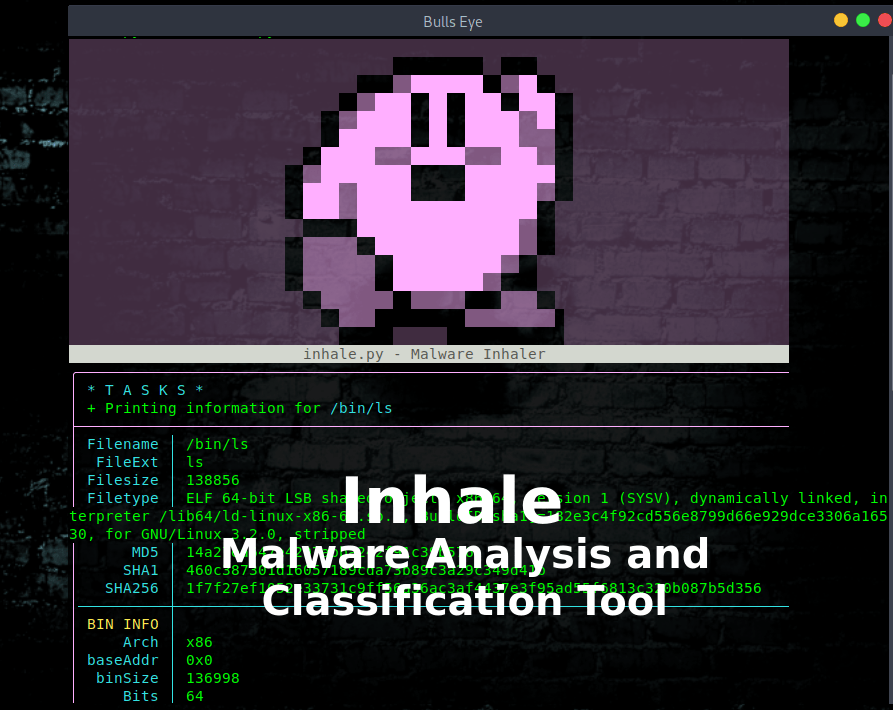
Inhale Malware Analysis Classification Tool
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Inhale is a malware analysis and classification tool that is capable of automating and scaling many static analysis operations.
This is the beta release version, for testing purposes, feedback, and community development. Thanks to netspooky The developer of this amazing tool.
Background
https://github.com/netspooky/inhale#background
Inhale started as a series of small scripts that I used when collecting and analyzing a large amount of malware from diverse sources. There are plenty of frameworks and tools for doing similar work, but none of them really matched my workflow of quickly finding, classifying, and storing information about a large number of files. Some also require expensive API keys and other services that cost money.
I ended up turning these scripts into something that people can quickly set up and use, whether you run from a research server, a laptop, or a low-cost computer like a Raspberry Pi.
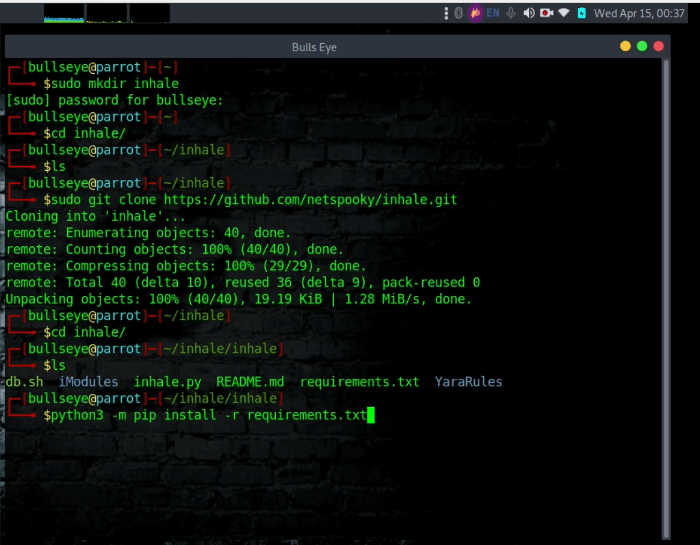
Install Inhale
This tool is built to run on Linux using Python3, ElasticSearch, radare2, yara, and binwalk. jq is also needed to pretty print output from the database. Here are some of the basic instructions to install.
Install Inhale Python3 Install requirements
| |
| |
| |
After Inhale is installed, the following tools must all be installed in Inhale before you can use this tool properly.
Also in the video, you can see in detail how to do all this.
Video: Inhale - Malware Analysis and Classification Tool
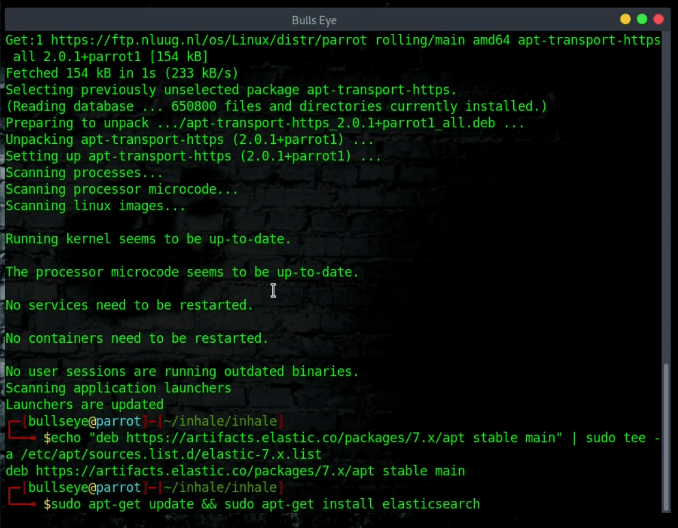
Installing ElasticSearch (Debian)
| |
| |
| |
| |
| |
ElasticSearch Documentation**
**You can also install manually by following this documentation
Additionally, you can set up a full ELK stack for visualization and data analysis purposes. It is not necessary for using this tool.
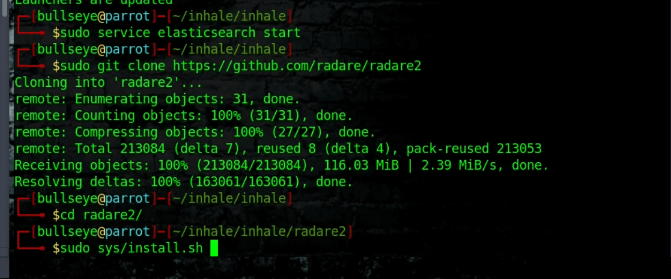
Installing radare2
It’s important to install radare2 from the repo, and not your package manager. Package manager versions don’t come with all the bells and whistles required for Inhale.
| |
| |
| |
Installing Yara
| |
| |
| |
| |
| |
| |
| |
| |
If you get any errors about shared objects, try this to fix it.
| |
| |
Installing binwalk
It’s most likely best to simply install binwalk from the repo.
| |
| |
| |
More information on installing additional features for binwalk is located here.
Inhale Usage
Specify the file you are scraping by type:
| |
Other options:
| |
Examples
Inhale help
| |
| |
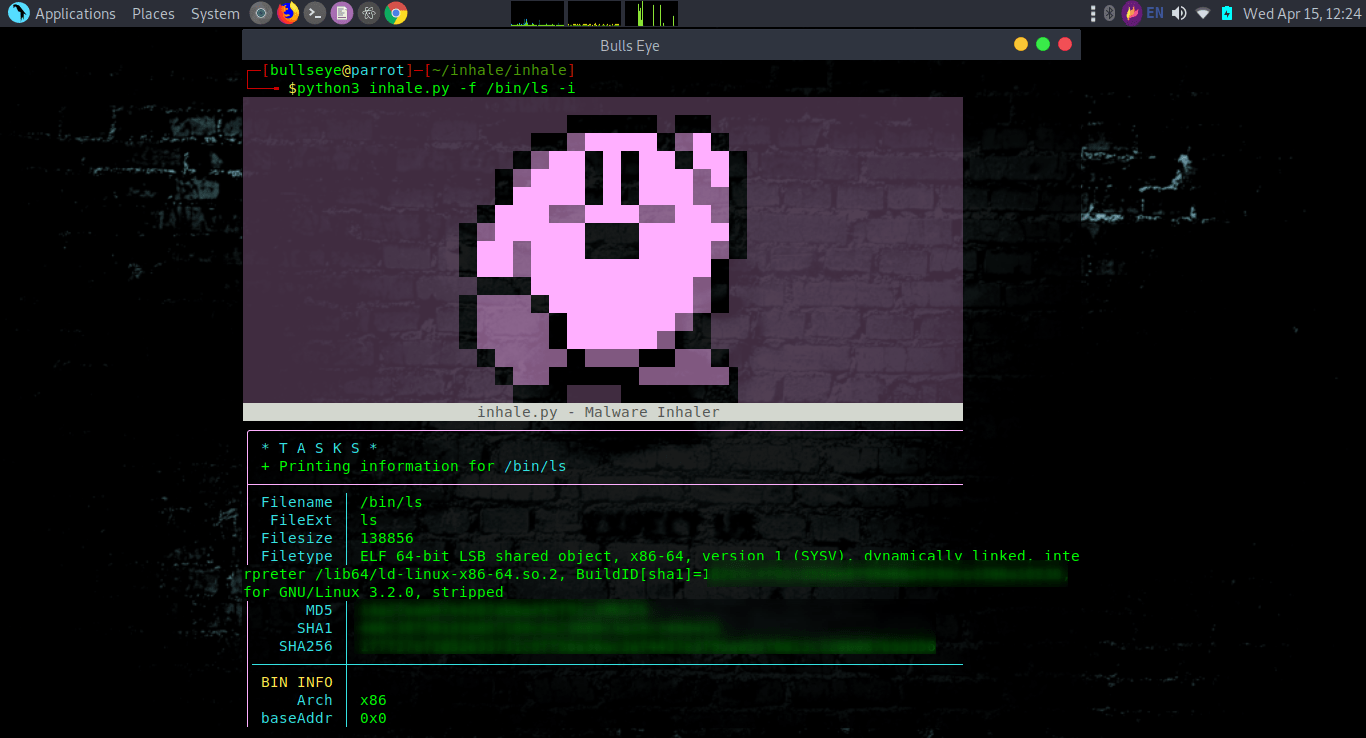
View info on /bin/ls
Running inhale.py will perform all of the analysis on a given file/directory/url and print it to your terminal.
View info on /bin/ls, but don’t add to the database
| |
Add directory ‘malwarez’ to database
| |
Download this file and add to the database
| |
Inhale Download everything in this remote directory, tag it all as “phishing”
| |
PROTIP: Use this Twitter hashtag search to find interesting open directories that possibly contain malware. Use it at your own risk.
Yara
You can pass your own Yara rules with -y, this is a huge work in progress and almost everything in “YaraRules” is from https://github.com/kevthehermit/PasteHunter/tree/master/YaraRules. Shoutout @KevTheHermit
Querying the Database
Use db.sh to query (Soon to be a nice script)
| |
Data Model
The following is the current data model used for the elasticsearch database. Not every one of these will be used for every given file. Any r2_* tags are typically reserved for binaries of some sort.
Name
Description
filename
The full path of the binary
file_ext
The file extension
The file size
filetype
Filetype based on magic value. Not as reliable as binwalk signatures.
md5
The files MD5 hash
sha1
The files SHA1 hash
sha256
The files SHA256 hash
added
The date the file was added
r2_arch
Architecture of the binary file
r2_baddr
The binary’s base address
r2_binsz
The size of the program code
r2_bits
Architecture bits - 8/16/32/64 etc.
r2_canary
Whether or not stack canaries are enabled
r2_class
Binary Class
r2_compiled
The date that the binary was compiled
r2_dbg_file
The debug file of the binary
r2_intrp
The interpreter that the binary calls if dynamically linked
r2_lang
The language of the source code
r2_lsyms
Whether or not there are debug symbols
r2_machine
The machine type, usually means the CPU the binary is for
r2_os
The OS that the machine is supposed to run on
r2_pic
Whether or not there is Position Independent Code
r2_relocs
Whether or not there are relocations
r2_rpath
The run-time search path - if applicable
r2_stripped
Whether or not the binary is stripped
r2_subsys
The binary’s subsystem
r2_format
The binary format
r2_iorw
Whether ioctl calls are present
r2_type
The binary type, whether or not it’s an executable, shared object etc.
yara
Contains a list of yara matches
binwalk
Contains a list of binwalk signatures and their locations in the binary
tags
Any user defined tags passed with the -t flag.
url
The origin url if a file was remotely downloaded
urls
Any URLs that have been pulled from the binary
Solutions to Issues
There are some known issues with this project (mainly to do with versions from package managers), and here I will track anything that has a solution for it.
ElasticSearch index field limit
If you get an error like this:
| |
You may have an older version of elasticSearch. You can upgrade, or you can increase the fields limit with this one liner.
| |
Video Inhale
In this video I show you how to install Inhale and how to use.
Here is the Link to the video: Inhale A malware analysis and classification tool.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.