Apple Approved It: MacSync Stealer Bypasses Notarization to Infect Hundreds of Macs
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
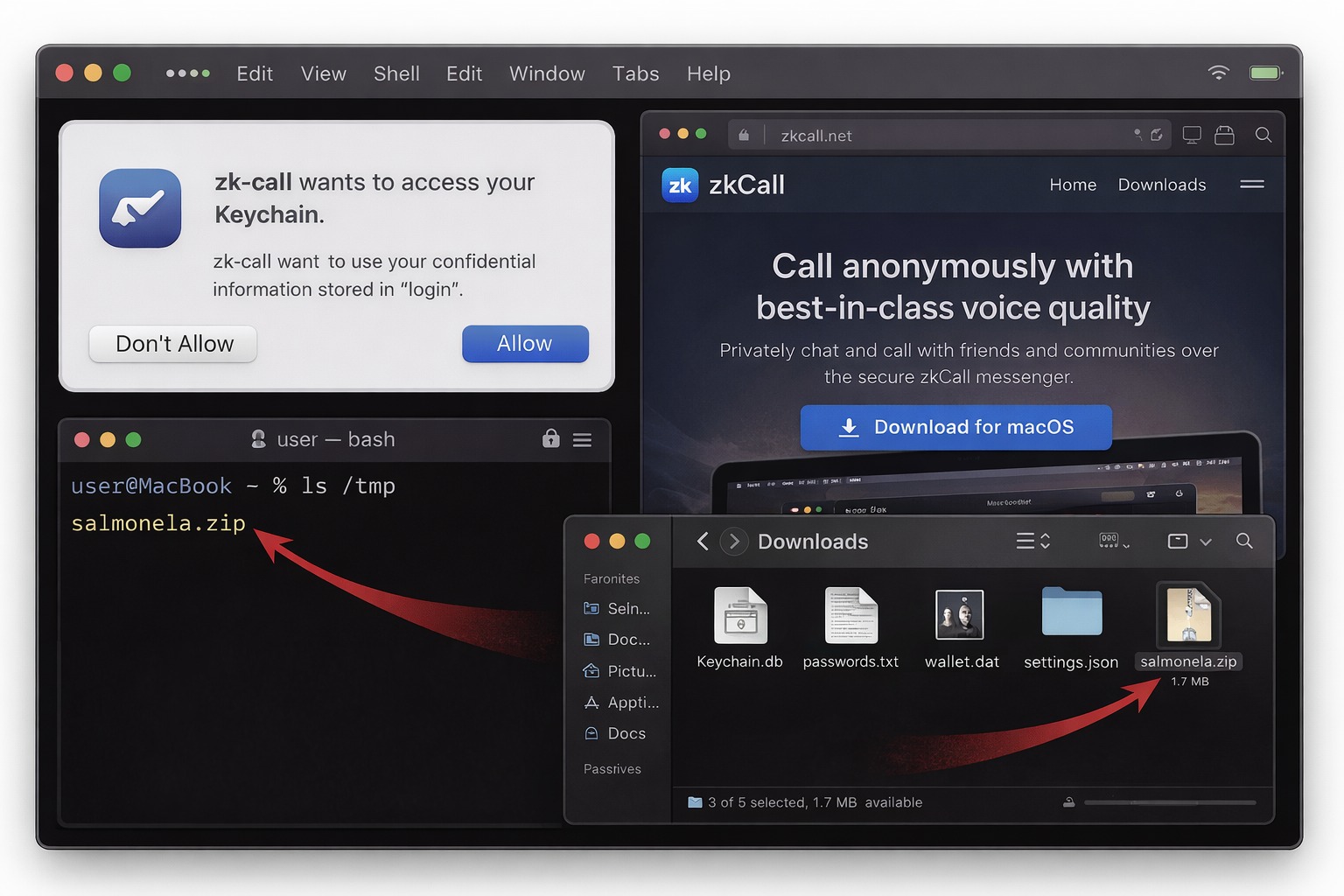
Apple’s security team reviewed this app. Approved it. But now it steals your passwords, crypto wallets, and Telegram account. 😳 Hundreds of Macs infected since mid-2025.
MacSync Stealer just hit number 6 on Red Canary’s top 10 threat list for December 2025. Most victims in Ukraine, the US, Germany, and the UK.
In April 2025, a hacker called “mentalpositive” built a cheap macOS stealer named Mac.c. Price tag: $1,000. That’s budget pricing in the malware world. AMOS, the market leader, charges $3,000 per month.
By July, the project was dying. No funding. No future.
Then someone bought it. Rebranded it to MacSync. Added a Go-based backdoor for remote control. And in December, they figured out how to get Apple to approve it.
The trick is simple but effective. The app itself contains no malware. It’s a clean Swift application. Apple’s automated security scan sees nothing wrong. Signs it. Notarizes it. Approves it for distribution.
After installation, the app silently downloads the actual malware from gatemaden.space. Executes it. Then deletes its tracks.
The dropper includes anti-analysis tricks: it won’t run twice within an hour, making automated sandbox detection harder.
What MacSync steals: → Your entire iCloud Keychain → Browser passwords from Chrome, Safari, Firefox, Brave → Crypto wallets: Exodus, Ledger Live, MetaMask, Coinomi → Your complete Telegram account → Credit card autofill data
But unlike older stealers, MacSync doesn’t just grab and go. The Go-based backdoor gives attackers persistent remote access. They can execute commands on your Mac whenever they want. The stolen data gets compressed into a file called /tmp/salmonela.zip (yes, really) and sent to their command server.
Security researcher g0njxa interviewed the criminals behind MacSync. When asked if they target CIS countries like Russia, Ukraine, or Belarus, the answer was clear:
“No. That’s a principled position and it will not change.”
Make of that what you will. I don’t like attribution and will not play that game.
The distribution method is clever. The malware hides inside a fake messenger app called “zk-call” from zkcall.net. The installer is 25MB, stuffed with decoy PDF files to look legitimate and confuse automated scanners.
Apple revoked the developer certificate (Team ID GNJLS3UYZ4) after Jamf Threat Labs reported it.
They’ll be back with a new certificate.
How to protect yourself: → Only download apps from the Mac App Store or verified developer websites → Check the publisher, not just if the app is signed → Be suspicious of messenger or crypto apps from unknown sources → If an app asks for your password immediately after installation: stop → Check Telegram for unknown active sessions (Settings → Devices)
Hacking is not a hobby but a way of life.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.