Clear Your Tracks on Linux
Clear Your Tracks on Linux
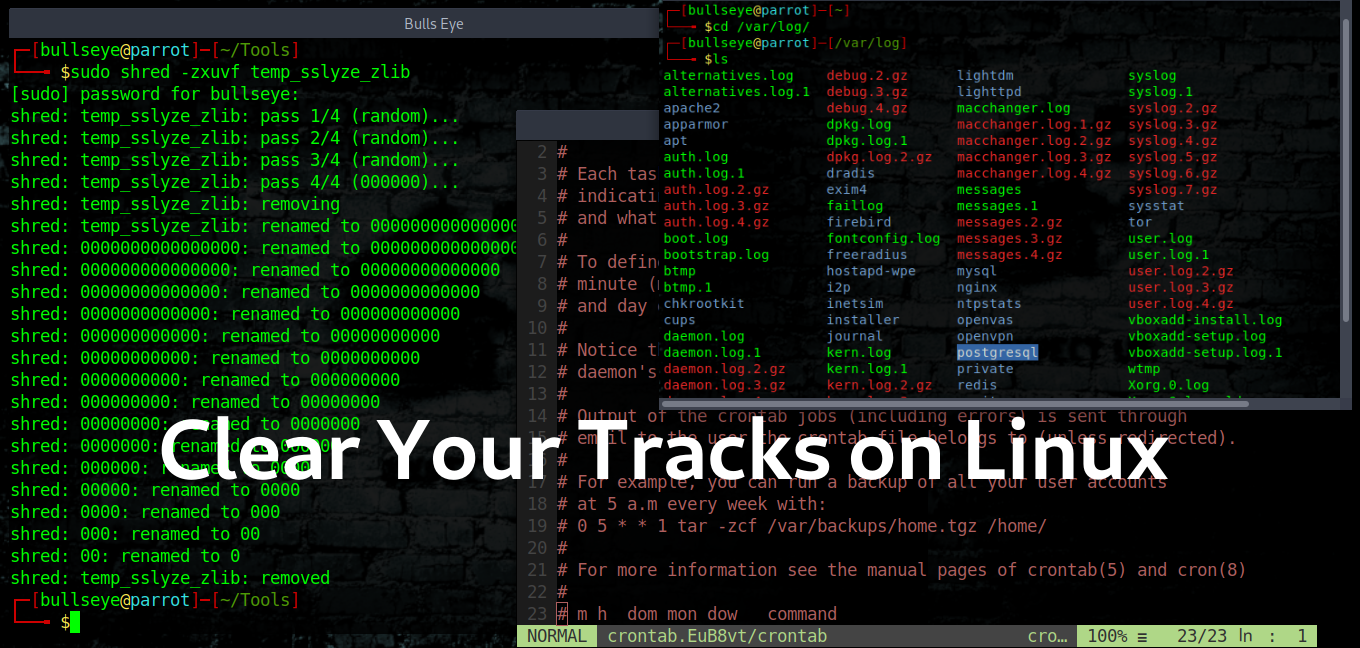
In this article and video, I show you how to clear your tracks in Linux. This is very important if you are a penetration tester, an ethical hacker, or a cyber security expert.
Clear Your Tracks The Final Step
It is one of the biggest mistakes an attacker makes to let a track behind.
If you see the biggest attacks in the past years, most of the detection was made really easy from the malware that the black hat hacker(s) have left, which they didn’t clear. Many of the “best hackers” got caught this way.