SAP Just Got Breached: Four Critical Vulnerabilities Let Attackers Steal Financial Data (CVE-2026-0501)
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
SAP just patched four critical vulnerabilities
SAP just patched four critical vulnerabilities. CVSS scores up to 9.9. One lets attackers run code with nothing but a malicious link. 425,000 companies run SAP. Over 85% of Fortune 500. The patches dropped today, January 13, 2026. 🧐
SAP Patch Tuesday just landed with seventeen security notes. Four are HotNews - SAP’s term for patch immediately or accept the consequences.
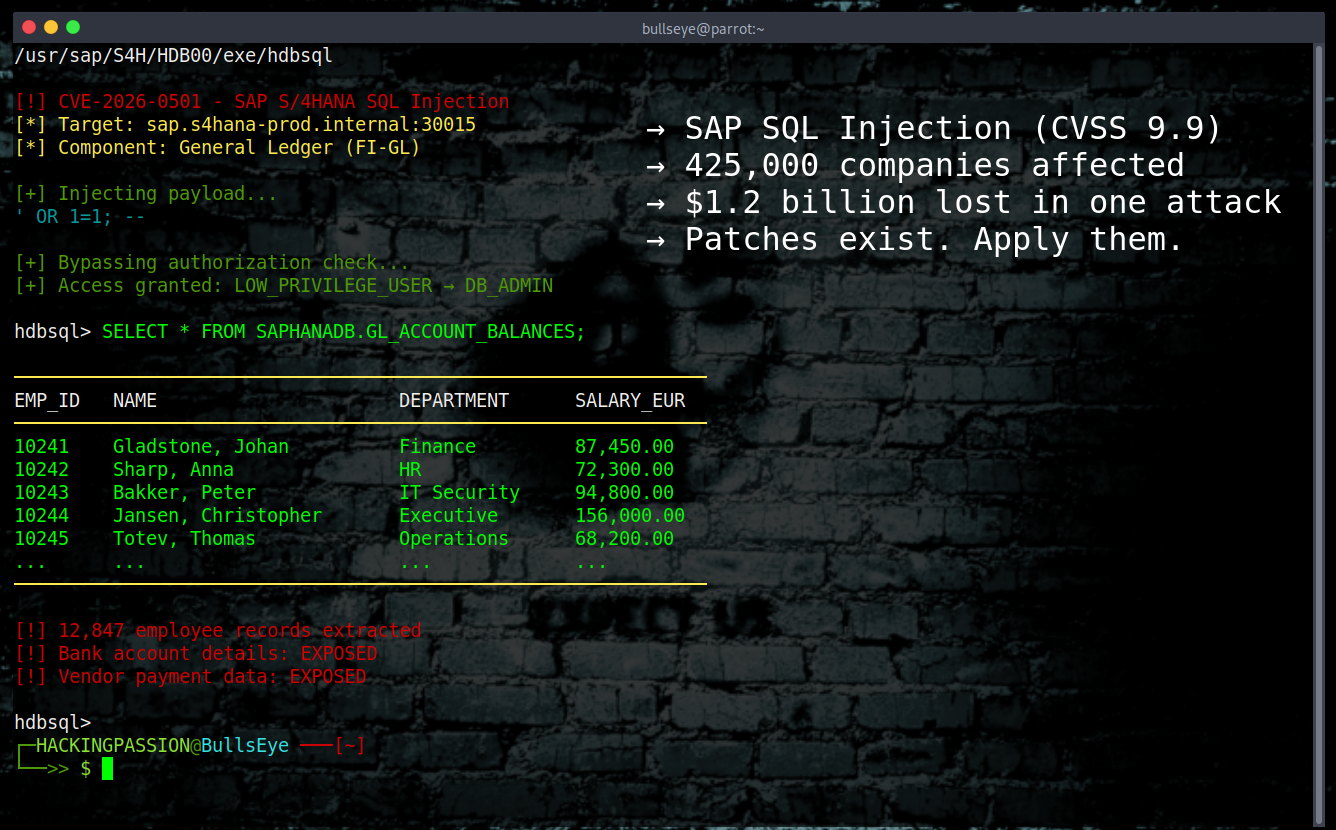
The most severe vulnerability lets someone with a basic user account run arbitrary SQL queries against the entire financial database.
The vulnerabilities
- → CVE-2026-0501 (CVSS 9.9): SQL injection in SAP S/4HANA Financials General Ledger
- → CVE-2026-0500 (CVSS 9.6): One-click RCE in SAP Wily Introscope Enterprise Manager
- → CVE-2026-0491 (CVSS 9.1): Code injection in SAP Landscape Transformation
- → CVE-2026-0498 (CVSS 9.1): Code injection in SAP S/4HANA
- → CVE-2026-0492 (CVSS 8.8): Privilege escalation in SAP HANA database
Here’s how the SQL injection works.
The General Ledger is where companies store everything financial. Employee salaries, vendor payments, bank account details, invoices, transaction records. An attacker who has obtained low-level credentials through phishing or credential stuffing can inject SQL commands directly into the database backend.
They can read all of it, modify entries to redirect payments, or delete records entirely. The vulnerability has cross-scope impact, meaning the damage propagates to other connected SAP systems.
Here’s how the one-click RCE works.
SAP Wily Introscope Enterprise Manager is a monitoring tool that many organizations leave exposed. The flaw comes from a vulnerable third-party component that handles JNLP files, which are Java Network Launch Protocol files used to launch applications.
An attacker creates a malicious JNLP file, hosts it on any public URL, and sends the link to someone inside the organization. When that person clicks, the file executes and gives the attacker the ability to run operating system commands on their machine. No credentials required.
Why SAP vulnerabilities hit different.
SAP processes 77% of global transaction revenue. Apple runs SAP. Amazon runs SAP. Walmart, Coca-Cola, Ford, Shell, Volkswagen, Nestlé, Microsoft, IBM. When SAP gets compromised, entire business operations stop.
In September 2025, a large UK manufacturer was compromised through an SAP vulnerability. Production facilities shut down. Workers sent home. Six weeks of paralyzed operations. Reported losses: $1.2 billion.
Stoli Group, the vodka company, filed for bankruptcy in November 2024. Court filings explicitly cite an SAP security breach as a major contributing factor. The ransomware encrypted critical data and disrupted operations so severely that recovery was estimated at five to seven months. They never made it.
The threat actors hunting SAP.
2025 was a record year. SAP vulnerabilities increased 39% compared to 2024. Active exploitation went up 210%. The price for a working SAP exploit on the underground has increased 5x over the past five years. Attackers know what SAP systems are worth.
Multiple APT groups spent most of 2025 actively exploiting SAP systems. They deployed webshells within hours of vulnerability disclosures.
In August 2025, a working SAP exploit was publicly released online. No special skills required anymore. Anyone can download it and use it against unpatched systems.
When SAP disclosed CVE-2025-31324 in April, attackers were exploiting it within hours. The window between disclosure and weaponization has collapsed.
Who needs to worry about this.
Any organization running SAP S/4HANA, SAP HANA database, SAP Wily Introscope, or SAP Landscape Transformation. That includes private cloud deployments and on-premise installations.
If your company uses SAP for financials, HR, supply chain, or any core business process, these vulnerabilities affect you.
Signs your SAP system may be compromised.
- → Unexpected new user accounts, especially with high privileges
- → SAP_ALL authorization assigned to accounts that shouldn’t have it
- → Unusual RFC calls in the logs
- → Failed login attempts followed by successful ones
- → Changes to financial records without matching business transactions
- → Unknown programs or reports appearing in the system
- → Webshells in the file system (look for .jsp files in unexpected locations)
If you see any of these, assume compromise and engage your incident response team.
Hacking is not a hobby but a way of life. 🎯
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.