Snap Store Domain Hijacking Lets Attackers Push Malware Through Trusted Linux Apps
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
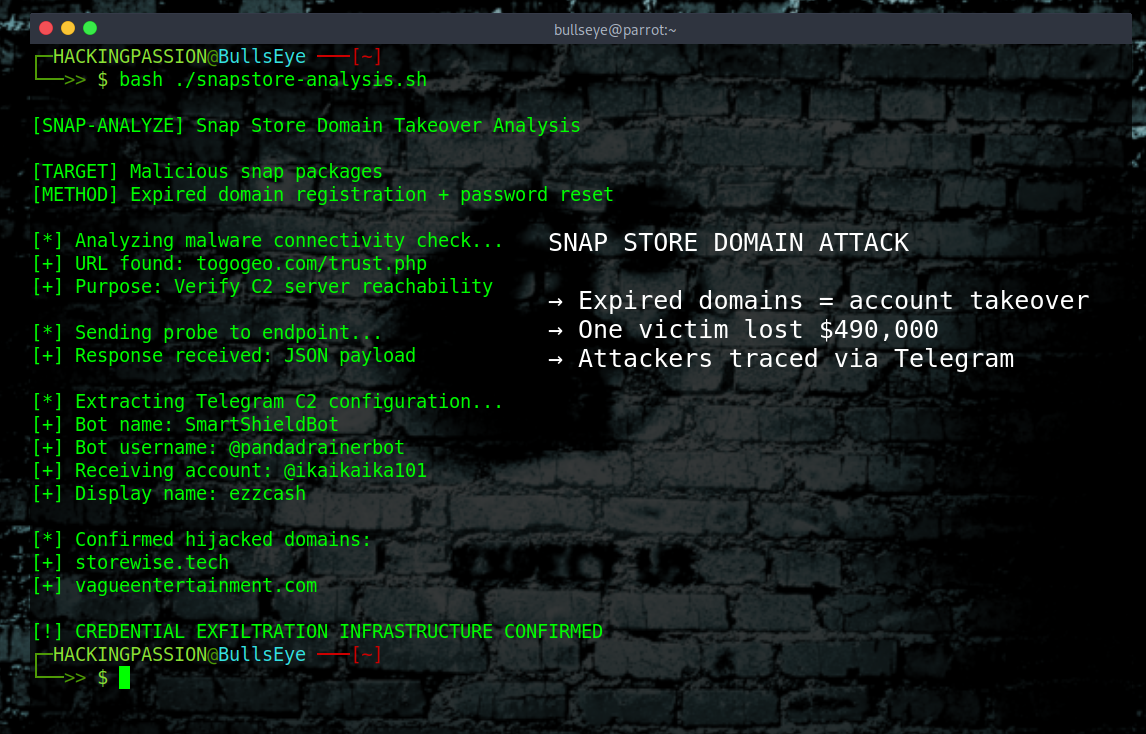
Attackers found a way to hijack legitimate apps in the Snap Store. 7000 packages. Millions of Linux users. One victim already lost 9 Bitcoin. That was $490,000. 🧐
The Snap Store is the official app store for Ubuntu and other Linux distributions, run by Canonical. When developers publish apps, they sign up with an email on their own domain. Something like dev@mycoolproject.tech. But domains expire. People forget to renew, move on to other things, and that domain goes back on the market for anyone to grab.
Attackers are watching for exactly this. They find Snap Store publishers whose domains lapsed, register those domains for a few bucks, set up email, and trigger a password reset. Suddenly they control an account that has been around for years, with apps people already have installed. The account looks exactly the same as before, same history, same publisher name, and the next update that gets pushed is malware.
The fake apps look like Exodus, Ledger Live, and Trust Wallet. They ask for a recovery phrase to “restore” the wallet, and the moment someone types those words, everything goes straight to the attackers through a Telegram bot. A fake error shows up on screen, and by the time anyone figures out what happened, the wallet is empty.
In February 2024, someone posted on the Snapcraft forum asking if the Exodus wallet in the store was legit. Their whole Bitcoin balance got transferred to an unknown address. 9 Bitcoin. Gone.
Alan Pope, a former Canonical employee who worked on the Snap Store team for ten years, has been tracking these scammers since early 2024.
He dug into the malware and found something the attackers probably did not want anyone to see. Before the malware steals anything, it pings a URL at togogeo.com/trust.php to check if it can reach the command server. When he hit that URL manually, the server spit back a full JSON dump of their Telegram setup. Bot name: SmartShieldBot. Username: @pandadrainerbot. The account getting the stolen credentials: @ikaikaika101, display name “ezzcash”.
After he wrote about this, the attackers changed their server to just return an exclamation mark and deleted their Telegram avatar.
Based on his research, the attackers are probably somewhere in or near Croatia. In cybersecurity, attribution is one of the hardest problems. IP addresses can be spoofed. Tools can be shared. Code comments can be faked. What we know for sure is how the attack works, not necessarily who is behind it.
Two hijacked domains confirmed so far: storewise.tech and vagueentertainment.com.
These scammers have been at it for two years and keep getting smarter. First they just uploaded fake apps with nice screenshots. When Canonical added filters, they switched to Unicode tricks, using letters from other alphabets that look almost the same. Armenian ժ instead of “d”, Cyrillic ӏ instead of “L”. Then came bait-and-switch. Upload a harmless game called “lemon-throw”, “alpha-hub”, or “tenor-freeze”, get it approved, then push malware in the next update. By the time anyone notices, people already installed it.
The domain takeover trick is the worst one yet because it breaks the last trust signal people had. An app that has been around for three years from a developer with history used to be safe. Now that same app can turn malicious tomorrow because the domain expired last month and someone else grabbed it.
Pope keeps pushing Canonical to fix this. Check if publisher domains are expiring. Add extra checks when old accounts suddenly wake up. Force two-factor authentication. The Snap Store does none of this.
In 2024, crypto wallet drainers stole $494 million worldwide, 67% more than 2023. Over 330,000 victims. The Snap Store attacks are just one piece of a much bigger problem.
- → Do not install crypto wallet apps from any app store, get them straight from the official project websites
- → If you publish snaps, keep your domain renewed and turn on two-factor authentication
- → Pope built a checker at snapscope.popey.com to see if a snap looks suspicious
Attackers use reconnaissance techniques to find targets like expired domains. I cover OSINT, how to map attack surfaces, and how to think like an attacker in my ethical hacking course:
Hacking is not a hobby but a way of life.
One of the sources: https://blog.popey.com/2026/01/malware-purveyors-taking-over-published-snap-email-domains/
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.