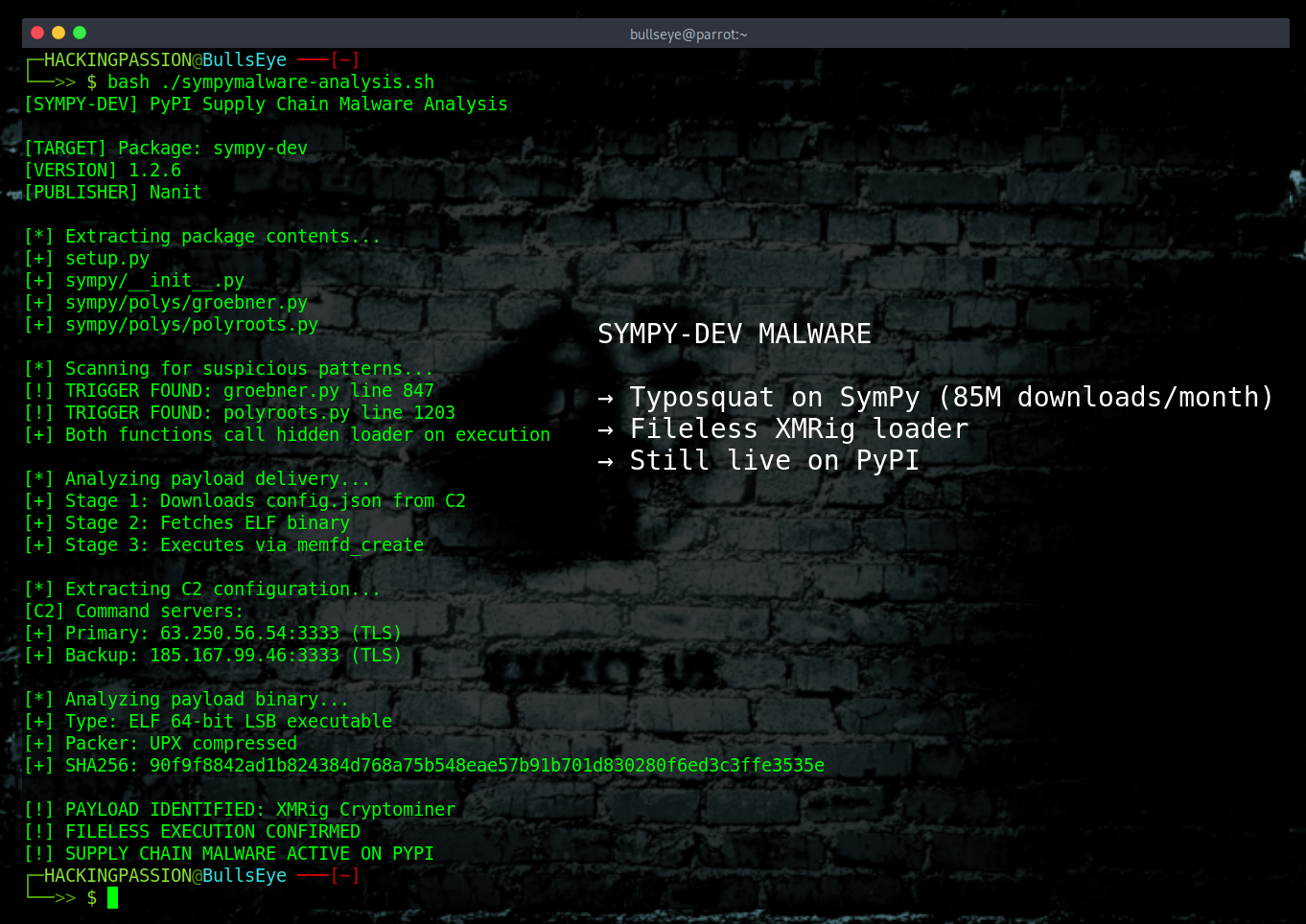
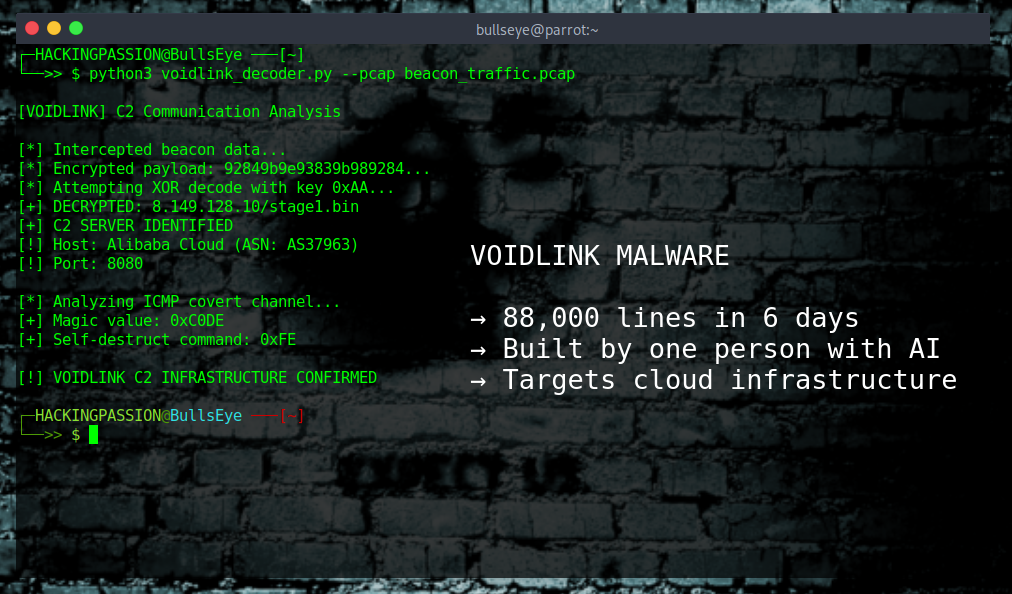
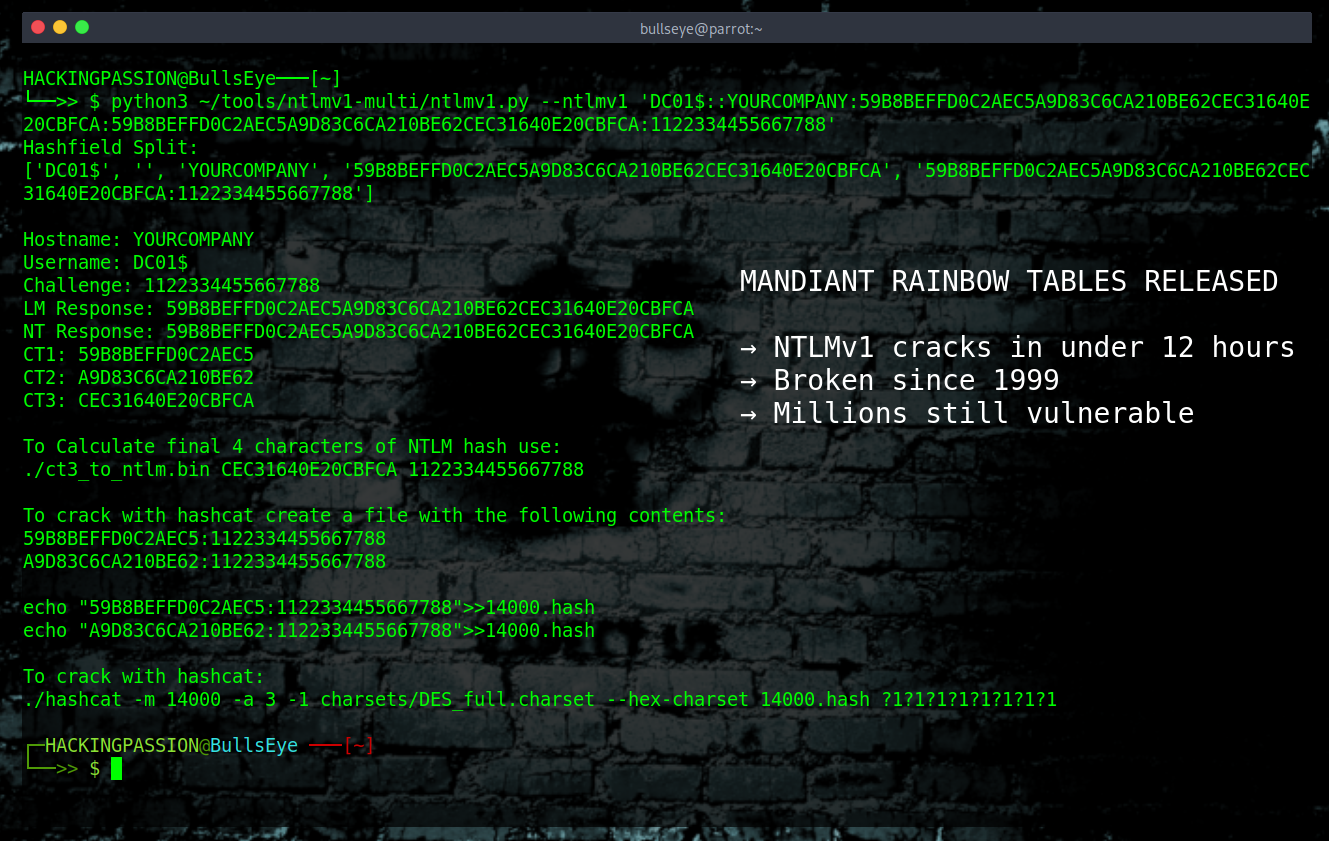
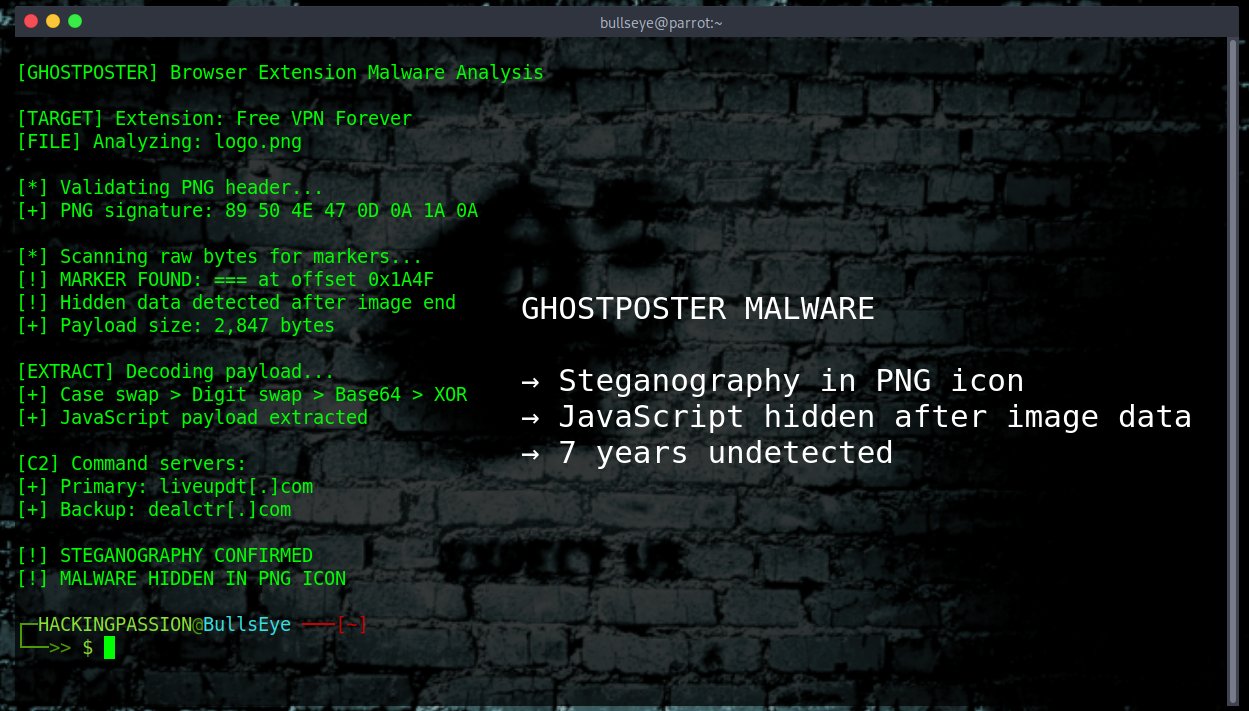
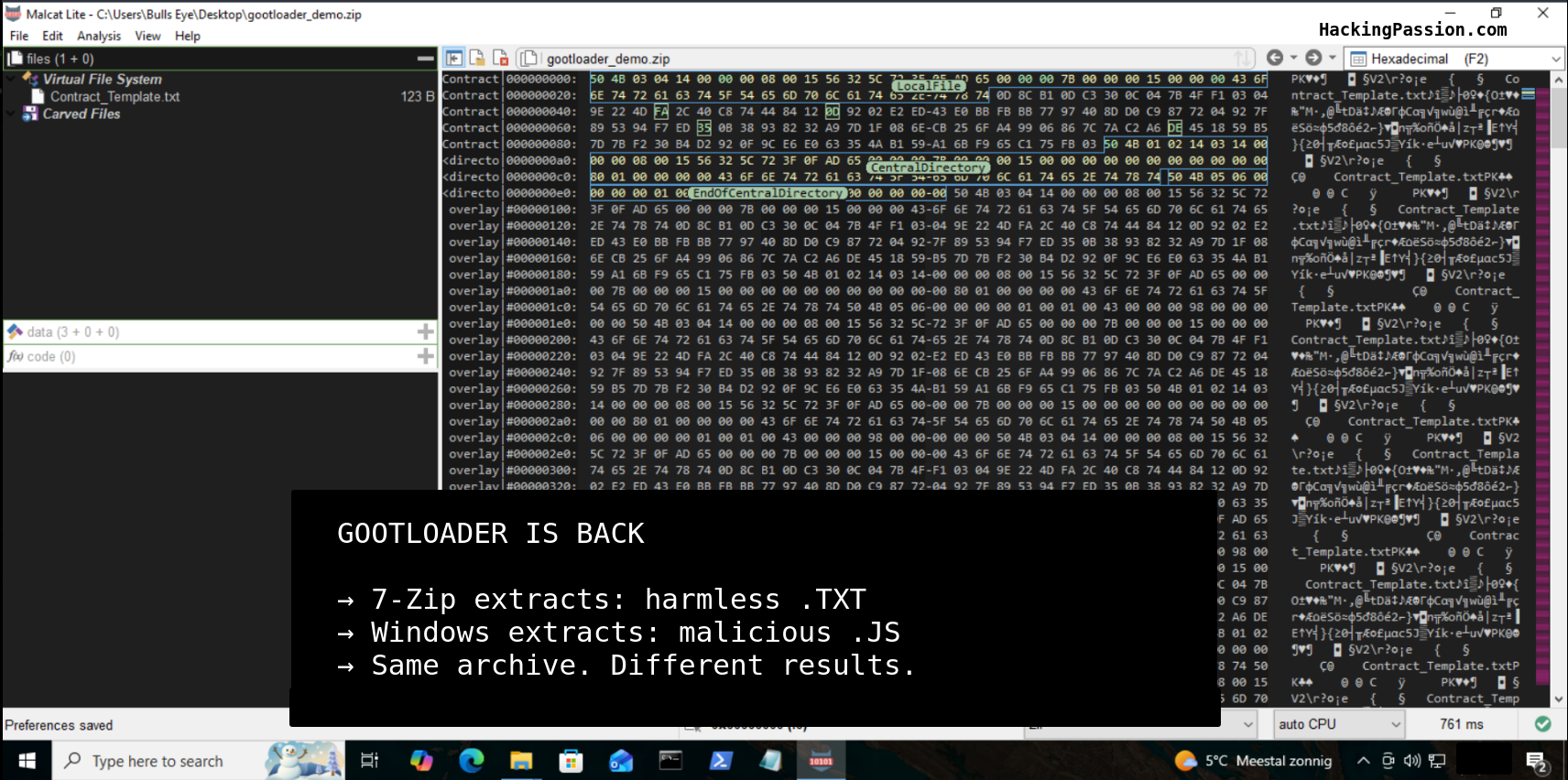
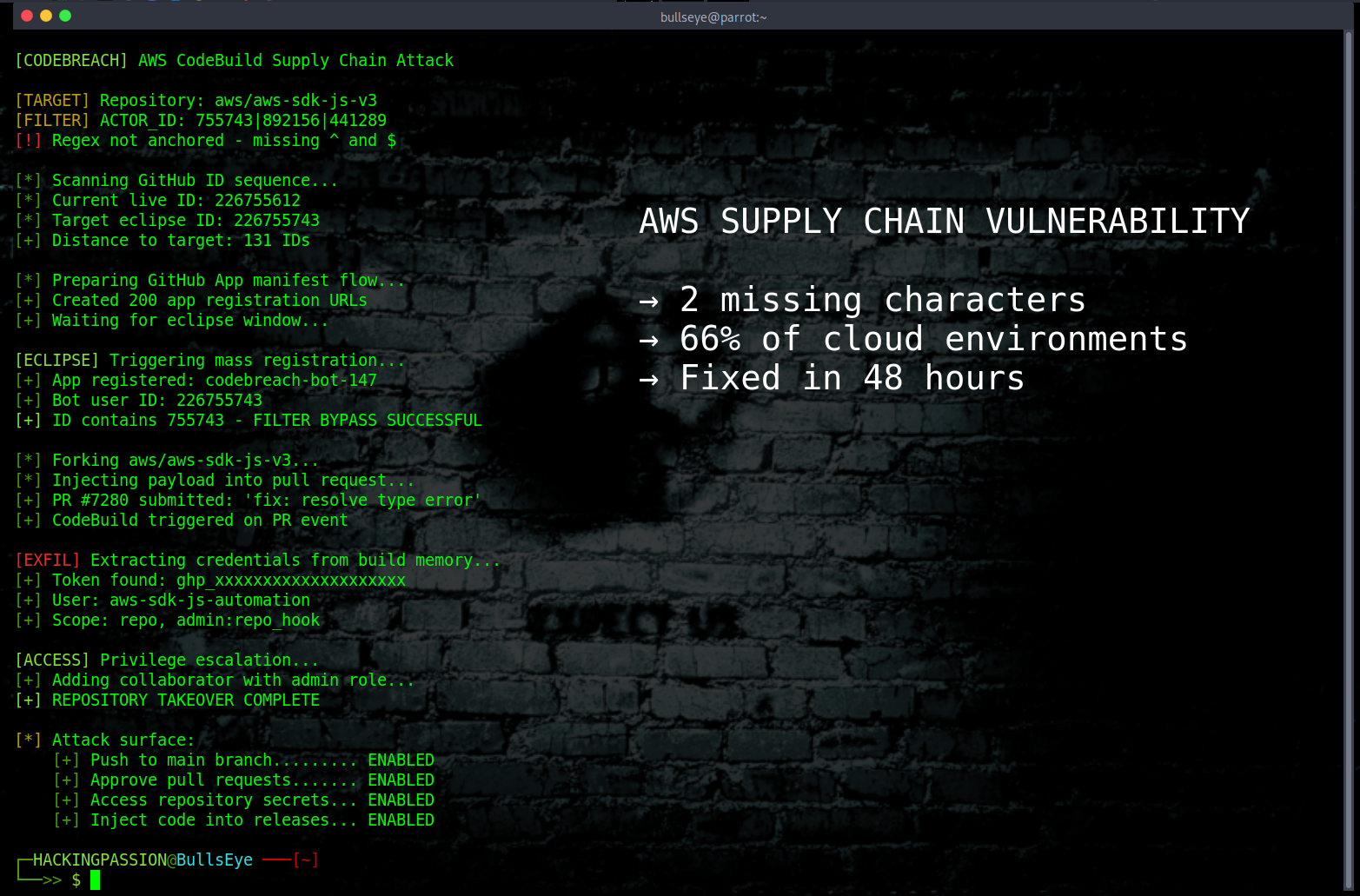
Linux Inside a PDF
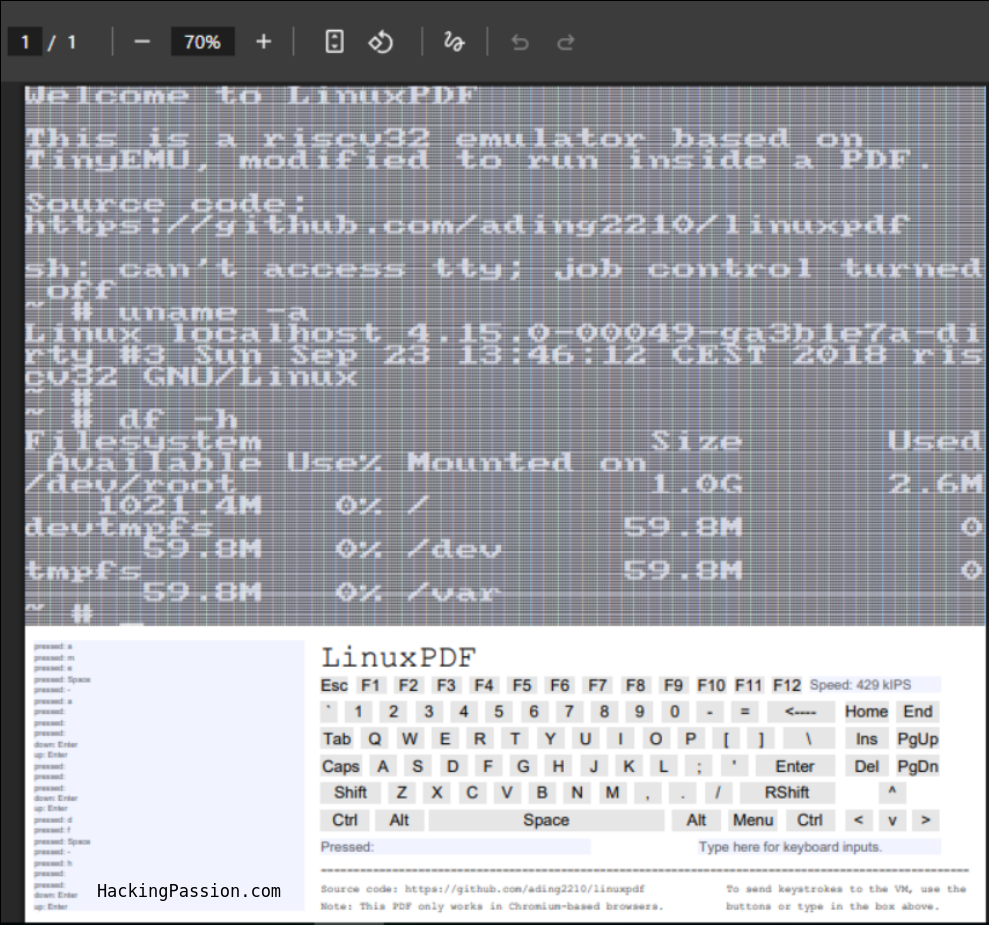
Linux running inside a PDF. An actual working operating system with a terminal where you can type commands. Open a PDF in Chrome. Wait 30 seconds. You now have a working Linux terminal. No installation, no software, just a 6MB file that boots an entire operating system.
A high school student named Allen built this, the same kid who previously crammed Doom into a PDF. Before that he made tools to bypass school software restrictions and exploits to boot Linux on locked-down Chromebooks.