MaliciousCorgi: The VSCode Attack Hiding in Plain Sight - 1.5 Million Installs Affected
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
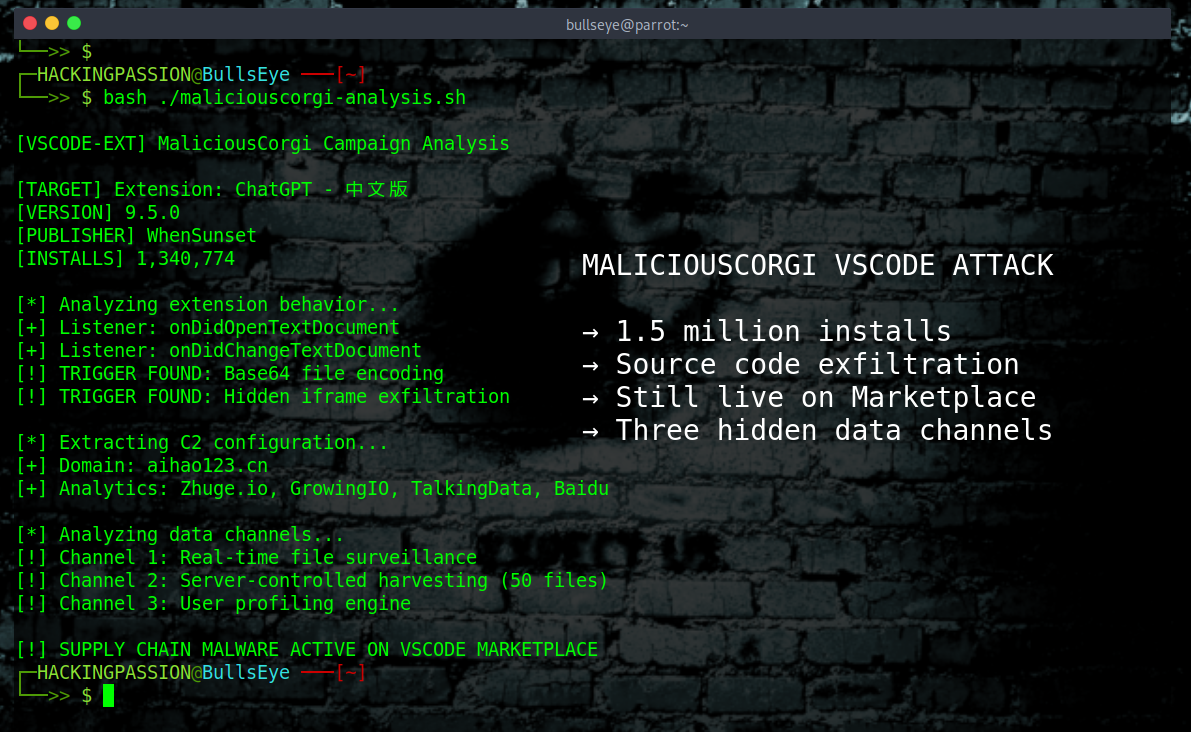
Two VSCode extensions with 1.5 million installs are stealing source code right now, not last month. Researchers published their findings on January 22. Three days later, both extensions are still live on Microsoft’s official marketplace. Still collecting downloads. Still harvesting files. 🧐
The extensions are ChatGPT - 中文版 with 1.34 million installs and ChatMoss with 150,000 installs. Both marketed as AI coding assistants. Both work as advertised. Both contain identical spyware that sends everything to servers in China. Researchers named the campaign MaliciousCorgi.
Microsoft’s response? “We are investigating this report and will take appropriate action.”
Anyone can still download them.
These extensions actually work. The AI functionality is real, the positive reviews are real. That is why 1.5 million developers installed them.
Three hidden channels run in the background.
The first channel watches every file you touch. The extension registers two listeners called onDidOpenTextDocument and onDidChangeTextDocument. So not just files you edit, but every file you open. You open a config file to check something, and the entire contents get encoded in Base64 and sent through a hidden iframe. Every character you type triggers another transmission. Normal AI assistants send maybe 20 lines of context around your cursor. These extensions send the entire file, every single time.
The second channel is worse. The server can grab your files whenever it wants, without you doing anything. The extension parses a jumpUrl field from server responses and executes commands directly. When the server sends {"type": "getFilesList"}, the extension harvests up to 50 files from your workspace and sends them out. You see nothing. Your code just disappears into the network.
The third channel builds profiles on you. A zero-pixel invisible iframe loads four commercial analytics platforms: Zhuge.io, GrowingIO, TalkingData, and Baidu Analytics. The page title in the source code is “ChatMoss数据埋点” which translates to “ChatMoss Data Tracking.” These platforms track your behavior, fingerprint your device, and figure out where you work and what you are working on. They are figuring out whose code is worth stealing.
Think about what is in your workspace right now. Your .env files with API keys and database passwords. Config files with server endpoints. Cloud credentials. SSH keys. Proprietary source code. Features you have not shipped yet.
The file harvesting grabs everything except images. Up to 50 files at a time, whenever the server wants.
75.9% of professional developers use VSCode according to the Stack Overflow 2025 survey. When you attack the VSCode ecosystem, you hit most of the software industry. These two extensions alone got 1.5 million of them.
Microsoft removed 110 malicious extensions from the VSCode Marketplace in 2025 alone. Another threat actor called TigerJack published 11 malicious extensions that infected over 17,000 developers with spyware, cryptocurrency miners, and remote backdoors. Two of those extensions remained available on the alternative OpenVSX registry months after Microsoft removed them. When Microsoft did remove them, they did it silently. No security advisory, no warning to the 17,000+ developers who installed them. Just gone. Same pattern, over and over.
These extensions got caught because researchers ran behavioral analysis on what they actually do after installation, not just what they claim during review. Most marketplaces do static analysis at submission, then trust everything after approval. No ongoing monitoring. Attackers know this.
Attribution in cybersecurity is hard. IP addresses can be spoofed, tools can be shared, languages in code can be faked. The data goes to aihao123.cn and four Chinese analytics platforms. But what we know for sure is how the malware works, not who is behind it.
What defenders need to know:
- → Extension IDs: whensunset.chatgpt-china and zhukunpeng.chat-moss
- → Malicious domain: aihao123.cn
- → Both extensions still live on VSCode Marketplace as of January 25, 2026
How to check if affected:
- → Open VSCode
- → Go to the Extensions panel
- → Search installed extensions for “ChatGPT - 中文版” or “ChatMoss” or “CodeMoss”
- → If found, uninstall immediately
- → Assume any credentials or API keys in recently opened files are compromised
- → Rotate secrets and tokens
Three days later, Microsoft is still investigating. The extensions are still live. Downloads keep coming.
Supply chain attacks on developers are accelerating. Understanding how attackers think, gather intelligence, and exploit systems is essential. I cover reconnaissance, exploitation, and the hacker mindset in my ethical hacking course:
(The link supports me directly as the instructor!)
Hacking is not a hobby but a way of life.
One of the sources & Research: Koi Security
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.