RondoDox Botnet: 56 Exploits, Gaming Traffic Disguise, and Self-Defense Against Recovery
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
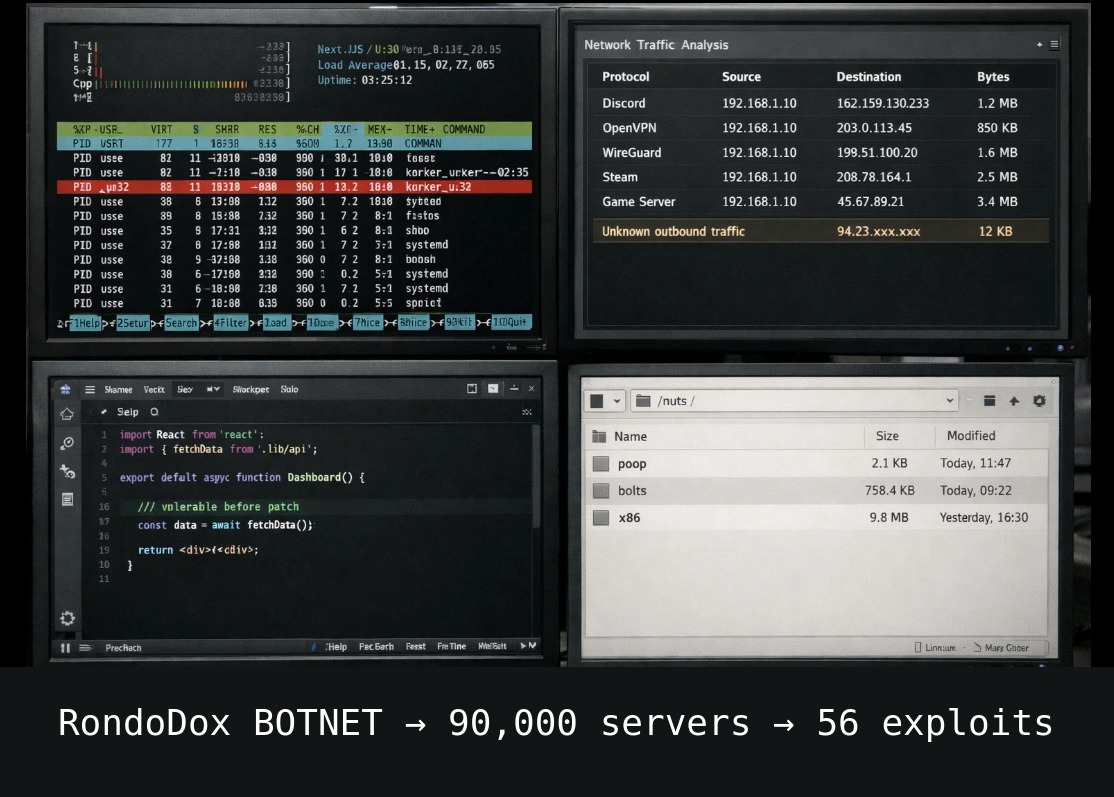
RondoDox added React2Shell to its arsenal. 90,000+ servers. 56 vulnerabilities. 30+ vendors. They call it the “exploit-shotgun” approach. Fire everything, see what hits. 😱
Once inside, RondoDox doesn’t just sit there. It launches DDoS attacks. Mines Monero. Turns infected devices into proxies to hide other attacks. And it breaks the tools needed to fight back.
The botnet has been running for 9 months. Three distinct phases. March to April 2025 was reconnaissance. April to June was daily probing of WordPress, Drupal, Struts2, and IoT devices. July onward became hourly automated attacks at scale.
December 8, 2025: RondoDox started scanning for vulnerable Next.js servers. Three days later, payloads were dropping.
The payload names: /nuts/poop → cryptominer /nuts/bolts → botnet loader and health checker /nuts/x86 → Mirai variant
Someone has a sense of humor.
What makes RondoDox different from typical botnets:
→ It ignores your commands. The shell script traps SIGINT, SIGTERM, SIGQUIT, SIGHUP, and five other signals. Ctrl+C does nothing. Kill commands get ignored. The malware decides when it stops, not you.
→ It sabotages recovery tools. After infection, it renames critical Linux binaries to random character strings. iptables becomes unrecognizable. ufw, passwd, shutdown, reboot. All renamed to gibberish. Configuring the firewall becomes impossible. Shutting down the machine becomes impossible. Changing passwords becomes impossible.
→ It kills everything useful. Every 45 seconds, RondoDox scans running processes and terminates anything it doesn’t control. Cryptominers, other botnets, analysis tools like Wireshark, gdb, tcpdump, strace. But also wget and curl. You can’t even download patches anymore.
→ It survives everything. The malware writes itself into /etc/init.d, /etc/rcS, /etc/inittab, crontab entries for both user and root. Remove one persistence method, five others bring it back after reboot.
→ It hides as gaming traffic. RondoDox disguises its DDoS floods and C2 communication as packets from Valve, Minecraft, Fortnite, Dark and Darker, Roblox, DayZ, GTA, Discord, OpenVPN, and WireGuard. Network monitoring tools see what looks like normal gaming or VPN activity. The malicious traffic blends right in.
Researchers found something odd in the code. The malware writes an email address to /tmp/contact.txt: vanillabotnet@protonmail.com. No function references it. No code uses it. It just sits there.
Nobody knows why.
RondoDox is also a business. The operators run a loader-as-a-service model, distributing RondoDox alongside Mirai and Morte payloads. You’re not just getting one botnet. You’re getting a package deal.
What RondoDox targets:
Routers → Linksys, Wavlink, Four-Faith F3x24/F3x36 DVRs → TBK DVR-4104 and DVR-4216 → CCTV systems → Next.js applications using React Server Components
Many of these devices sit in retail stores, warehouses, and small offices. Unmonitored for years. Exposed directly to the internet. Firmware never updated.
For the technical crowd:
→ XOR obfuscation key → 0x21 → SSH banner → SSH-2.0-MoTTY_Release_0.82
Signs of infection:
→ Renamed binaries. If iptables, ufw, passwd, shutdown, or reboot have become random character strings, that’s RondoDox.
→ Unexpected crontab entries. Modifications to /etc/inittab, /etc/rcS, or new @reboot entries that weren’t there before.
→ Outbound connections to the C2 IPs listed above.
Not infected yet? Keep it that way:
For Next.js developers:
→ React versions 19.0 through 19.2.2 are vulnerable. Update to 19.0.3, 19.1.4, or 19.2.3. → Next.js → update to the latest patched version (check vercel[.]com/changelog for your release line)
For IoT devices:
→ Update firmware. Disable remote management from WAN. Replace default credentials. Isolate on separate VLANs.
9 months of operation. 56 exploits. Traffic that looks like Fortnite. Tools that can’t be used against it. A business model built on top.
RondoDox is what modern botnets look like.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.