Malicious npm Package Stole WhatsApp Messages for 6 Months: 56,000 Downloads
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
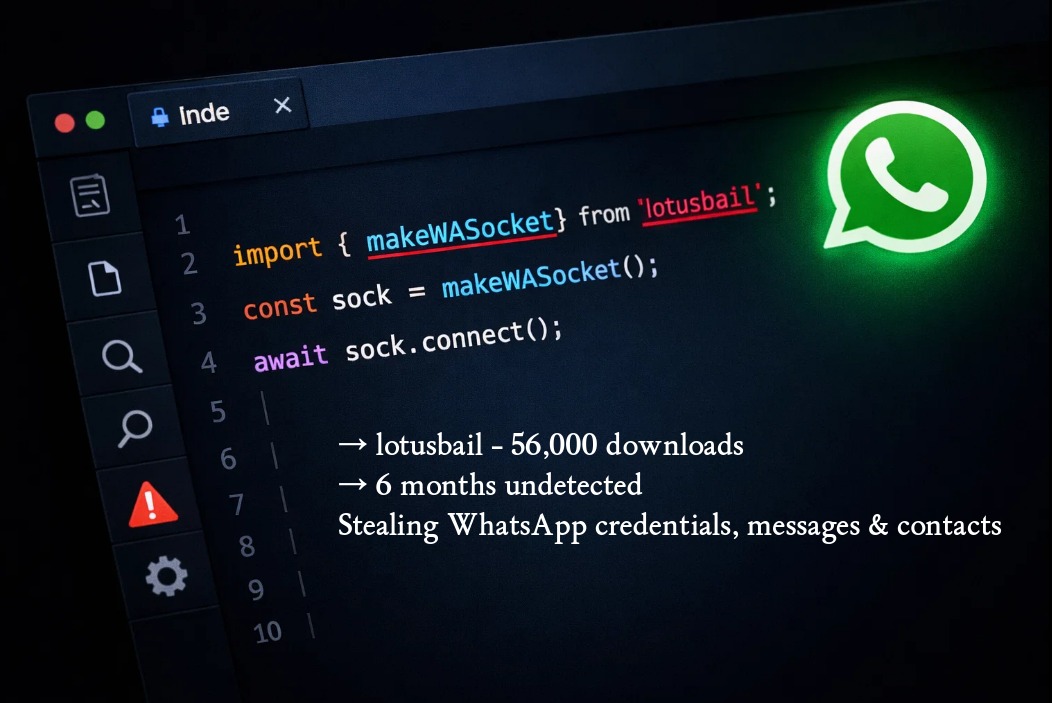
56,000 downloads. 6 months online. A WhatsApp library on npm was stealing credentials, messages, and contacts. Nobody noticed. 🤔 The package is called “lotusbail” and it looks like a legitimate fork of the popular WhatsApp API library @whiskeysockets/baileys.
Same functionality. Works perfectly. Send messages, receive messages, handle media. Everything you’d expect.
Except it does something extra.
→ Your WhatsApp authentication tokens → Every message you send and receive → Your complete contact list with phone numbers → All media files and documents → Session keys for persistent access
You know WhatsApp’s device pairing feature? The one you use to connect WhatsApp Web?
This malware hijacks that.
It contains a hardcoded pairing code hidden in AES-encrypted strings. The attacker’s device gets silently linked to the developer’s WhatsApp account.
And here’s what makes lotusbail truly dangerous:
Uninstalling the package is NOT ENOUGH.
The attacker’s device stays linked to your WhatsApp account. They keep reading messages. They keep seeing contacts. Until you manually go into WhatsApp Settings, open Linked Devices, and remove every device you don’t recognize.
How many developers will actually do that?
The malware author thought of everything: → 27 infinite loop traps that freeze your system if you try to debug. They even left helpful comments in the code marking which sections were malicious. Someone probably has a Jira board for this. → 4 layers of obfuscation: Unicode manipulation, LZString compression, Base-91 encoding, AES encryption → Custom RSA implementation to encrypt stolen data before sending
Why custom RSA? WhatsApp already has end-to-end encryption. Legitimate libraries don’t need extra encryption. This exists only to hide the theft from network monitoring.
The package was uploaded by user “seiren_primrose” in May 2025. It’s been live for 6 months. 711 downloads in the final week before discovery. Was still available on npm at the time of discovery.
Context matters here.
2025 has been brutal for npm: → September: Shai-Hulud worm compromises 500+ packages, self-replicates across the ecosystem → September: Chalk and debug hijacked (2.6 BILLION weekly downloads), removed within 2 hours but downloaded 2.5 million times → November: Shai-Hulud 2.0 hits 700+ packages with better obfuscation
And now this. A functioning WhatsApp library that passes every code review because it actually works.
3 billion people use WhatsApp every month. Over 140 billion messages per day. One compromised library in the hands of developers building WhatsApp integrations, and the blast radius becomes enormous.
Check if you’re affected:
→ Search your package.json and package-lock.json for “lotusbail” → If found, remove immediately → Open WhatsApp on your phone → Go to Settings then Linked Devices → Remove ANY device you don’t recognize → Even if you removed the package months ago, check anyway
They’re getting smarter. Static analysis sees working WhatsApp code and approves it. Reputation systems see 56,000 downloads and trust it.
The malware hides in the gap between “this code works” and “this code only does what it claims.”
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.