Wi Ploit Wi Fi Exploit Tool

Wi-Ploit is a library of Wi-Fi exploitation tools. Supports the latest other tools e.g: Aircrack-ng etc.
Attacks:
- Rogue Access Point (hostapd).
- Rogue Access Point (hostapd-mana).
- WPS attack (Reaver) * Upcoming.
A rogue access point is a wireless access point that has been installed on a secure network without explicit authorization from a local network administrator, whether added by a well-meaning employee or by a malicious attacker.
Rogue Access Point (hostapd)
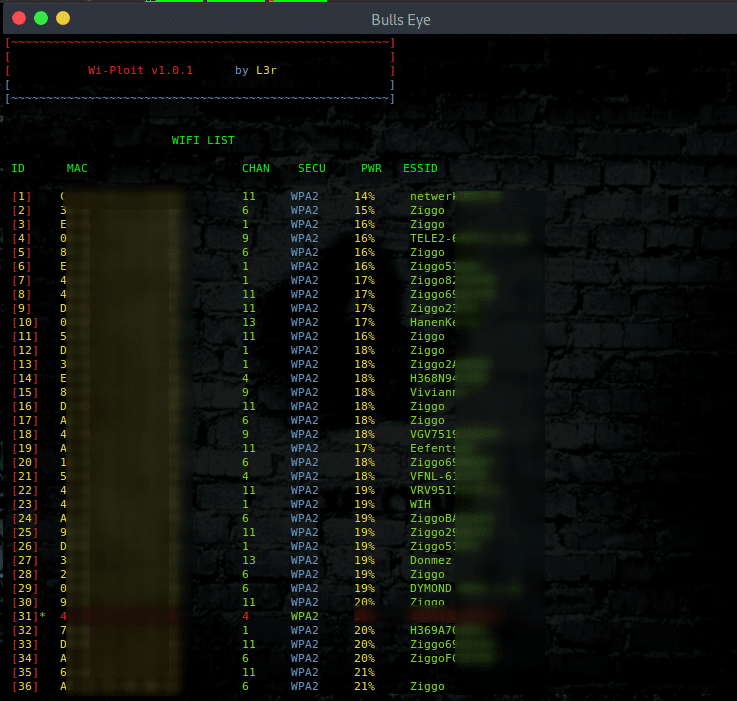
- Scan the networks.
- Capture a handshake (can’t be used without a valid handshake, it’s necessary to verify the password)
- Use WEB Interface *
- Launch a FakeAP instance to imitate the original access point
- Spawns a MDK3 process, which deauthenticated all users connected to the target network, so they can be lured to connect to the FakeAP and enter the WPA password.
- A fake DNS server is launched in order to capture all DNS requests and redirect them to the host running the script
- A captive portal is launched in order to serve a page, which prompts the user to enter their WPA password
- Each submitted password is verified by the handshake captured earlier
- The attack will automatically terminate, as soon as a correct password is submitted.
Rogue Access Point (hostapd-mana)
hostapd-mana is a featureful rogue wifi access point tool. It can be used for a myriad of purposes from tracking and deanonymising devices (aka Snoopy), gathering corporate credentials from devices attempting EAP (aka WPE) or attracting as many devices as possible to connect to perform MitM attacks.
Attracting as many devices as possible to connect to perform MitM attacks.
- Scan the networks.
- Capture a handshake (can’t be used without a valid handshake, it’s necessary to verify the password)
- Use WEB Interface *
- Launch a FakeAP instance to imitate the original access point AND VICTIMS AUTOMATICALLY CONNECTS TO CREATED FAKEAP
- Spawns a MDK3 process, which deauthenticated all users connected to the target network, so they can be lured to connect to the FakeAP and enter the WPA password.
- A fake DNS server is launched in order to capture all DNS requests and redirect them to the host running the script
- A captive portal is launched in order to serve a page, which prompts the user to enter their WPA password
- Each submitted password is verified by the handshake captured earlier
- The attack will automatically terminate, as soon as a correct password is submitted
Requirements
- Kali Linux OS or Ubuntu 18.04 OS (Also tested on Parrot Security)
- You will need an external Wireless Adapters
Recommended Wireless Adapters Chipsets
https://github.com/Johnler/Wi-Ploit#recommended-wireless-adapters-chipsets
- Atheros: ATH9KHTC (AR9271, AR7010)
Tested: AR9271 (AWUS036NHA) - Ralink: RT3070
- Realtek: RTL8192CU

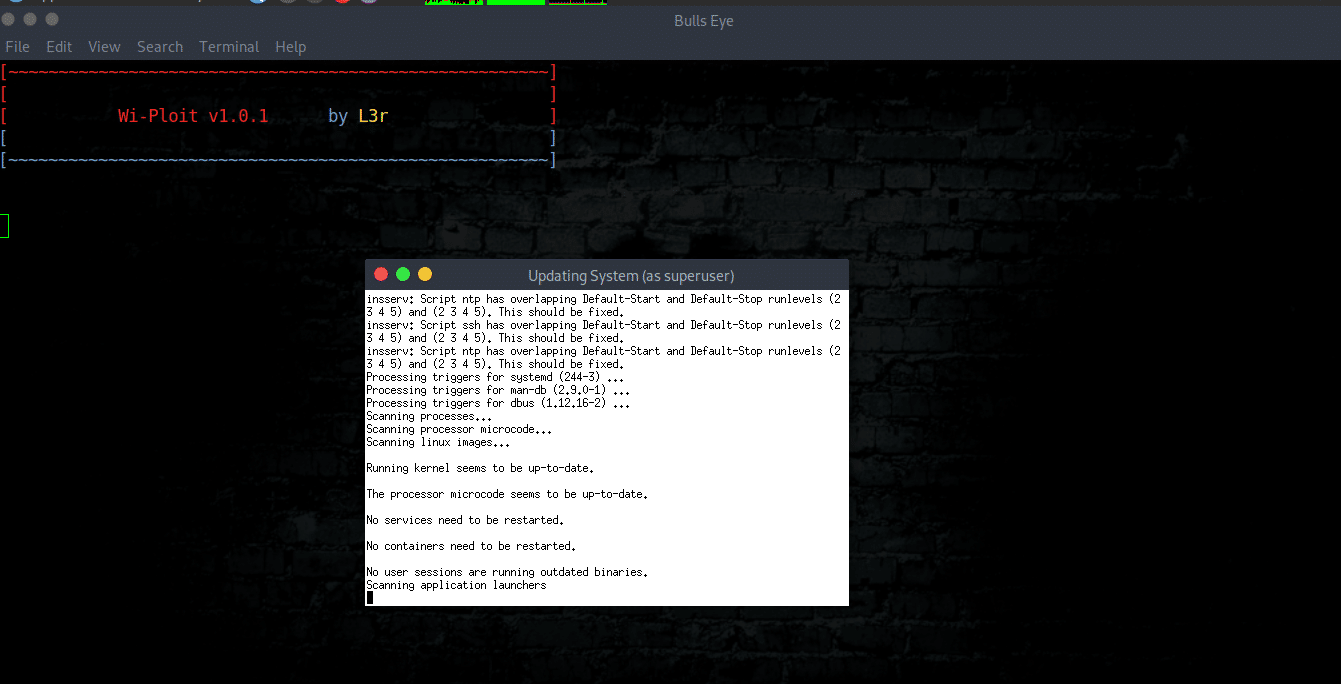
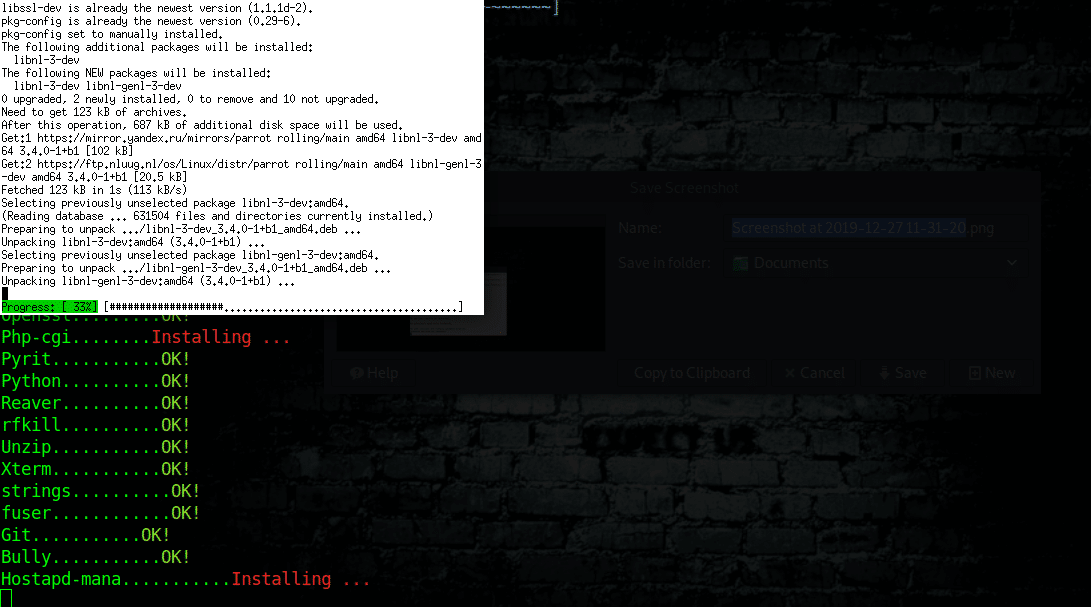
Installation
|
|
|
|
|
|
|
|
|
|
Use
|
|
Just make sure you hit ctrl+c when you’re satisfied with the SSID scan, capture the handshake and then launch.
Wi-Ploit Version
1.b.c
b = major release
c = minor release
Credits
- vk496 - developer(s) of linset
- deltaxflux - developer(s) of fluxion
- SensePost - developer(s) of hostapd-mana
- https://github.com/Johnler/Wi-Ploit (Johnler)
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.