Maltrail Malicious Traffic Detection System
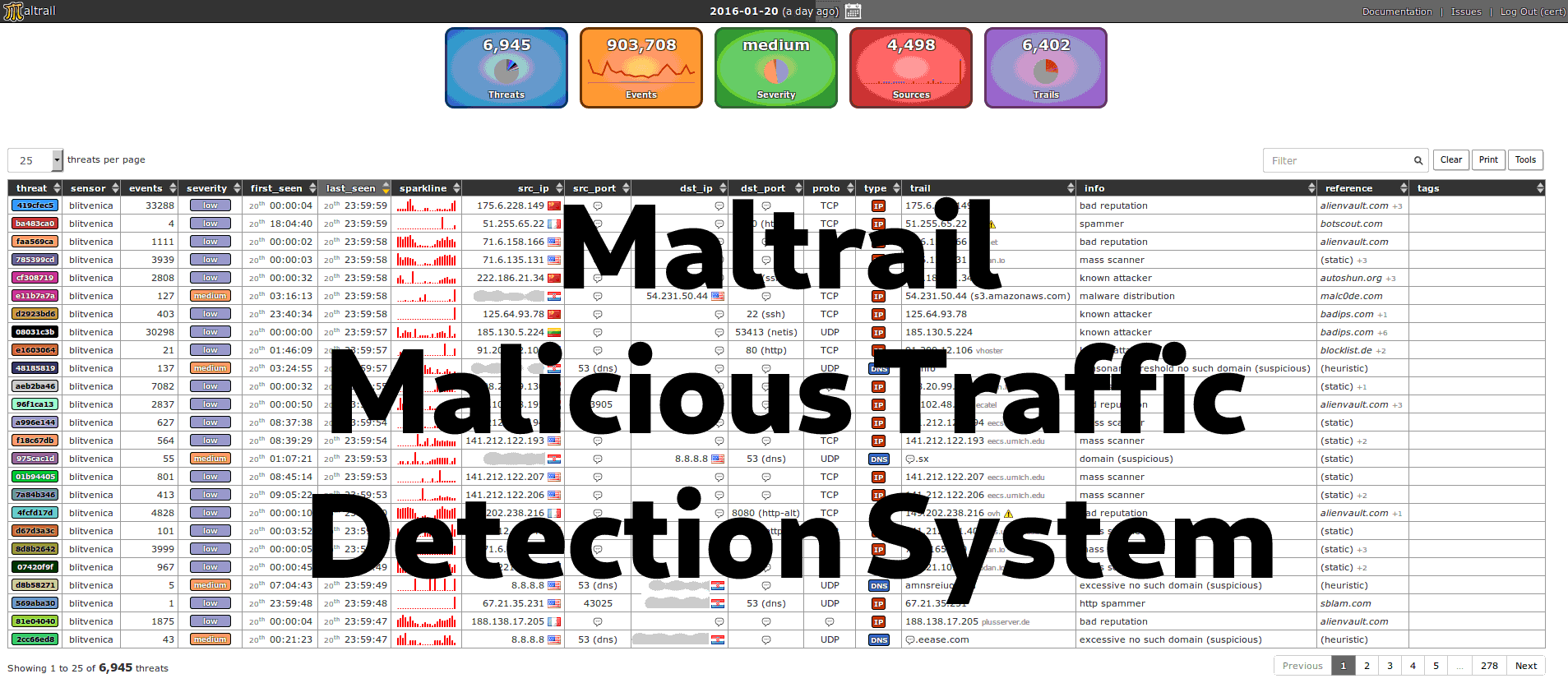
Maltrail is a Malicious Traffic Detection System that utilizes publicly available blacklists (and other trails from various AV reports and user-defined lists) to help discover unknown threats by monitoring traffic against those lists. Maltrail is run from the command line but does include a handy (and optional) web interface.
If you take the security of your servers and computers really seriously, then you know how important it is to be constantly alert to malicious behavior. This can be a 24/7/365 job, and if you have a lot of equipment, this task is almost impossible. Fortunately, there are a number of useful tools available that reduce this burden considerably. Such a tool is Maltrail.

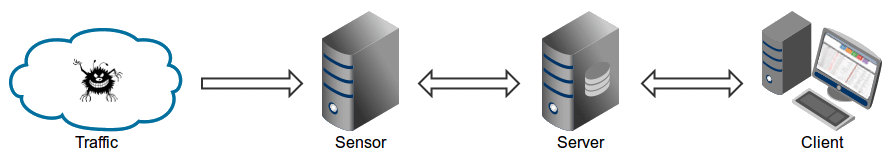
Maltrail is made up of three components
1. The **Sensor** which monitors traffic for threats
2. **Server** which provides logging for the event details of the detected malicious traffic.
The **Client** that provides visualization and reporting of the event details.
Install and Configure
With this install, I will use a Debian based Operating System.
For other Linux distros search for the required Package Management Systems.
Update and upgrade your system
| |
Install the required dependencies
Maltrail requires the python pcap packages. Hence, to install pcap and other necessary dependencies, run the command below. In this command, we do this all in one because this is always the easiest way.
| |
Install Maltrail
The following set of commands should get your Maltrail Sensor up and running (out of the box with default settings and monitoring interface “any”)
| |
| |
Start Maltrail Sensor
To run the Sensor, execute the command below to run the Maltrail sensor in the background.
| |
Start Server
To start the Server on same machine, open a new terminal and execute the following:
| |
Access the interface by visiting http://127.0.0.1:8338 from your web browser.
Default credentials:
Username: admin
Password: changeme!
Testing Maltrail
A while ago I wrote an article about: How to use Nmap NSE Scripts to find Vulnerabilities In this article you can find a lot of information about Nmap NSE. In the video below, I show a nmap vuln scan.
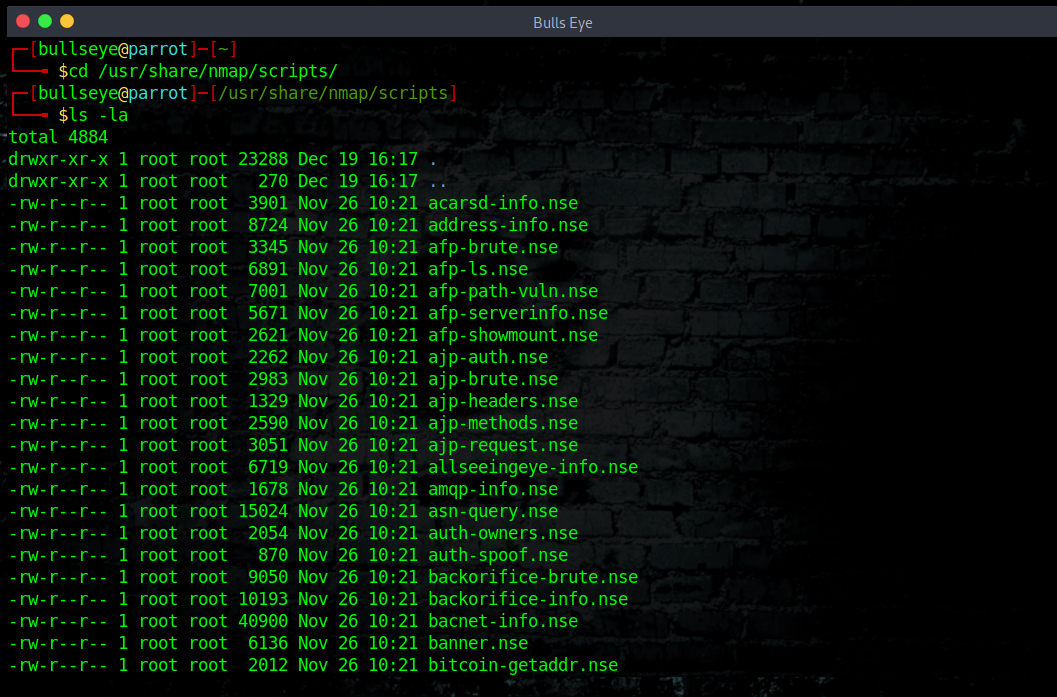
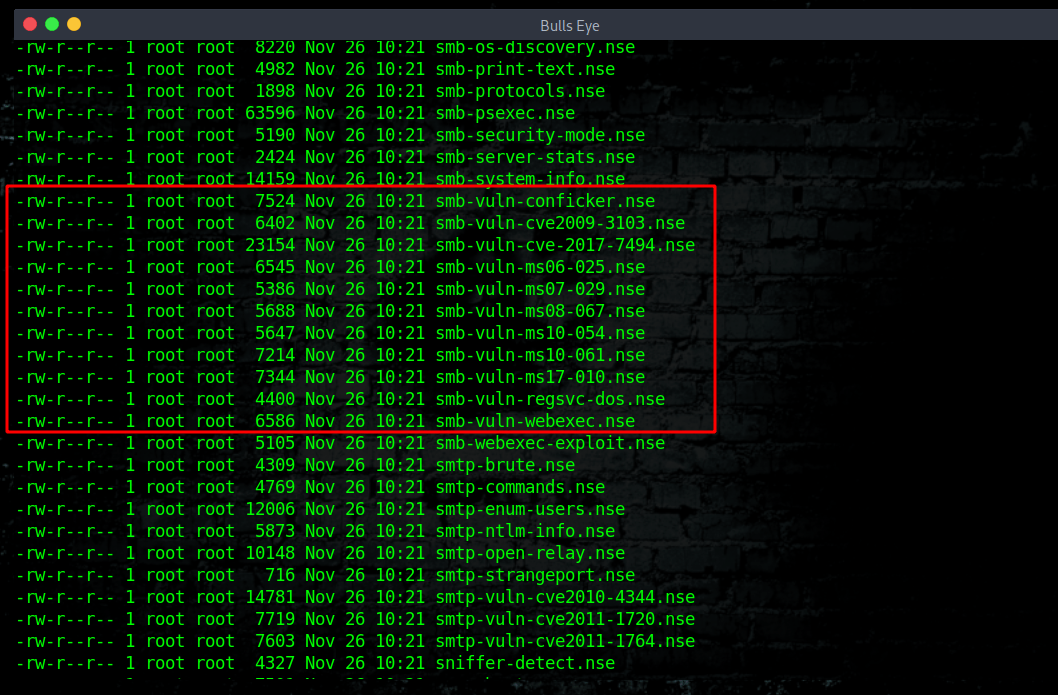
Nmap NSE script
To find the Nmap NSE scripts
| |
| |
Video Maltrail
Maltrail Malicious Traffic Detection System
In this video, I show you how to set up this awesome tool. Because I use a Vulnerable server and will use the Nmap NSE script “Vuls” to get some action.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
For more information you can visit the GitHub page:
Maltrail and Download the tool here.
They have made enormous much info about this tool.
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.