Install Tor on Windows Kali Linux and Search the Dark Web

Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
What is the Dark Web? In this article and video, I will cover how to install Tor on (Kali) Linux and Windows, explain The Dark Web, What is The Hidden Wiki. The Dos and Don’ts to stay anonymous. Install Deep Explorer to make searching easier on the Deep Web.
The differences between Surface Web, Deep Web, and the Dark Web
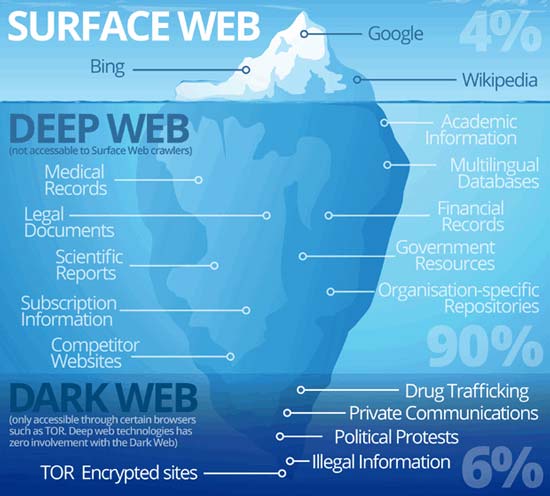
What is the Surface Web
As you can see in the image, the Surface Web would only consist of 4% of the web. And then this is the web that most people visit every day. Really incredible if you already consider how large the Surface Web is.
The Surface Web is the part of the World Wide Web that is available to the general public and searchable with standard web search engines.
What is the Deep Web
The deep web is just like it sounds, below the surface and not completely dark
“A Goldmine of Information”
The Deep Web holds the content that’s invisible to search engines. Here are a few examples of what’s on the deep web:
The content of your personal email accounts
The content of your online banking accounts
Medical records
Data that companies store on their private databases
Content of social media accounts
Content contained within scientific and academic databases
Legal documents
A lot of what exists on the deep web consists of information that you probably wouldn’t want to turn up in a web search (like your checking account information) because it’s private and could be misused.
If you have to log in to one of your accounts by providing a user name, password, or some other type of authentication, the information you access is on the deep web.
What is the Dark Web
The Dark Web - Darknet is a different story. The Dark Web operates with a high degree of anonymity. It hosts harmless activities and content, as well as a lot of criminal ones.
The Dark Web also hosts many legitimate companies like the New York Times and **Facebook **who offer Tor-based services, as well as generally benign content you can join a chess club or BlackBook, a social network described as the “the Facebook of Tor. The Dark Web is not always synonymous with cybercrime.
To enter the Darknet you need a Tor browser (More about this later)
The Dark sides of The Dark Web
The Dark Wet is also a place where illegal drugs and services - and much worse - may be found.
It is also possible to buy credit card numbers, all types of drugs, guns and other weapons, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software and scripts that help you break into other people’s computers. It’s also possible to buy login credentials to a $ 50,000 Bank of America account for $ 500, get $ 3,000 in counterfeit $ 20 bills for $ 600, buy seven prepaid debit cards, each with a $ 2,500 balance, for $ 500 (express shipping included). You can hire hackers to attack computers for you. You can buy usernames and passwords. Unfortunately, many other serious crimes also take place on the Dark Web.
Here are a few safety issues to consider.
Criminal element. There’s a chance you will find websites run by criminals. Beyond selling illegal goods and services, they may seek to exploit you and steal from you.
Suspicious links. If you click on any links, you may be taken to the material you might not want to see. It’s also possible that clicking a link or downloading a file could infect your device with malware.
Law enforcement. Law enforcement officials operate on the dark web to catch people engaged in criminal activity. Like others on the dark web, law enforcement can do their work under a cloak of anonymity.

Some frequently asked questions about the Dark Web
Who started dark web?
The dark web was created by the US government in the mid-1990s. Because this allowed spies to be able to distribute information completely anonymously. US military researchers developed the technology, known as Tor (The Onion Router) and released it into the public domain for everyone to use.
How big is the Dark Web
The internet contains at least 6.5 billion websites that have been indexed by search engines, according to one Dutch researcher. The rest is known as the deep web, which is probably 500 times larger than the surface internet.
Is it illegal to go on the Dark Web?
In one simple word: no. The Dark Web is legal. The use of the Tor browser is also completely legal. However, if you use the dark web to perform acts that violate the law, that is of course illegal. So here too we strongly emphasize that illegal activities must be avoided.
Silk Road
Silk Road was founded in 2011, Silk Road was a platform designed to enable its users to buy and sell illegal drugs and other unlawful products to buy and sell goods with the use of bitcoin, an untraceable digital currency,
The creator, Ross Ulbricht, was arrested in 2013. (Ross Ulbricht was sentenced to life in prison.) By the time it was shut down in 2013, the marketplace had accumulated 1,400 vendors and 957,079 registered users, and it had brokered more than 1.2 million transactions worth $214 million, according to the FBI.
More levels of the Web
Some claim that there are more layers on the internet. Whether this is true? Nevertheless, I would also like to mention this. Because several sources are writing about this. You can decide for yourself whether it is nonsense or not. I leave this up to you.
1. Common web
2. Surface web
3. Bergie web
4. Deep web
5. Charter web
6. Marianas web
7. (?)
8. The Fog/Virus Soup
9. The Primarch System
Suggest reading this… Source: https://rationalwiki.org/wiki/Deep_web

Dark Web step-by-step plan
How to surf the Dark Web safely. Read everything carefully before browsing the dark web.
Make sure you have a good basic knowledge
The Dark Web is a complex environment where a lot can go wrong. It is full of scammers, malware and phishing websites. It’s is better to learn by doing. However, this is not the best method. You would rather not infect your computer with malware or lose a lot of money before you understand how it all works. There are more than enough people on the dark web who want to abuse ignorance.
Use a Linux distribution
Anonymity is the most important thing on the Dark Web. Not because it’s illegal, but because the more anonymous you are - the safer you are. Unfortunately, Windows 10 is not a strong OS for privacy. This is because of Windows 10
1 Your data is synchronized by default: Browser history and open websites, app settings, Wi-Fi hotspots are all tracked.
2 Windows connect your device (PC, laptop or smartphone) to a unique advertiser ID as standard.
3 Cortana can collect your user data such as your keystrokes, searches, microphone recordings, calendar data, music playlists, and purchases.
4 Windows also collect all kinds of personal information such as your identity, passwords, interests and habits, contact details and locations.
Use a VPN
Even if you use the Tor browser, your internet traffic can be followed by someone who has enough time and knowledge. In 2017, there was a leak where in some cases IP addresses were simply given away. However, if these users had a VPN running in the background, this would not have been a problem.
Therefore it’s advisable to have a VPN (This link is sponsored)on, even if you are on the dark web via Tor. VPNs anonymize your internet traffic and ensure that your IP address is hidden from hackers or government agencies. It is good to know that not every VPN is equally reliable. And free VPN can be very slow.
Download Tor from the official website
The Tor browser is an interesting target for hackers and government agencies. Fake versions of the Tor browser have been put online. In this way, Tor users can be hacked even before they get to the dark web or to track user behavior once they are on the dark web. The latter method is mainly used by government agencies that want to trace illegal behavior on the dark web.
Therefore it’s important to always download the correct version of Tor on their official web page: https://www.torproject.org/
Take precautions
Before opening the Tor browser
Very important. Change your DNS settings. (I’ll come back to this in another article, and I explain how to adjust it (and why) you should always change your DNS settings).
1 Close all non-essential apps.
2 Switch off all services that are not necessary.
3 Cover your webcam with adhesive tape. Hacking someone’s webcam is amazingly easy.
4 Turn off your computer location. In addition to your IP address, your computer can also give away your location.
Once you have opened Tor, do not change the size of the Tor browser screen. Strangely enough, this keeps you safer.
Change the Tor security level
In Tor, you can set the security level to low, medium and high. Of course, high is the most secure. Unfortunately, this level ensures that your internet connection will be delayed and some websites will not run completely smoothly.
Check whether you are not bothered by an IP leak or a DNS leak
It’s possible that your VPN is leaking IP and DNS information. You can also suffer from a WebRTC leak through multiple browsers such as Chrome. To be sure that your connection is properly anonymized, you can go to the following websites:
ipleak.org
dnsleaktest.com
WebRTC test
If you buy something, use cryptocurrency
If someone on the dark web wants to arrange a transaction through a regular bank, then you have unlawfully hooked up a scammer or a black hat hacker, or something else. The dark web is an anonymous zone and nobody wants to use traceable banks for transactions.
Bitcoin is the best-known cryptocurrency and is also often considered to be completely safe and anonymous. This is not the case. Bitcoin has a number of privacy problems that make it possible (albeit with great difficulty) to link someone’s personal data to a Bitcoin transaction.
That is why it’s better to go for a cryptocurrency that specializes in privacy and anonymity.
Close everything as soon as you are done
Once you have finished browsing the dark web you must close all programs and other related content. To take it for granted, it is best to reboot your computer.
Be aware that you are never 100% safe
Even if you perform all these steps correctly, it is still possible that something will go wrong. You are never 100% safe on the internet, especially on the dark web. You can accidentally give away personal information or click on the wrong link. Hackers are constantly trying to find new ways to exploit security measures. If the hardware of your device is infected, you are not safe anyway. In other words, there are a lot of precautions you can take to improve your safety on the dark web, but nothing is 100% safe.
Bonus Tip if you really want to remain anonymous
If you follow this step-by-step plan, you don’t actually have to worry so much. Unless you click on dangerous links at random. How careful you have to be on the Dark Web also depends on what you want to do there. This is sometimes called your “threat model”. If you only want to read some discussions on a dark web forum, it is not necessary to follow all precautions. If you set the Tor browser to its safest and do not click on strange links, you will not get any problems.
Never type anything directly into the Tor browser.
There is an incredible number of ways you can be identified online. With browser fingerprinting you can distinguish yourself from other Tor users in countless ways. There are strategies for this, but these are not watertight. In addition, there is another method to find you: your “fingerprint type”.
You have a completely unique way of typing. How fast you type, which words often type or not, whether you use the left or right shift key, they are all so-called “identifiers” which you can find even if you are completely anonymous on the internet. That is why you should never type anything into the Tor browser since this can be followed. To work around this problem you can do the following
Open a text editor as a screen next to your Tor browser
Type everything in the text editor and copy-paste everything into the browser. The chance that someone will analyze your typing type via the Tor browser is astronomically small. But it is always possible. By not typing anything in the browser, you are just that one step more careful.
Note if you are really wanted, these tips will not help you either. If intelligence services are after you, your best option is not to go online anymore.
Install Tor
In the video I will cover both installs and much more.
Download and install Tor on Windows
To download Tor for Windows, go to the Tor Project and click on download. Make sure the URL is correct and do not download it from any other source. And click on “Run”
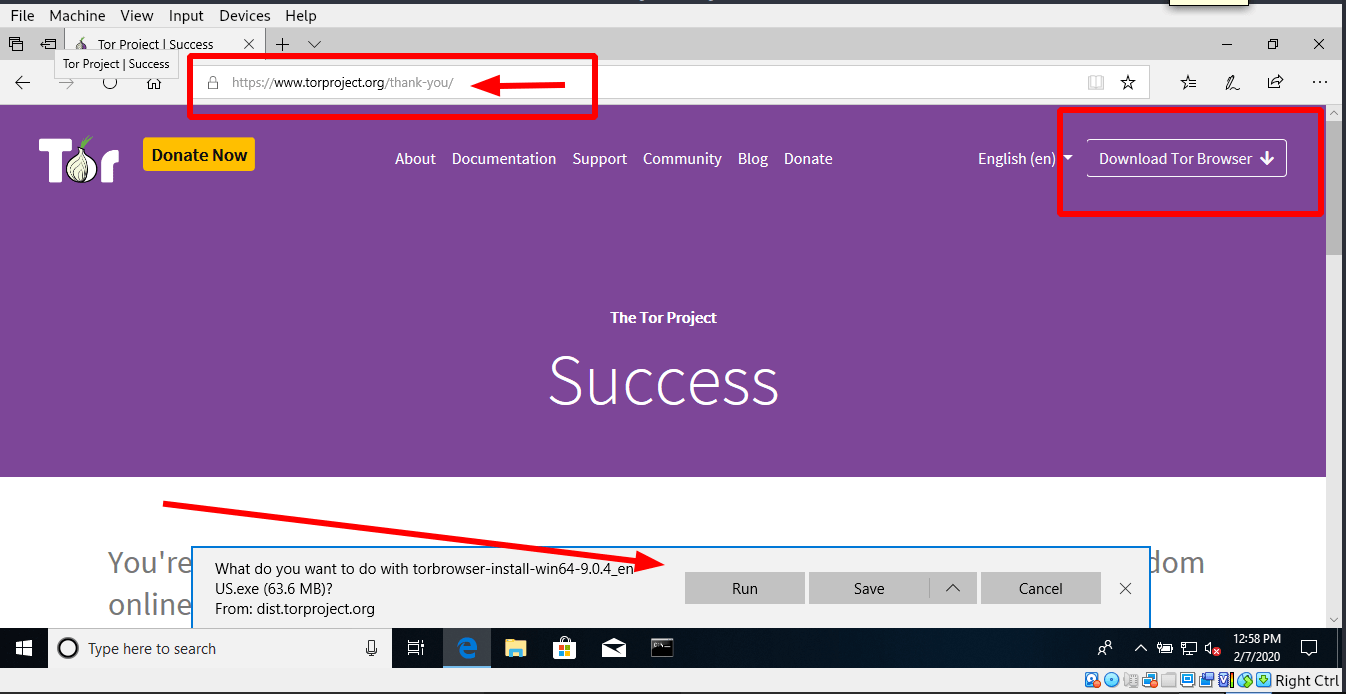
You can see more in the video I made for this article. Subscribe to the channel for way more videos to come.
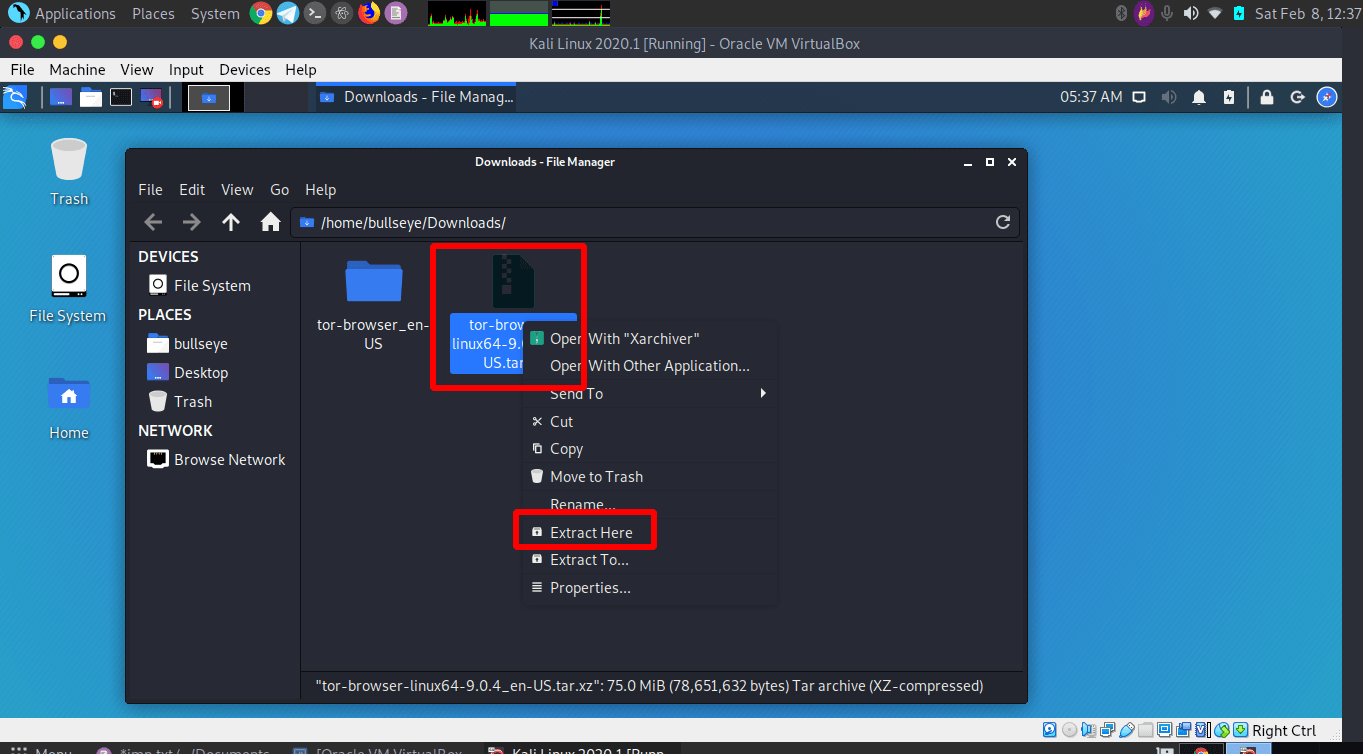
Install Tor on “Kali” Linux
In the video, I’ll explain and show how to install Tor on Kali Linux. But for other Linux distributions (distro) it works the same. Parrot OS or Parrot security, I use as the main Operating System (OS) has already Tor installed. But also Anonsurf, in another article. I will cover that.
Note:
If you install Tor, it is safer to do this with a new root user name. And this new account can only be used for surfing the Dark Web. You can imagine that with “The normal” use you have left some traces behind.
How to add a new user can you find here:
https://hackingpassion.com/best-linux-commands-hacks-and-other-cool-tricks-for-beginners/#Another_way_to_add_a_user_is
Download Tor
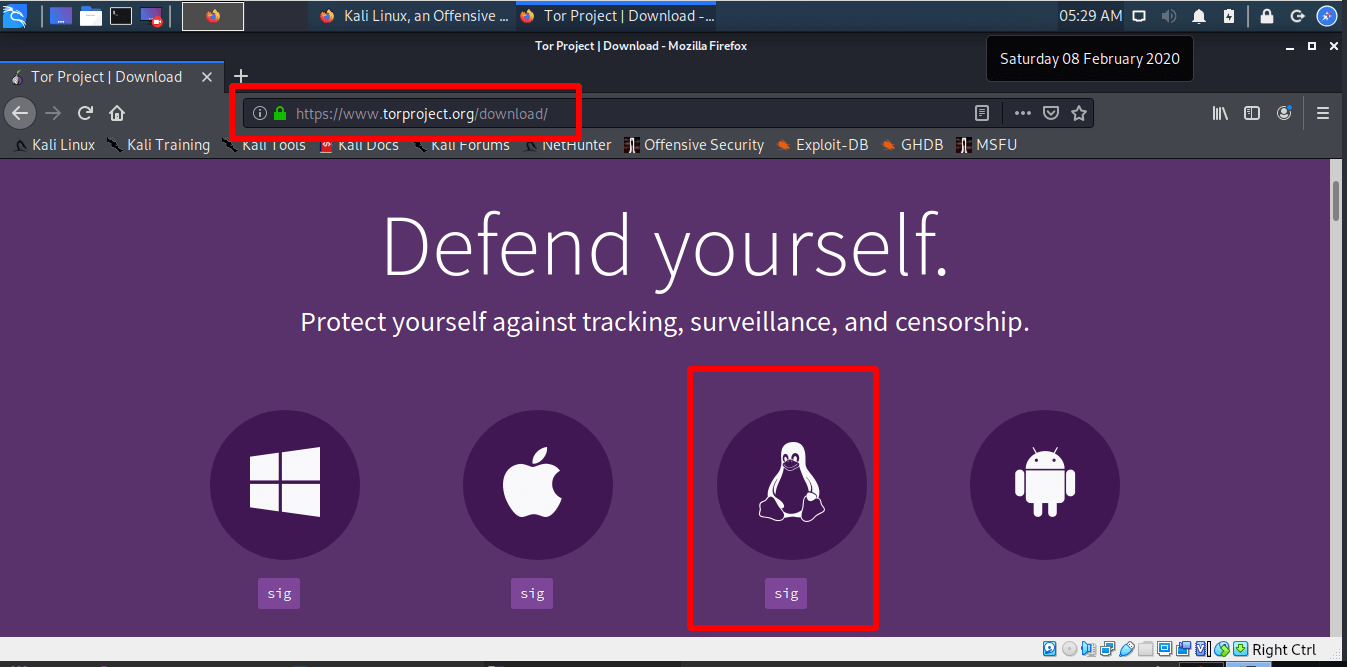
Make sure you use the right link..! https://www.torproject.org/download/
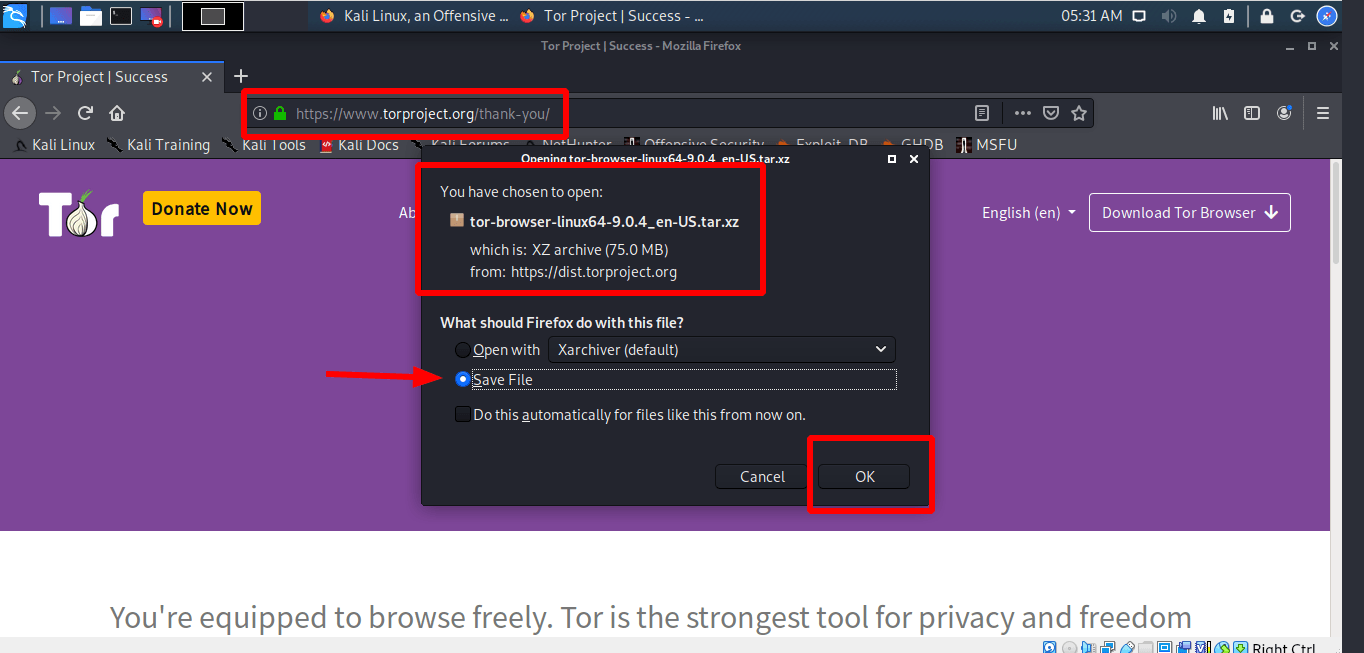
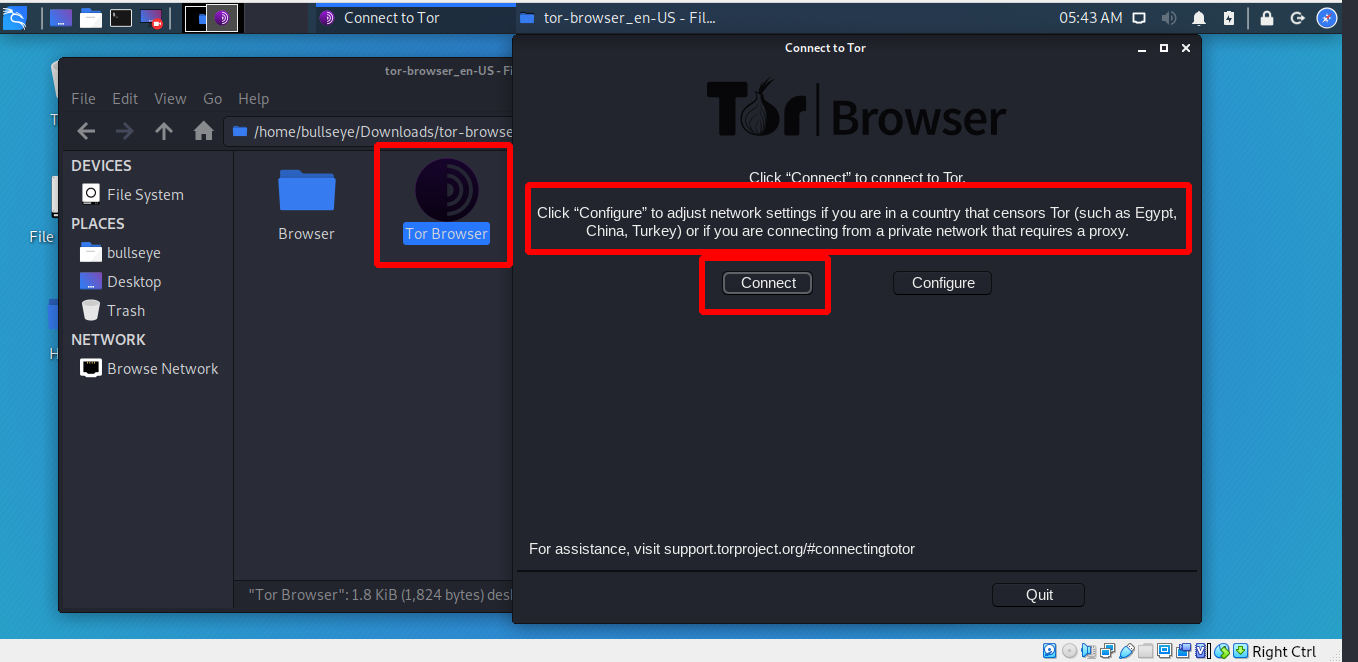
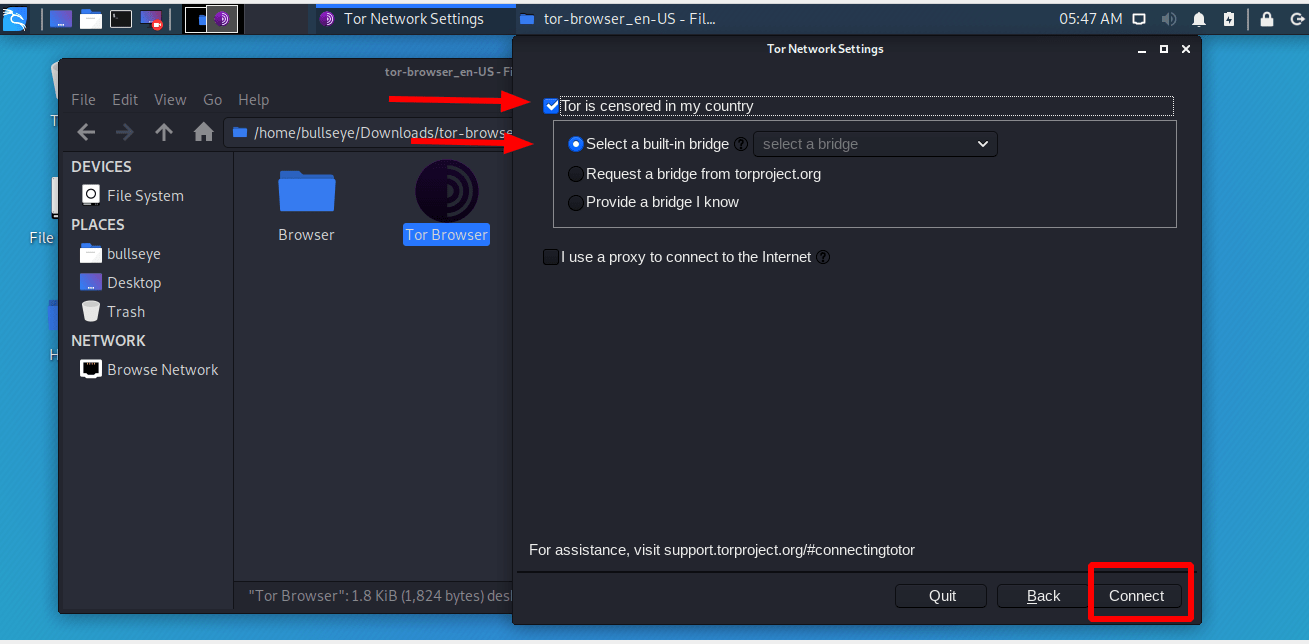
If Tor is censored in your country, then click on configure and Tor give you some other options.
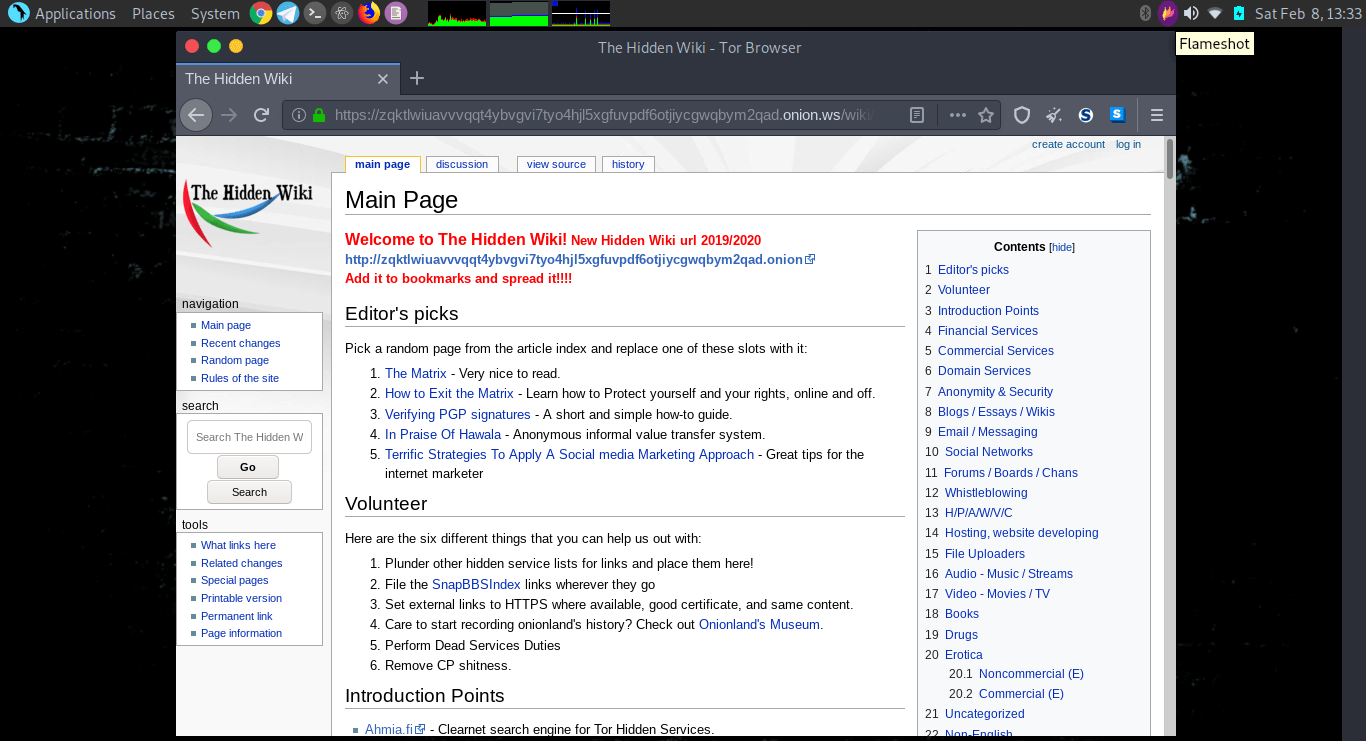
The Hidden Wiki
The Hidden Wiki is a Dark Web Wikipedia where you can find links to different websites. As you note in this article, the URLs of dark web pages are often nonsensical and the links end with .onion. This makes it difficult to find the website that you are looking for. The Hidden Wiki does a lot of searching for you. In addition, they offer informative pages on a range of topics that may be of interest.
Be careful not to click on a link to something that you do not want to see because the Hidden Wiki not only indexes legal websites.
Deep Explorer
A while ago I came across this very handy Deep Explorer tool to search the Dark Web. As you will know it can be difficult to find something on the Dark Web. This tool makes life a little easier :-)
Deep Explorer is a tool developed in python which purpose is the search of hidden services in the Tor network, using Ahmia Browser and crawling the links obtained. You should have Tor installed for using Deep Explorer.
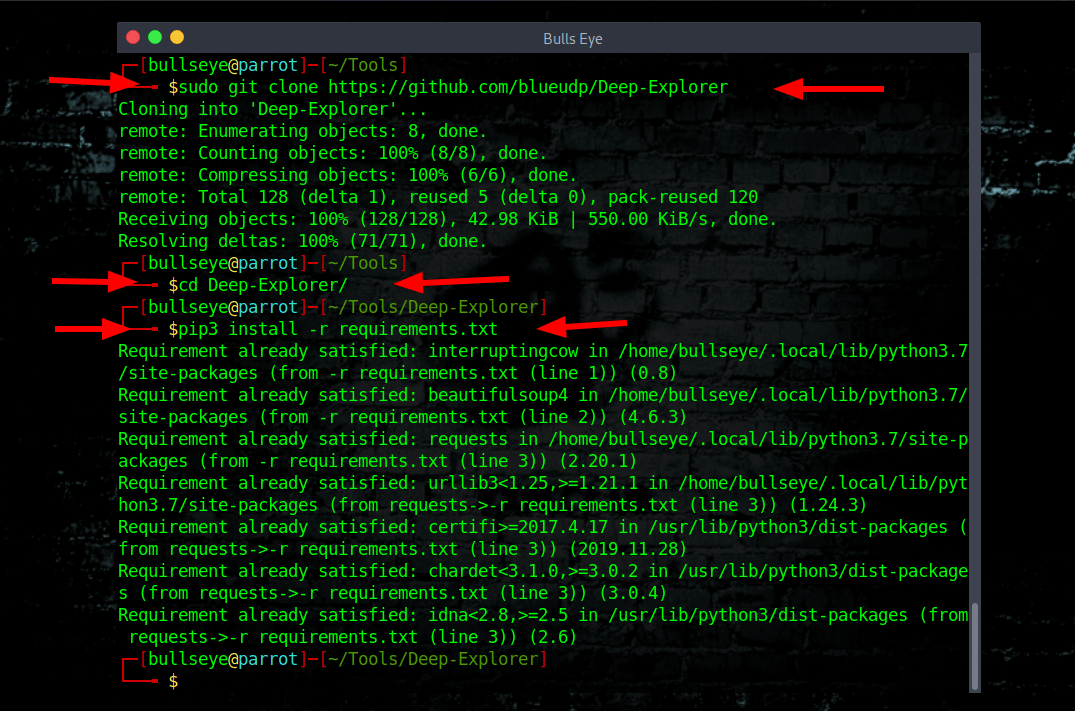
Installing Deep Explorer
| |
| |
| |
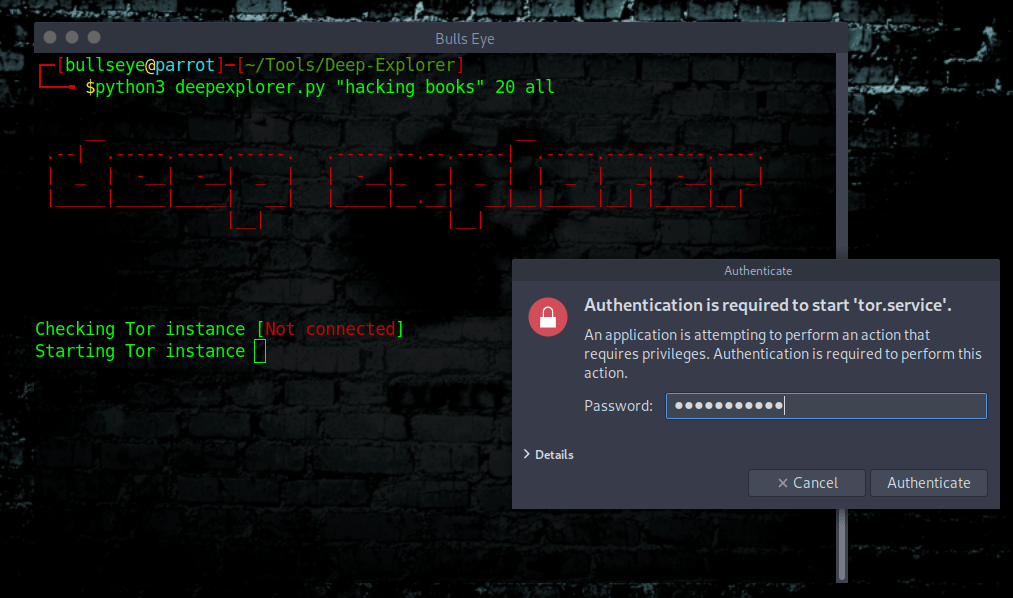
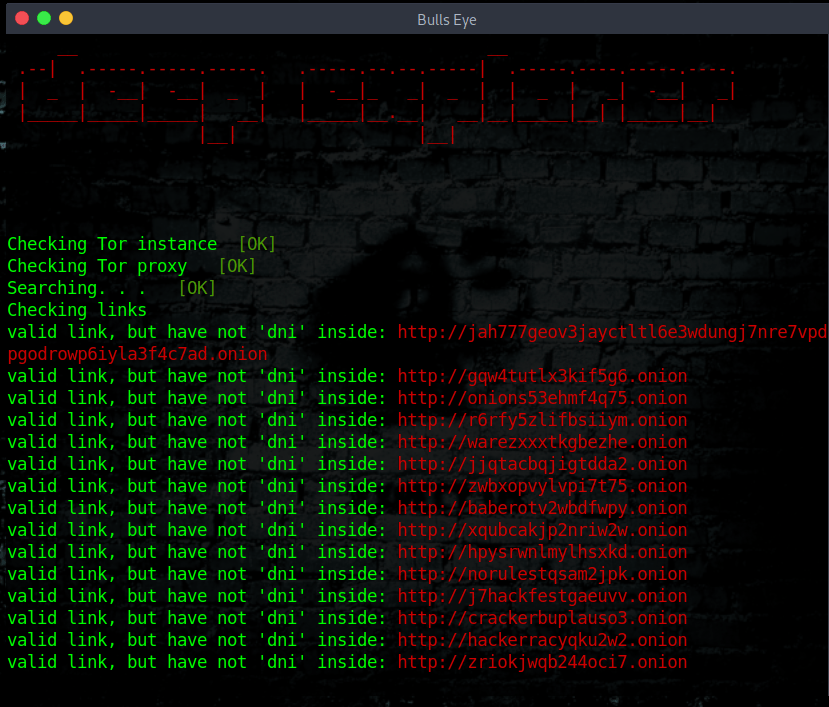
Using Deep Explorer
Here is an example: (Be careful when you download something from the Dark Web).
| |
Video
TorGhost Anonymously Rout Your Traffic Through Tor | Install on Kali and Parrot OS
Install Tor on Windows, (Kali) Linux and search The Dark Web
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
Conclusion
There is much to tell about this topic, and I have tried to be as clear as possible. There are many articles that could be interesting related to this topic.
Install Kali Linux 2020.1 on VirtualBox
Best Operating System for Ethical Hacking
Best Linux Commands Hacks and other Cool Tricks for Beginners
Google Dorks an Easy Way of Hacking
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.