Red Hawk Information Gathering Vulnerability Scanner and Crawling

RED HAWK is A all in one tool for Information Gathering, Vulnerability Scanning, and Crawling. A must-have tool for all penetration testers. A Step-by-Step walkthrough.
Scans That You Can Perform Using RED HAWK
- Basic Scan
- Site Title NEW
- IP Address
- Web Server Detection
IMPROVED - CMS Detection
- Cloudflare Detection
- robots.txt Scanner
- Whois Lookup
IMPROVED - Geo-IP Lookup
- Grab Banners
IMPROVED - DNS Lookup
- Subnet Calculator
- Nmap Port Scan
- Sub-Domain Scanner
IMPROVED- Sub Domain
- IP Address
- Reverse IP Lookup & CMS Detection
IMPROVED- Hostname
- IP Address
- CMS
- Error Based SQLi Scanner
- Bloggers View NEW
- HTTP Response Code
- Site Title
- Alexa Ranking
- Domain Authority
- Page Authority
- Social Links Extractor
- Link Grabber
- WordPress Scan NEW
- Sensitive Files Crawling
- Version Detection
- Version Vulnerability Scanner
- Crawler
- MX Lookup NEW
- Scan For Everything - The Old Lame Scanner
Installation:
| |
| |
Run RED HAWK
| |
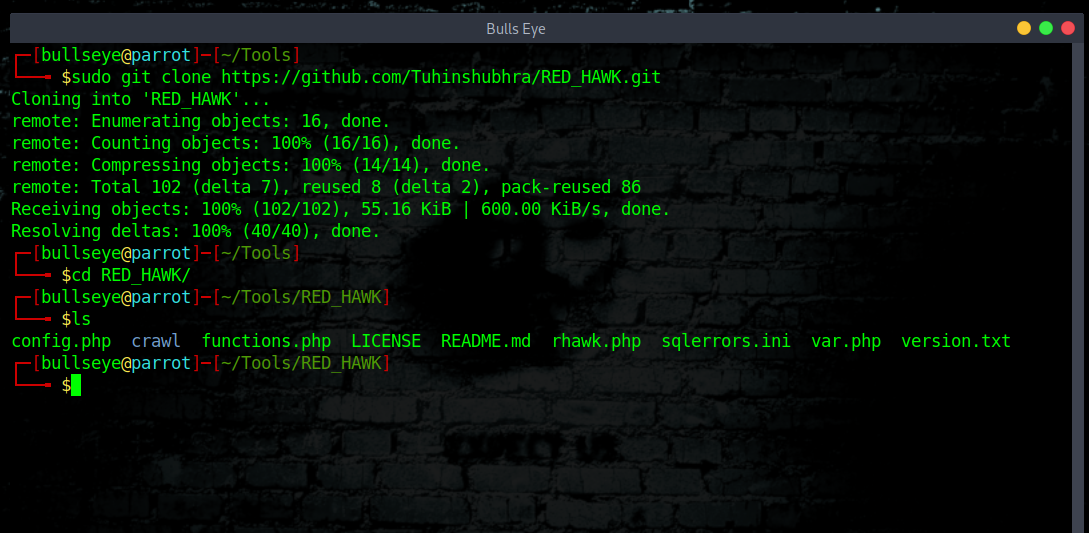
GitHub link: https://github.com/Tuhinshubhra/RED_HAWK
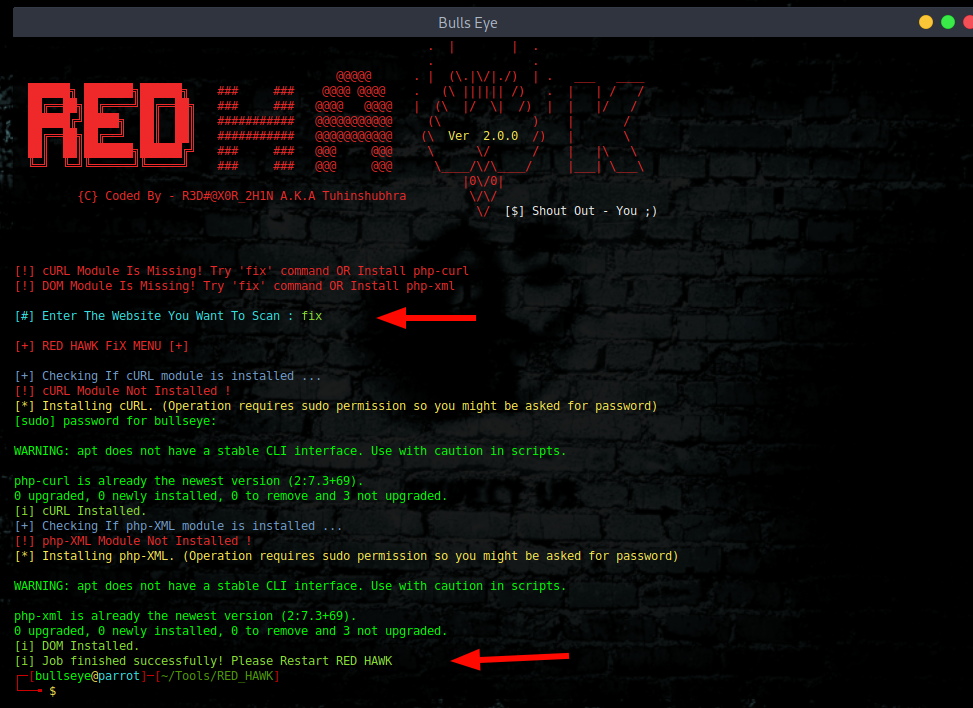
Run The Tool and Type **fix** This will Install All Required Modules.
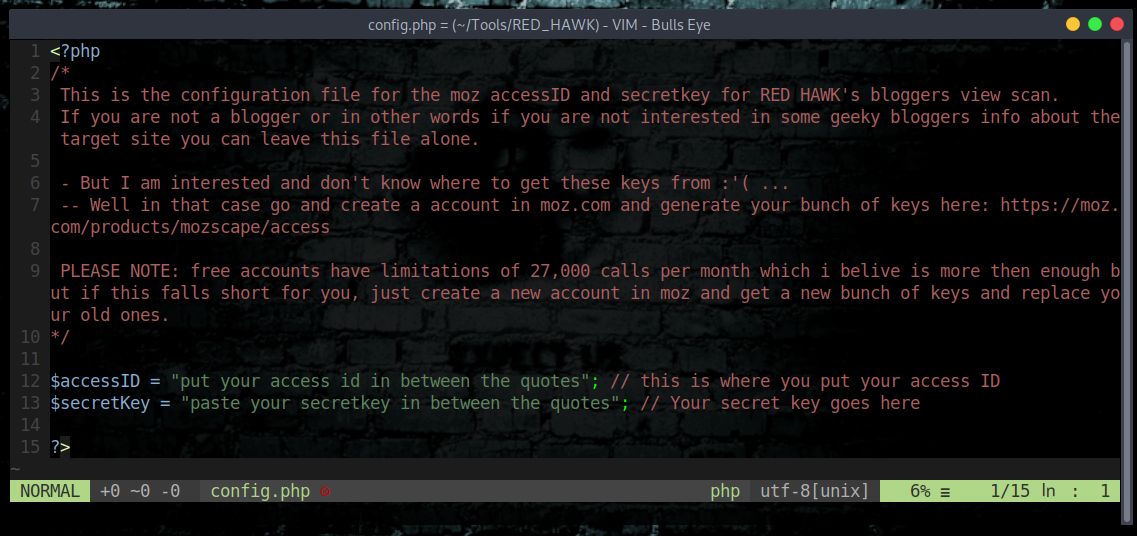
How To Configure RED HAWK with moz.com for Bloggers View Scan
- For The Bloggers View To Work Properly you have to configure RED HAWK with moz.com’s API keys for that follow the following steps:
- Create an account in moz follow this link: https://moz.com/community/join
- After successful account creation and completing the verification you need to generate the API Keys
- You can get your API Keys here: https://moz.com/products/mozscape/access
- Get your AccessID and SecretKey and replace the
$accessIDand$secretKeyvariable’s value in theconfig.phpfile - All set, now you can enjoy the blogger’s view.
Usage:
https://github.com/Tuhinshubhra/RED_HAWK#usage
Use the “help” command to see the command list or type in the domain name you want to scan (without Http:// OR Https://).
Select whether The Site Runs On HTTPS or not.
Select the type of scan you want to perform
Leave the rest to the scanner
List of CMS Supported
https://github.com/Tuhinshubhra/RED_HAWK#list-of-cms-supported
RED HAWK’s CMS Detector currently is able to detect the following CMSs (Content Management Systems) in case the website is using some other CMS, Detector will return could not detect.
- WordPress
- Joomla
- Drupal
- Magento
Video RED HAWK
RED HAWK Best Information Gathering, Vulnerability Scanner and Crawling Tool
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.