AI Finds 12 OpenSSL Vulnerabilities Including a 27-Year-Old Bug
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
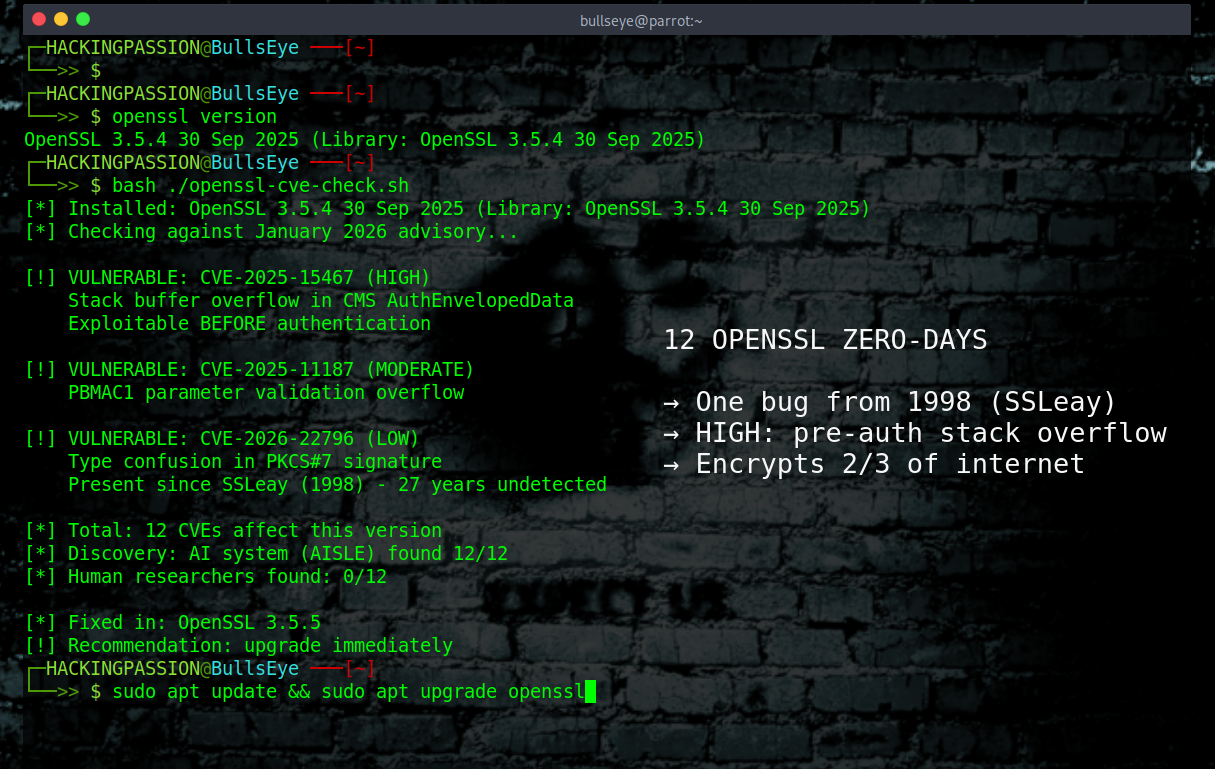
An AI just found 12 zero-day vulnerabilities in OpenSSL. All 12. In a single release. One of those bugs is older than OpenSSL itself, sitting in the code since 1998. 🧐
OpenSSL is the cryptographic library that encrypts roughly two-thirds of all internet traffic. It runs on 95% of IT organizations worldwide. Banks use it. Hospitals use it. Governments use it. Cloud platforms, enterprise applications, operating systems, critical infrastructure. When OpenSSL has a vulnerability, the entire internet has a problem.
This is also one of the most scrutinized codebases in existence. Security researchers have been picking it apart for over 25 years. Automated tools scan it constantly. Finding even one real vulnerability in OpenSSL is rare.
On January 27, 2026, OpenSSL released a coordinated security update. Twelve previously unknown vulnerabilities fixed in a single patch. One rated HIGH severity with potential for remote code execution. Ten rated LOW. One MODERATE.
Every single one was discovered by an AI system.
The company behind it is called AISLE. They started analyzing OpenSSL in August 2025 and reported findings through responsible disclosure. The OpenSSL maintainers confirmed all 12, assigned CVEs, and patched them across seven release branches.
The oldest bug tells the real story.
CVE-2026-22796 is a type confusion vulnerability in PKCS#7 signature verification. When OpenSSL processes signed data, it reads a value without checking what type that value actually is. Feed it malformed data and the code dereferences an invalid pointer. Crash. Denial of service.
This bug does not come from OpenSSL. It comes from SSLeay, the original SSL implementation written by Eric Young in Australia starting in 1995. When Young and Tim Hudson left to join RSA Security in late 1998, volunteers forked their code and created OpenSSL. The first release was December 23, 1998.
CVE-2026-22796 was already in that code. It survived the fork. It survived 27 years of development, audits, and security research. It took an AI to find it.
Three other vulnerabilities in this release also date back to 1998-2000. Quarter-century-old bugs in the most reviewed cryptographic library on the planet.
The HIGH severity bug is the dangerous one.
CVE-2025-15467 is a stack buffer overflow in CMS AuthEnvelopedData parsing. CMS is the Cryptographic Message Syntax, used for things like encrypted email and signed documents. When OpenSSL parses an encrypted message using AEAD ciphers like AES-GCM, it copies the initialization vector into a fixed-size buffer on the stack.
The problem: it does not check if the IV actually fits.
An attacker can craft a message with an oversized IV. OpenSSL copies it anyway and overflows the buffer. Stack-based overflow means potential code execution.
The nasty part is when this overflow happens. It triggers before any cryptographic verification. No valid key material required, no authentication needed. Just send a malformed message to anything that parses CMS content. S/MIME email processors, document verification systems, anything handling encrypted payloads.
Whether this leads to actual code execution depends on platform mitigations like ASLR and stack canaries. But the primitive is there, and that is what attackers look for.
The other vulnerabilities spread across the codebase.
CVE-2025-11187 hits PKCS#12 files, the format used to bundle certificates and private keys. Missing validation on password-based MAC parameters lets an attacker trigger another stack buffer overflow.
CVE-2025-15468 crashes QUIC protocol handling. Send an unknown cipher suite to an application using QUIC and the code dereferences NULL.
CVE-2025-15469 silently truncates files larger than 16MB when signing with post-quantum algorithms like ML-DSA. The signature covers the first 16MB. Everything after that is unauthenticated but the tool reports success.
CVE-2025-69418 is a cryptographic failure in OCB mode on hardware-accelerated systems. The last 1-15 bytes of a message can be left unencrypted and unauthenticated. The encryption literally does not cover the end of the data.
CVE-2025-66199 lets attackers force 22MB memory allocations per TLS 1.3 connection through certificate compression. Enough connections and the server runs out of memory.
The rest are various crashes through NULL pointer dereferences and type confusion bugs. Lower severity but still real vulnerabilities that got CVE identifiers from a project known for being conservative about what counts as a security issue.
AISLE did not just report these bugs. Their AI system proposed patches for 5 of the 12 vulnerabilities, and the OpenSSL maintainers accepted them into the official release. They also caught 6 additional bugs in development branches that got fixed before ever shipping to users.
The timing makes this story even more interesting.
One day before the OpenSSL release, curl announced it was shutting down its bug bounty program. Curl is installed on over 10 billion devices. The bug bounty ran since 2019 and paid out over $90,000 for 81 genuine vulnerabilities.
It ended because of AI-generated garbage. People pointing AI tools at code, getting output they do not understand, and submitting it for bounty money. The flood of useless reports was drowning the volunteer security team. Twenty submissions in the first three weeks of 2026 alone, none of them actual vulnerabilities.
Garbage in, garbage out. The tool does not matter, the skill behind it does.
That contrast is the real story here. AI in security is not good or bad. It depends entirely on who uses it and how. The gap between garbage and groundbreaking is getting wider.
For anyone running systems that depend on OpenSSL, here are the versions to upgrade to:
- → OpenSSL 3.6 users should upgrade to
3.6.1 - → OpenSSL 3.5 users should upgrade to
3.5.5 - → OpenSSL 3.4 users should upgrade to
3.4.4 - → OpenSSL 3.3 users should upgrade to
3.3.6 - → OpenSSL 3.0 users should upgrade to
3.0.19 - → OpenSSL 1.1.1 users need
1.1.1ze(premium support only) - → OpenSSL 1.0.2 users need
1.0.2znfor some fixes (premium support only)
If there are bugs this old in the most audited cryptographic library on earth, they exist everywhere else too. The codebase humans can review is smaller than the codebase that actually runs. That gap keeps growing.
Understanding encryption, how attackers find and exploit vulnerabilities, and how real CVE hunting works is core security knowledge. I cover encryption with OpenSSL, exploitation techniques, and how to analyze targets in my ethical hacking course:
Hacking is not a hobby but a way of life.
Research: Stanislav Fort (AISLE) → https://www.lesswrong.com/posts/7aJwgbMEiKq5egQbd/
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.