Fake GitHub Exploits Target Security Researchers: Download a PoC, Get Malware
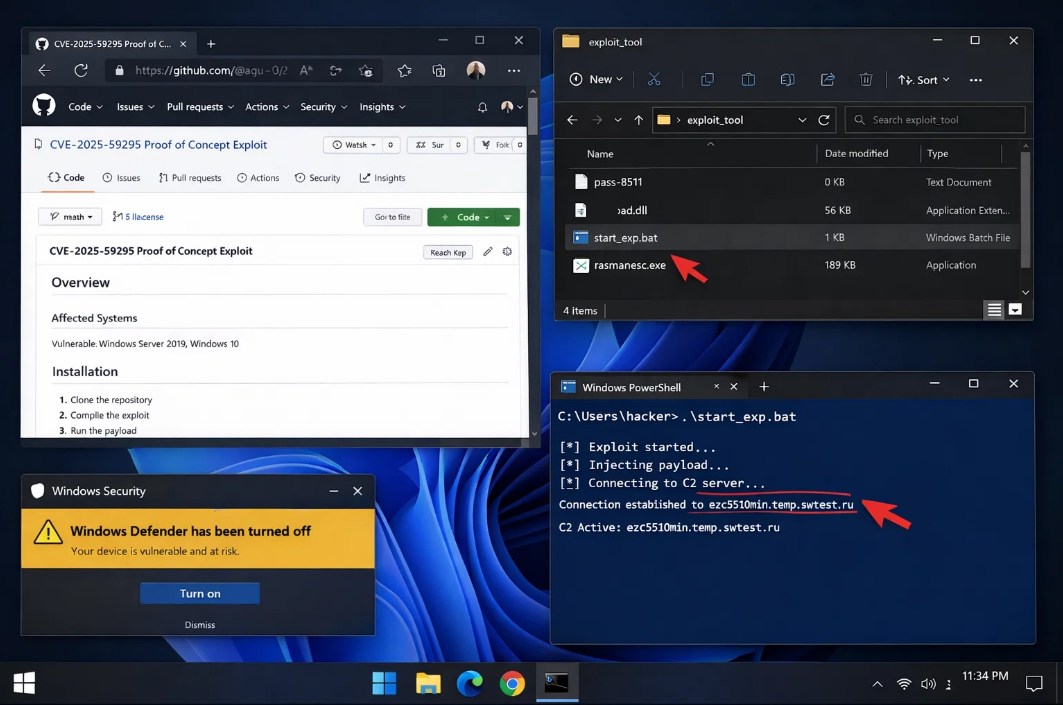
Attackers are targeting security researchers through GitHub. You downloaded a proof-of-concept exploit from GitHub. Professional README. Detailed instructions. Real CVE number. Except it’s malware. 😱 And now your system is compromised.
Kaspersky published their findings on December 23, 2025.
Attackers are creating GitHub repositories with fake exploits for real vulnerabilities. CVE-2025-59295 (CVSS 8.8), CVE-2025-10294 (CVSS 9.8), CVE-2025-59230 (CVSS 7.8). Fake exploits that install malware.
Kaspersky identified 15 malicious repositories pushing this malware. GitHub has removed them, but new repositories will pop up under different account names.