Security Webcam Hacking Way Too Easy
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Security webcams are often way too easy to hack. In this article + video I show you how this is done. How simple it is to hack a lot of cameras. After many years, it still seems there a few people who are told what is security. Or is it that most people just don’t know what the consequences might be and just ignore the warnings?
One of the big ironies of life can be that the devices we create to protect us, can sometimes be used against us.
One of the reasons for writing this article is to show how easy it can be to hack a surveillance camera in a very simple way.
Before continue, I am writing this post so that:
✓ Factories of these security cams will also focus on security
✓ That software makers will focus more on security. (This must be there nr 1 focus.)
✓ People should be well informed about the security of these (any) devices.
How is it possible that this has been going on for years. How difficult is it to inform people.
IMPORTANT THINGS TO REMEMBER
This article was written for educational purposes and pentest only.
The author can not be held responsible for damages caused by the use of these resources.
You will not misuse the information to gain unauthorized access.
This information shall only be used to expand knowledge and not for causing malicious or damaging attacks.
Just remember, Performing any hacks without written permission is illegal ..!

Somebody’s Watching: Hackers Breach Ring Home Security Cameras
A family in Mississippi said a man hacked into a Ring home security camera in a bedroom shared by their daughters. Credit…Ashley LeMay
To monitor what’s happening in your area, the security cameras have to be connected to the internet. And the moment you connect any device to the internet “hypothetically” someone can get access to it. See the article about Shodan Eye a tool that I make, you will read that you can search for any device that is connected to the internet. (Later more about this).
What’s even scarier is once a camera is compromised, a “hacker” can make “lateral movements” into other connected devices..!
So a hacker could, in theory, disable your alarm system, hack your computer, torment your household by blasting music, turn on your tv and much more. As long as it is connected to the same network..!
“People don’t care about Security and Privacy,
I’m convinced that people care… And if they don’t,
It’s our duty to show them why they should..!”
How to secure your security webcam
Create a complex password
Don’t use the default user name and password that comes with your device that you buy. Change your passwords to something long and difficult to break. Don’t use last names, addresses, pet names or birthdays. I recommend a combination of upper and lower case letters, numbers and symbols.
Change your passwords frequently..!
Regularly update your security camera’s firmware
Keep your software up to date. This helps patch vulnerabilities in your software that could allow hackers access to your device. Surveillance camera vendors often expect users to update the devices manually. So every few months, you should check to see if yours has an available update. Set up manual security updates, if that’s an option.
Keep your firewall activated
Installing a firewall between your Internet connection and all of your devices is one more way to protect yourself. A firewall is a network security system. It provides a wall of defense by monitoring traffic to and from your network. In short, it helps keep the bad guys out. Keep in mind, most firewalls need to be turned on.
Place security webcams on their own network
It’s also recommended that you consider placing your security cameras on a network of their own. Isolating your cameras to a single network means that if the cameras are somehow compromised, the hacker won’t be able to gain access to any of your other devices. I recommend using a cloud server for your security camera.
Buy a security cam from a reputable vendor
Choose a company that treats security with more responsibility. Get informed or explore what the best security camera is for you.
Avoid all suspicious links
Never click on suspicious links in emails or download files from people you don’t know, tricking you into installing malware. This is one of the most common ways that hackers gain access to your machine.
Botnets
Botnets have been one of the most common methods of malware implementation and have infected hundreds of millions of computers. Because botnets infect new technologies such as “Internet of Things” (IoT) devices in homes, public spaces, and secure areas.
They perform major operations while remaining small
Most people would be shocked to hear that the spam they receive comes from thousands or even millions of computers, just like theirs. The real owners of those computers can still use them and are probably unaware that something is wrong, except that their computer sometimes seems slow. Most botnets have an extremely small footprint. They usually also have the ability to mask themselves so that they can carry out large-scale attacks without being noticed.
They connect open-source and unsecured devices
Mirai, a botnet discovered in 2016, mainly attacked IoT devices, including security webcams and internet routers. In essence, devices infected with Mirai malware became bots that would scan the internet to find IoT devices. Mirai would then use common standard usernames and passwords set by device manufacturers to attempt to infiltrate and infect those devices. Usually, infected devices would function normally
Source

Different ways to hack Security Webcams
“In the years I’ve spent as a professional hacker, I’ve learned that the simplest approach is usually the best. As hackers, we tend to get down into the weeds, focusing on technology, not realizing there may be non-technical methods at our disposal that work as well or better than their high-tech counterparts. I always kept an eye out for the simplest solution to advanced challenges"
- Johnny Long 2011.
Hacking Security Cameras Using Google Dorks
What data can we find using google dorks?
- Username and passwords
- Admin login pages
- Sensitive documents
- Govt/military data
- Email lists
- Bank account details
- Vulnerable websites
- So much more …
A Google Dork is a search that uses one or more of these advanced techniques to reveal something interesting. Something important to keep in mind, the web can be crawled by anyone. Google automatically indexes a website, and unless sensitive information is explicitly blocked from indexing (nofollow, robots.txt), all of the content can be searched via Dorks or advanced search operators.
A few security webcam searches using Dorks
| |
| |
| |
| |
| |
| |
| |
| |
| |
| |
Google Dorks Lists
I have made a huge Google Dorks List on GitHub. A collection of around 10.000 Dorks..! Here is an article about How Using Google Dorks. Very interesting to read.

inurl:LvAppl
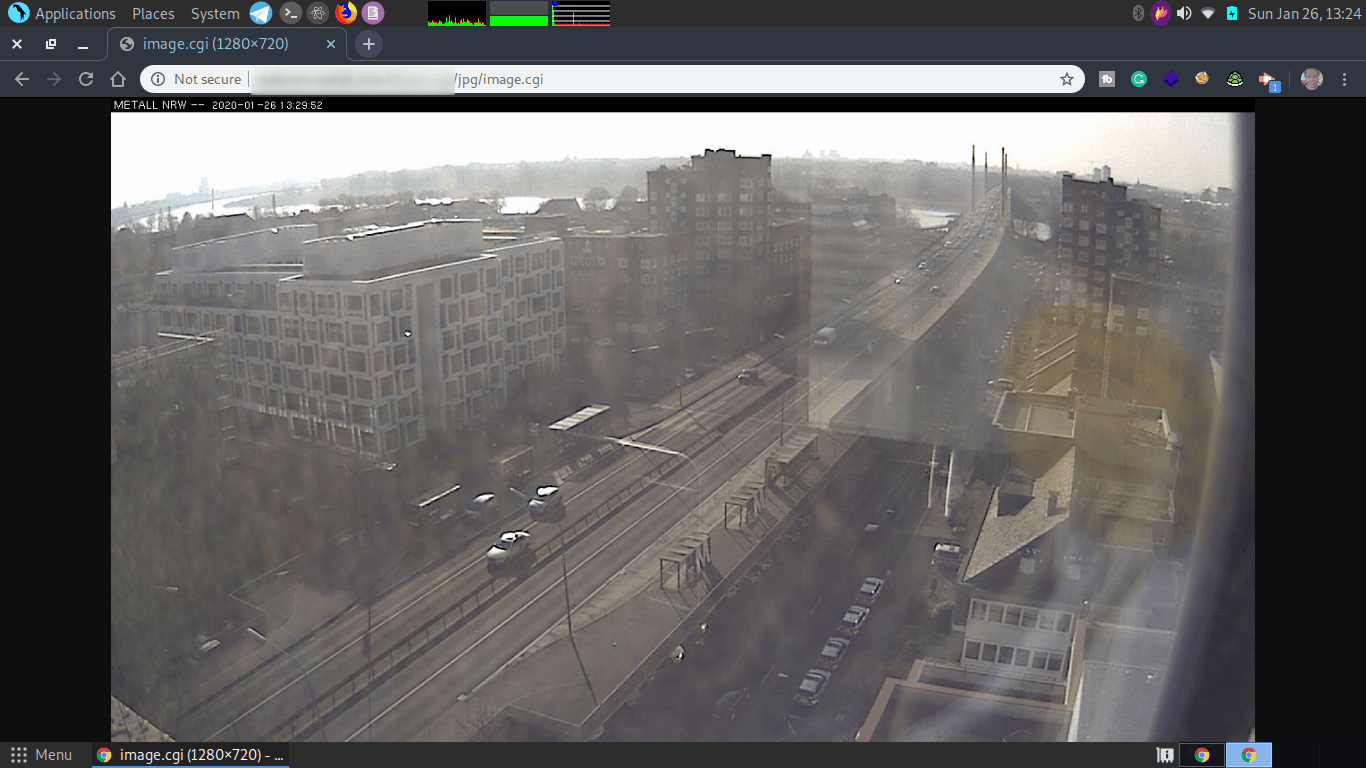
Dork: inurl:axis-cgi/jpg
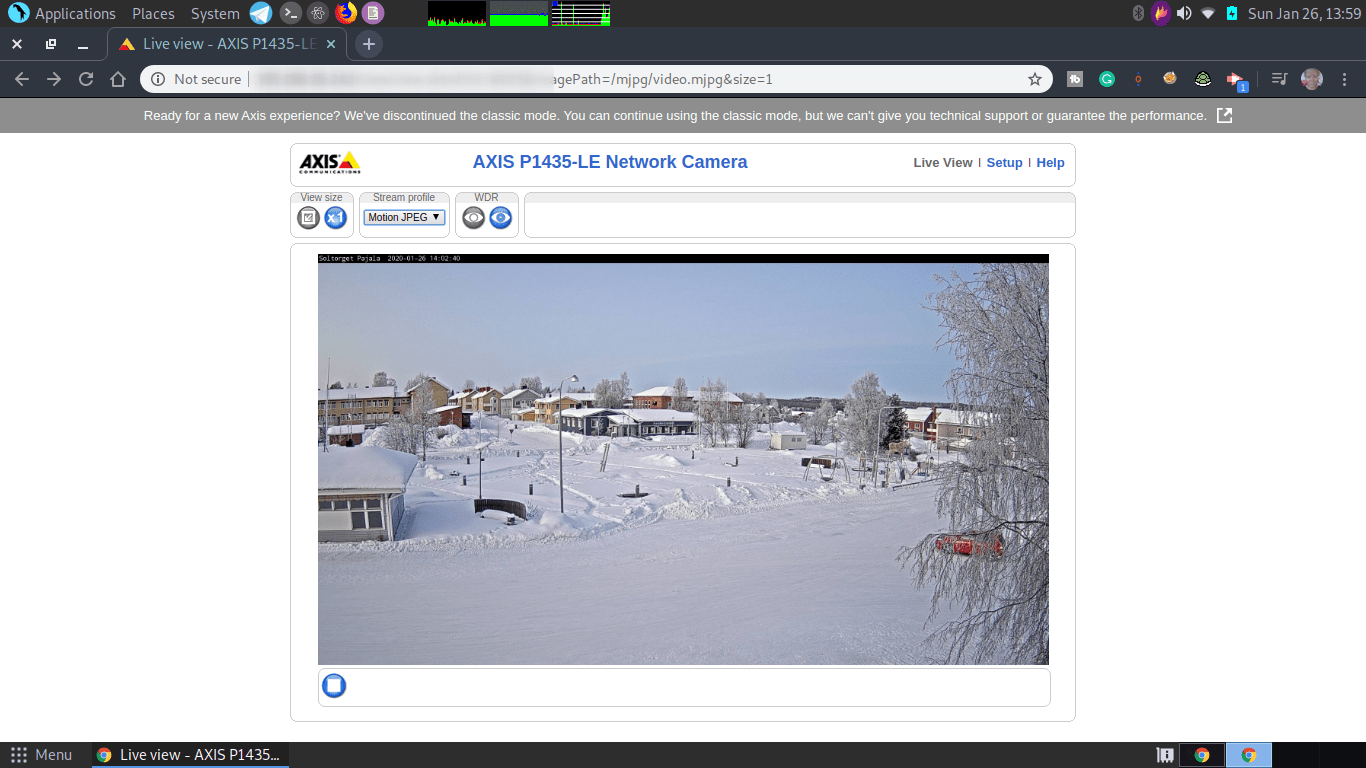
Dork: inurl:view/view.shtml
Hacking Security Cameras Using Shodan
Shodan is a search engine for Internet-connected devices. Google lets you search for websites, Shodan lets you search for every device connected to the internet. You can find out more here on this page.
Find security cams on the Shodan website
Website: https://shodan.io/
Searching for Hikvision:
| |
| |
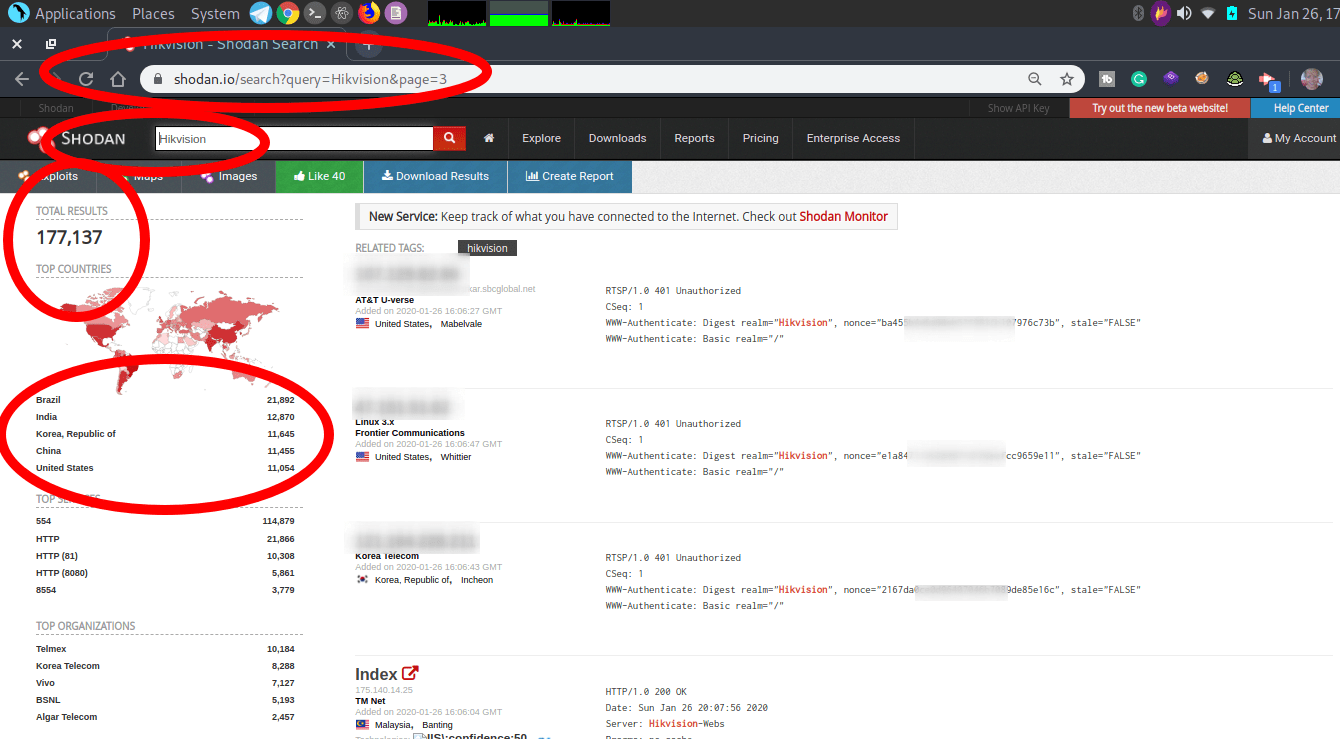
I’m working on a (big) list of Shodan Dorks that I will put online soon. You can find a small one here (In the Shodan Eye script):
https://github.com/BullsEye0/shodan-eye/blob/master/Shodan_Dorks_The_Internet_of_Sh*t.txt
Install Shodan on your terminal
Shodan is already installed.
To install the Shodan library, simply:
| |
Or if you don’t have pip installed (which you should seriously install):
| |
Once the tool is installed you have to initialize the environment with your API key using shodan init
| |
You can get your API key from your Shodan account page located at:
Get you Shodan API key
Get your shodan API key
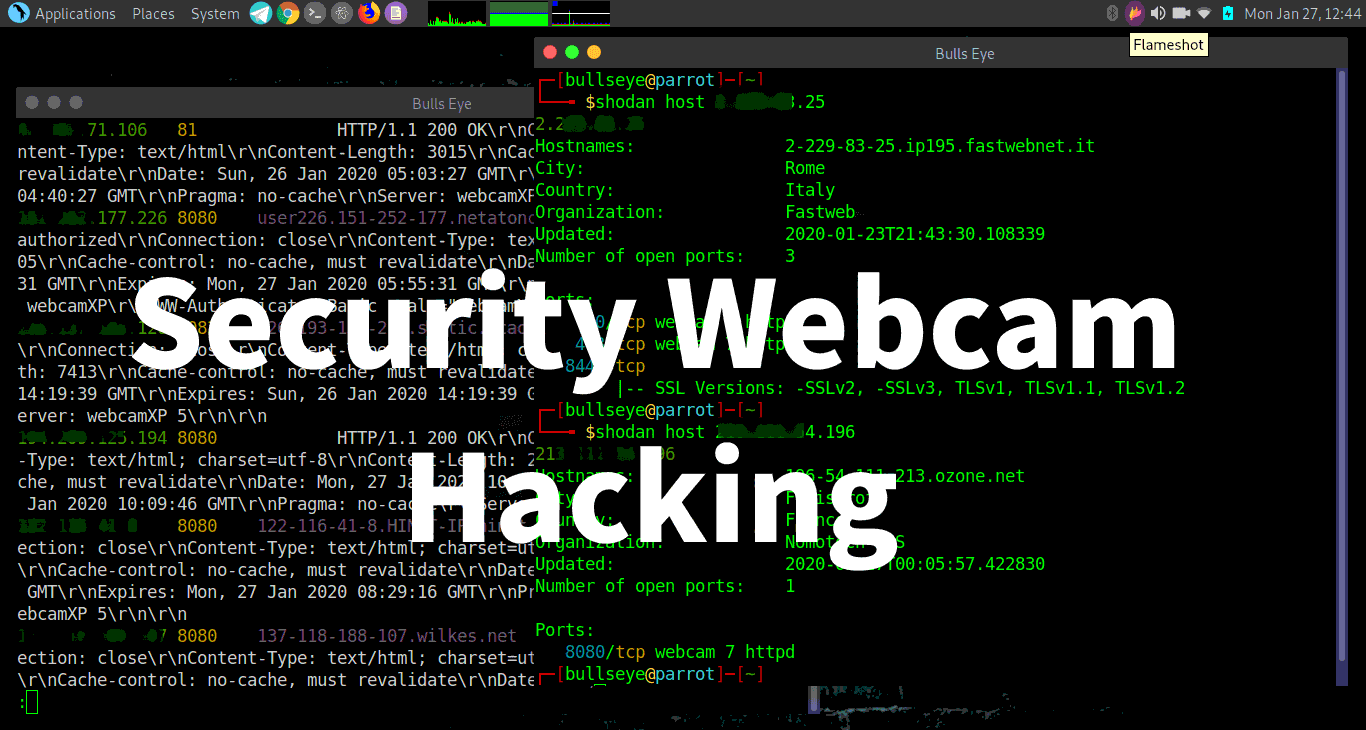
Security webcams hacking
Now that you have installed Shodan on your computer,
let’s have some fun..! :)
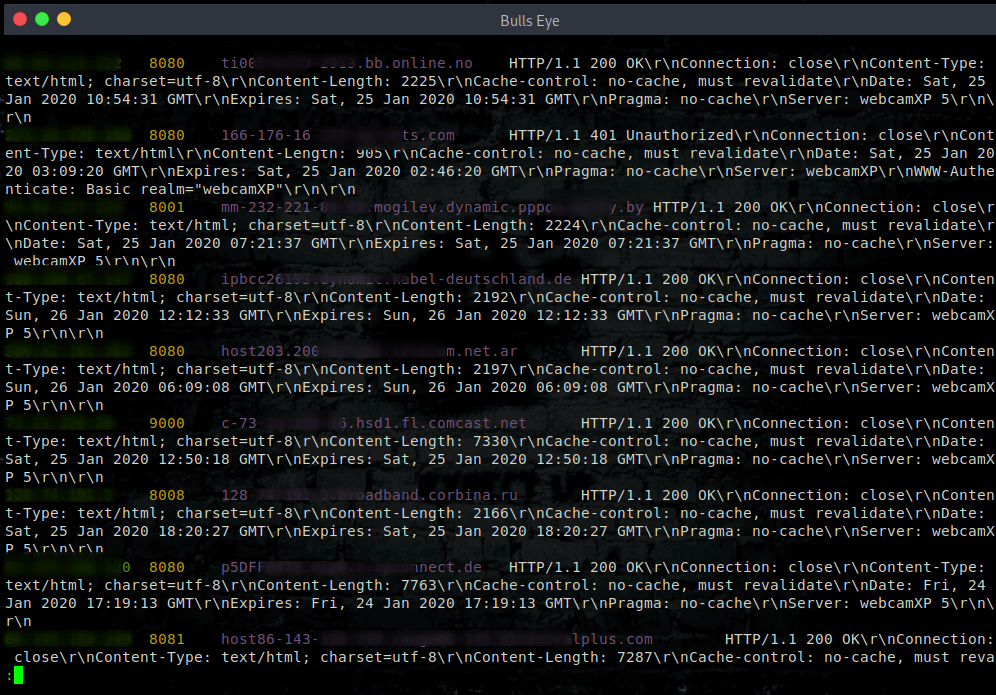
shodan search webcamXP
The search begins. Copy the IP address and port, and put it in your browser. ipaddress:8080
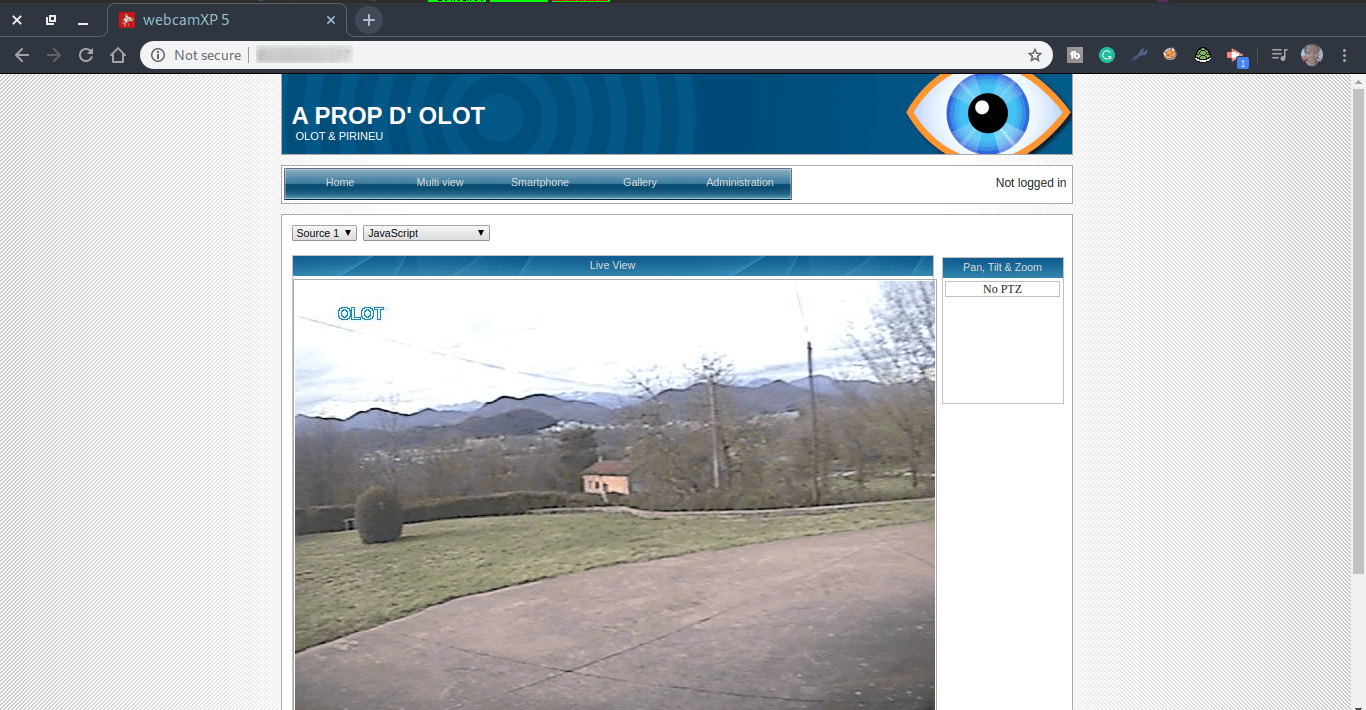
webcamXP
Shodan Host Search
With Shodan, you also can find more information about the IP address. And even find some vulnerabilities if there are any.
| |
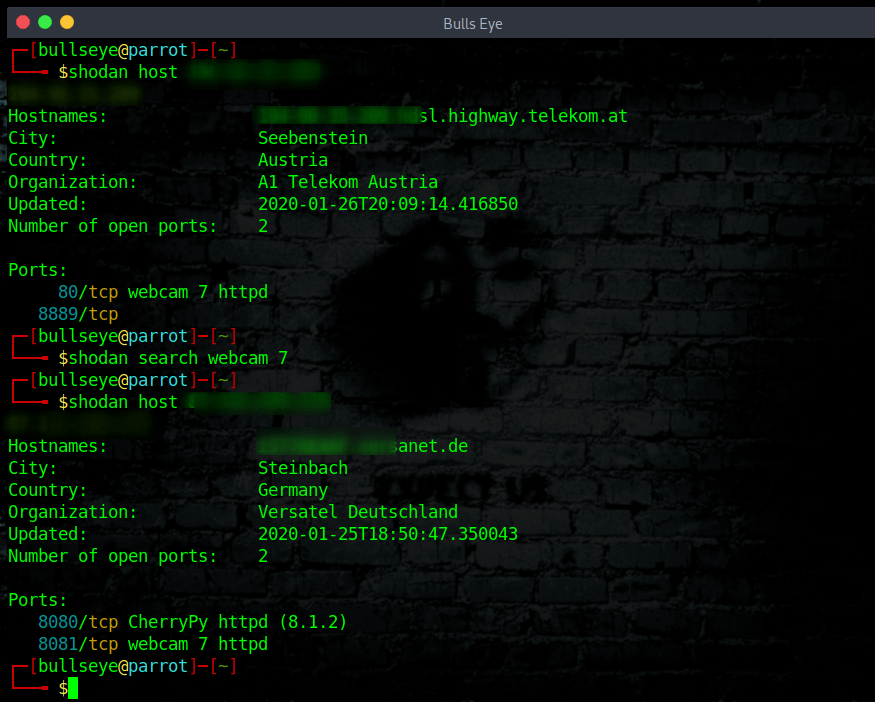
Security Webcam hacking with Shodan Eye getting more information.
Install Shodan Eye
You can find the script here:
https://github.com/BullsEye0/shodan-eye
In terminal:
| |
| |
| |
How to use Shodan Eye
(You will be asked for a Shodan API key)
| |

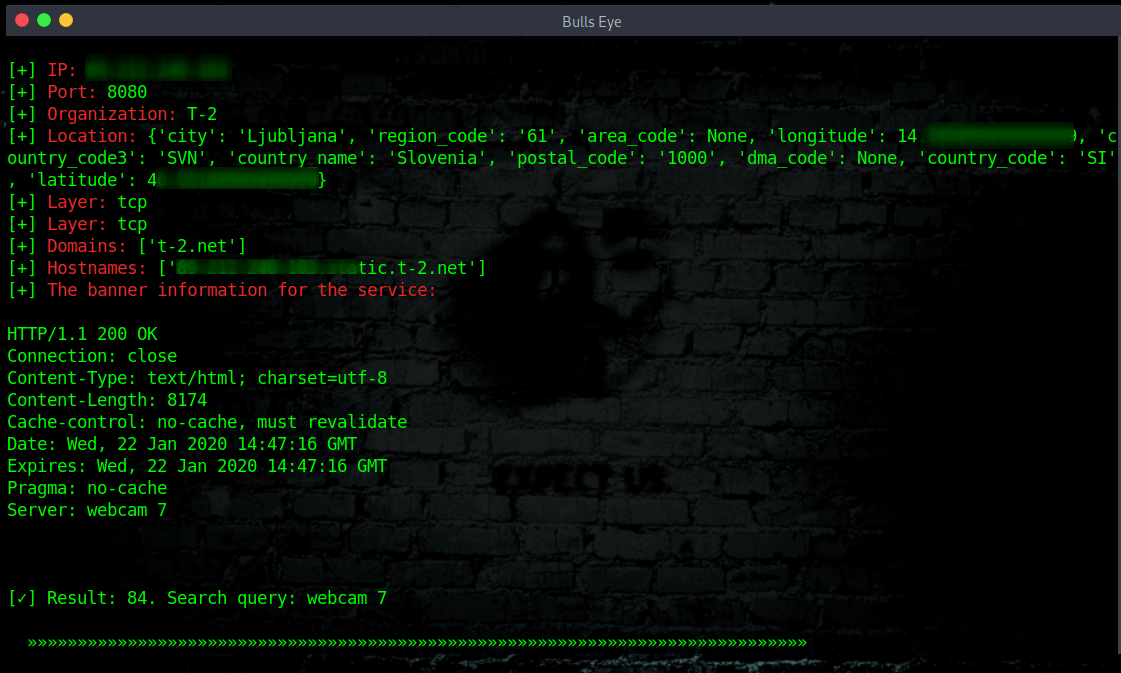
Webcam 7

Doing a Nmap scan for even more info
To find out more about the IP of the Security camera and to find some vulnerabilities, always do a Nmap scan. After that, you can search for an exploit. I have made an article about How to use Nmap NSE Scripts to find Vulnerabilities So that you can even find more vulnerabilities on an IP address.
With the use of Shodan, you can discover (some) open ports. But to discover more open ports on an IP address you better take a step to Nmap. We make an extensive Nmap scan below.
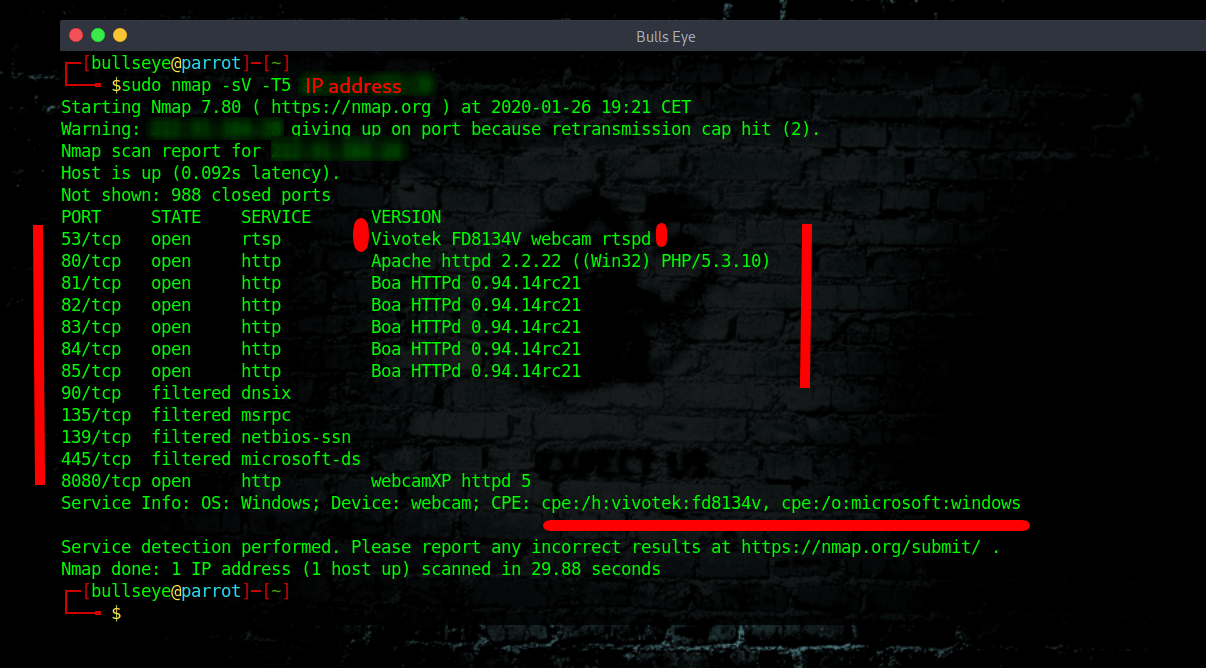
exploits Vivotek FD8134V webcam rtspd
As this Nmap scan shows, there are a lot of open ports, and a lot of info ..!
For this article I have used the following command:
| |
**The command meaning:
**-sV = Attempts to determine the version of the service running on port
-T5 = Insane (5) speeds scan; assumes you are on an extraordinarily fast network
* Optional -A = for a Traceroute
Looking for Exploits
In this example we search for: exploits Vivotek FD8134V webcam rtsp. (See the photo above)
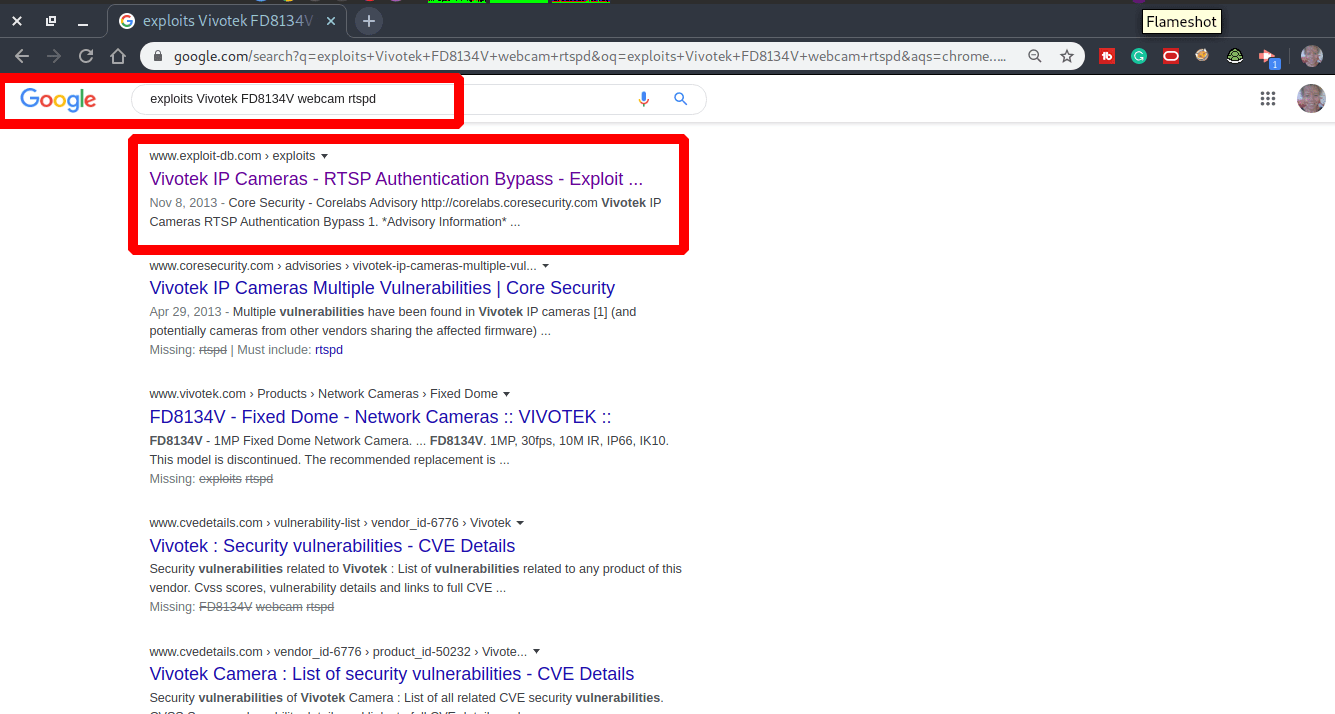
This way you can search for exploits for every vulnerability that you encounter.
“What hackers do is figure out technology and experiment with it in ways many people never imagined. They also have a strong desire to share this information with others and to explain it to people whose only qualification may be the desire to learn.”
― Emmanuel Goldstein
Video Security Webcam Hacking
To make things even clearer, I have recorded a video.
All IP addresses are randomly selected.
Obviously I’m assuming that the information I give would not be misused. See Disclaimer.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
Conclusion
It took a while before I decided to make an article about this. I also discussed this with various people. Because it is so simple to hack those security webcams. My goal is to warn everyone about this. Also, the factories that make these security web cameras.
(People are not - insufficiently informed) People are not aware of the risks they run.
Be aware that everything you connect to the internet is - can be visible to everyone..!
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.