Ni8mare: n8n Vulnerability Gives Full Admin Access with One HTTP Header Change
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
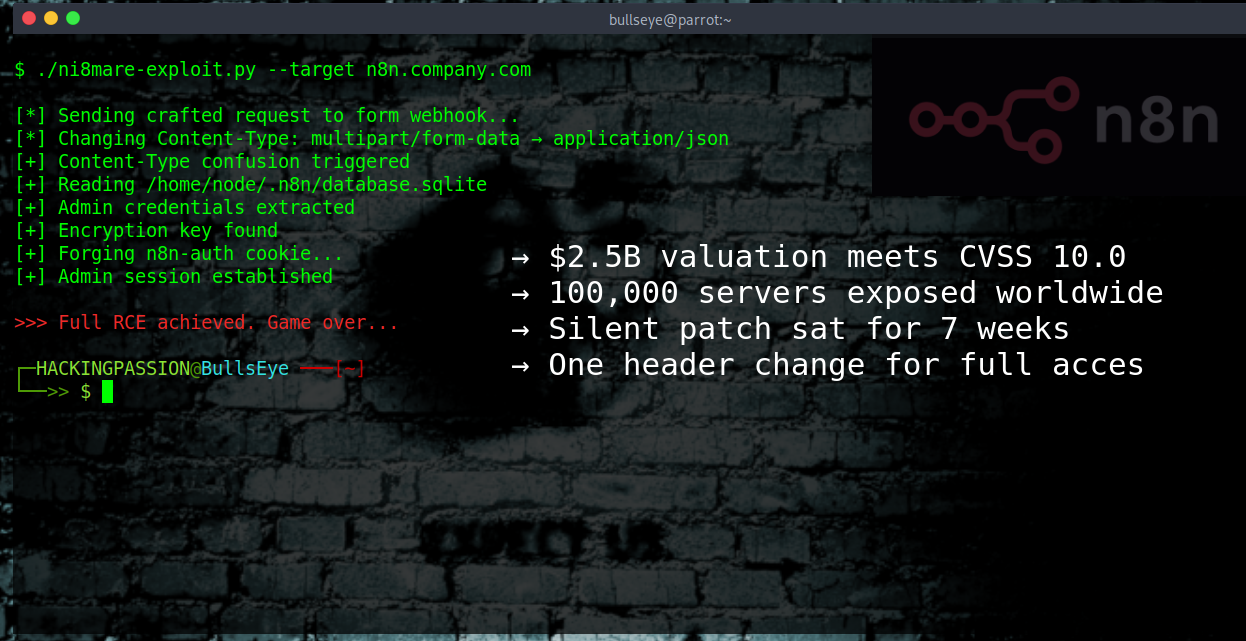
100,000 servers. One HTTP header change. Full admin access. No password required. They call it “Ni8mare.” CVSS 10.0. The patch existed for 7 weeks. The release notes mentioned nothing. 😏
CVE-2026-21858. “Ni8mare” The name says it all.
n8n is a workflow automation platform. Think Zapier, but open source and self-hosted. Over 100 million Docker pulls. Used by Vodafone, Delivery Hero, StepStone. Thousands of enterprises run their entire automation infrastructure on it, with 400+ integrations connecting everything in one central hub.
What’s happening:
→ Attacker sends a crafted request to any n8n form → Changes Content-Type header from multipart/form-data to application/json → n8n gets confused and lets attacker control file paths → Attacker reads any file on the server: database, config, secrets → Forges admin session cookie → Creates workflow with “Execute Command” node → Full remote code execution. Game over.
The technical term is “Content-Type confusion.” n8n’s form handler doesn’t check if the Content-Type matches what it expects. So you tell it you’re sending JSON, but structure it like a file upload. n8n copies whatever file path you specify instead of the uploaded file.
Here’s why this one is worse than an average vulnerability:
n8n sits at the center of everything. It connects your Google Drive, OpenAI API keys, Salesforce, CI/CD pipelines, payment processors, and customer databases all in one place. One compromised server means access to all of it.
The researchers said: “A compromised n8n instance doesn’t just mean losing one system. It means handing attackers the keys to everything.”
Important nuance: Horizon3.ai analyzed this vulnerability and found that successful exploitation requires specific workflow configurations. You need an n8n form that’s publicly accessible AND a way to retrieve the files, like an AI chatbot with file access. Their Shodan search showed 70,000 n8n instances, but only 76 had the chatbot component that makes full exploitation trivial. Most default configurations aren’t immediately exploitable. That said, if your setup matches these conditions, the risk is real.
No active exploitation has been observed yet. But proof-of-concept code is public and the vulnerability is well-documented. The clock is ticking.
The timeline:
→ November 9, 2025: Cyera reports vulnerability to n8n → November 10, 2025: n8n acknowledges → November 18, 2025: n8n releases patch. Silently. No CVE. No security advisory. Release notes mention nothing. → December 29, 2025: Researcher asks “when are you publishing this?” → January 6, 2026: n8n finally assigns CVE → January 7, 2026: Cyera publishes details
Seven weeks, the patch existed for seven weeks. Nobody knew to update because n8n didn’t tell anyone it was a security fix.
This is the fourth critical vulnerability in n8n in the past few weeks (As you might know I wrote about it before):
→ CVE-2025-68613 (CVSS 9.9) - Sandbox escape, authenticated
→ CVE-2025-68668 “N8scape” (CVSS 9.9) - Python sandbox bypass, authenticated
→ CVE-2026-21877 (CVSS 10.0) - File upload RCE, authenticated
→ CVE-2026-21858 “Ni8mare” (CVSS 10.0) - Content-Type confusion, NO authentication
Pattern recognition: workflow automation platforms are becoming prime targets. They have high privileges, store credentials, and connect to everything. One vulnerability gives attackers access to dozens of systems.
Check if you’re exposed:
→ Vulnerable versions: 1.65.0 up to but not including 1.121.0 → Fixed in: 1.121.0 → Latest versions: 1.123.10, 2.1.5, 2.2.4, 2.3.0
Censys found 26,512 n8n instances exposed to the internet. Most are in the US (7,079), Germany (4,280), France (2,655), Brazil (1,347), and Singapore (1,129).
If you run n8n:
→ Update to version 1.121.0 or later immediately → Don’t expose n8n to the internet unless absolutely necessary → Require authentication for all forms you create → Check your instance: is it reachable from outside your network?
There is no workaround. If you can’t patch, take it offline.
n8n is based in Berlin, valued at $2.5 billion, and markets themselves as privacy-first. “We built n8n from the ground up with your data security in mind.” A CVSS 10.0 vulnerability sat in their code for months, and the patch was silent.
Patch your systems.
Hacking is not a hobby but a way of life. 🎯
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.