Xspear Powerful Xss Scanner
Want to learn ethical hacking? I built a complete course. Have a look!
Learn penetration testing, web exploitation, network security, and the hacker mindset:
→ Master ethical hacking hands-on
(The link supports me directly as your instructor!)
Hacking is not a hobby but a way of life!
Xspear is a very powerful XSS scanning and parameter analysis tool on ruby gems, capable of both static and dynamic XSS vulnerability analysis.
In this article and video, I will show you how to install and use Xspear. This awesome tool has the ability to scan, detect and analyze potential XSS vulnerabilities on web applications.

What is (XSS) Cross-site Scripting
XSS is one of the most common hacking technique when it comes to web application vulnerabilities, and occurs when a web app generates an output based on user input.
XSS Example
The HTML snippet
| |
is intended to show a template snippet that, if the variable title has value Cross-Site Scripting, results in the following HTML to be emitted to the browser:
| |
A site containing a search field does not have the proper input sanitizing. By crafting a search query looking something like this:
| |
sitting on the other end, at the webserver, you will be receiving hits where after a double space is the user’s cookie. If an administrator clicks the link, an attacker could steal the session ID and hijack the session.
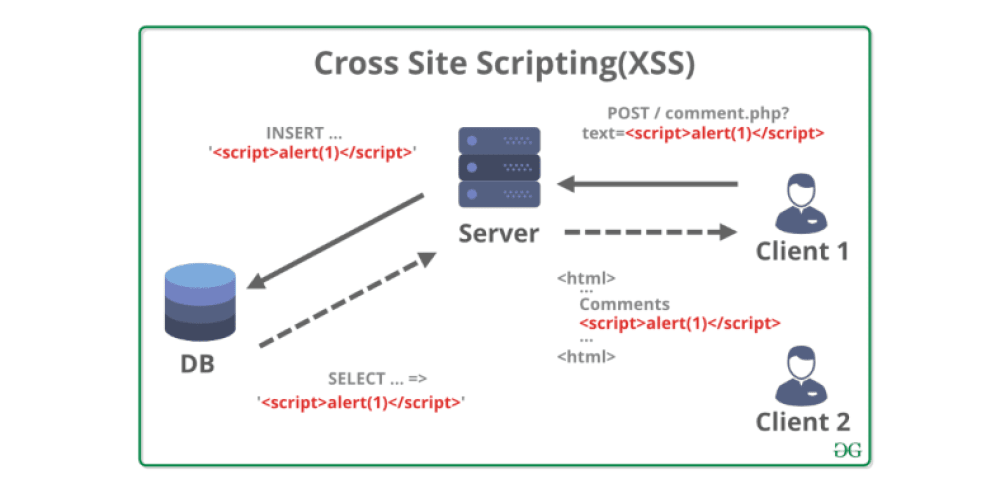
In another subsequent article I would go further in Cross-site Scripting.
XSpear: Powerful XSS Scanning and Parameter Analysis Tool
It’s one of the XSS vulnerability scanning tools available on ruby gems that can run analysis on both responses and requests, including pattern matching based XSS scanning, Blind XSS testing as well as testing at selected parameters.
Key features
Pattern matching based XSS scanning
Detect
alertconfirmpromptevent on headless browser (with Selenium)Testing request/response for XSS protection bypass and reflected(or all) params
- Reflected Params
- All params(for blind XSS, anything)
- Filtered test event handler HTML tag Special Char Useful code
- Testing custom payload for only you!
Testing Blind XSS (with XSS Hunter, ezXSS, HBXSS, Etc all URL base blind test…)
Dynamic/Static Analysis
- Find the SQL Error pattern
- Analysis of Security headers(CSP HSTS X-frame-options, XSS-protection, etc.. )
- Analysis Other headers..(Server version, Content-Type, etc…)
- XSS Testing to URI Path
- Testing Only Parameter Analysis (aka no-XSS mode)
Scanning from Raw file(Burp suite, ZAP Request)
XSpear running on ruby code(with Gem library)
Show table base cli-report and filtered rule, testing raw query(URL)
Testing at selected parameters
Support output format cli JSON HTML
- cli
- json
- HTML
Support Verbose level (0~3)
- 0: quite mode(only result)
- 1: show scanning status(default)
- 2: show scanning logs
- 3: show detail log(req/res)
Support custom callback code to any test various attack vectors
Support Config file
Installation XSpear
Install it yourself as:
| |
Or install it yourself as (local file / download latest ):
| |
Add this line to your application’s Gemfile:
| |
And then execute:
| |
Dependency gems
colorize selenium-webdriver terminal table progress_bar
If you configured it to install automatically in the Gem library, but it behaves abnormally, installs it with the following command.
| |
| |
| |
| |
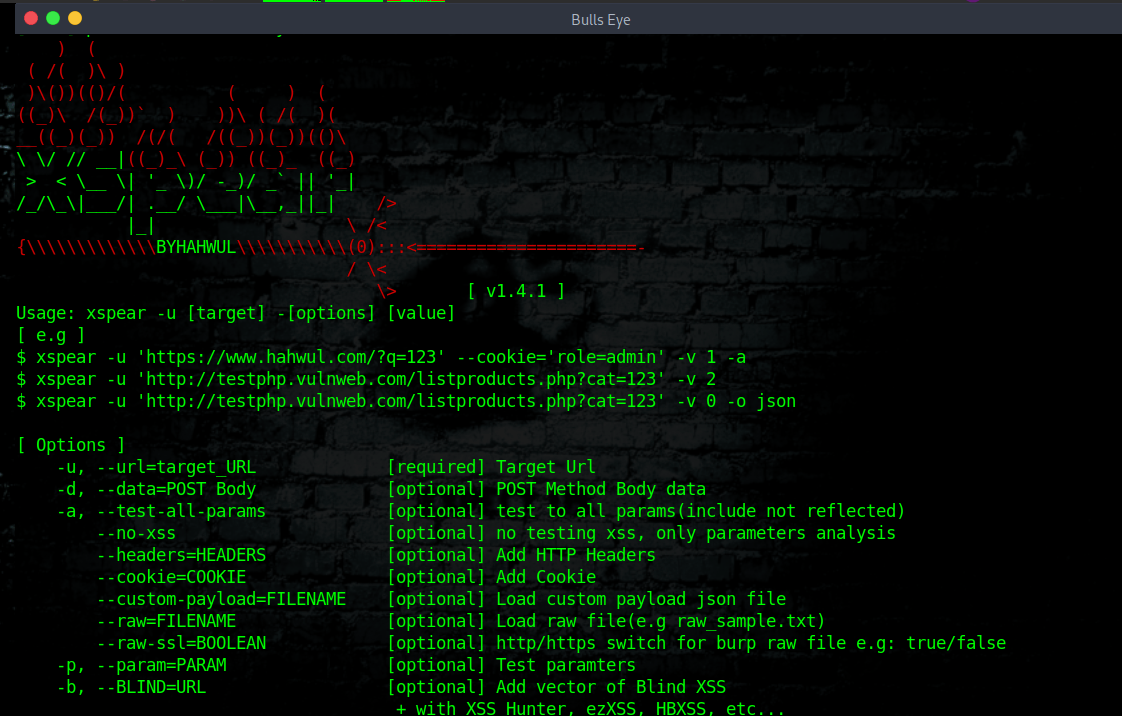
Usage XSpear
Run -h to get a list of available options:
| |
| |
Example: Scanning XSS
Quite mode
| |
Show scanning log
| |
XSS Test Website
(XSS) Cross-site Scripting Testing
Fortunately, there are companies that have set up certain “test websites”. They make it easier for us “Hackers” to test these kinds of tools and improve your skills. There are several such websites. I want to talk about that in a future article.
This web application is open source! Get your copy from GitHub and take advantage of advanced features
The AltoroJ website is published by IBM Corporation for the sole purpose of demonstrating the effectiveness of IBM products in detecting web application vulnerabilities and website defects.
This site is not a real banking site. Similarities, if any, to third party products and/or websites are purely coincidental. This site is provided “as is” without warranty of any kind, either express or implied. IBM does not assume any risk in relation to your use of this website.
If you’d like to try AltoroJ but want to skip all of the cool software development stuff, use publicly hosted version, available at http://altoromutual.com:8080/. You will not be able to enable any of the advanced options and this site may not always be available, but it’s the easiest way to get started
XSpear Video
In this video, I’ll show you how to install and use XSpear. It is a handy tool for Bug Bounty. Be creative. And have fun.
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.
→ Stay updated!
Get the latest posts in your inbox every week. Ethical hacking, security news, tutorials, and everything that catches my attention. If that sounds useful, drop your email below.