WIRED Magazine Hacked: 2.3 Million Records Leaked via Basic IDOR Vulnerability
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
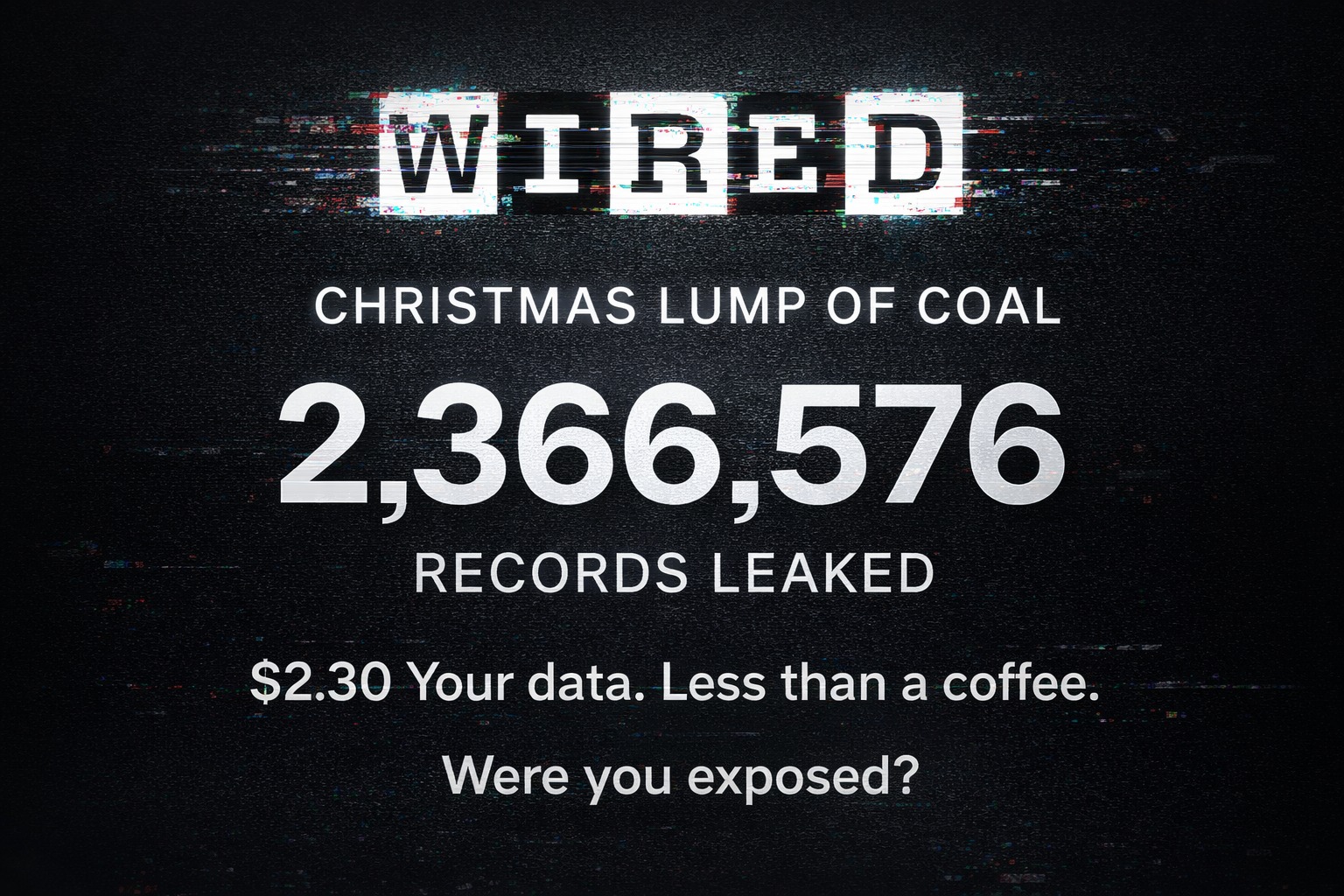
WIRED magazine got hacked. 2.3 million subscriber records leaked. And this is just the beginning. 😏 A hacker called “Lovely” dumped the database on Christmas Day. Called it a “Christmas Lump of Coal.”
The vulnerability? IDOR. Insecure Direct Object Reference. That’s OWASP Top 10. Basic web security. A flaw that’s been documented since 2007. Companies still get it wrong.
IDOR happens when a website uses a number to identify your data, but doesn’t check if you’re actually allowed to see it. Your profile lives at /api/user/12345. Change that to /api/user/12346? You see someone else’s profile. No password needed. The server just hands it over.
The attacker simply iterated through user IDs. There was no authentication required. Just… count up. 1, 2, 3, 4… all the way to 2.3 million profiles.
What got exposed: → 2,366,576 email addresses → 285,936 full names → 102,479 HOME ADDRESSES → 32,426 phone numbers → Birthdates, genders, account data going back to 2011
No passwords or payment data were exposed. But everything else? Out there.
102,000 home addresses in criminal hands. Your digital identity sold for $2.30 in forum credits. Less than a cup of coffee.
The hackers tried to report the vulnerability FIRST. “Lovely” contacted DataBreaches[.]net on November 22nd, claiming to be a security researcher. Asked for help reaching Condé Nast’s security team. Why couldn’t they reach Condé Nast directly? Because this billion-dollar media company has NO security.txt file.
security.txt is RFC 9116. A simple text file that tells researchers how to report vulnerabilities. Google has one. Facebook has one. GitHub has one. CISA recommends it.
Condé Nast? Nothing. Nowhere on their site explains how to report security issues. Weeks of silence. No response from Condé Nast.
The hacker got frustrated. Turned out they claimed to have downloaded 33 MILLION accounts. Found SIX vulnerabilities, not one. DataBreaches[.]net got played.
→ December 20th: Data leaked on hacking forums
→ December 25th: Full WIRED database dumped publicly
→ December 30th: Still no statement from Condé Nast
The threat? 40 million MORE records coming.
Condé Nast owns Vogue, The New Yorker, Vanity Fair, GQ, Architectural Digest, Bon Appétit, Ars Technica, and more. The hacker claims access to their ENTIRE centralized identity platform.
Hudson Rock verified the leaked data by cross-referencing it with RedLine and Raccoon infostealer logs. Latest entries dated September 9, 2025.
Check if YOU are in the leak: → Go to haveibeenpwned[.]com → Enter your email address → Click “pwned?” → Look for “WIRED” in the results
The WIRED data is already indexed. If you ever had a WIRED account, even years ago, check it.
If you’re affected: → Change your password on any Condé Nast site immediately → If you reused that password elsewhere, change it there too → Enable 2FA wherever possible → Be alert for phishing emails using your leaked data
IDOR vulnerabilities are embarrassingly common. And embarrassingly easy to find. Companies without proper vulnerability disclosure channels CREATE the problems they fear. A security.txt file takes 5 minutes to create. There’s no excuse.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.