The best vulnerable websites to improve your hacking skills

Some of the best places to learn ethical hacking. The best vulnerable websites to exercise your hacking skills whether you are a hacker, cybersecurity, pen-tester or still a n00b.
These vulnerable websites are great for developing our minds, increasing our capacity to solve problems, new innovative ideas come to our minds. Also, you will face brainfuck a lot of difficulties. Never give up always try to give your best. Because if you want to be a professional hacker, then you must know about the hacker attitudes and …
“real hackers never give up”
There are a lot of gaping holes in almost every security system. And to discover these is this is also a great opportunity to also discover the various tools that are needed for hacking. What the different options are etc. Use these websites to practice your hacking skills so you can be the best defense.
“An attack is definitely the best form of defense”
This applies to a lot of companies, they are hacking their own websites and even recruiting ethical hackers in an attempt to find vulnerabilities before the bad guys do as such ethical hacking is now a much sought after skill.
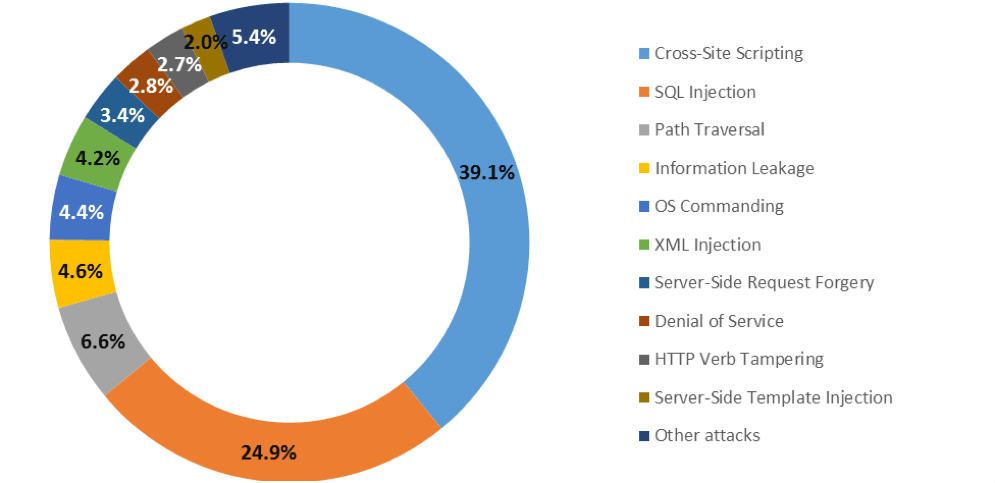
Legal vulnerable websites are useful to practice various types of web application attacks like:
Cross-Site Scripting (XSS)
The goal of this threat could be to inject code that can be executed on the client-side browser.
XML External Entities (XXE)
The goal of this may lead to the disclosure of confidential data, denial of service, server-side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts.
SQL Injection
The goal of this threat could be to bypass login algorithms, sabotage the data, etc.
Sensitive data exposure
The goal of this can vary anything from passwords, session tokens, credit card data to private health data and more can be exposed.
Defacement
The goal of this threat is to modify the page been displayed on a website and redirecting all page requests to a single page that contains the attacker’s message.
Session Hijacking
The goal of this attack compromises the session token by stealing or predicting a valid session token to gain unauthorized access to the Web Server.
Session Fixation
The goal of this attack permits an attacker to hijack a valid user session. The attack explores a limitation in the way the web application manages the session ID, more specifically the vulnerable web application
Cross-Site Request Forgery (CSRF)
The goal of this is forcing an end user to execute unwanted actions on a web application in which they’re currently authenticated. If the victim is an administrative account, CSRF can compromise the entire web application
Cookie/Session Poisoning
The goal of this threat is to modify cookies/session data by an attacker to gain unauthorized access.
Broken Authentication
The goal of this attack permits automated attacks such as credential stuffing, where the attacker has a list of valid usernames and passwords.
Form Tampering
The goal of this threat is to modify form data such as prices in e-commerce applications so that the attacker can get items at reduced prices.
**Code Injection **
The goal of this threat is to inject code such as PHP, Python, etc. that can be executed on the server. The code can install backdoors, reveal sensitive information, etc, etc.
Try to push boundaries ..!
Try to learn hacking in various ways. I know some people who can solve the best challenges but cannot write a line of code. Or many think they are learning how to hack by just coming off with a few buttons. (In most cases it doesn’t work that way)
“A script kiddie” is someone who knows nothing about hacking and only uses a few buttons of tools made by others. These are often the most dangerous people because they don’t know what they’re doing. And can cause so much major damage.
How nice, is it if you know more about how to do it. Try to discover your own ways. And maybe write your own tools..!
Improve your Linux skills
In this article, I wrote before you can Improve your Linux skills.
Best Linux Commands Hacks and other Cool Tricks for Beginners
Here are some vulnerable websites to test your mettle against without getting into trouble.
pwnable.kr
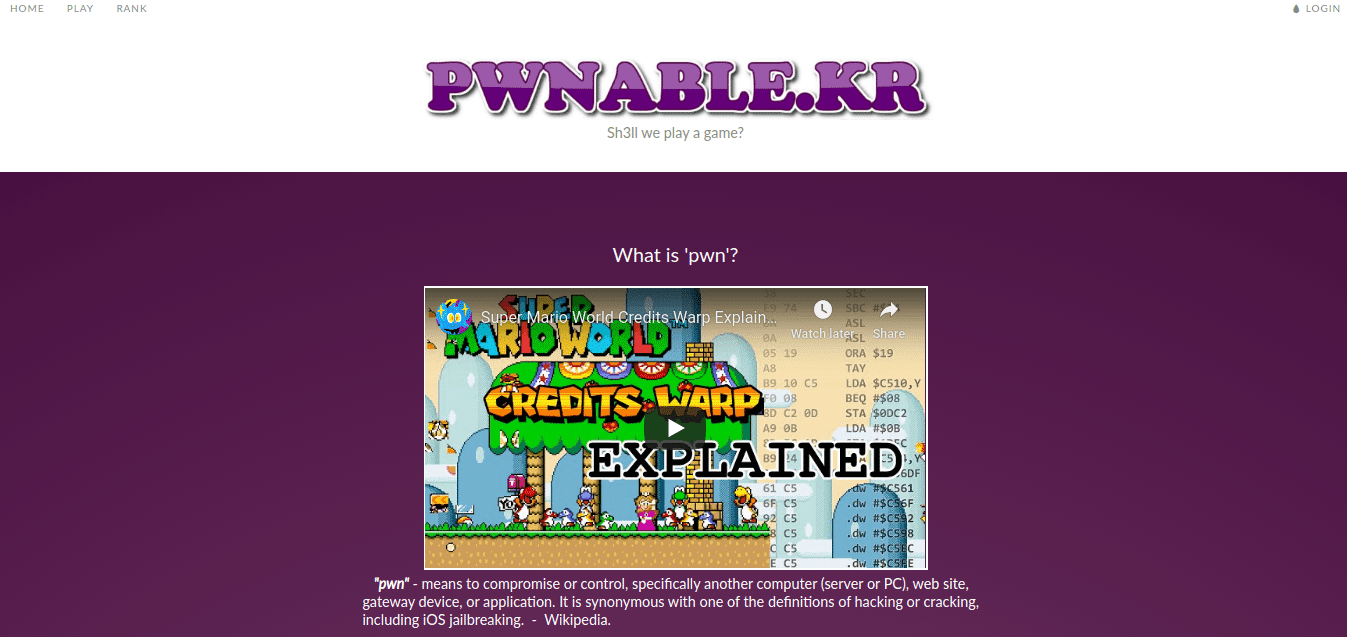
pwnable.kr is a non-commercial wargame site which provides various pwn challenges regarding system exploitation. the main purpose of pwnable.kr is ‘fun’. please consider each of the challenges as a game. while playing pwnable.kr, you could learn/improve system hacking skills but that shouldn’t be your only purpose.
pwnable.tw
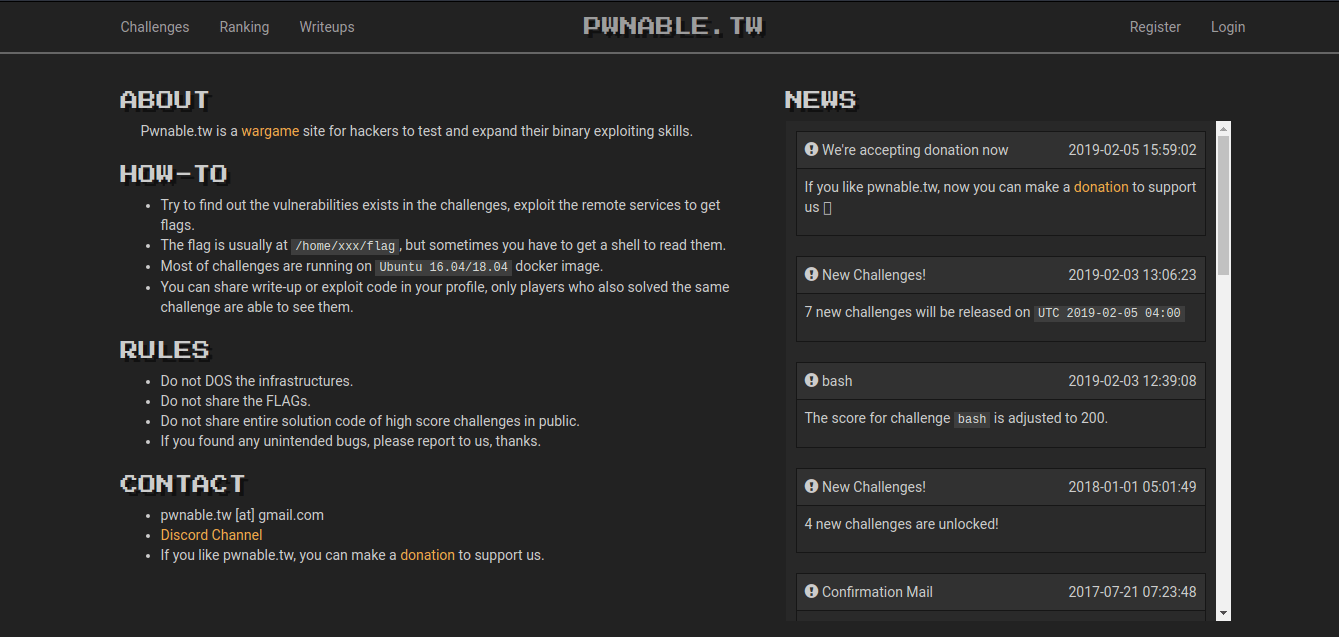
Pwnable.tw is a wargame site for hackers to test and expand their binary exploiting skills.
HOW-TO
- Try to find out the vulnerabilities that exist in the challenges, exploit the remote services to get flags.
- The flag is usually at /home/xxx/flag, but sometimes you have to get a shell to read them.
- Most of the challenges are running on Ubuntu 16.04/18.04 docker image.
- You can share a write-up or exploit code in your profile, only players who also solved the same challenge are able to see them.
hack.me
Hack.me is a FREE, community-based project powered by eLearnSecurity. The community can build, host and share vulnerable web application code for educational and research purposes.
It aims to be the largest collection of “runnable” vulnerable web applications, code samples and CMS’s online.
(This is more a test website..But still can improve your hacking skills a lot ..!)
The platform is available without any restriction to any party interested in Web Application Security:
- students
- universities
- researchers
- penetration testers
- web developers
CTFlearn
CTFlearn is an ethical hacking platform that enables tens of thousands to learn, practice, and compete.
The main attraction, of course, is the user-submitted Problems and Challenges which span the typical CTF theology such as Binary Exploitation, Cryptography, Reverse engineering, Forensics, Web attacks (see XSS, SQL Injection and the likes). There are also group the challenges by Popularity, level of Difficulty and order of Appearance.
Google Gruyere
Gruyere It’s not often we see the pairing of cheese and hacking, but this website is a lot like good cheese—full of holes. It also uses a “cheesy” code and the entire design is cheese-based. Gruyere is a great option for beginners who want to dive into finding and exploiting vulnerabilities, but also learn how to play on the other side and defend against exploits.
Gruyere is written in Python, with bugs that aren’t specific to Python, and offers a substantial number of security vulnerabilities chosen to suit beginners. Some of the vulnerabilities are:
- Cross-site scripting (XSS)
- Cross-site request forgery (XRF)
- Remote code execution
- DoS attacks
- Information disclosure
Gruyere code lab has divided vulnerabilities into different sections, and in each section, you will have a task to find that vulnerability. Using both black and white box hacking, you’ll need to find and exploit bugs.
Root Me
Root Me A multilanguage security training platform, Root Me is a great place for testing and advancing your hacking skills. It features over 300 challenges which are updated regularly and more than 50 virtual environments, all to provide a realistic environment. Root Me also has a passionate community of over 200,0000 members, all of whom are encouraged to participate in the development of the project and earn recognitions.
Different subjects covered on Root Me include:
- Digital investigation
- Automation
- Breaking encryption
- Cracking
- Network challenges
- SQL injection
It’s a solid platform and a great way to practice your hacking skills, although it’s not as beginner-friendly as some of the other entries on this list.
Hack The Box
Hack The Box (HTB) is an online platform allowing you to test your penetration testing skills. It contains several challenges that are constantly updated. Some of them simulating real-world scenarios and some of them leaning more towards a CTF style of challenge. It contains several challenges that are constantly updated. Some of them simulating real-world scenarios and some of them leaning more towards a CTF style of challenge. You should try this site out if you have an interest in network security or information security.
"I suggest you to try to hack your way into this website."
Hacking-Lab

Hacking-Lab is an online ethical hacking, computer network, and security challenge platform, dedicated to finding and educating cybersecurity talents. … Hacking-Lab’s goal is to raise awareness towards increased education and ethics in information security.provides the CTF (Capture The Flag) challenges for the European Cyber Security Challenge but hosts challenges on their own platform which anyone can take part in once you have registered.
Hacking-Lab is providing CTF and mission style challenges for international competitions like the European Cyber Security Challenge, and free OWASP TOP 10 online security labs. Hacking-Lab’s goal is to raise awareness towards increased education and ethics in information security.
Game of Hacks
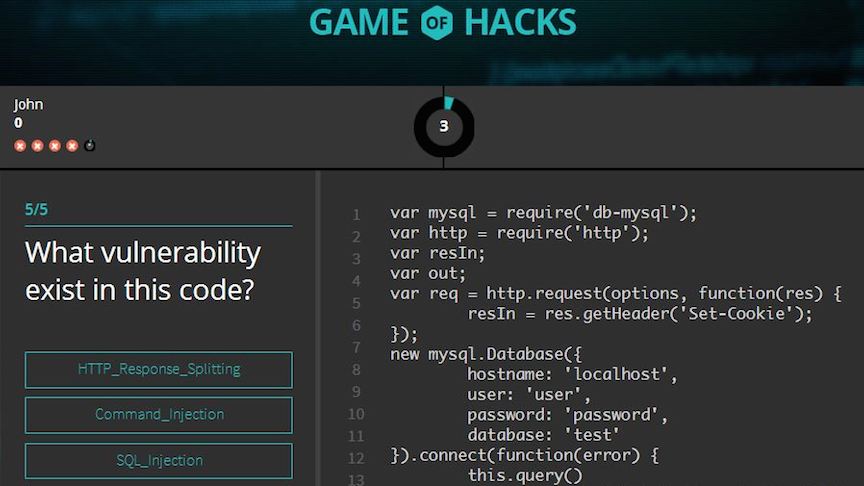
Game of Hacks, This game was designed to test your application hacking skills. You will be presented with vulnerable pieces of code and your mission if you choose to accept it is to find which vulnerability exists in that code as quickly as possible. In the game, developers and security professionals test their application hacking skills, improve their code security know-how and facilitate better security practices in hope of reducing the number of vulnerabilities in their applications.
Available for desktop, tablet, and mobile, Game of Hacks presents developers with vulnerable pieces of code and challenges them to identify the application layer vulnerability as quickly as possible. It even has a two-player mode allowing head-to-head competition. Players analyze vulnerabilities including SQL injection, XSS, log forgery, path traversal, parameter tampering and others in myriad programming languages.
OverTheWire
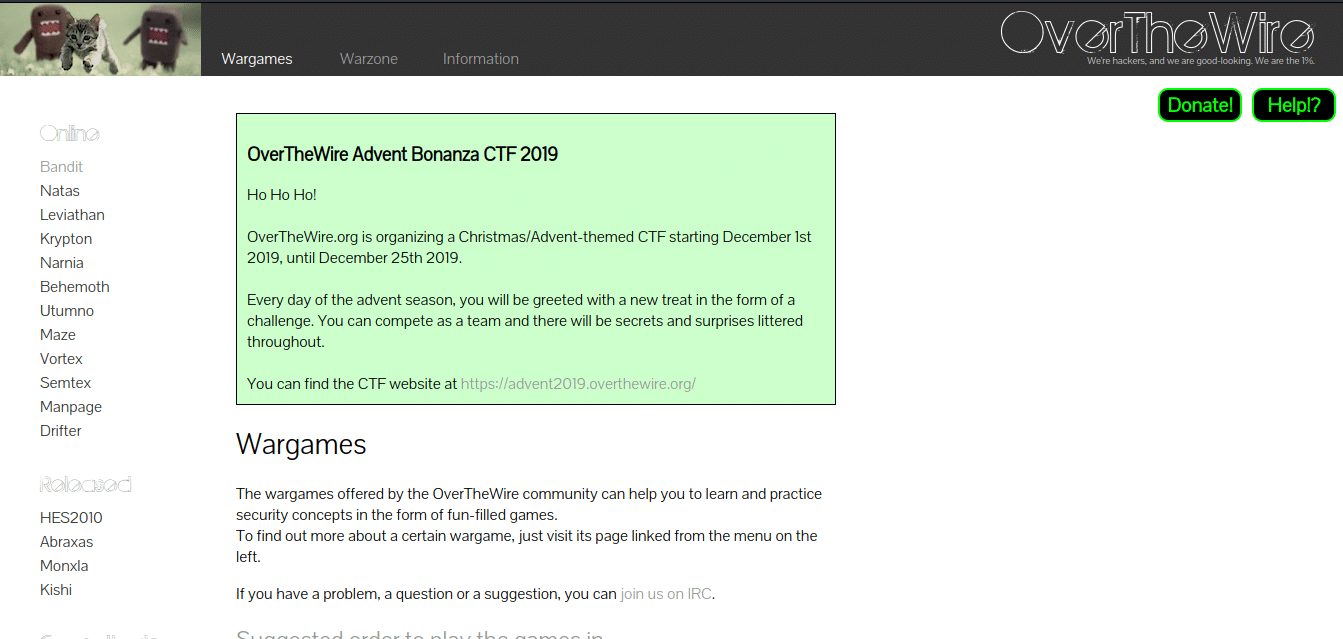
OverTheWire The wargames offered by the OverTheWire community can help you to learn and practice security concepts in the form of fun-filled games. To find out more about a certain wargame, just visit its page linked from the menu on the left. Suggested order to play the games in
- Bandit
- Leviathan or Natas or Krypton
- Narnia
- Behemoth
- Utumno
- Maze
- …
Each shell game has its own SSH port
Information about how to connect to each game using SSH is provided in the top left corner of the page. Keep in mind that every game uses a different SSH port.
microcorruption.com
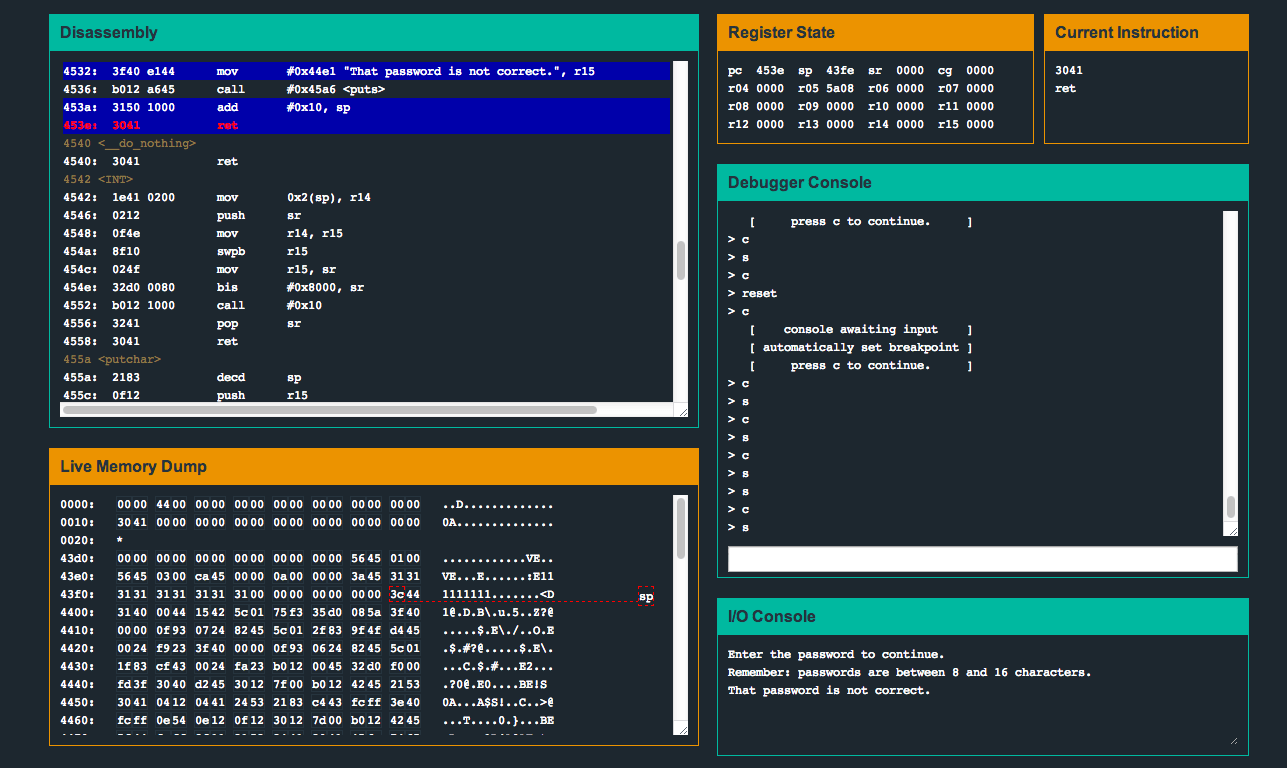
microcorruption.com Scattered throughout the world in locked warehouses are briefcases filled with Cy Yombinator bearer bonds that could be worth billions comma billions of dollars. You will help steal the briefcases.
Cy Yombinator has cleverly protected the warehouses with Lockitall electronic lock devices. Lockitall locks are unlockable with an app. We’ve positioned operatives near each warehouse; each is waiting for you to successfully unlock the warehouse by tricking out the locks. The Lockitall devices work by accepting Bluetooth connections from the Lockitall LockIT Pro app. We’ve done the hard work for you: we spent $15,000 on a development kit that includes remote-controlled locks for you to practice on, and reverse engineered enough of it to build a primitive debugger.
Using the debugger, you’ll be able to single-step the lock code, set breakpoints, and examine memory on your own test instance of the lock. You’ll use the debugger to find an input that unlocks the test lock, and then replay it to a real lock. It should be a milk run. Good luck. We’ll see you on a beach in St Tropez once you’re done.
XSS game
XSS game Cross-site scripting (XSS) bugs are one of the most common and dangerous types of vulnerabilities in Web applications. These nasty buggers can allow your enemies to steal or modify user data in your apps and you must learn to dispatch them, pronto!
In this training program, you will learn to find and exploit XSS bugs. You’ll use this knowledge to confuse and infuriate your adversaries by preventing such bugs from happening in your applications.
There will be cake at the end of the test.
HackThis!!
HackThis!! was initially designed so that the students can be taught how to hack, and teach the students about dumps and defacement. If you are an expert hacker then for you, there are 50 levels of difficulty to offer. The website comes with a great online community to help you with hacking, and it would keep you up to date with the security news.
crackmes.one
crackmes.one This is a simple place where you can download crackmes to improve your reverse engineering skills. If you like to submit a crackme or a solution to one of them, you must register. But before that, I strongly recommend you to read the FAQ.
HackThisSite

Hack This Site is a free, safe and legal training ground for hackers to test and expand their hacking skills. HackThisSite commonly referred to as HTS, is an online hacking and security website founded by Jeremy Hammond. More than just another hacker wargames site, we are a living, breathing community with many active projects in development, with a vast selection of hacking articles and a huge forum where users can discuss hacking, network security, and just about everything. Tune in to the hacker underground and get involved with the project.
Pentest training

Pentest training is a simple website used as a hub for information revolving around the varies services we offer to help both experienced and new penetration testers practice and hone their skills. We offer a fully functioning penetration testing lab that is ever-increasing in size, complexity, and diversity. The lab has a fully functioning Windows domain with various Windows OS’s. There is also a selection of Boot2Root Linux machines to practice your CTF and escalation techniques and finally, pre-built web application training machines.
Hellbound Hackers
Hellbound Hackers provides a hands-on approach to computer security. Learn how hackers break-in, and how to keep them out. Huge resource for computer security researchers. The website emphasizes being hands-on, and it offers you many challenges to make you the best hacker out there. It offers a variety of challenges to teach you how to identify potential vulnerabilities, and it also suggests the ways to patch the vulnerabilities. The website comes with an array of tutorials and a thriving community of more than 100K registered members.
HAX.TOR
hax.tor.hu is a very old site (founded in 2006). But it serves the purpose of learning the stuff. Many problems are not functioning because of technology changes. Because many problems relied on the old PHP version flaws. Also, the player gets a free shell account to use (with web/mail hosting) on a server (with gigabit bandwidth) dedicated to security folks.
A few examples of HaX.ToR challenges:
Level 1. Make a nasa.gov URL display a text of my choice
Level 7. snifflog.txt - ngrep format
Level 13. PHP with a source - needs exploiting and/or -t-b thinking
Level 16. root:hsmfs;g@10.0.0.5
Level 21. Backdoor on a suspended domain
Level 26. PHP file manager with a source - needs more exploit
Level 28. telnet://hax.tor.hu:1800 - Google Word Game
Level 33. Defense Information Systems Agency - 209.22.99.66
Level 39. China Science And Technology Network
Level 48. .htaccess editor vs basic auth
Level 49. Forged DNS from the CIA
ThisIsLegal
ThisisLegal, a hacker wargames site with much more - such as forums and tutorials. The aim of the site is to help you learn and improve as much as we can and also provide a community with a chance to chat. The site is always up for suggestions for improvement and any challenge submissions or tutorial content are also welcome so please help to improve our community.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.