Ollama Security Failure Exposes 175,000 AI Servers to Attackers
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
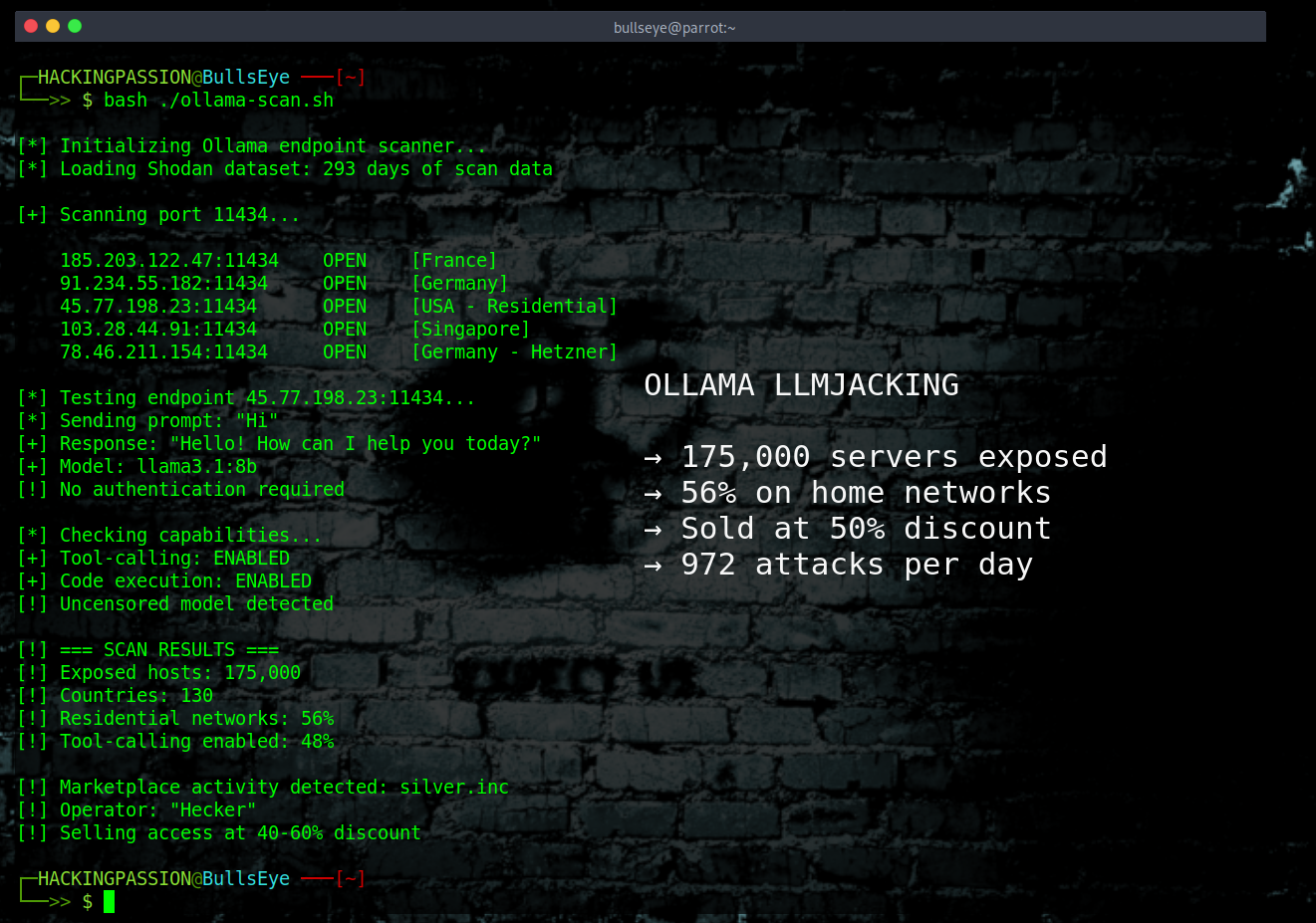
175,000 AI servers wide open to the internet. 130 countries. Attackers are selling access to other people’s hardware at a 50% discount, and using it for spam, phishing, and worse. 🧐
Running AI locally sounds like the safe option. No cloud, no third parties, everything stays on your own machine. So people install Ollama, fire up a language model, and assume they’re good. Except the default settings expose the server to anyone who knows where to look.
Security researchers analyzed 293 days of internet scan data and found 175,000 Ollama instances sitting there with no authentication, no firewall, nothing. In mid-2024, that number was around 1,000. The problem grew 175 times in less than two years.
Scanner bots crawl the internet looking for open Ollama ports, and when they find one, they test it with simple prompts like “Hi” or “How many states are there in the United States?” If the server responds, it goes on a list.
That list ends up at a marketplace called silver.inc, operated by someone who goes by “Hecker.” The admin panel literally displays “Hiii I’m Hecker.” Researchers call this “LLMjacking,” which is basically carjacking but for AI infrastructure.
The marketplace offers access to over 30 AI providers including OpenAI, Anthropic, Google, and Meta, all at 40 to 60 percent below normal prices. Payment accepted in crypto and PayPal. The compute comes from stolen servers, servers like the one running in someone’s home office right now.
Between December and January, security firm Pillar tracked 35,000 attack sessions, which works out to 972 attacks per day for 40 days straight. GreyNoise set up honeypots and caught 91,000 sessions between October 2025 and January 2026. One campaign fired 80,000 enumeration requests in just 11 days, and the source IPs had histories of exploiting over 200 different vulnerabilities. This is organized reconnaissance, not random scanning.
56 percent of these exposed servers run on residential networks, meaning home computers with the kind of IP addresses that banks and services trust because they look like regular users.
Attackers route their traffic through these machines, and suddenly their spam, phishing, and fraud all comes from “trusted” sources. The server owner pays for the hardware, pays for the electricity, pays for the internet connection, and attackers use it all for free while selling access to others.
48 percent of exposed servers have tool-calling capabilities, which means the AI can execute code, access APIs, and interact with other systems. An attacker doesn’t just get free AI, they get a foothold into whatever network that server sits on.
201 servers were running “uncensored” models with all safety guardrails removed, models designed to comply with any request no matter what.
The official Ollama documentation barely mentions security. The default configuration binds to all network interfaces, and most users never change it.
On top of that, multiple critical vulnerabilities have been found in Ollama itself:
- → CVE-2024-37032, nicknamed Probllama, allows remote code execution through a path traversal attack
- → CVE-2024-7773 is another RCE through malicious ZIP files
Patches exist, but researchers estimate only a small minority of exposed servers run the latest version.
How to check if Ollama is exposed:
- → Run:
ss -tuln | grep 11434 - → If it shows
0.0.0.0:11434or:::11434, the server is open to the world - → Fix: set
OLLAMA_HOST=127.0.0.1to allow only local access - → Better: put it behind a reverse proxy with authentication
- → Best: never expose AI infrastructure to the internet without protection
The pattern here is familiar. New technology ships with convenience as the priority, and security comes later if it comes at all. Developers under pressure skip the documentation, IT teams don’t know these servers exist, and attackers find them faster than defenders can patch them.
GreyNoise put it simply: “If you’re running exposed LLM endpoints, you’re likely already on someone’s list.”
This is reconnaissance in action. Finding exposed systems, mapping infrastructure, understanding what’s vulnerable. I cover these techniques hands-on in my ethical hacking course:
Hacking is not a hobby but a way of life.
Research: Gabriel Bernadett-Shapiro (SentinelLabs) & Silas Cutler (Censys)
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.