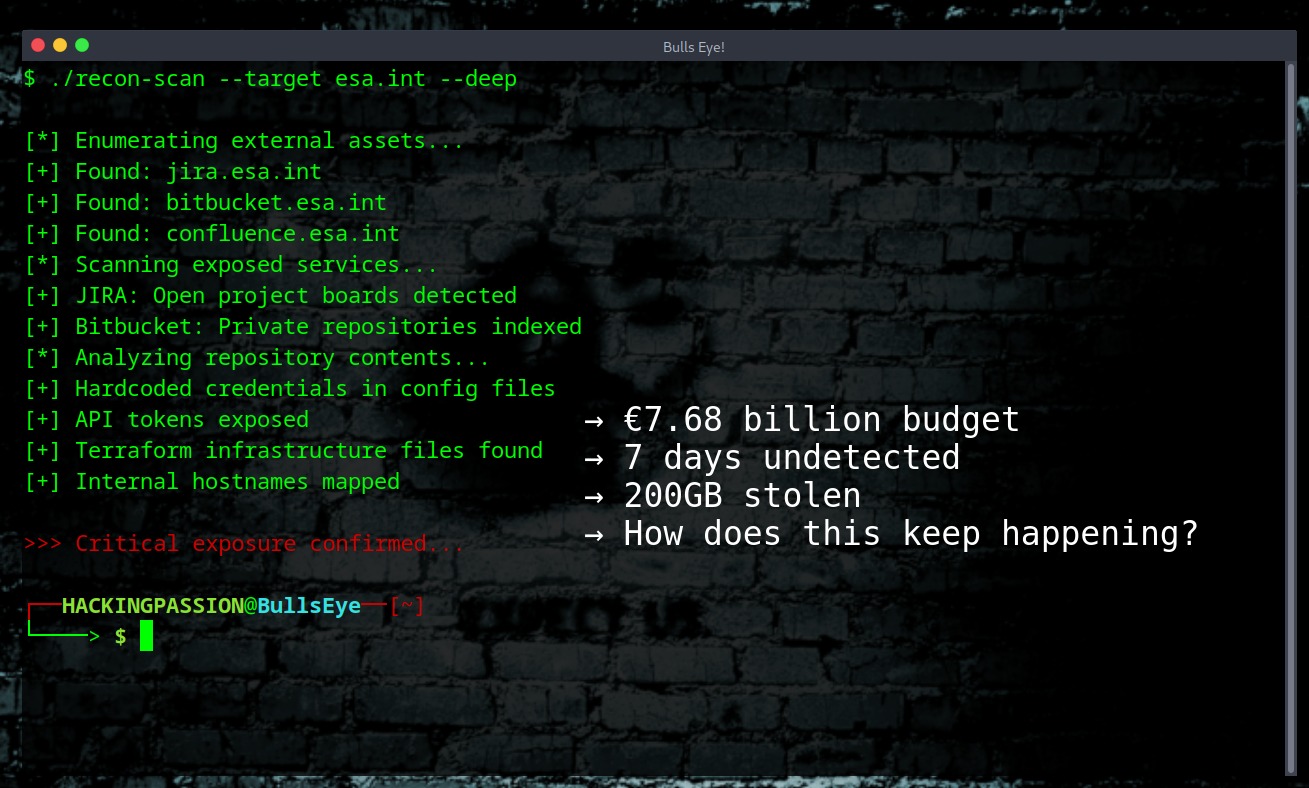
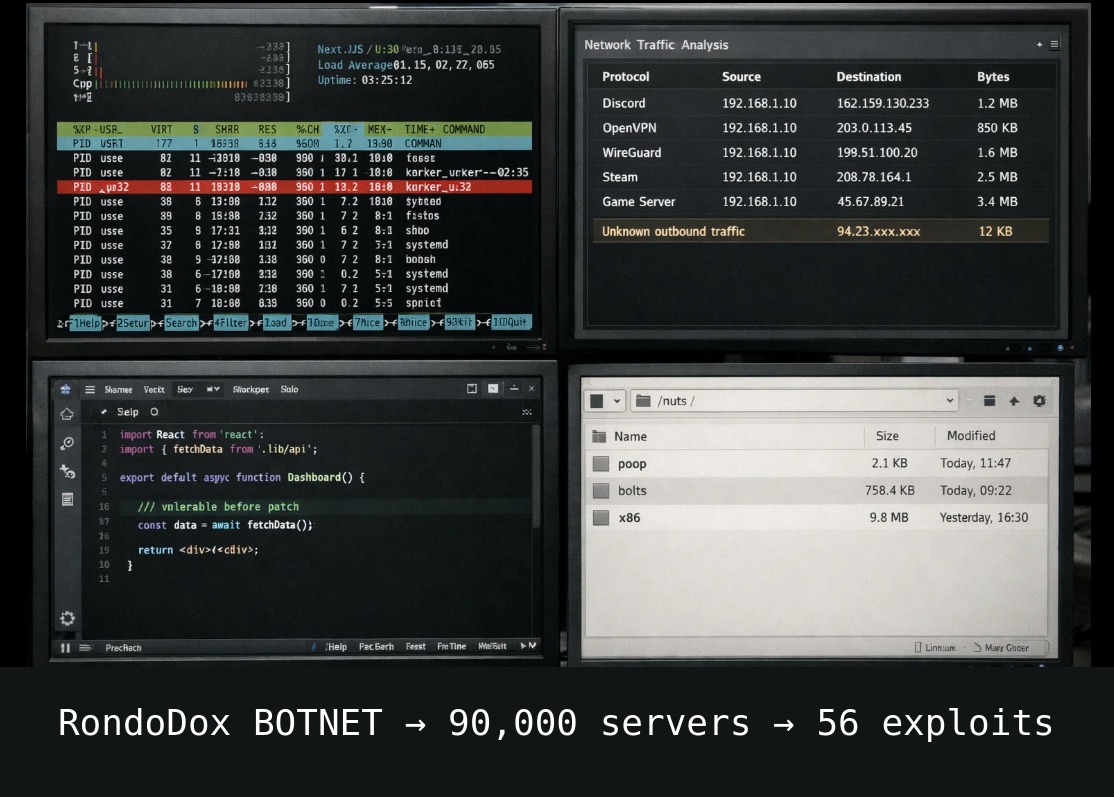
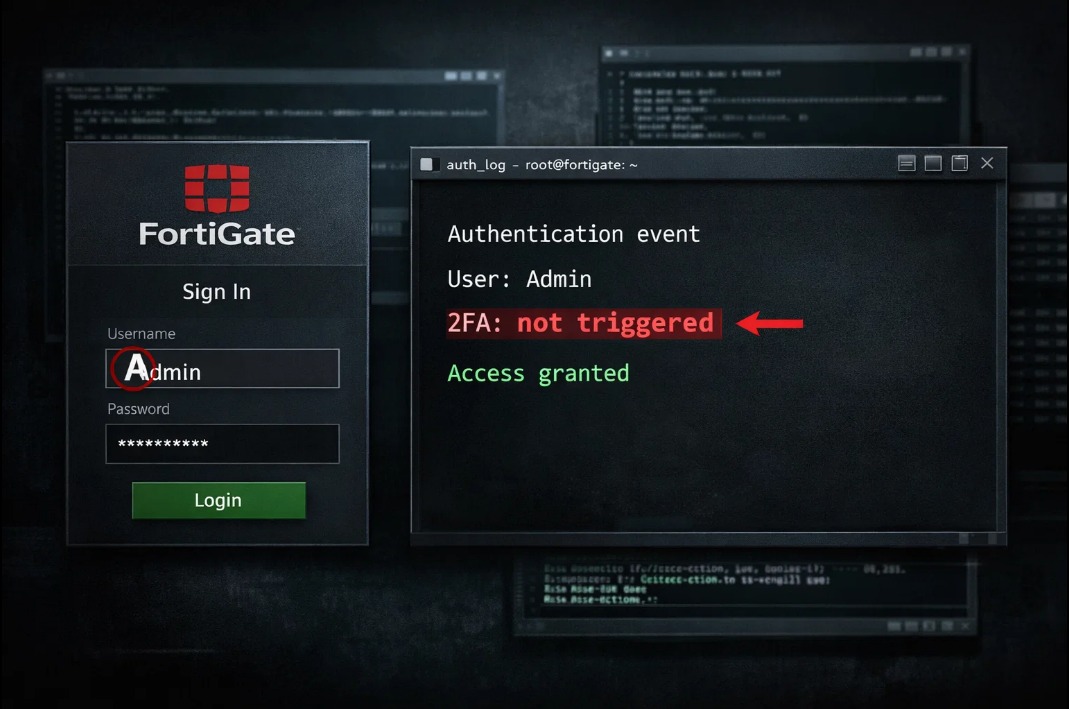
European Space Agency Hacked: 200GB Stolen in 7 Days, Data Sold on FBI Honeypot
€7.68 billion budget. 3,000 staff. A brand new Cyber Security Operations Centre opened. A hacker spent 7 days inside their systems downloading 200GB of data. Data for sale on FBI honeypot 😏 On December 18, a hacker using the alias “888” got into ESA servers. JIRA project management. Bitbucket code repositories. Internal documentation systems. For seven days, nobody noticed.
On December 26, screenshots appeared on BreachForums. On December 30, ESA finally confirmed the breach.