HackingPassion.com
Hacking is not a hobby but a way of life ♥
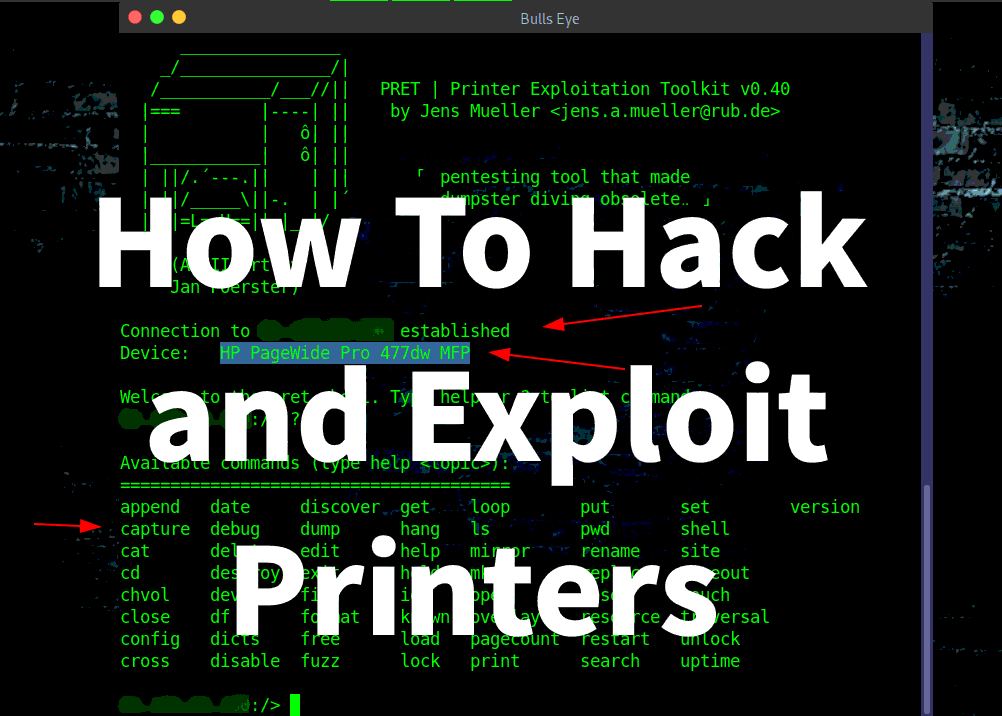
A Step-by-Step walkthrough..! In this article and video, I will show you how to hack and exploit printers. How easy it is to hack, how to get full control, capture, and start sending documents our way. So all future print jobs that are going to come across the printer we’ve connected to which are going to start spooling over.
Why I chose to show you this Again… I chose to show you this, because it is so incredibly easy to hack printers, and through this hack to get further in systems and can cause incredible damage.
Windows is a common operating system used by billions of people. And because of that, there are always many vulnerabilities on Windows.
Because in the future I will use, show and exploit a lot of those vulnerabilities, Therefore I think it is necessary to show the setup of Windows in VirtualBox.
For beginners, but also for advanced people who like to watch and discover maybe something new.
“Difference between a virus and windows?
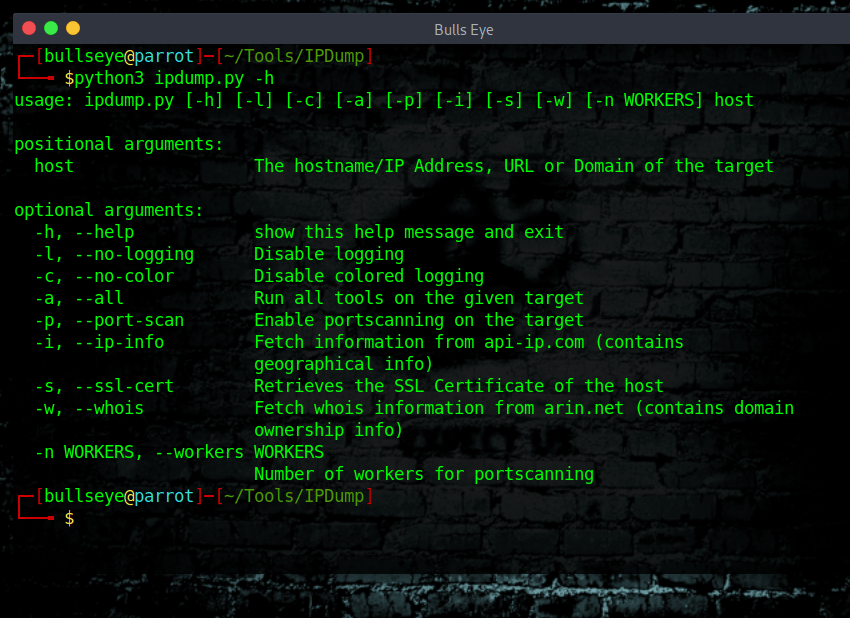
IPDump is a python utility for quickly generating reports for IP Addresses, Websites, and domains. I also show you how to save the terminal output to a file. (The tool is made by bruceybonus01)
Current features Geolocation Information SSL Certificate Fetching WHOIS Information Portscanning Install 1 sudo git clone https://github.com/bruceybonus01/IPDump.git 1 cd IPDump 1 pip3 install -r requirements.txt 1 python3 ipdump.py -h Usage Help Menu 1 python3 ipdump.py -h 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 usage: ipdump.
What is the Dark Web? In this article and video, I will cover how to install Tor on (Kali) Linux and Windows, explain The Dark Web, What is The Hidden Wiki. The Dos and Don’ts to stay anonymous. Install Deep Explorer to make searching easier on the Deep Web.
The differences between Surface Web, Deep Web, and the Dark Web What is the Surface Web As you can see in the image, the Surface Web would only consist of 4% of the web.
In this article and video, I will show you how to install Kali Linux 2020.1 on VirtualBox. Also, install a single boot with Kali Linux. I will cover some big changes that have been made with this new release.
“Kali Linux is an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.”
Kali Linux 2020.1 Release On 28 January 2020, Kali has kicked off with the first release of the decade, Kali Linux 2020.
DARK EAGLE is an all in one tool for Information Gathering and Vulnerability Scanning written in PHP by NANDYDARK.
In the video down below, you can see how to install DARK EAGLE and how this tool is working.
Scans That You Can Perform Using DARK EAGLE Basic Scan Site Title IP Address Web Server Detection CMS Detection Cloudflare Detection robots.txt Scanner Whois Lookup Geo-IP Lookup Grab Banners DNS Lookup Subnet Calculator Nmap Port Scan Sub-Domain Scanner Sub Domain IP Address Reverse IP Lookup & CMS Detection Hostname IP Address CMS Error Based SQLi Scanner HTTP Response Code Site Title Alexa Ranking Domain Authority Page Authority Social Links Extractor Link Grabber WordPress Scan Sensitive Files Crawling Version Detection Version Vulnerability Scanner Crawler Version 2.
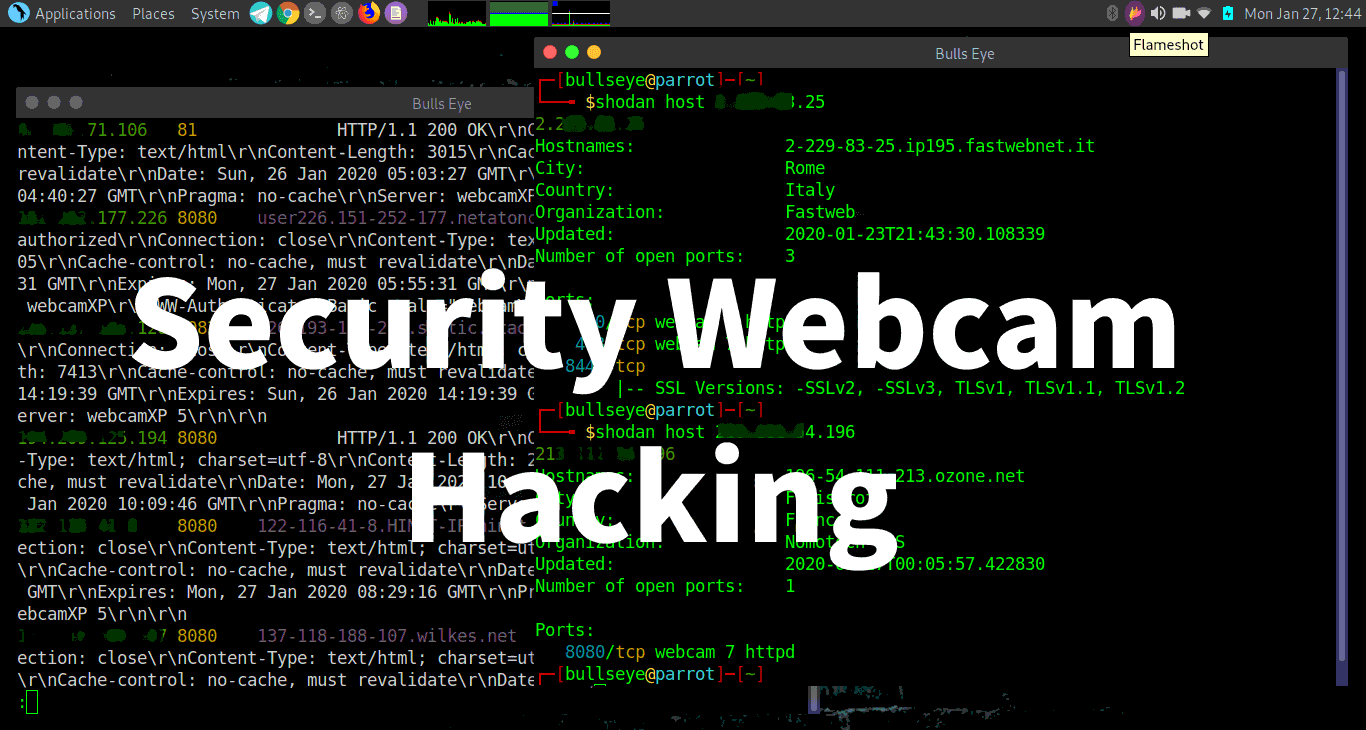
Security webcams are often way too easy to hack. In this article + video I show you how this is done. How simple it is to hack a lot of cameras. After many years, it still seems there a few people who are told what is security. Or is it that most people just don’t know what the consequences might be and just ignore the warnings?
One of the big ironies of life can be that the devices we create to protect us, can sometimes be used against us.
The end of Windows 7 is rapidly approaching. After January 14, 2020, Microsoft will no longer provide security updates or support for Windows 7..! So what should you do? Buy a new computer with Windows 10? Upgrade the current system to Windows 10 or switch to Linux?
I will try to list the pros and “some” cons for you. Why should you upgrade to Linux right away as an ethical hacker.
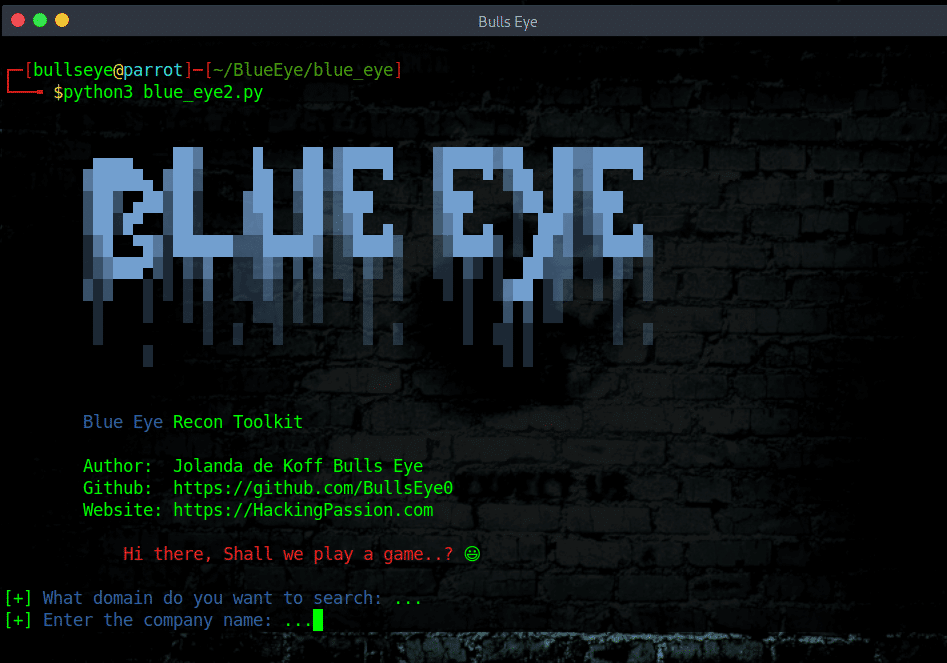
Blue Eye is a Recon Toolkit script I made in python3. Blue Eye shows the subdomain resolves to the IP addresses, ports and headers, company email addresses and much more ..!
The Blue Eye script shows the: Subdomain resolves to the IP addresses Open Ports HTTP Header Mail Servers DNS Text Records Nameserver Records Sites of interest “email, okta, webmail and slack” Lists of GitHub user pages List of possible company email addresses harvested from GitHub user pages and from DuckDuckGo and Linkedin searches The Subdomain resolves to the IP addresses.
Some of the best places to learn ethical hacking. The best vulnerable websites to exercise your hacking skills whether you are a hacker, cybersecurity, pen-tester or still a n00b.
These vulnerable websites are great for developing our minds, increasing our capacity to solve problems, new innovative ideas come to our minds. Also, you will face brainfuck a lot of difficulties. Never give up always try to give your best. Because if you want to be a professional hacker, then you must know about the hacker attitudes and …