Notepad++ Supply Chain Attack Full Story
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
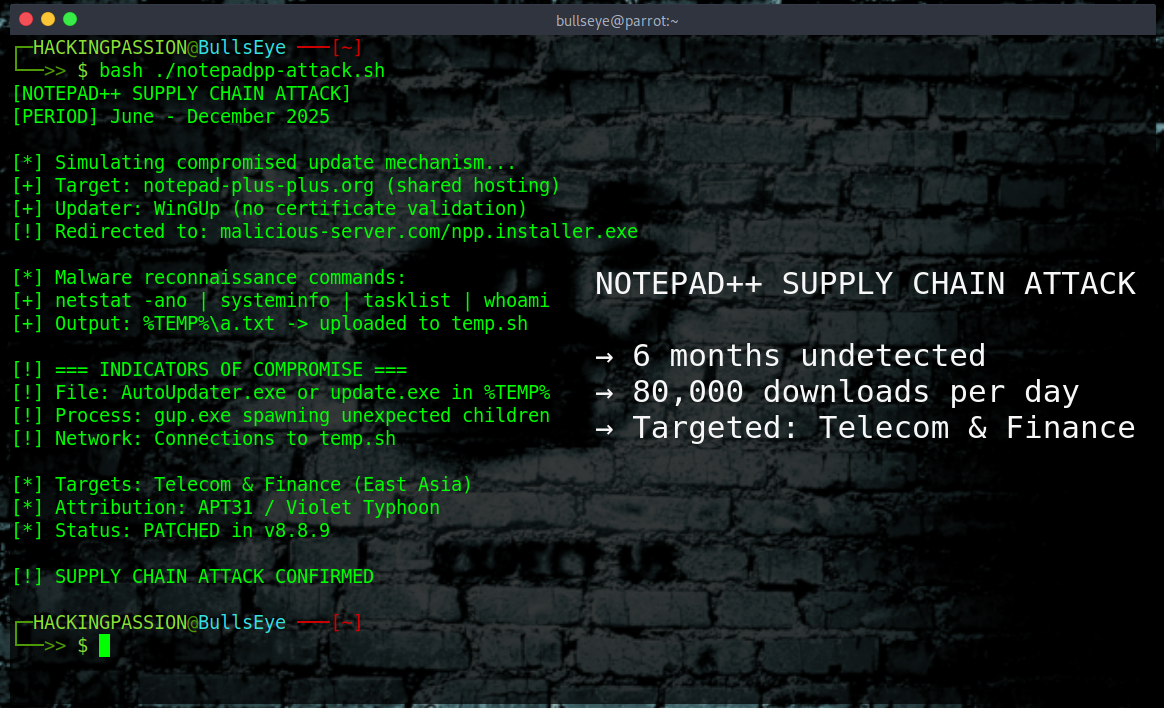
Notepad++ delivered malware for six months. From June to December 2025, the update system was compromised. Millions of people use this software. Some of them clicked update and got spyware instead of a patch. Here is what we now know. 🧐
The attackers did not hack Notepad++ itself, they went after the hosting provider instead. On February 2, 2026, developer Don Ho published the full disclosure of what happened. The website notepad-plus-plus.org sat on a shared hosting server, which means it shared space and resources with other customers on the same machine. Once the attackers broke into that server, they could see all the traffic flowing through it and intercept whatever they wanted.
Here is the part that should make every software maintainer uncomfortable: Notepad++, a tool downloaded 80,000 times per day, was running on a cheap shared hosting plan. Not a dedicated server. Not a VPS with proper isolation. A shared environment where one compromised neighbor means everyone is exposed.
The hosting provider later confirmed something interesting in their incident report. They found no evidence that any other customers on that server were targeted. The attackers specifically searched for notepad-plus-plus.org traffic and ignored everything else. They knew exactly what they wanted, and they had access to everything on that server to get it. The other customers got lucky. They could have been collateral damage but weren’t.
To understand why this attack worked, it helps to know how Notepad++ updates normally function. A component called WinGUp contacts the server and requests a small XML file that contains the download URL for the latest version. WinGUp then fetches the installer, drops it in the temp folder, and runs it. The whole process is designed to be simple and fast, but older versions had a critical weakness: they never verified whether the downloaded file was actually legitimate. No certificate check, no signature validation, just blind trust that whatever came back was the real thing.
The attackers exploited this by sitting inside the hosting infrastructure and waiting. When certain users requested updates, they swapped the download URL in that XML response. Instead of pointing to the real Notepad++ installer, it pointed to their server. The updater grabbed the malicious file and executed it without question, because it had no way to tell the difference.
Security researcher Kevin Beaumont was one of the first to investigate what was happening. He spoke with three organizations that got hit, all of them telecommunications and financial services companies in East Asia. Every single one reported the same pattern: after the initial infection, there were real attackers sitting at keyboards and actively exploring the compromised networks. This was not automated malware blasting out to random targets, it was targeted espionage with humans making decisions in real time.
The malware itself did exactly what reconnaissance malware always does. It dropped a file called AutoUpdater.exe in the temp folder, which is already suspicious because Notepad++ does not use that filename. Then it ran a series of commands to map the environment:
- →
netstat -anoto see all network connections and which processes own them - →
systeminfoto grab hardware specs, OS version, and domain information - →
tasklistto enumerate every running process - →
whoamito identify the current user and their privileges
All of that output was saved to a text file called a.txt, and then the malware used curl to upload it to temp.sh, an anonymous file sharing service that has shown up in other malware campaigns before. Once the attackers had that information, they knew exactly what they were dealing with and could plan their next moves.
Three things made this attack possible.
First, the self-signed certificate. Older versions of Notepad++ used a custom root certificate for code signing, and that certificate was sitting publicly on GitHub for anyone to find. An attacker who grabbed it could sign malicious files that the updater would accept as legitimate.
Second, the lack of proper certificate validation. Even though the updater communicated over HTTPS, it never verified the certificate chain properly. If someone could intercept the traffic, they could substitute their own responses and the updater would accept them without complaint.
Third, and this is the big one: shared hosting. As mentioned earlier, the Notepad++ website shared a server with other customers. One compromised server meant access to all traffic flowing through it.
One detail from the hosting provider’s statement stands out: after the server was patched in September and the attackers lost their initial access, they tried to re-exploit the same vulnerability and failed. They were persistent, they came back to check if the door was still open, but this time it was locked.
The timeline shows how long this went undetected.
- → June 2025: hosting server compromised
- → September: routine maintenance locked attackers out of the server, but they kept credentials for internal services
- → October: a user on the Notepad++ forum noticed
AutoUpdater.exelaunching from the temp folder and running strange commands. First public sign something was wrong - → November: version 8.8.8 forced updates through GitHub
- → December: version 8.8.9 added proper certificate verification. Attackers lost access on December 2
- → February 2, 2026: Don Ho published the full disclosure with the hosting provider’s statement
Multiple researchers attribute this to a group known as APT31, also called Zirconium or Violet Typhoon, which has been active for over a decade and typically goes after intelligence targets rather than money. The targeting pattern fits: telecommunications and finance in East Asia, hands-on-keyboard activity after initial access, selective targeting rather than mass infection.
In cybersecurity, attribution is one of the hardest problems. IP addresses can be spoofed. Tools can be shared. Languages in code can be faked. What we know for sure is how the malware works, not necessarily who is behind it. The operational style points toward state-sponsored activity, but certainty is rare in this field.
One detail worth mentioning: Notepad++ has a history with Chinese censorship. Developer Don Ho has released versions named “Free Uyghur” and “Boycott Beijing,” and Chinese browsers blocked the download page in response. Whether that history played a role here is impossible to prove, but it would be strange not to mention the context.
If Notepad++ is installed on any systems, here is what to check:
- → Look for
gup.exemaking network requests to anything other than notepad-plus-plus.org, github.com, or release-assets.githubusercontent.com - → Check the temp folder for files named
AutoUpdater.exeorupdate.exe, because Notepad++ does not create files with those names - → Look for
gup.exespawning unexpected child processes, since it should only launch explorer.exe and installers that start with npp - → Check logs for any connections to temp.sh
And here is what to do about it:
- → Update to version 8.8.9 or newer immediately
- → Download manually from the official website rather than trusting the built-in updater on older versions
- → Remove the old self-signed root certificate if it was ever installed
- → If any system shows signs of compromise, investigate thoroughly before assuming it is clean
The bigger picture here is that supply chain attacks more than doubled in 2025, and the OWASP Top 10 now lists software supply chain failures as the third biggest security risk. The logic for attackers is simple: why attack a thousand companies individually when compromising one update server reaches them all at once?
Don Ho has since moved the website to a new hosting provider with stronger security practices, added certificate verification and signature checks, and forced all updates through GitHub. The immediate threat is resolved.
Don Ho has maintained Notepad++ for over twenty years, for free. The infrastructure ran on shared hosting. He has since moved to a new provider with stronger security practices. But twenty years of updates and bug fixes for millions of users does not pay for itself.
Want to understand how attackers exploit software update systems and supply chains?
I cover traffic interception, network attacks, and real exploitation scenarios in my ethical hacking course:
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life.
Source: Don Ho - Notepad++ Hijacked by State-Sponsored Hackers
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.