HackingPassion.com
Hacking is not a hobby but a way of life ♥
Ghost Eye is an Information Gathering - Footprinting and Reconnaissance Tool I made in Python 3. It includes some important tools for Information Gathering.
Install Ghost Eye on Linux I advise everyone to read this carefully, it is often forgotten during installation that Ghost Eye is using python3. So before to move further, please check if Python 3 is already present in your machine. If you need to install it, just follow the below commands.
Linux is an extremely popular operating system for hackers. First of all, Linux’s source code is freely available because it is an open-source Operating System (OS). This means that Linux is very easy to modify and customize. Second, there are countless Linux security distros available.
It is extremely important to develop your Linux skills to become an “Ethical Hacker”. Nearly all the tools that hackers use are developed for Linux.
If you want to immerse yourself more about how to hack with Android, then Termux is a very good “App” to use an discover. I have been using it for a long time and I still love to see what you can do with it! And that with or without root privileges.
Because the possibilities with Termux are almost unlimited, I would not be able to cover everything in this article, but I will try my level best to provide you a good start.
In this article, I will try to cover the most useful Linux commands that every hacker, pentester, and expert in cybersecurity must know !!
HACKERS LOVE THE TERMINAL You are a hacker Your home is the terminal. You work on several projects at once, You know every keystroke is valuable. With just some commands, you can automate tasks, install your favorite software, view a whole network, find vulnerabilities on just about anything connected to the internet, compile a script, create additional user accounts, properly configure anonymity software, and optimize our interactions with terminals.
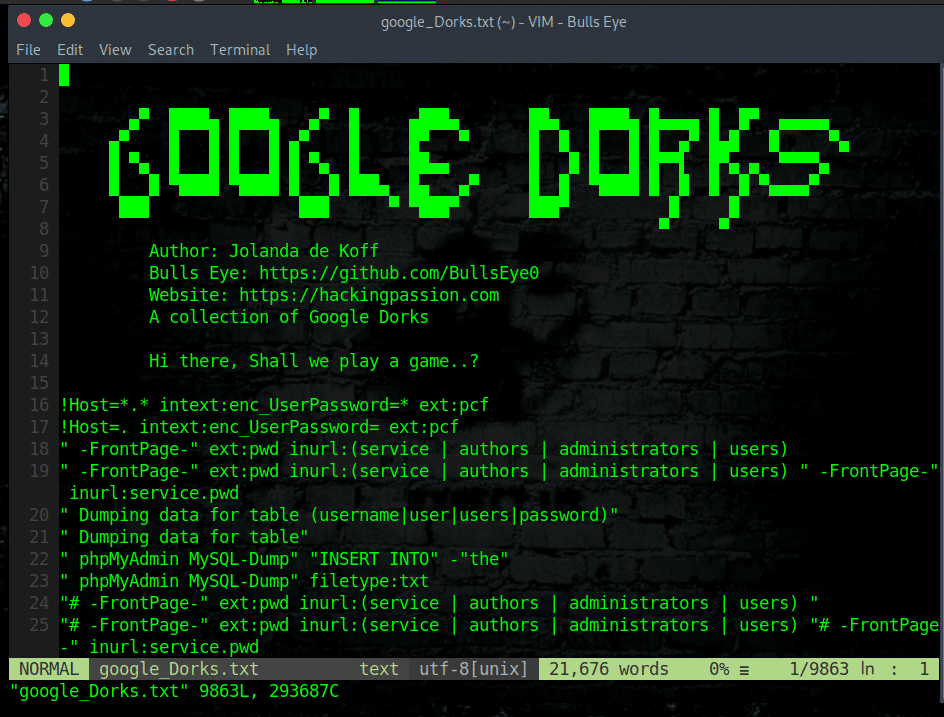
Google Dorks Google Dorks A frequently asked question to me, “Where should I start learning how to hack ?". And every time, the first thing I want to answer is: “Why don’t you start by using Google ?". Personally, Google is one of my best friends in Hacking, and I’m sure Google will be yours too after reading this article.
All you need to carry out to move further with “Google Dork”, is a computer, an internet connection, and knowledge of the appropriate search syntax.
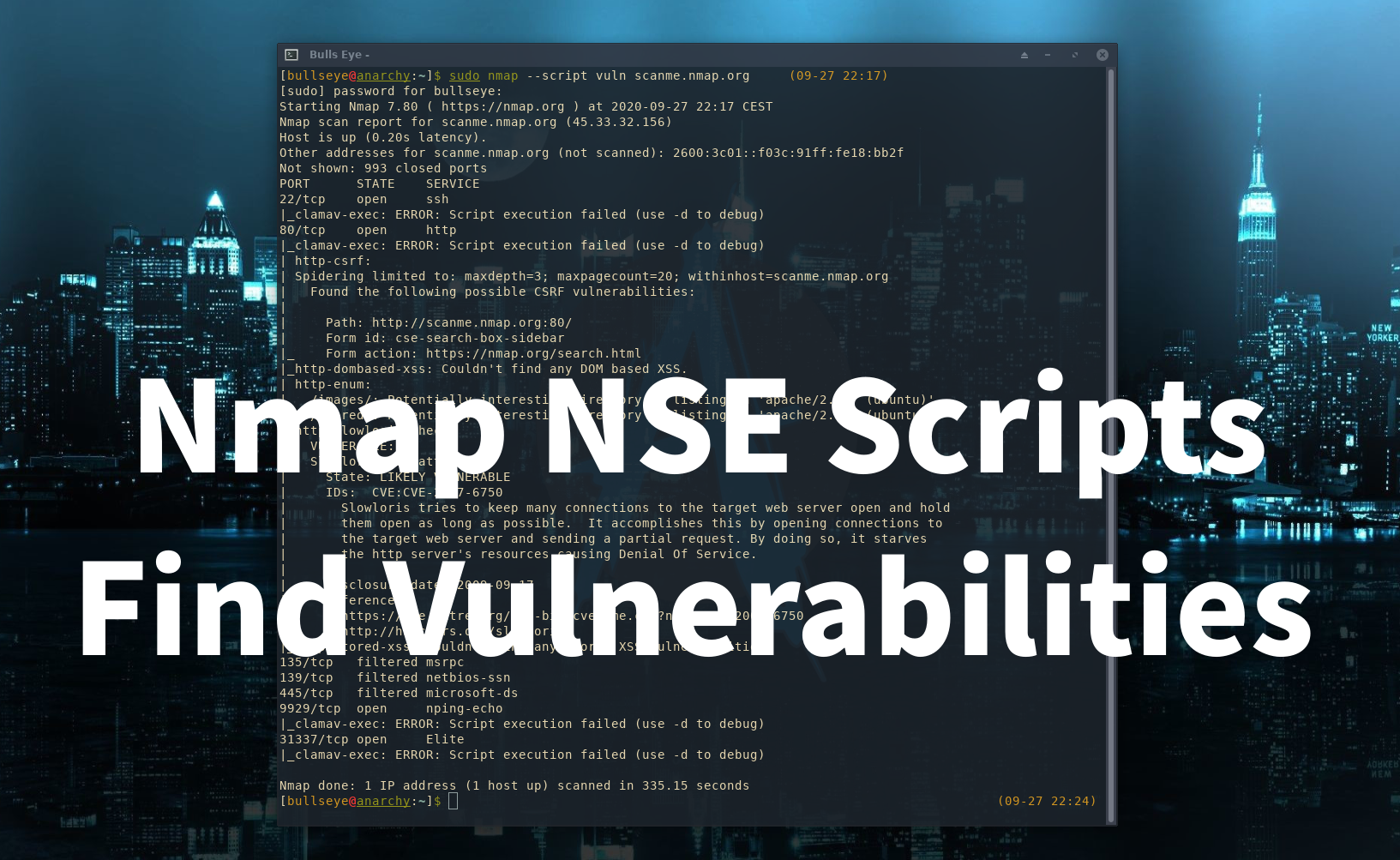
Find Vulnerabilities, Nmap has a lot of features and one of them is a built-in script interpreter called NSE Nmap Scripting Engine.
Nmap is one of the most used and best port scanning tools that exist and is the favorite for many people including for me. But Nmap is not only a port scanner, but this tool is also much more and has so many features. In this article, we highlight the Nmap Script Engine (NSE).
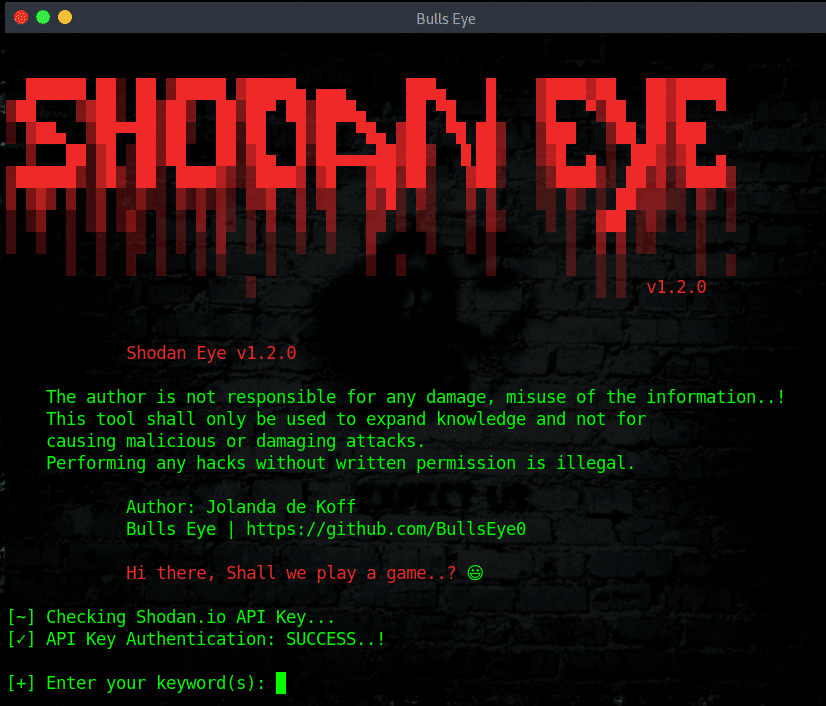
Shodan Eye collects and returns all information about every device that is directly connected to the internet and according to the keywords you entered.
What type of devices can be found with Shodan Eye The types of devices that are indexed can vary enormously. It can be from small desktops to refrigerators or either nuclear power plants, webcams, water treatment facilities, coffee machines, yachts, medical devices, traffic lights, wind turbines, license plate readers, smart TVs and much more.
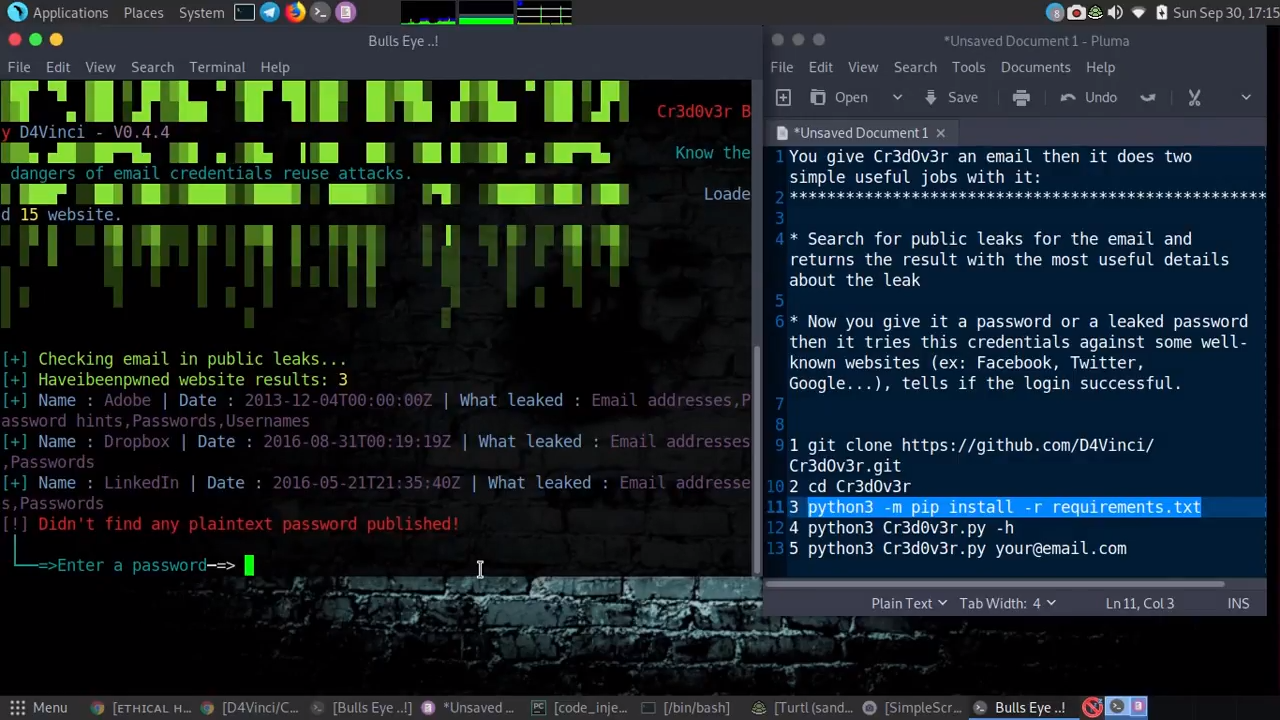
Cr3dOv3r This tool checks your credentials on different websites and looks for if your email is in some data leak.
Your best friend in credential reuse attacks. You give Cr3dOv3r an email then it does two simple useful jobs with it:
Search for reuse attack public leaks for the email and returns the result with the most useful details about the leak Now you give it a password or a leaked password then it tries these credentials against some well-known websites (ex: Facebook, Twitter, Google…), tells if the login was successful and if there’s captcha somewhere blocking our way!
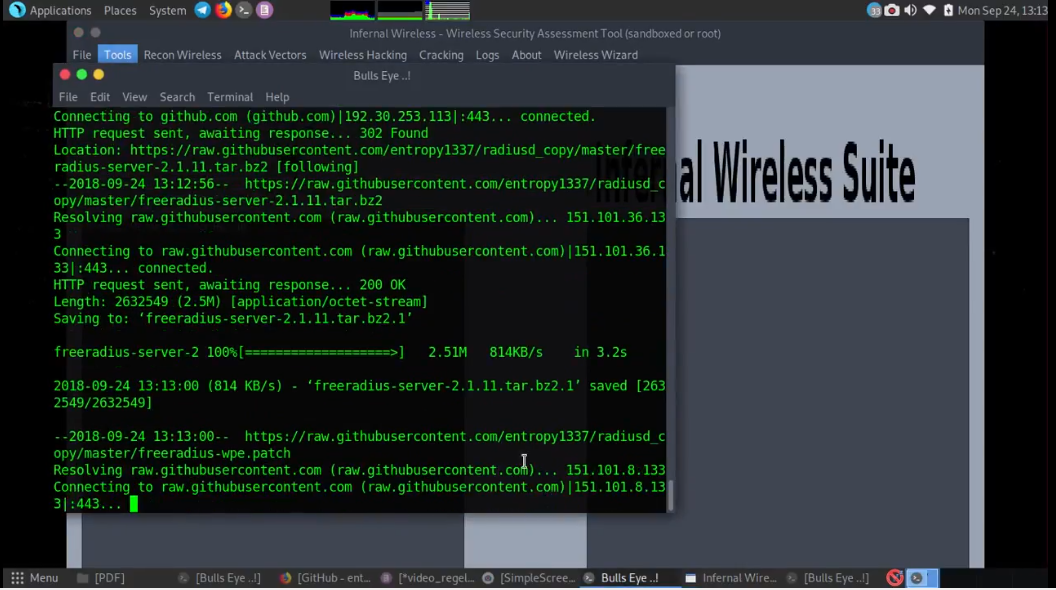
Infernal Twin is an automated wireless hacking suite written in Python which automates many of the repetitive tasks involved in security testing for wifi networks.
Infernal-Twin GitHub: https://github.com/entropy1337/infernal-twin
Features added and improved: Added BeeF XSS framework Integration Added HTTP Traffic View within tool Improved Infenral Wireless Attack Visual View of some of the panel improved Improved Basic Authentication during Social engineering assessment over wireless network Infernal-Wireless v2.6 This tool is created to aid the penetration testers in assessing wireless security.
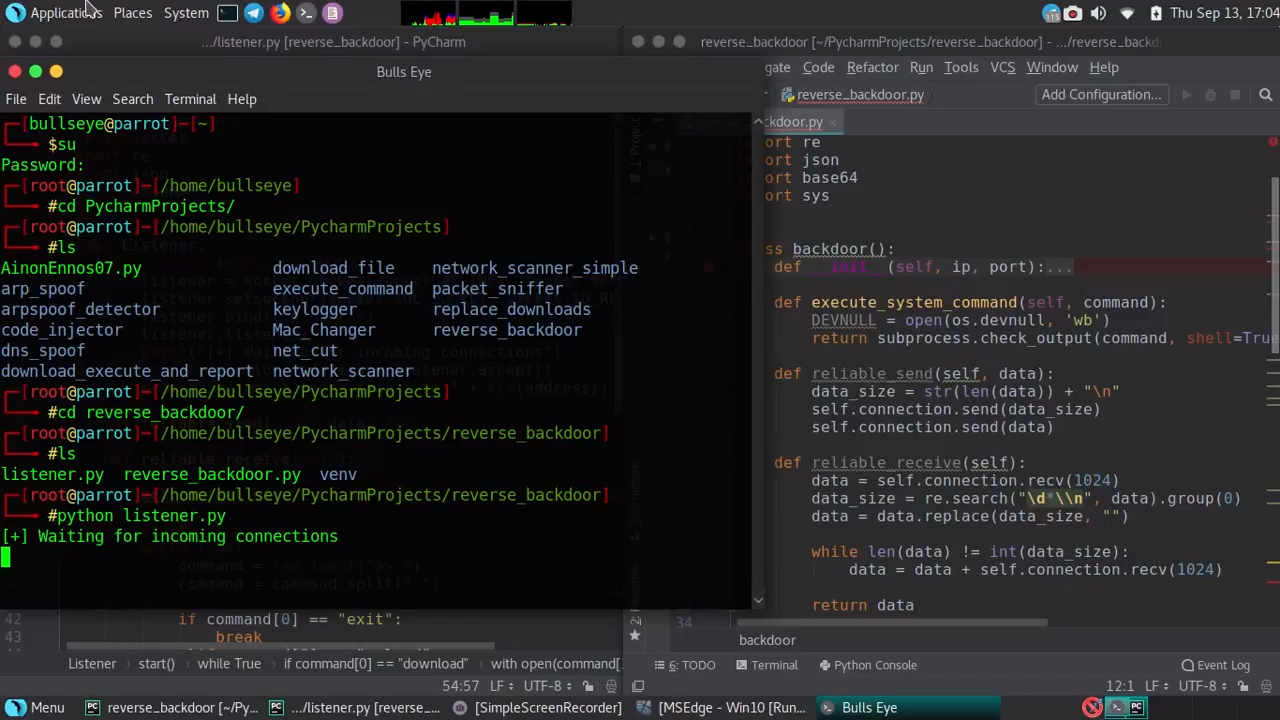
A reverse backdoor made in python, I put this on my VirtualBox on Windows. This backdoor can be used on - Linux, Mac, and Windows. I also made a Listener. All types of files. On both of these, I made a download and upload function. So you can download everything from the target computer but also upload and vice versa.
This tool is not public. This was my second video. The date was Sept 13, 2018, when I publish this video on YouTube.