Shodan Command Line a Step by Step Walkthrough
Shodan Command line in this article and video, I show you what you can do, and the benefit of using the Shodan command line in your terminal. Searching for Vulnerabilities to port scanning, there is an incredible amount possible with Shodan.
What is Shodan
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc …) currently connected to the internet using a variety of filters. Some have also described it as a search engine of service banners, which are metadata that the device sends back to the client.
Shodan the scariest search engine on the internet
Shodan terrifies non-technical people who don’t understand how the internet works. CNN called Shodan the “Scariest search engine on the internet” in 2013. This is definitely of no sense since attackers intent on causing harm don’t need Shodan to find targets.

Shodan Eye is a tool I made.
Beware of the attacks on your own devices!
A quick search for the term “default password” reveals countless printers, servers and system control devices that use “admin” as their user name and “1234” as their password. In many cases, it doesn’t even have a password, and you leave it blank. Until today, many connected systems require no credentials at all!
Some nice articles to read are the “Hacking printers” and “Hacking Security webcams” In these articles, I show you how to use Shodan for that.
What is the difference between Google or another search engine?
The most fundamental difference is that Shodan Eye analyzes the Internet, while Google analyzes the World Wide Web. Moreover, the devices connected to the World Wide Web are only a small part of what is really connected to the Internet.
Hackers love the terminal
“You are a hacker. Your home is the terminal. You work on several projects at once, You know every keystroke is valuable. With just some commands, you can automate tasks, install your favorite software, view a whole network, find vulnerabilities on just about anything connected to the internet, compile a script, create additional user accounts, properly configure anonymity software, and optimize our interactions with terminals. When you search for something, it should be blazing fast. If something is less than 100% efficient, you will spend hours figuring out the right way to save yourself seconds.”
Install Shodan
Shodan is already installed with the most penetration and security Linux distros, such as Kali Linux, Parrot OS, and BlackArch.
To show you a Shodan installation I have set up a Minimal Ubuntu Server 18.04
Shodan command line interface (CLI)
The shodan command-line interface (CLI) is packaged with the official Python library for Shodan, which means if you’re running the latest version of the library you already have access to the CLI. Also, the Shodan command line is more powerful than the website is.
Since I chose a Minimal Ubuntu Server to show the installation, I also have to install all other packages (eg python and pip) that are needed before you can install Shodan on your computer. It is good to try different Linux distros, you will learn a lot from that. And it is just fun..!
Python is not installed by default on CentOS. This also applies to a lot of other Linux distributions. I show you in the video how to install all of this.
Insall python and pip
To make it very easy, I put all the packages you need for python 2 and python 3 in one line.
To learn the command line well, I recommend that you don’t just copy everything, but type everything over, it’s a good way to learn
|
|
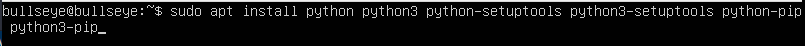
After the Python and Pip install you have this result down below.
Shodan Install using Pip
Shodan is then easy to install using pip.
|
|
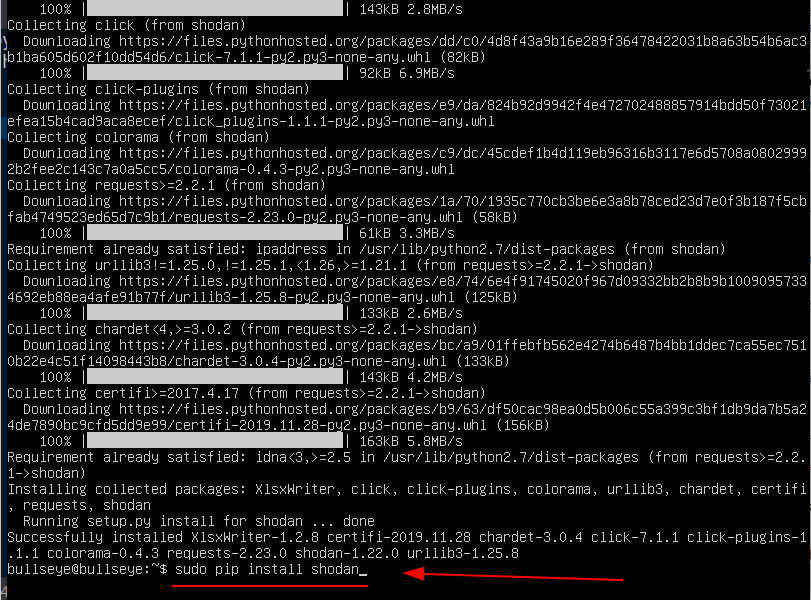
On the website of Shodan, they indicate installing Shodan using easy_install. (In this article I choose the pip install), see above.
|
|
Shodan account
_You **don't** need to have a paid account **to use Shodan**._ You always can use the free version. But if you want to use Shodan very extensively, if it is for your security company, then I can recommend this. For myself, I have had a Shodan lifetime membership for years. This offers many advantages and much more is possible.
Shodan Membership In short: more access to the Shodan website and the API. On Black Friday “2019” shodan had an awesome deal “Shodan lifetime membership for $ 1 (instead of $ 49) I don’t know if you can still get a shodan account for that $ 50. Otherwise, waiting for another black Friday might be a good choice.
Get your shodan API key
Now that Shodan is installed you have to make a Shodan account. A Shodan API key can be found here. Once your account has been confirmed you will receive your own API Key.
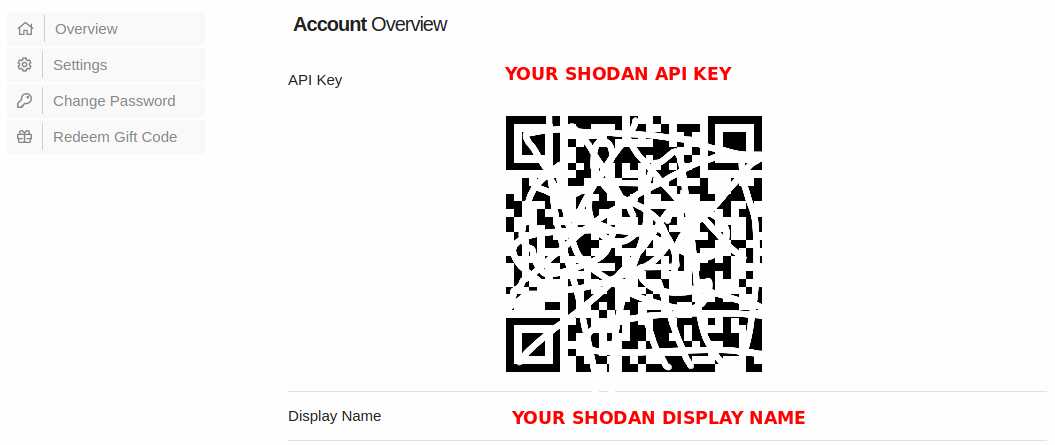
Initialize your Shodan API Key
Once the tool is installed you have to initialize the environment with your API key using shodan init
|
|
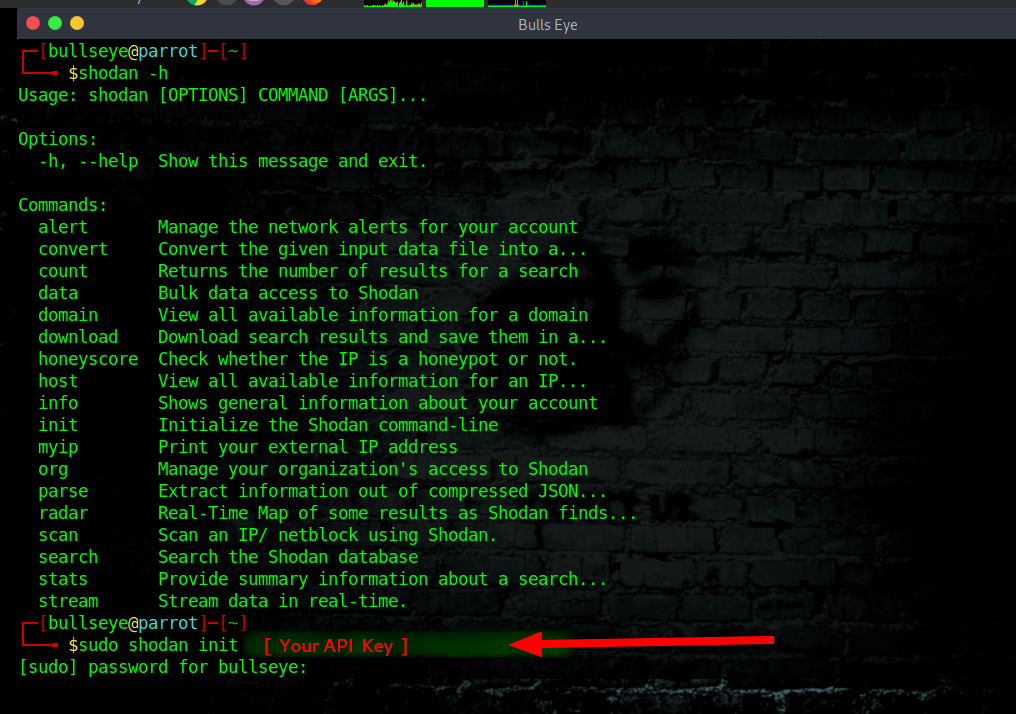
The Shodan command line
shodan -h / –help
|
|
|
|
myip
Print your external IP address
|
|
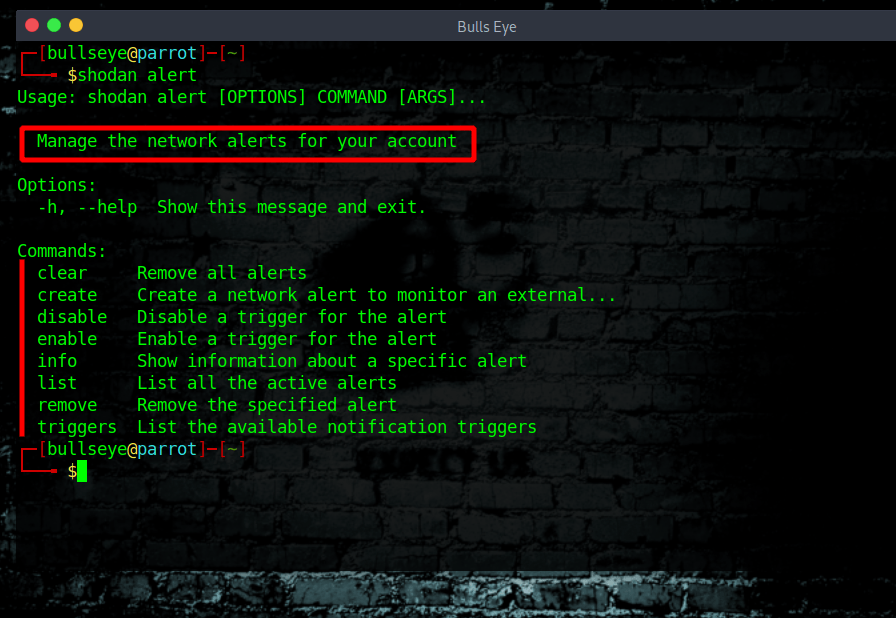
Shodan alert
Here is a list of all the commands to use for the Shodan alert. Keep track of the devices that you have exposed to the Internet. Setup notifications, launch scans and gain complete visibility into what you have connected. Here you can give it a try (It’s free)
|
|
|
|
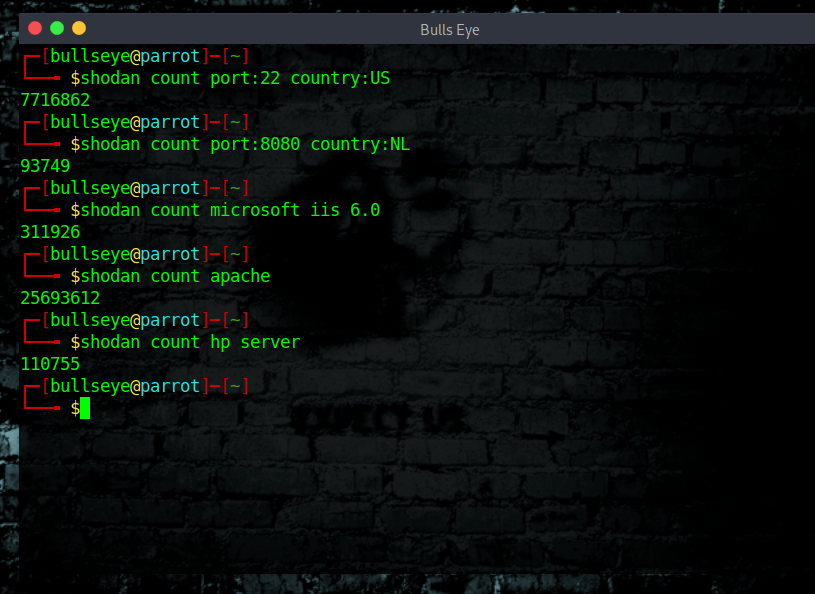
Shodan count
Shodan count returns the number of results for a search
|
|
|
|
|
|
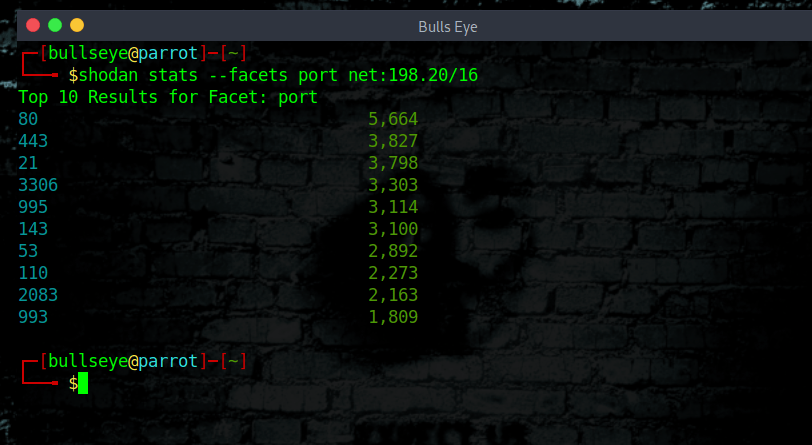
Using Shodan stats
|
|
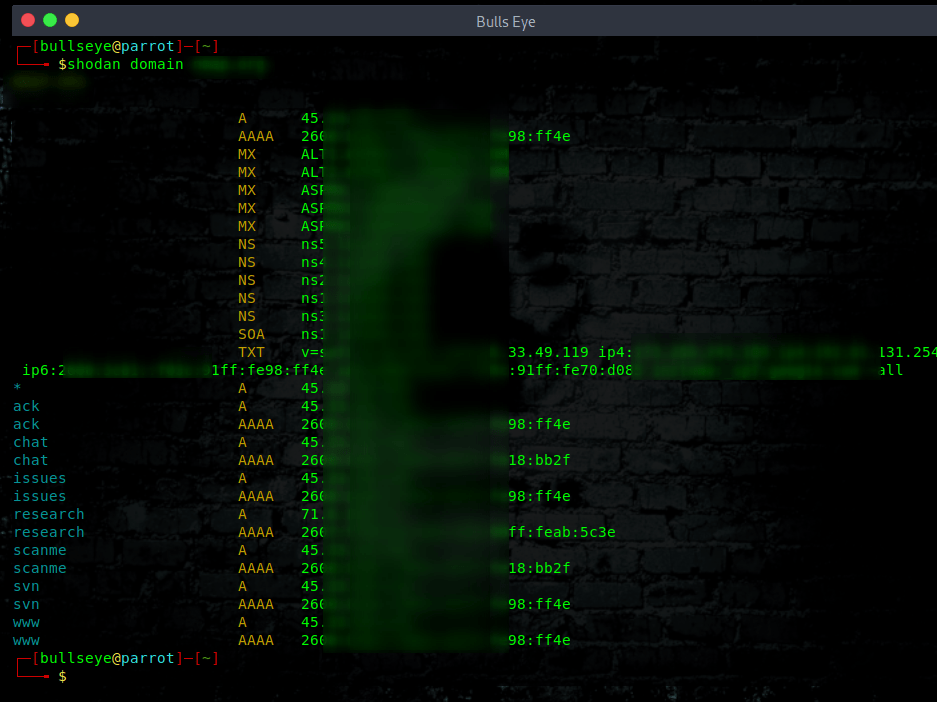
Domain Shodan
View all available information for a domain.
|
|
Shodan search
In the following lists you can see what keywords you can use for the Shodan Search
General
all, asn, city, country, cpe, device, geo, has_ipv6, has_screenshot, has_ssl, has_vuln, hash hostname, ip, isp, link, net, org, os, port, postal, product, region, scan, shodan.module, state, version
Screenshots
screenshot.label
HTTP
http.component, http.component_category, http.favicon.hash, http.html, http.html_hash, http.robots_hash, http.securitytxt, http.status, http.title, http.waf
Bitcoin
bitcoin.ip, bitcoin.ip_count, bitcoin.port, bitcoin.version
SNMP
snmp.contact, snmp.location, snmp.name
SSL
ssl, ssl.alpn, ssl.cert.alg, ssl.cert.expired, ssl.cert.extension, ssl.cert.fingerprint, ssl.cert.issuer.cn, ssl.cert.pubkey.bits, ssl.cert.pubkey.type, ssl.cert.serial, ssl.cert.subject.cn, ssl.chain_count, ssl.cipher.bits, ssl.cipher.name, ssl.cipher.version, ssl.version
NTP
ntp.ip, ntp.ip_count, ntp.more, ntp.port
Telnet
telnet.do, telnet.dont, telnet.option, telnet.will, telnet.wont
SSH
ssh.hassh, ssh.type
Restricted
The following filters are only available to users of higher API plans.
tag, vuln
Filters Cheat Sheet Shodan
Shodan currently crawls nearly 1,500 ports across the Internet. Here are a few of the most commonly-used search filters to get started.
Filter Name
Description
Example
city
Name of the city
Devices in San Diego
country
2-letter Country code
Open ports in the United States
http.title
Title of the website
“Hacked” Websites
net
Network range or IP in CIDR notation
Services in the range of 8.8.0.0 to 8.8.255.255
org
Name of the organization that owns the IP space
Devices at Google
port
Port number for the service that is running
SSH servers
product
Name of the software that is powering the service
Samsung Smart TVs
screenshot.label
Label that describes the content of the image
Screenshots of Industrial Control Systems
state
U.S. State
Devices in Texas
Examples of a Shodan Search
|
|
|
|
|
|
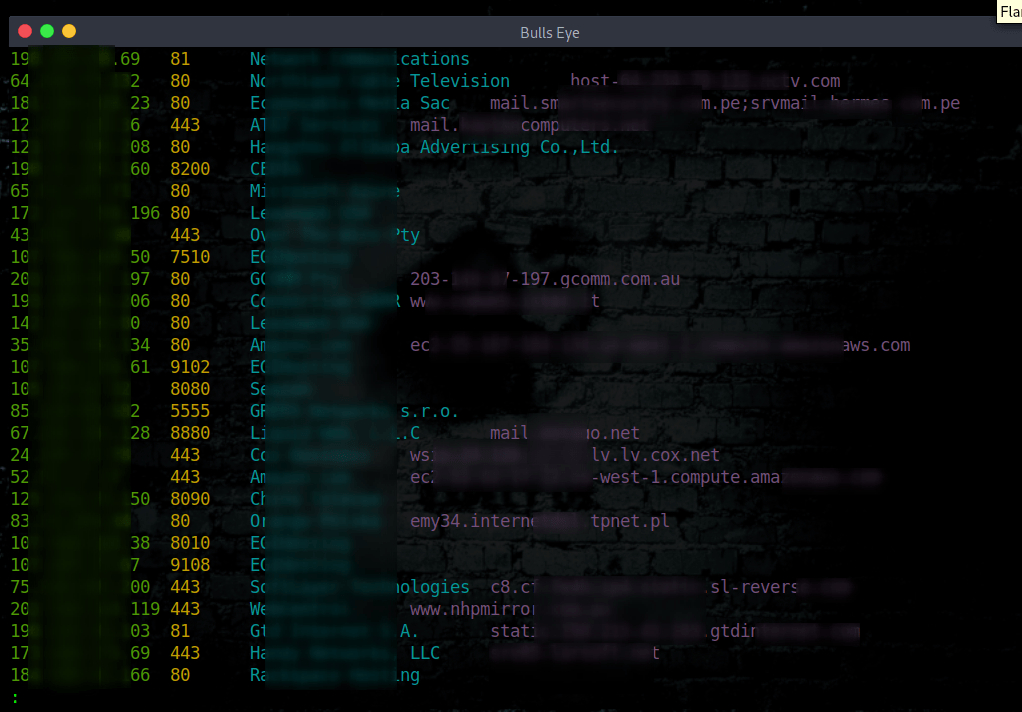
shodan search hacked by
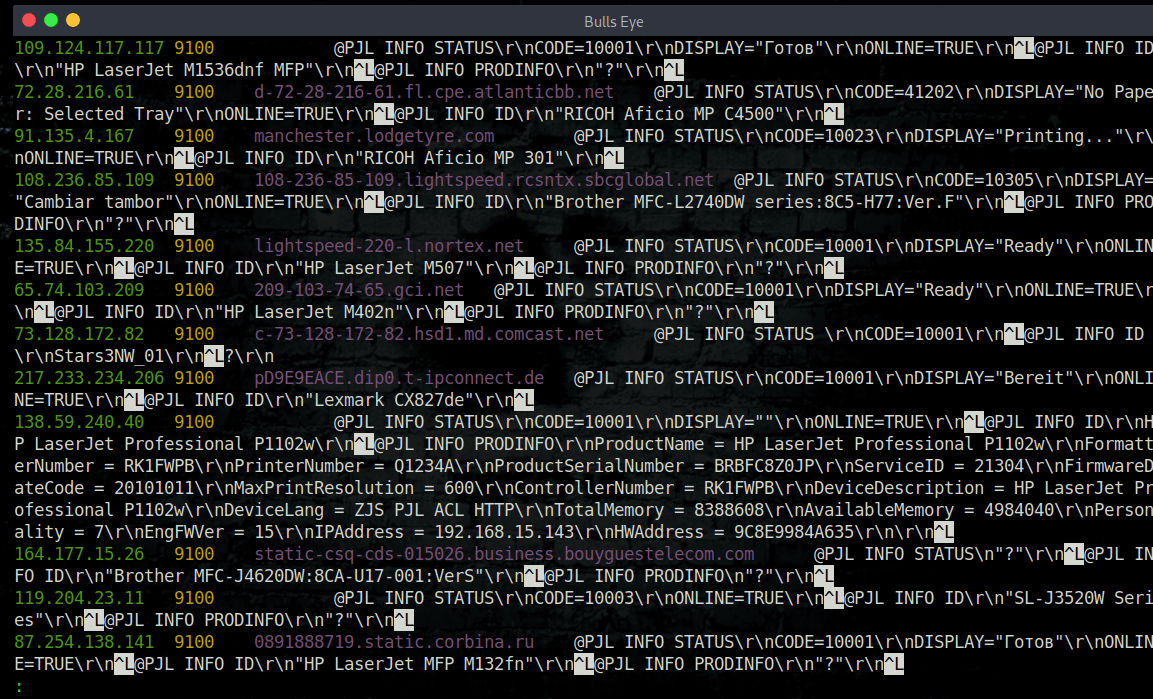
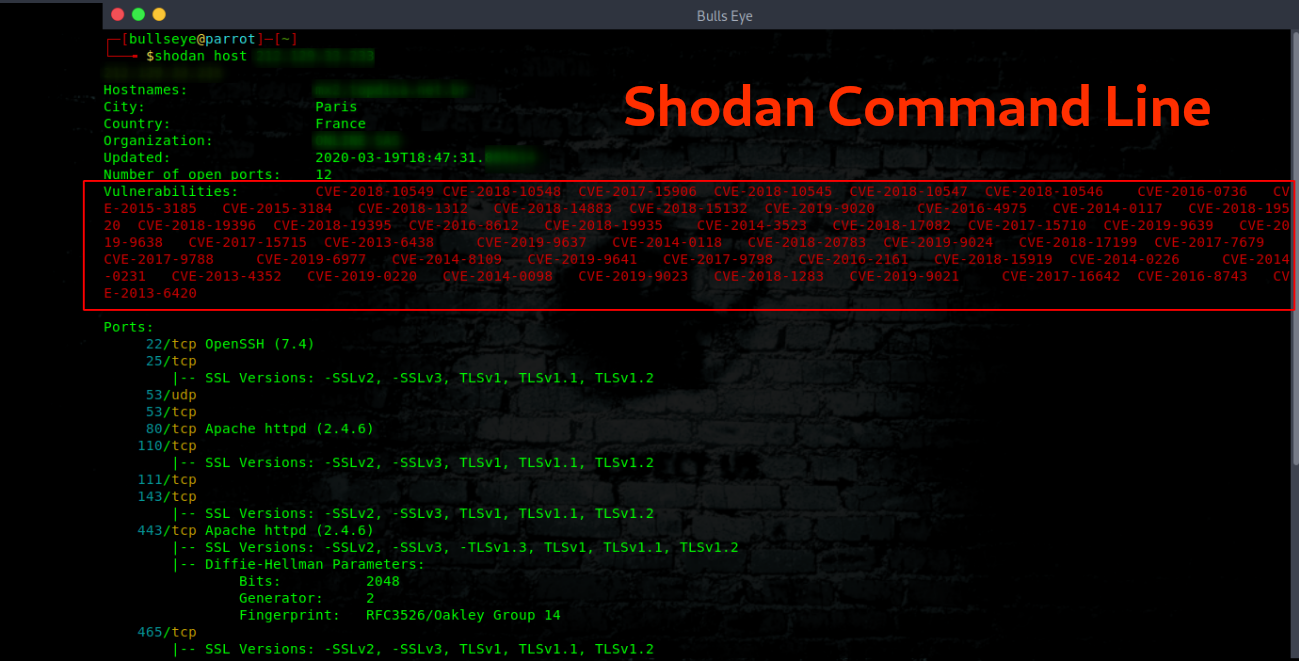
shodan host ip
View all available information for an IP. This also means that you often will find vulnerabilities, such as one of the photos you can see below. In the video, I will elaborate on this in more detail.
|
|
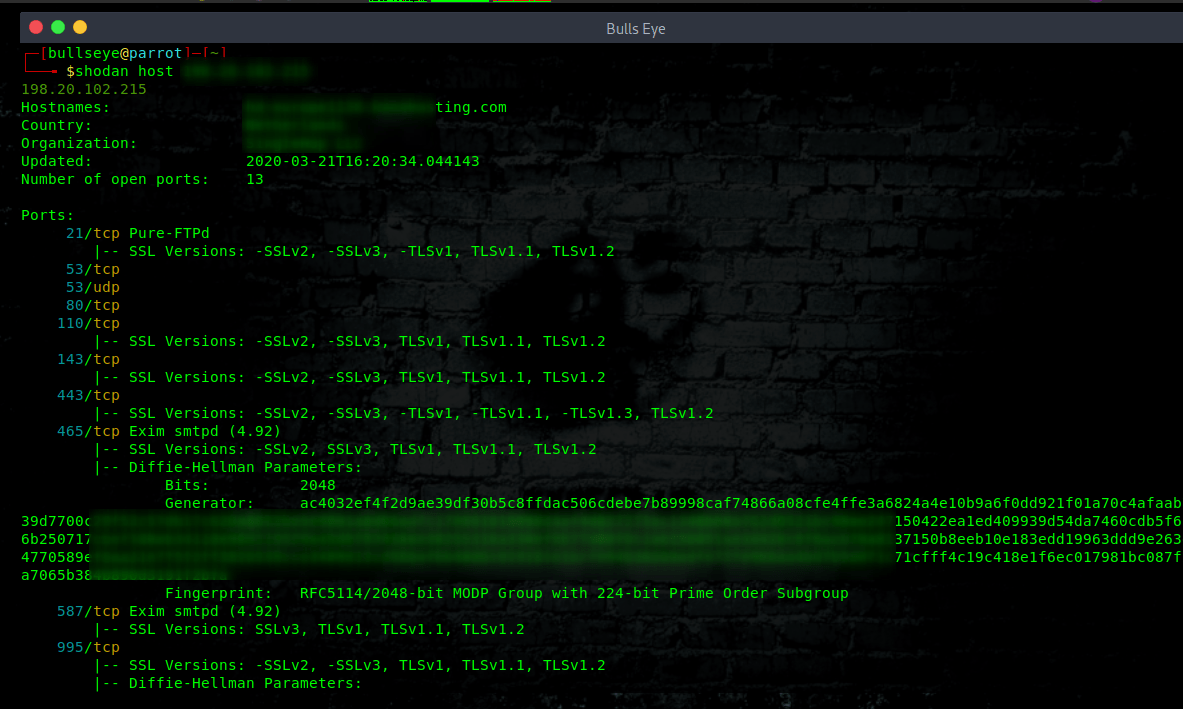
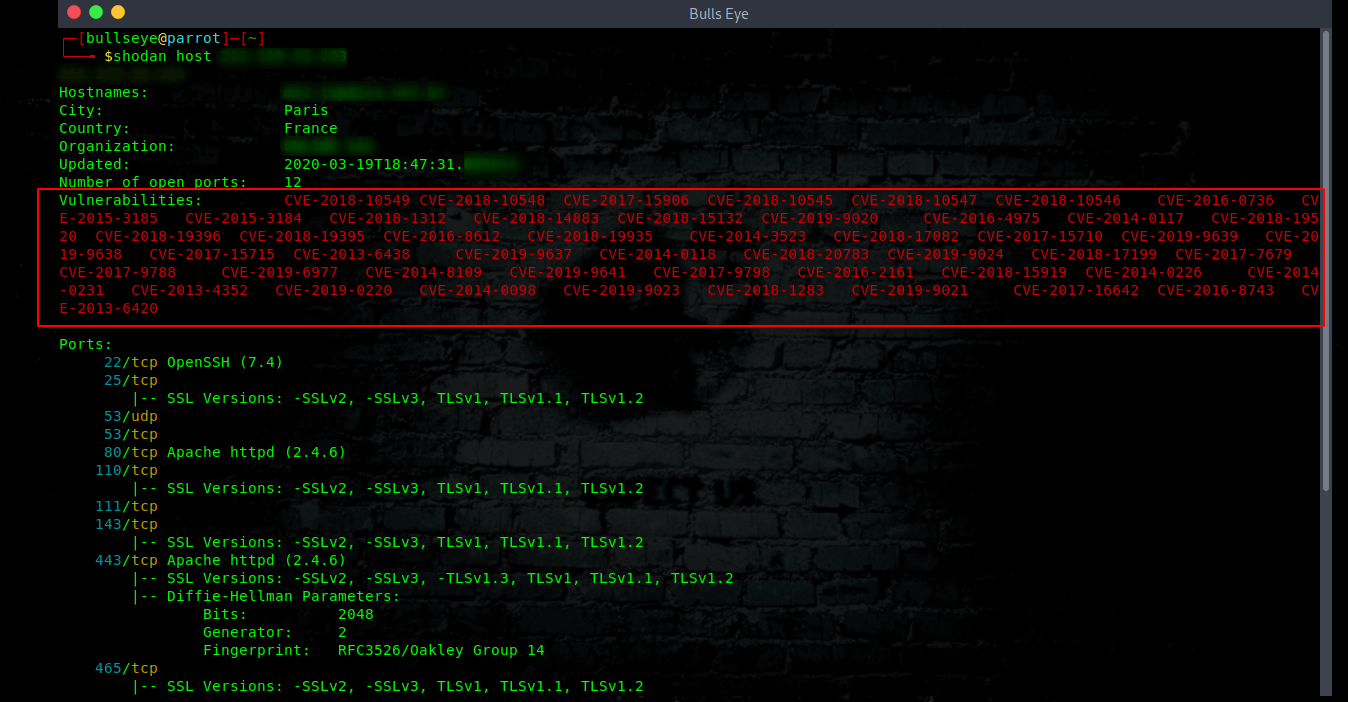
Finding vulnerabilities with Shodan
With this host, I don’t have to explain very much. Because this all seems very clear. Prevention in this is everything. “Don’t get hacked”
A way to prevent this kind of thing happens
Do some upgrades! It’s that simple.
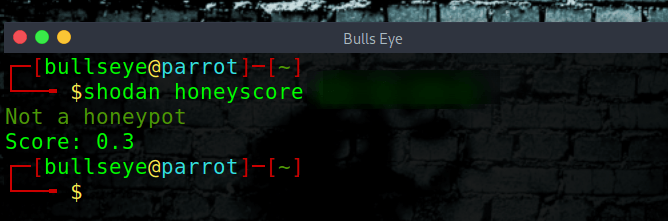
Honeyscore
To see if an IP address is perhaps a honeypot, you can find out with this simple Shodan command line
|
|
Video Shodan Command line
In this video I show you what options the Shodan Command line has and how you can use them. I’ll have setup a Ubunty 18.04 minimal server for this video to show you how to setup Shodan. I have choosen the Minimal Ubuntu server because i have to install python and pip on it as well. And this is just a CLI.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
Conclusion “Shodan Command line”
I can speak from my own experience and I advise everyone to take a Shodan account. A free Shodan account is enough for many. You can do so much with Shodan. In this article, I only talked about Shodan Command-Line. Not about the website where you can do and lookup an incredible amount of things.
Also, this is not my first article and video that I make more or less about Shodan. (In many videos you see Shodan come back) Some time ago I made Shodan Eye. A tool with which you can find all devices that are connected to the internet. Here you can find more about Shodan Eye and also in this article The first version of Shodan Eye.
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.