VoidLink: 88,000 Lines of AI-Built Malware in 6 Days
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
One developer just built 88,000 lines of advanced malware in six days using AI. A single person with an AI coding assistant created a framework sophisticated enough to target AWS, Azure, Google Cloud, Alibaba, Tencent, Kubernetes pods, and Docker containers. 🧐
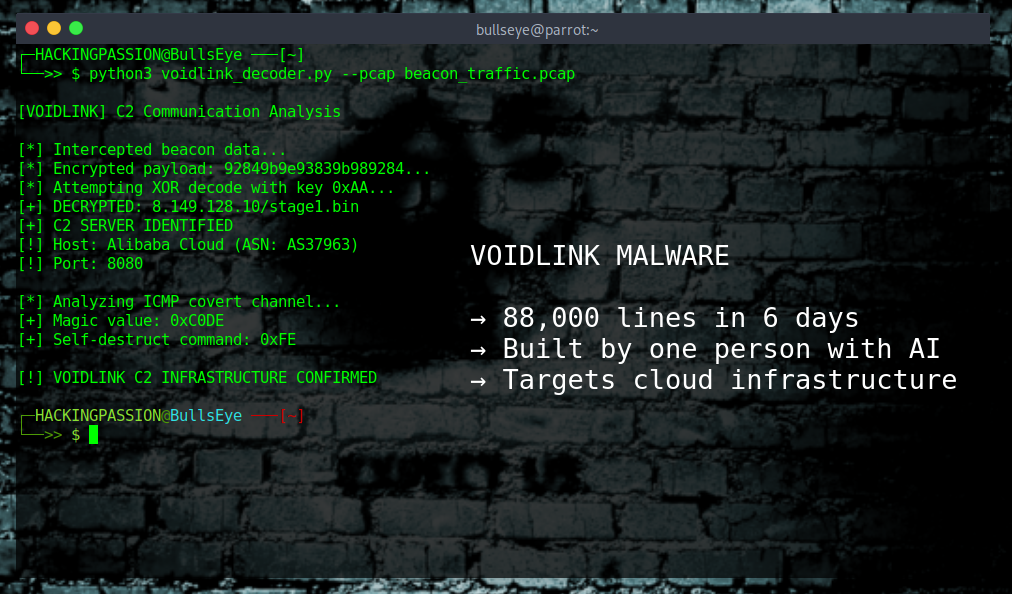
Check Point revealed VoidLink on January 20, 2026. A Linux malware framework designed to compromise cloud infrastructure. The malware detects where it runs and changes its behavior based on what it finds.
But the malware itself is not the story. How it was built is…
The developer used TRAE SOLO, an AI coding assistant made by ByteDance, the company behind TikTok. The AI generated a complete development plan spanning 30 weeks across three separate teams. Sprint schedules, coding guidelines, feature breakdowns, testing criteria. A full enterprise software roadmap for building malware.
One person followed that roadmap alone. The project started November 27, 2025. By December 4, the framework had 88,000 lines of working code. A 30-week plan for three teams, executed by one developer in less than a week.
Researchers only discovered the AI involvement because the developer made multiple mistakes. An open directory on their server exposed everything: source code, documentation, sprint planning files, and the helper files that TRAE automatically generates. The developer copied those helper files to the server along with the source code, and that exposed the entire development process.
And then there was VirusTotal… On December 4, a compiled version of the malware was uploaded to VirusTotal. That submission is what triggered this research in the first place. Uploading your own malware to a service that shares samples with every security vendor in the world is a bit stupid, don’t you think?
The leaked documents show something interesting. The developer instructed the AI not to implement code or provide technical details about malware techniques. Researchers believe this was an attempt to bypass safety guardrails. Get the design and architecture first, then build it step by step using the blueprint.
VoidLink is written in Zig. Security tools are not tuned for Zig patterns yet, which means traditional detection methods struggle with it.
What does the malware actually do?
Once deployed, VoidLink fingerprints the environment. It queries cloud provider metadata APIs and scans for installed security products by looking for specific process names and installation paths.
- → CrowdStrike falcon-sensor
- → SentinelOne
- → Carbon Black
- → Falco
- → Wazuh
- → OSSEC
- → osquery
- → auditd
When security tools are detected, the malware slows down. It spaces out communication with the command server and reduces scanning activity. VoidLink calculates a risk score for each environment and adjusts its behavior accordingly. In well-defended networks it moves carefully, and gets aggressive.
The framework includes 37 plugins covering reconnaissance, credential harvesting, lateral movement, persistence, and anti-forensics. It steals SSH keys, Git credentials, API tokens, and browser data. It wipes logs, cleans shell history, and overwrites deleted files with random data. If the malware detects tampering, it triggers self-destruct and takes all evidence with it.
The rootkit capabilities use three different methods depending on the kernel version. LD_PRELOAD for older systems, Loadable Kernel Modules for others, and eBPF for modern kernels. The malware picks whichever method works best for the target.
The malware also hides by pretending to be normal system processes. Names like [kworker/0:0], migration/0, and watchdog/0. Any sysadmin looking at a process list would scroll right past these. They look like standard kernel threads that belong there.
Sysdig researchers discovered something that has never been documented in malware before. The command server compiles kernel modules on demand for each target’s specific kernel version. They call it Serverside Rootkit Compilation. The C2 server builds exactly what the target needs and delivers a custom rootkit. Previous malware either shipped multiple pre-compiled modules or required build tools on the target itself. This approach solves the kernel portability problem without bloating the implant.
Technical details for defenders:
- → C2 server: 8.149.128.10 on port 8080, hosted on Alibaba Cloud
- → XOR obfuscation key: 0xAA
- → ICMP covert channel with magic value 0xC0DE
- → Self-destruct command: 0xFE
File hashes:
- → Stage 0: 70aa5b3516d331e9d1876f3b8994fc8c18e2b1b9f15096e6c790de8cdadb3fc9
- → Stage 1: 13025f83ee515b299632d267f94b37c71115b22447a0425ac7baed4bf60b95cd
- → Implant: 4c4201cc1278da615bacf48deef461bf26c343f8cbb2d8596788b41829a39f3f
The code has comments in Mandarin. Real Mandarin, not Google Translate. Whoever wrote this knows how kernel development works. Sysdig thinks a human was in charge, but AI did most of the coding.
No victims have been found yet. The framework looks almost ready to use, and researchers think it might have been built to sell to other attackers.
Here is the thing about attribution. In cybersecurity, attribution is one of the hardest problems. IP addresses can be spoofed. Tools can be shared. Languages in code can be faked.
What is clear: one developer with AI assistance built in six days what would normally take a professional team months. The framework is advanced, modular, and ready to deploy.
Group-IB published a report on January 20 showing AI-related discussions on dark web forums have increased 371% since 2019. Dark LLMs are selling for $30. Deepfake tools for $5. The tools that used to require serious skill and time are now available to anyone willing to pay.
VoidLink is not theoretical. It exists, it works, and nobody has been caught.
Hacking is not a hobby but a way of life. 🎯
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.