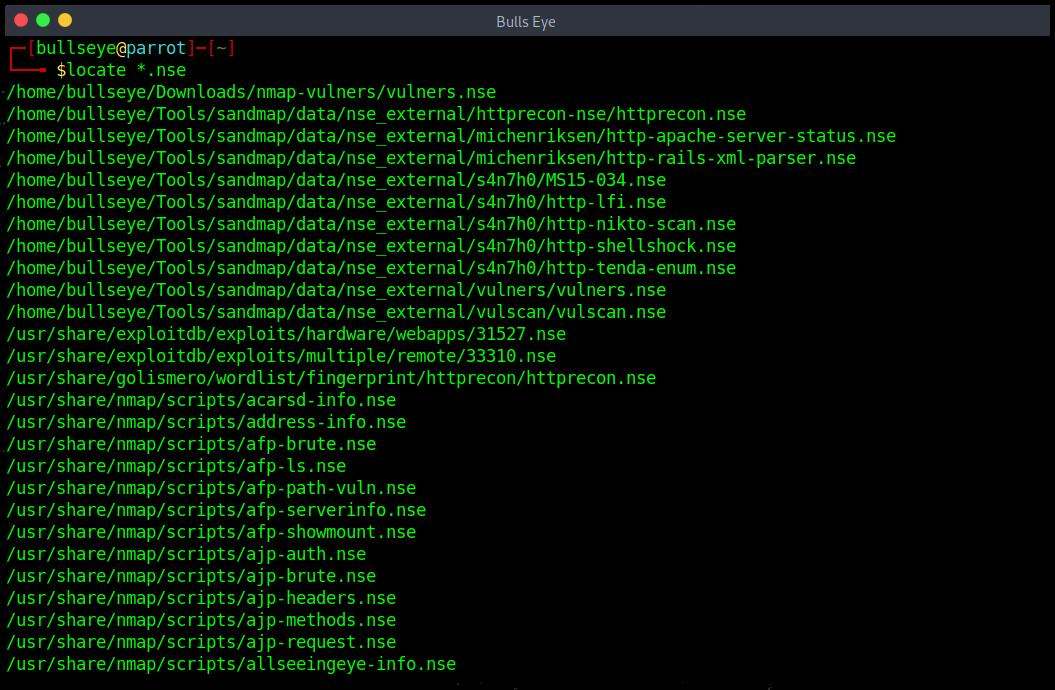
In the above screenshot, we can see that the Nmap NSE Scripts can be found are located:
| |
Maybe you like to know more about Linux commands, you can find them here.
How to install the new NSE Nmap script
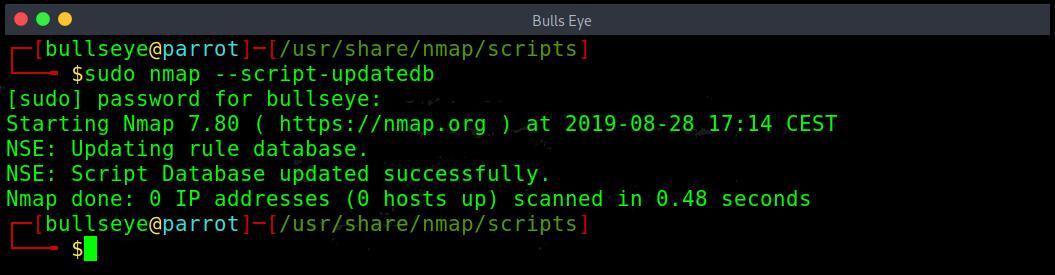
To add new scripts to your script.db database, you simply need to copy your .nse files to the NSE scripts directory in our example referenced by “/usr/share/nmap/scripts”, and run the following command to update the Nmap script database:
| |
Output
Use of the NSE Nmap scripts
You can view the description of a script using --script-help option. Additionally, you can pass arguments to some scripts via the --script-args and --script-args-file options, the later is used to provide a filename rather than a command-line arg. To perform a scan with most of the default scripts, use the -sC flag or alternatively use --script=default.
Hacking vulnerabilities using NSE script
Personally, I use very often many NSE scripts provided by default with Nmap. In addition, you will find below a number of vulnerability scanners that you can add to your Nmap software.
winnti-nmap-script
This Nmap script can be used to scan hosts for Winnti infections. It uses parts of Winnti’s protocol as seen in the wild in 2016/2017 to check for infection and gather additional information.
Github: https://github.com/TKCERT/winnti-nmap-script
How to Use
For Help Type:
| |
For Detection Type
| |
SSL-Heardbleed
Detects whether a server is vulnerable to the OpenSSL Heartbleed bug (CVE-2014-0160).
Download : https://svn.nmap.org/nmap/scripts/ssl-heartbleed.nse
How to Use
| |
Nmap-vulners
NSE script based on Vulners.com API. This NSE script uses this well-known service to provide information about vulnerabilities that may be present on a system.
Github: https://github.com/vulnersCom/nmap-vulners
How to Use
| |
Freevulnsearch
Free Nmap NSE script to query vulnerabilities via the cve-search.org API.
GitHub: https://github.com/OCSAF/freevulnsearch
How to Use
| |
Vulscan
Advanced vulnerability scanning with Nmap NSE. The script does not perform a vulnerability scan by itself, but using the fingerprinting feature (-sV), it can detect the running applications and versions and use this information to lookup keys in some vulnerabilities databases.
Git****hub: https://github.com/scipag/vulscan
How to Use
| |
http-pulse_ssl_vpn.nse
Simple NSE script to detect the Pulse Secure SSL VPN file disclosure breach via specially crafted HTTP resource requests. This exploit reads /etc/passwd as a proof of concept. This vulnerability affect (8.1 R15.1, 8.2 before 8.2 R12.1, 8.3 before 8.3 R7.1, and 9.0 before 9.0 R3.4).
Github: https://github.com/r00tpgp/http-pulse_ssl_vpn.nse
How to Use
| |
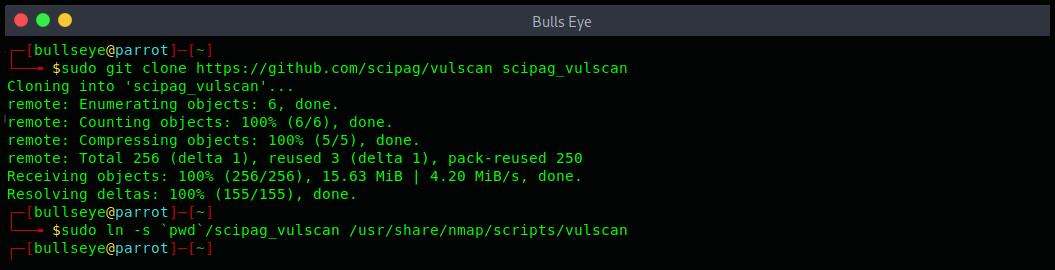
An example of installing Nmap Vulscan:
In order to follow the below example, you will need to open your terminal and type the following commands:
| |
| |
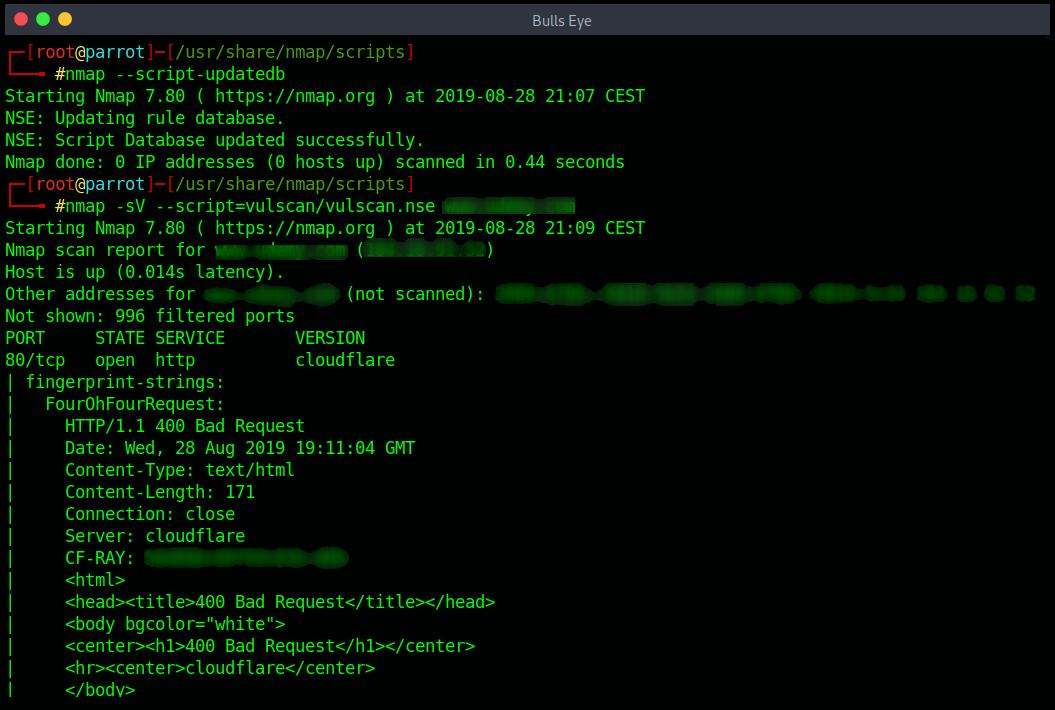
| |
Hacking the NSE Libraries
Libraries often accidentally make use of global variables when a local scope was intended. The scripts that make use of library functions which unintentionally use the same global variable will find that variable constantly rewritten.
This is a very serious bug that can cause NSE to stall or a correct script to spectacularly fail. Another common bug is due to the use by Lua of global-by-default scope assignment when it encounters a variable.
Consider a global variable being used by two different scripts, within the library, to hold sockets or data. When one script is yielded after storing data in the variable, another script awakens only to replace that data. In contrast, a local variable would store the information on the stack of the running script separate from others.
To help correct this problem, NSE now uses an adapted library from the standard Lua distribution called strict.lua. The library will raise a runtime error on any access or modification of a global variable that was undeclared in the file scope. A global variable is considered declared if the library makes an assignment to the global name in the file scope.
If you areplanning to write a Nmap NSE script yourself
Then these NSE Libraries can help you further. All scripts used by NSE are written in an embedded scripting language called Lua.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.