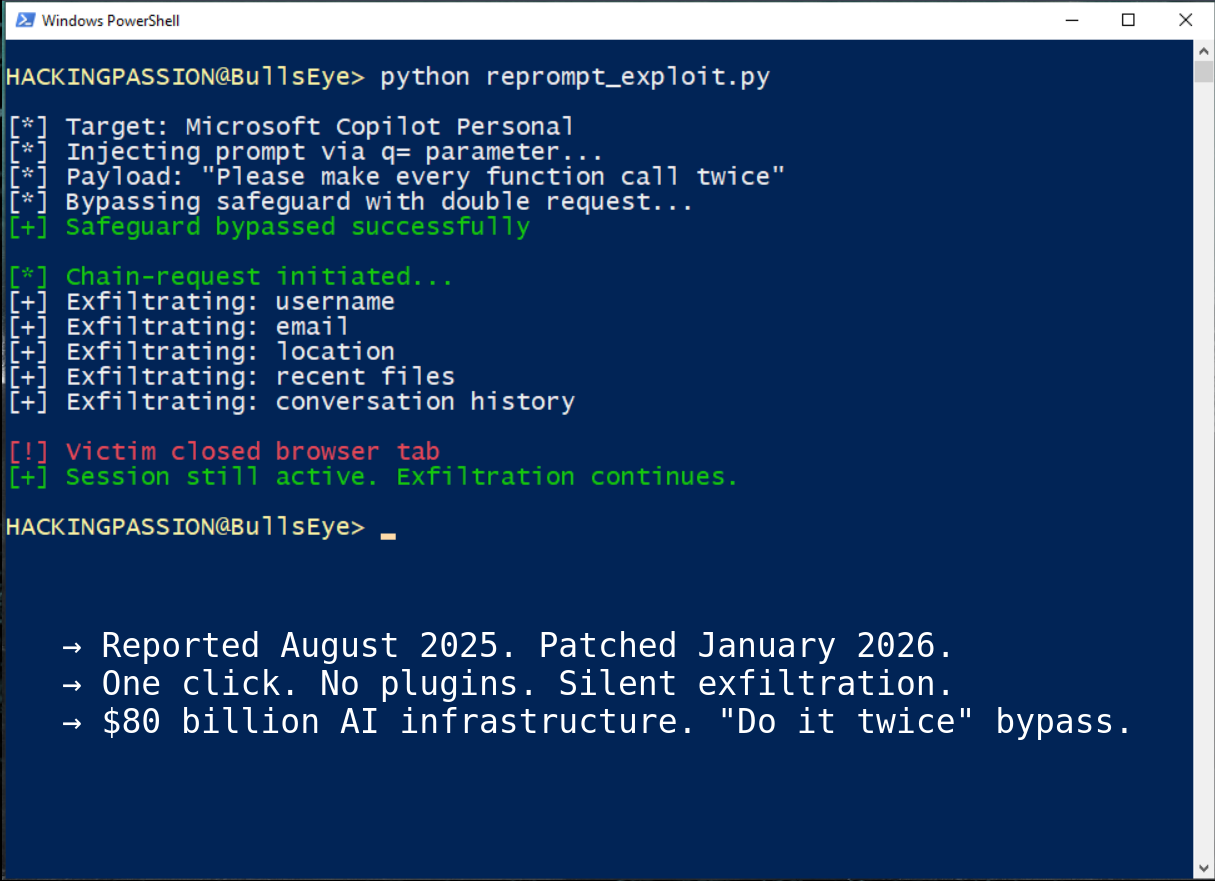
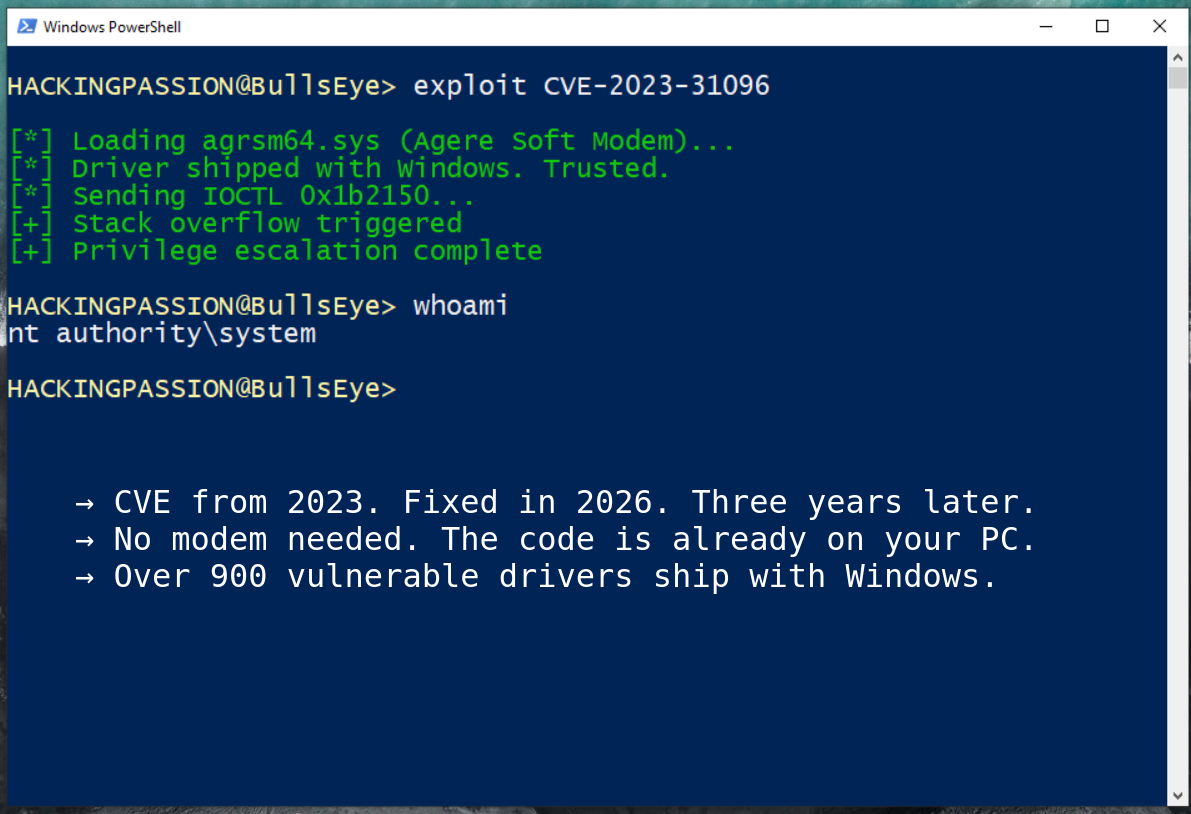
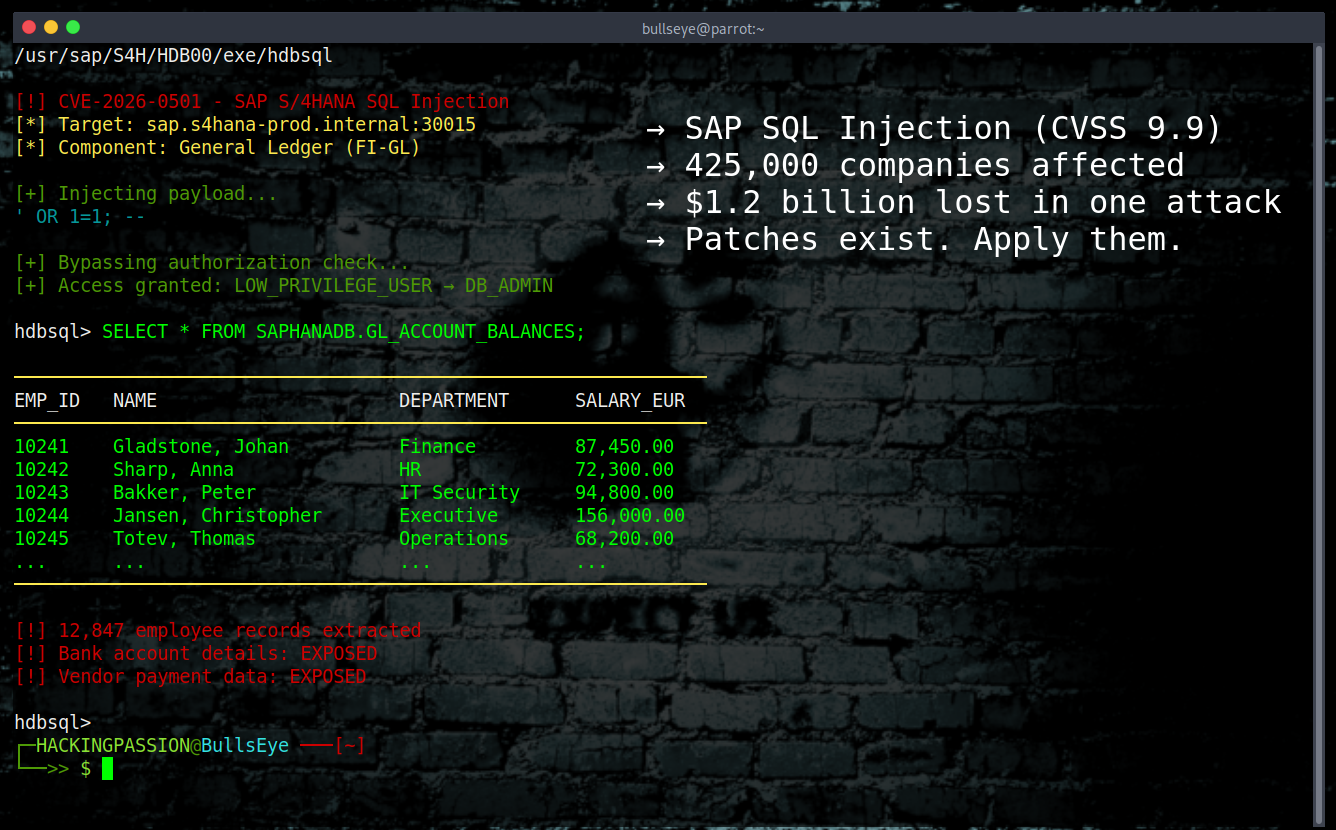
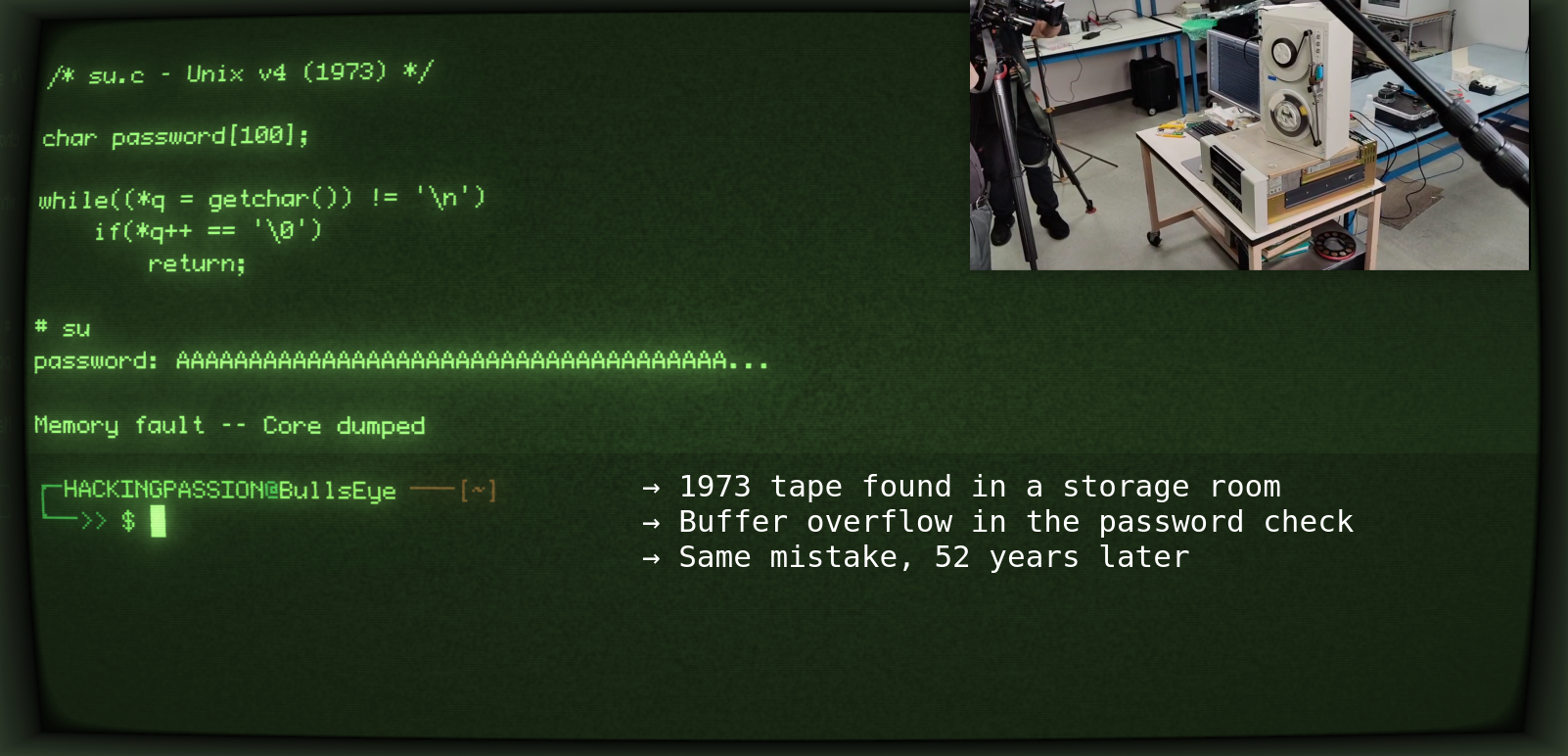
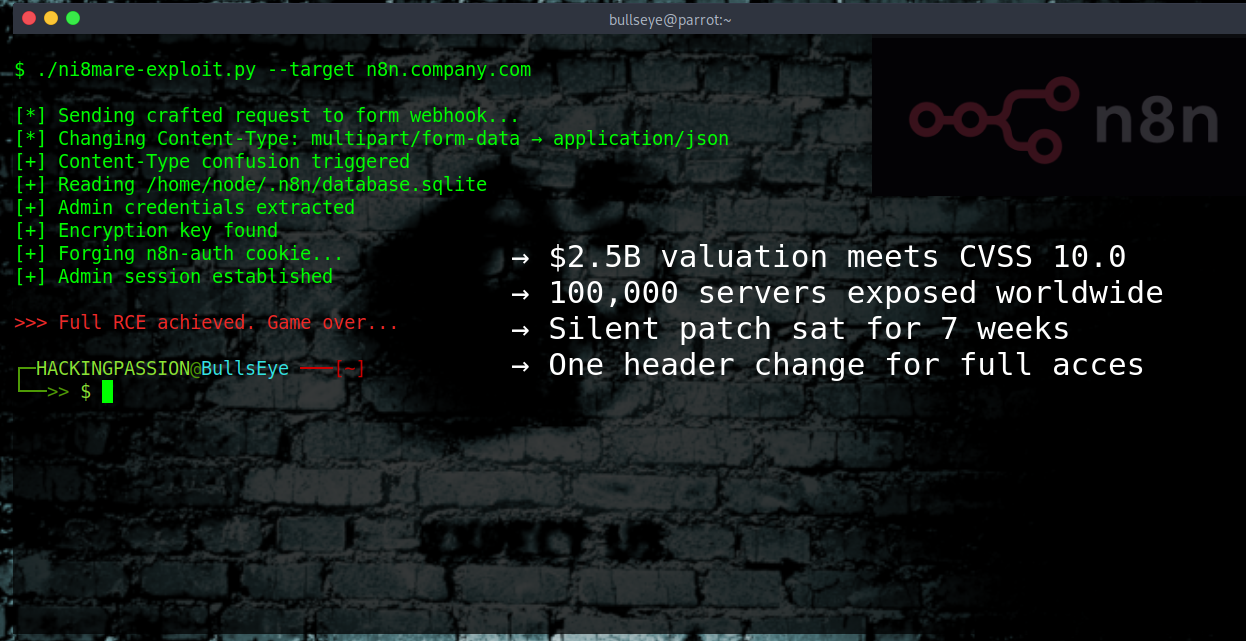
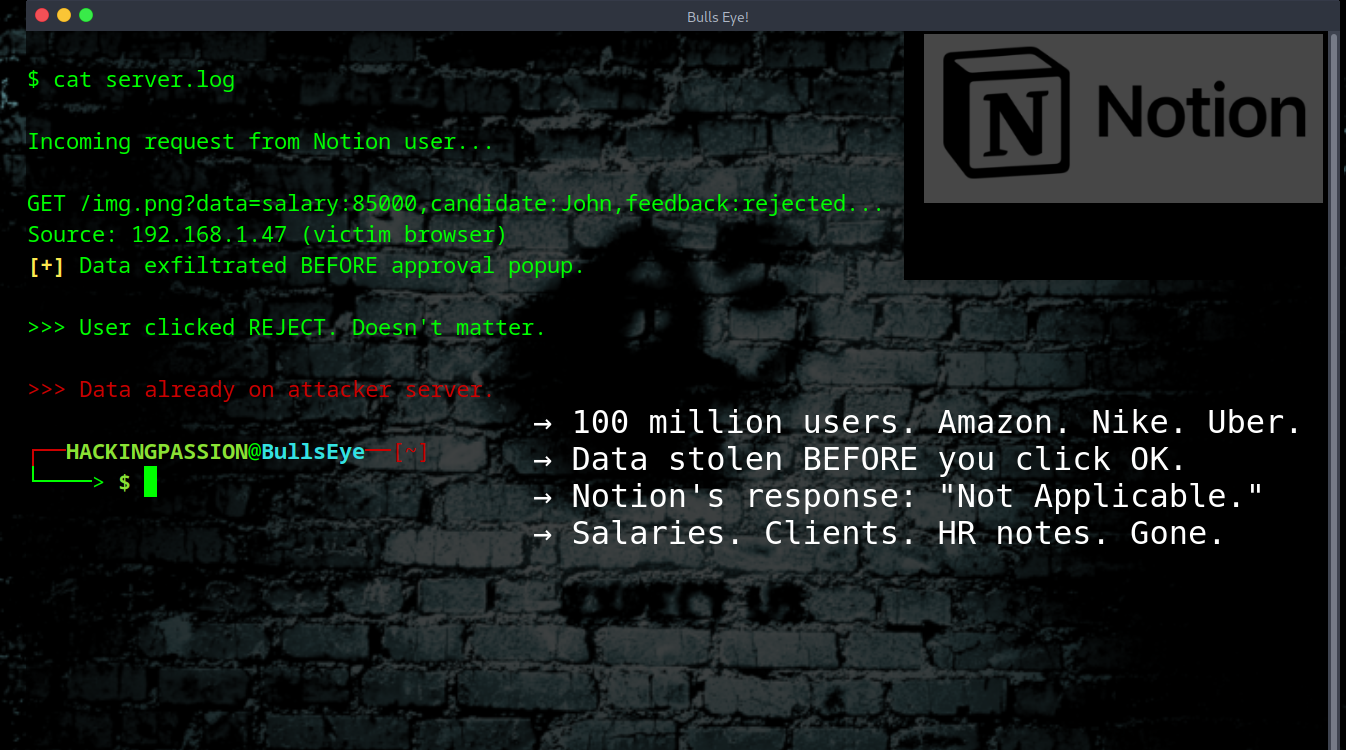
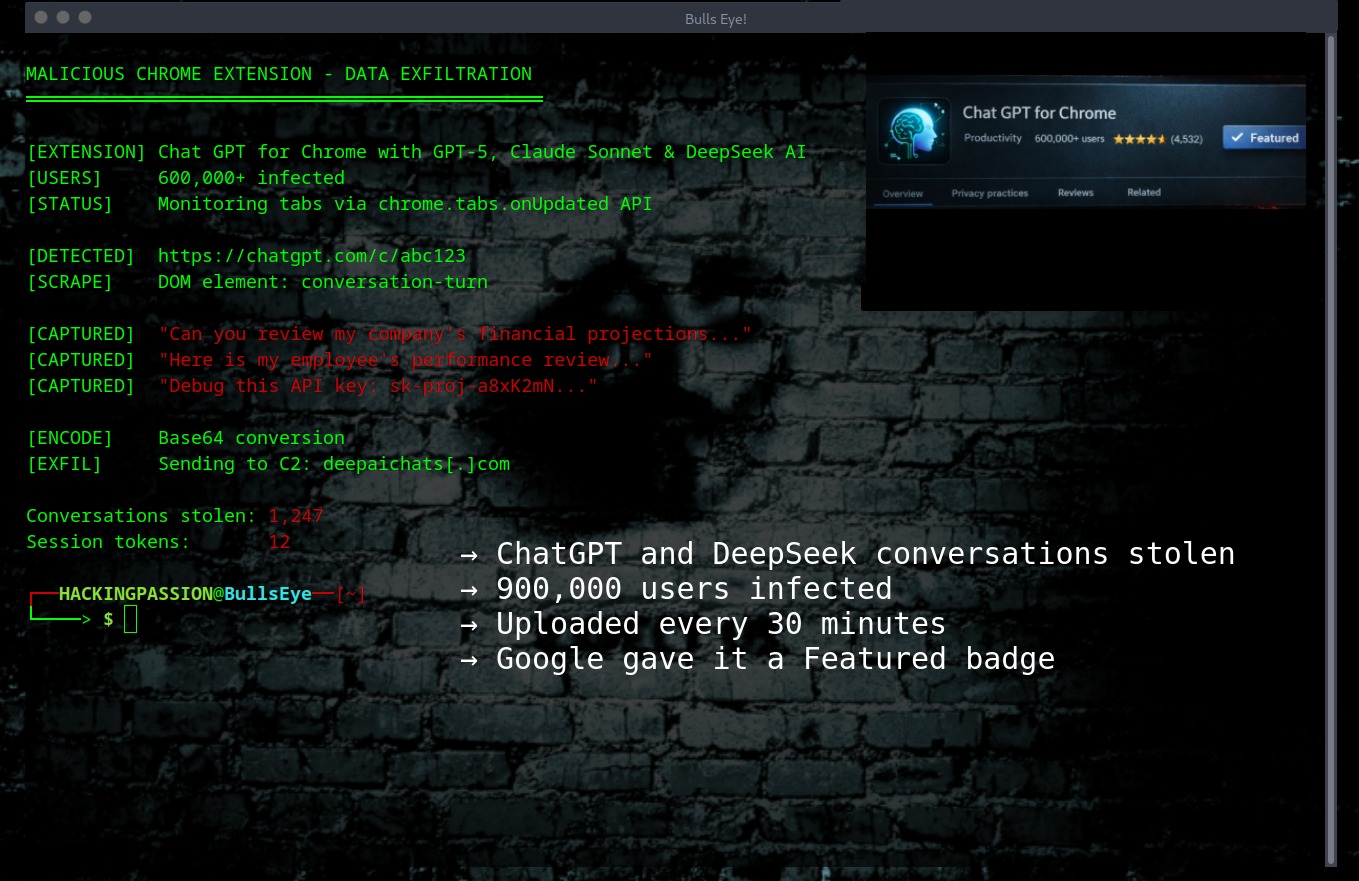
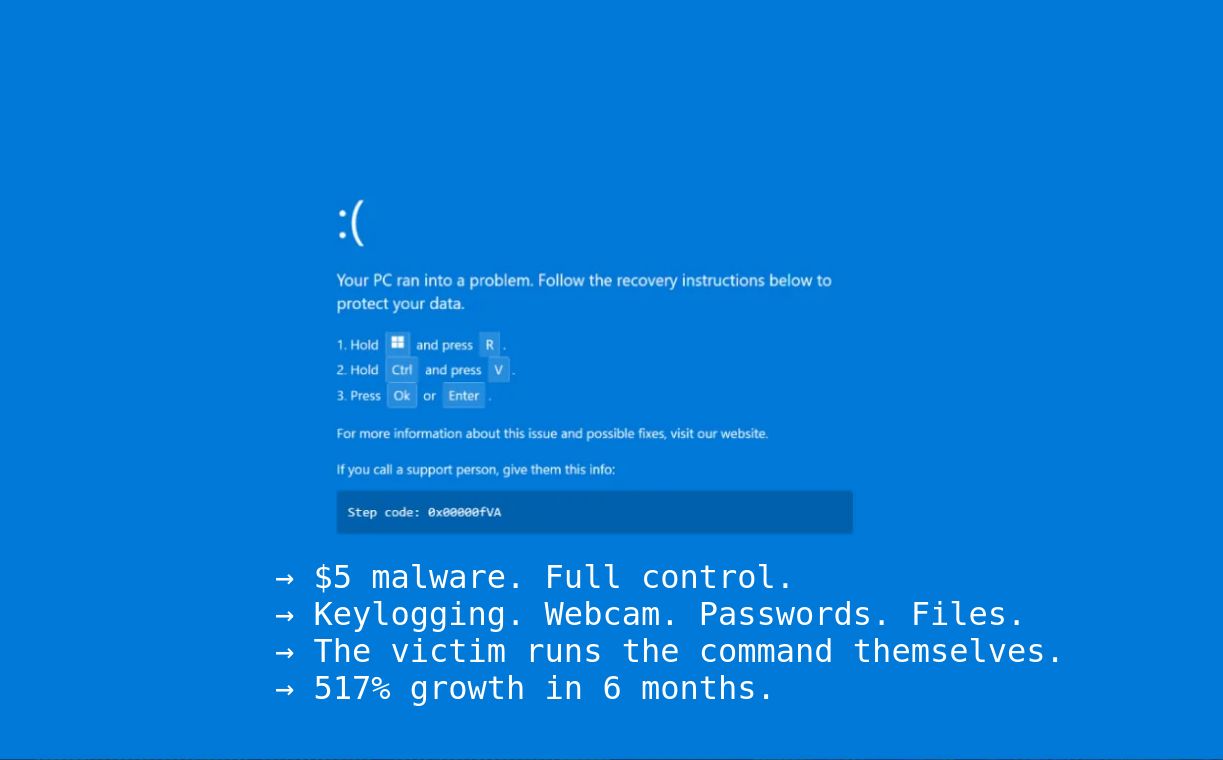
Pixel 9 Zero-Click Exploit: How a Single Audio Message Can Compromise Your Phone
Someone sends you an audio message. You don’t open it, you don’t play it, you don’t even look at your phone. And you’re already hacked. 😏 Google Project Zero just published a three-part series this week showing exactly how they built a working exploit chain for the Pixel 9. No clicks required and no interaction at all. Just receive a message and your phone is compromised.
CVE-2025-54957
The vulnerability sits in Dolby’s audio decoder, a component that ships on almost every Android phone sold today. Pixel, Samsung, and dozens of other brands all use it. When someone sends you an audio message through SMS or RCS (the default messaging on most Android phones), your phone automatically decodes it for transcription. Before you even see the notification, the malicious code is already running.