CVE-2026-24061. One Command, Root Access: The 11-Year Telnet Bug
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
It’s 2026 and attackers are still getting root shells via Telnet with a single command that requires no password whatsoever. 😏
SSH has existed for 31 years. Yet 221,000 telnet servers are still running online, and a bug hidden in the code since 2015 just handed attackers the keys to the kingdom. CVE-2026-24061. CVSS 9.8. Critical.
The vulnerability sat in GNU InetUtils telnetd for almost 11 years before anyone noticed. Security researcher Kyu Neushwaistein found it on January 20, 2026, and by January 21, attackers were already exploiting it in the wild.
Here’s how simple this exploit is.
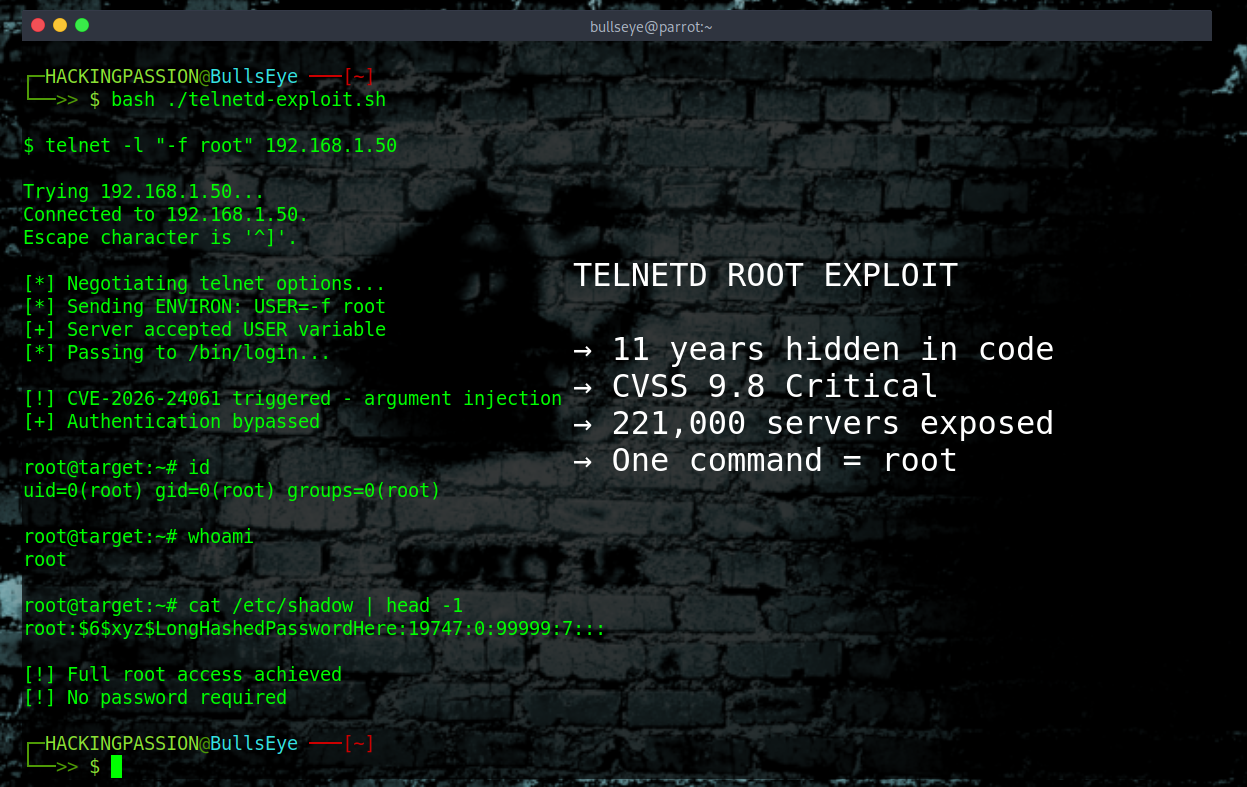
When someone connects via telnet, the server passes the USER environment variable to the login program. The login program has a flag called -f that means “skip authentication, this user is already verified.” Telnetd never checked if the USER value started with a dash. So attackers just send this:
USER='-f root' telnet -a target
The server receives “-f root” as the username and passes this straight to login. Login sees the -f flag and thinks “oh, pre-authenticated, no password needed.” Root shell granted instantly.
With root access, attackers own the system. They can read sensitive files, install backdoors, pivot to other machines on the network, or add the device to a botnet.
The vulnerable code in telnetd/utility.c is simple:
| |
No check if the value starts with a dash. It just grabs whatever the client sends and passes it straight to login.
One line of code that checks if the value starts with a dash. That’s literally all it took, and this check was missing for nearly eleven years. The bug was introduced on March 19, 2015, when a developer added the USER variable handling to support auto-login functionality. Someone on the mailing list wanted it, they added it, nobody thought about sanitization. The code shipped in version 1.9.3 on May 12, 2015, and stayed broken until now.
Simon Josefsson, the GNU maintainer who wrote the advisory, opened with this line: “If you are tired of modern age vulnerabilities, and remember the good old times on bugtraq, I hope you will appreciate this one.”
Within 48 hours of disclosure, multiple working exploits appeared on GitHub. SafeBreach-Labs, Chocapikk, and others published proof-of-concept code that anyone can download and run. That’s how easy this vulnerability is to weaponize.
GreyNoise started tracking exploitation within 24 hours of disclosure. Their data shows 18 to 21 unique attacker IPs running automated scans, with 60 telnet sessions recorded and over 1,500 packets captured. 83% of the attacks targeted root specifically. The attacks came from Hong Kong, the United States, Japan, the Netherlands, China, Germany, Singapore, and Thailand. Some were fully automated scripts while others showed signs of human operators at the keyboard, manually exploring compromised systems.
In cybersecurity, attribution is one of the hardest problems. IP addresses can be spoofed. Tools can be shared. Attack patterns can be copied. What we know for sure is how the exploit works and that it’s being actively used, but who exactly is behind it remains unclear.
Affected systems include Debian, Ubuntu, Kali Linux, Trisquel, and basically any Linux distribution shipping GNU InetUtils telnetd versions 1.9.3 through 2.7. Embedded devices and legacy systems running telnet for remote management are at highest risk because they often don’t receive security updates at all.
Canada’s Cyber Centre issued alert AL26-002. Belgium’s CCB published a critical warning. The Dutch NCSC released an advisory. Spain’s INCIBE also warned about active exploitation. When four national cybersecurity agencies all say “patch now,” they mean it. Debian pushed a fix within two days and GNU released version 2.8 with the patch.
But here’s the problem: many telnet servers run on embedded devices and legacy systems that will never get updated. Industrial equipment and old routers. These systems will stay vulnerable forever, and Shodan shows around 221,000 devices with telnet exposed to the internet right now. Not all of them run the vulnerable GNU implementation, but plenty do.
Telnet sends everything in plain text: passwords, commands, data. Anyone on the network can intercept it. SSH replaced telnet in 1995 specifically because of these problems, and thirty-one years later, we’re still finding critical vulnerabilities in software that should have been retired decades ago.
If telnet is running somewhere it shouldn’t be:
→ Disable it immediately and replace it with SSH → If disabling isn’t possible, block port 23 at the firewall → Restrict access to trusted IPs only → Check logs for suspicious authentication attempts
To see if a Linux system is running telnetd:
systemctl status inetutils-inetd
Or check if anything is listening on port 23:
netstat -tlnp | grep :23
If telnetd is there and it’s not absolutely necessary, turn it off.
This is exactly the kind of legacy vulnerability that penetration testers look for. Old services, forgotten code, assumptions that were never questioned. I cover reconnaissance, service enumeration, and exploitation in my ethical hacking course:
Join my complete ethical hacking course(The link supports me directly as the instructor!)
Hacking is not a hobby but a way of life.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.